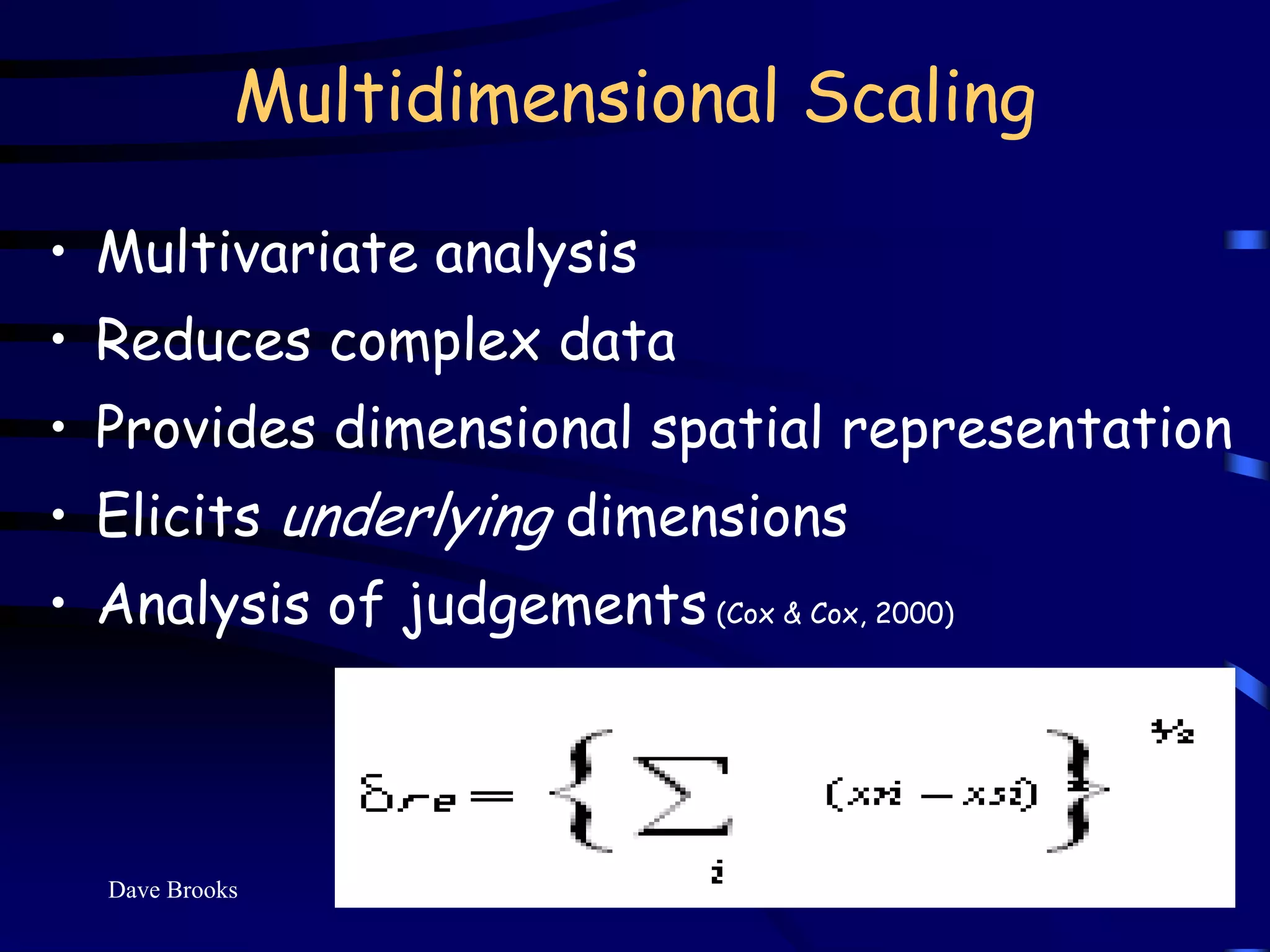
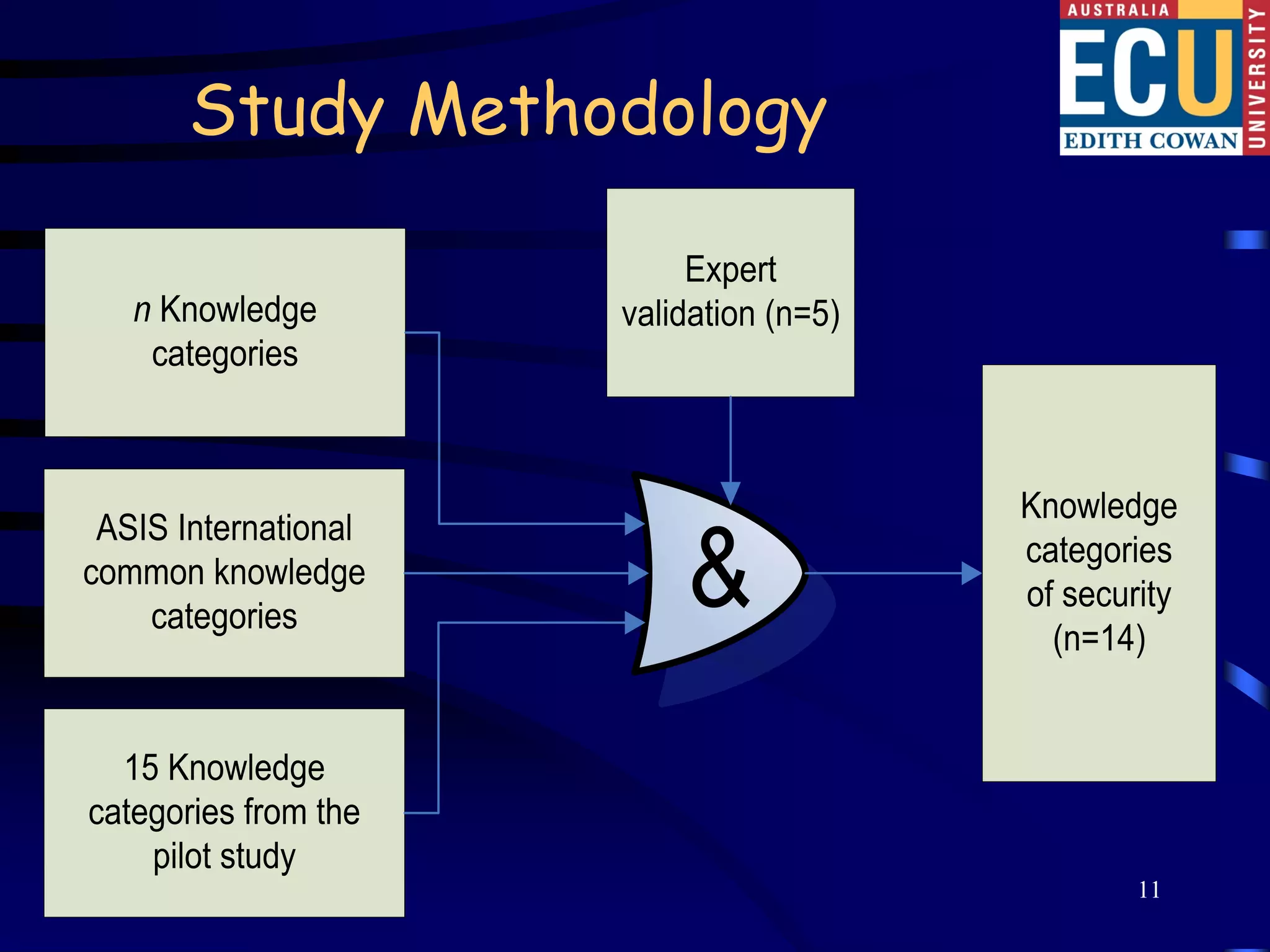
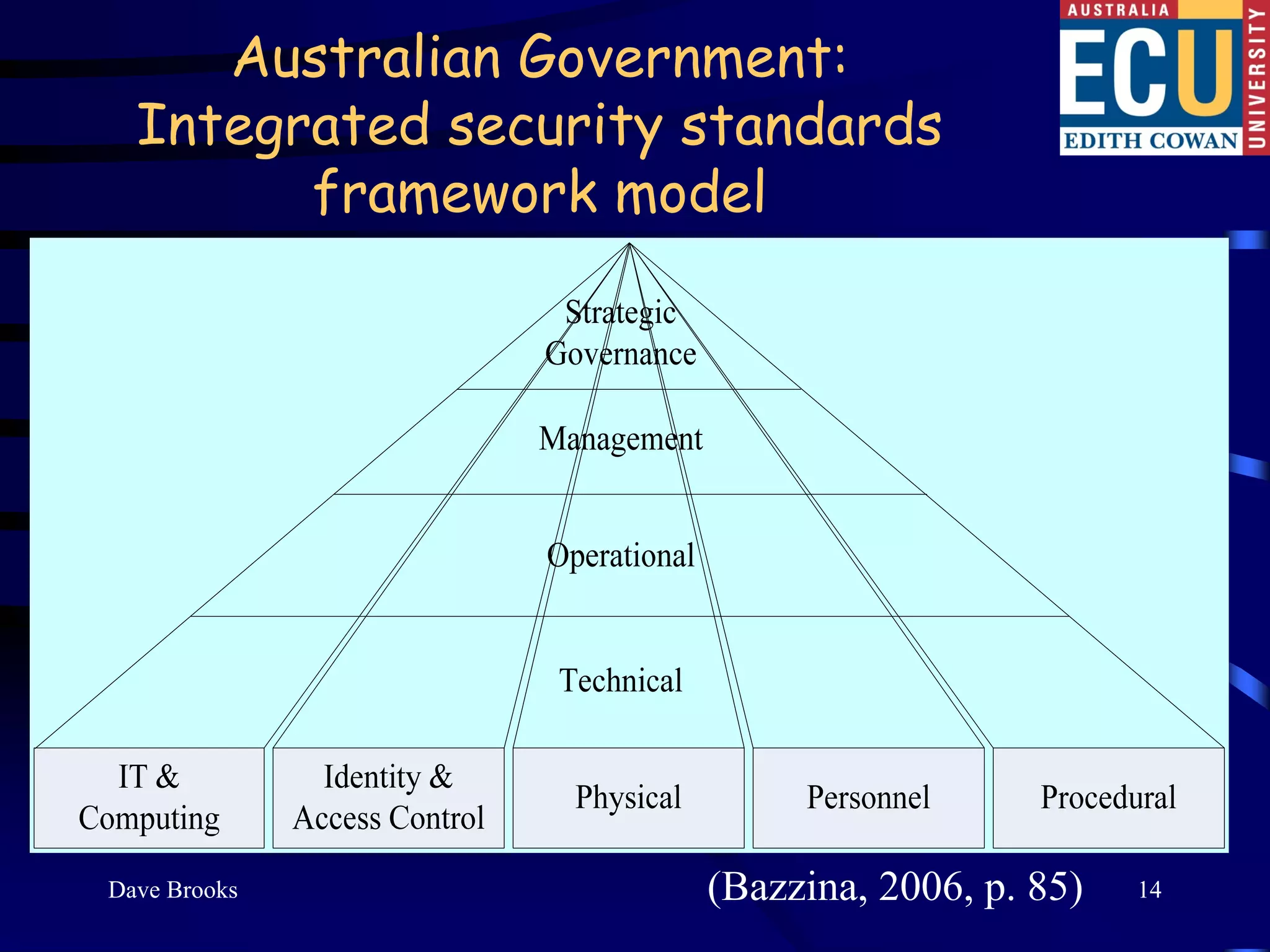
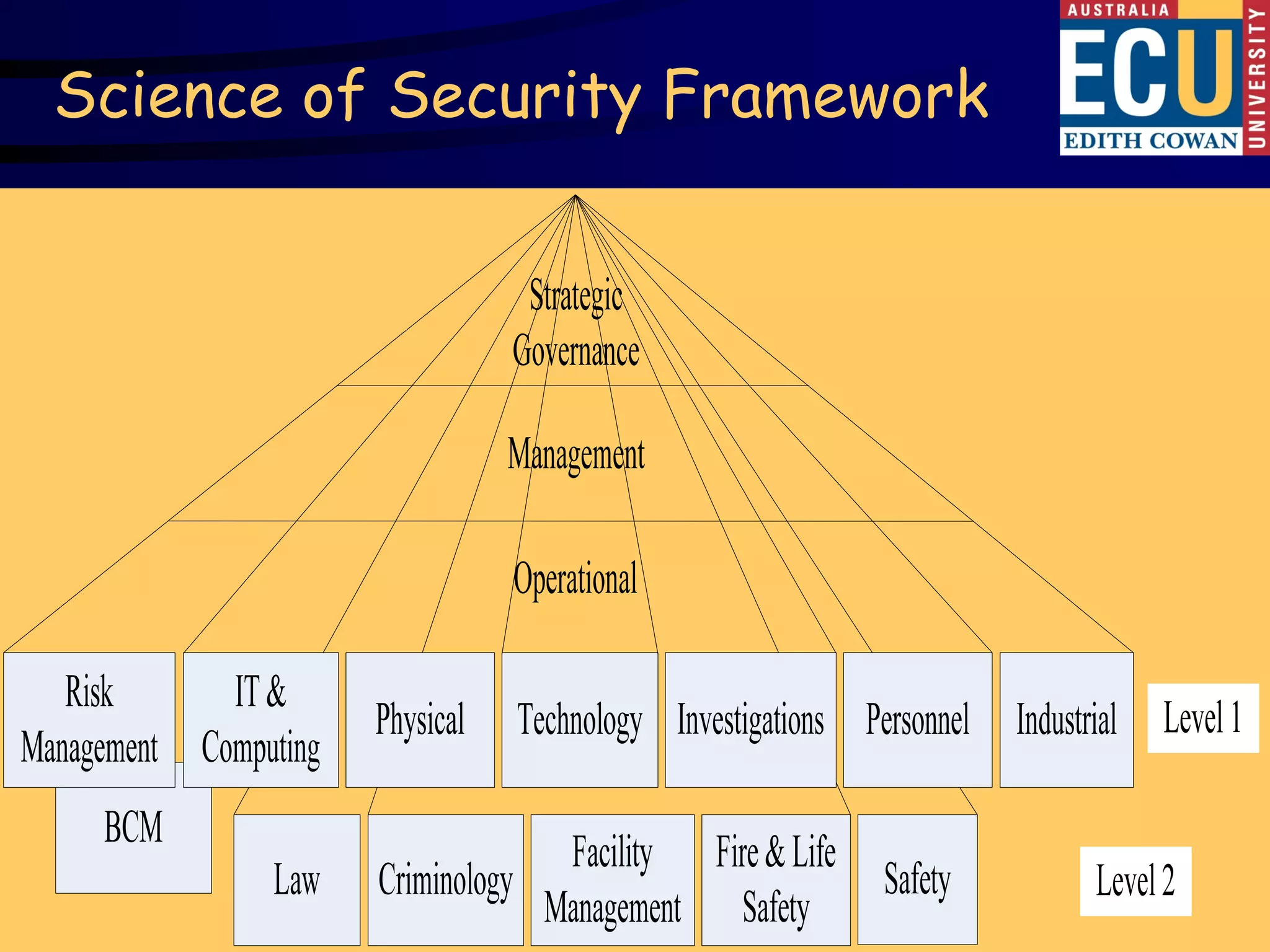
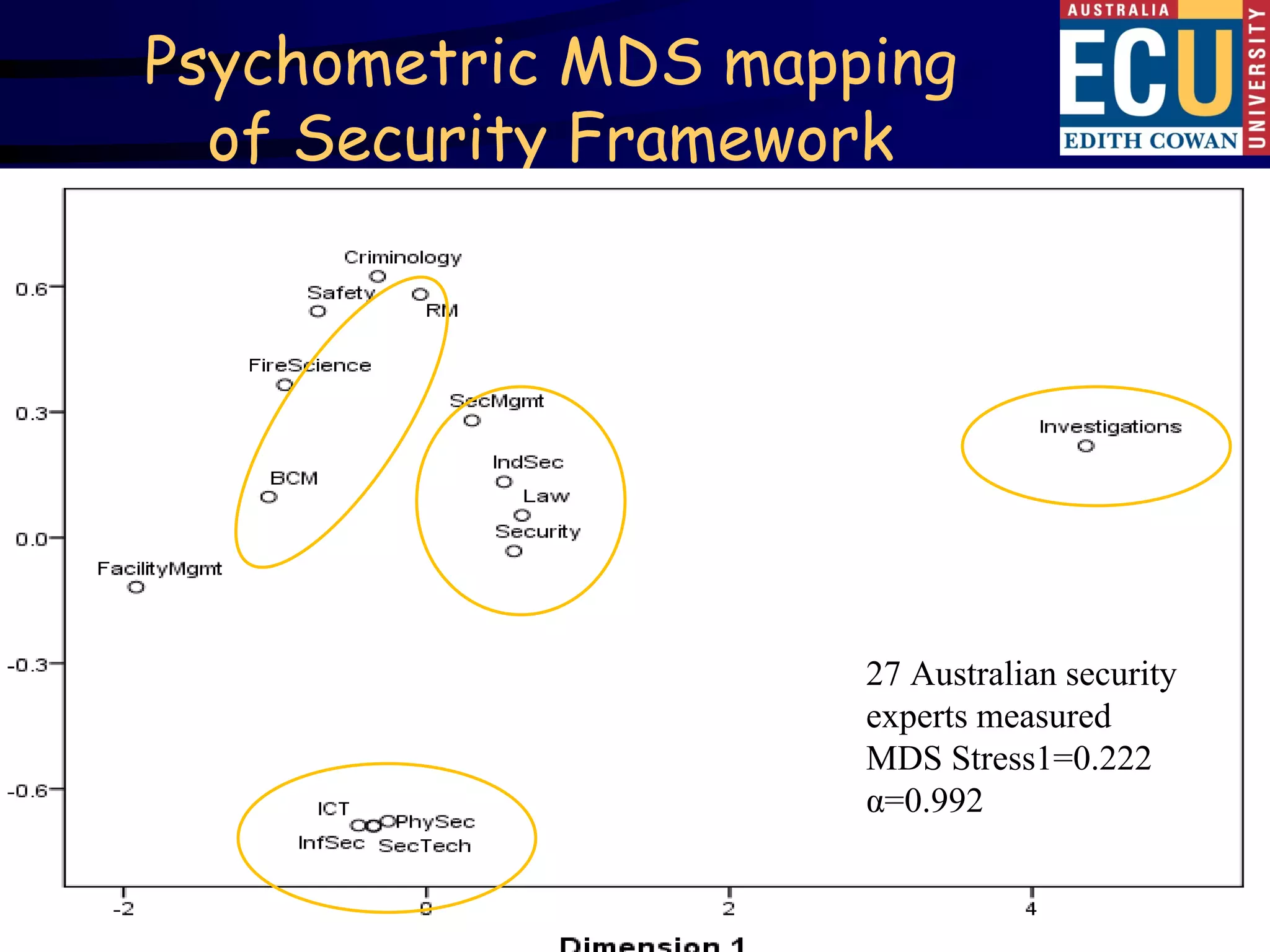
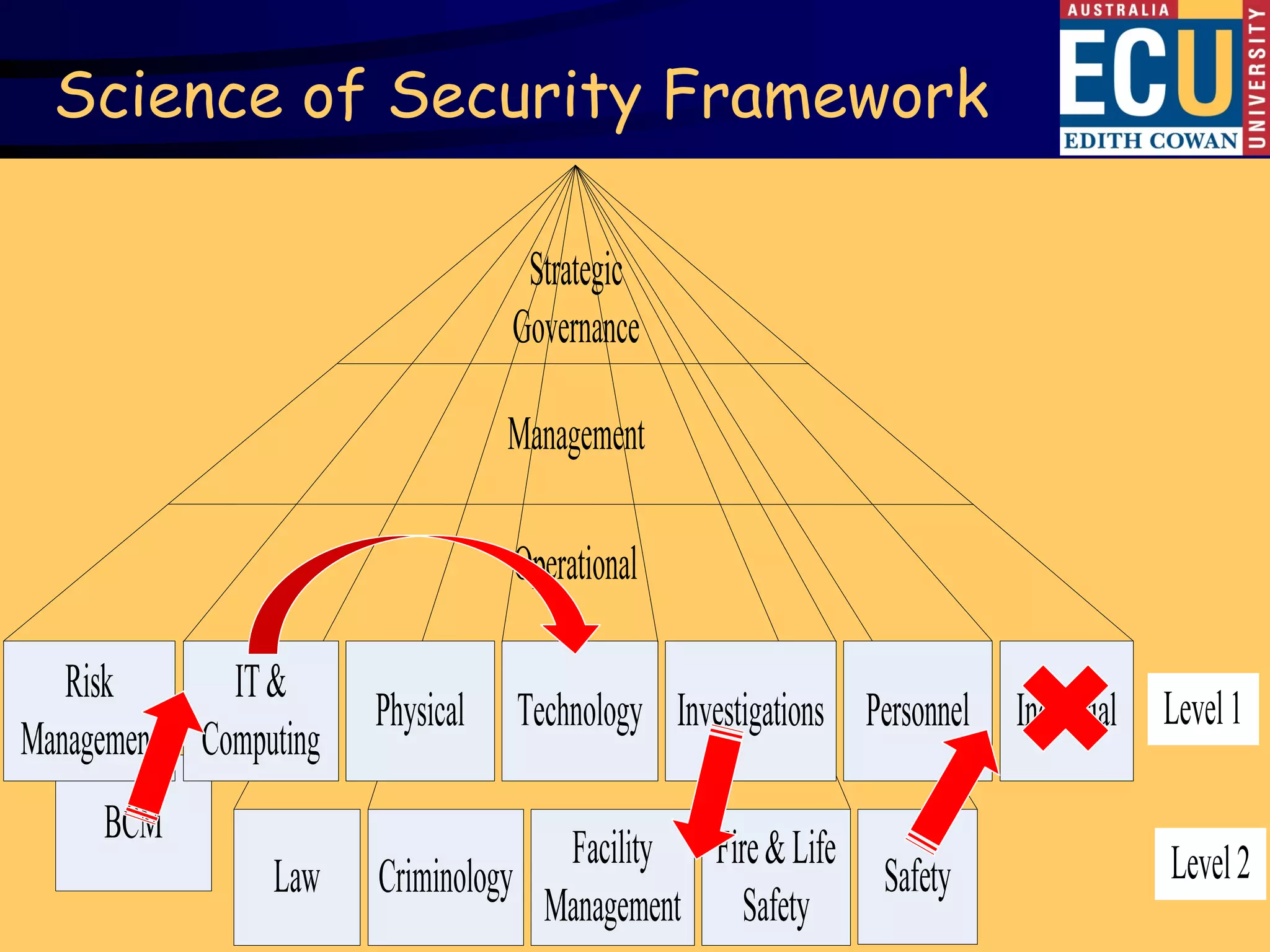
This document summarizes Dr. David Brooks' presentation at the 2009 ASIS International Security Conference in Hong Kong. The presentation developed an educational framework of integrated security knowledge categories through analyzing over 100 tertiary security courses. Key findings included identifying common security categories and developing a science of security framework through multidimensional scaling of experts' knowledge ratings. The framework aims to develop a consensus on the body of knowledge for corporate security.