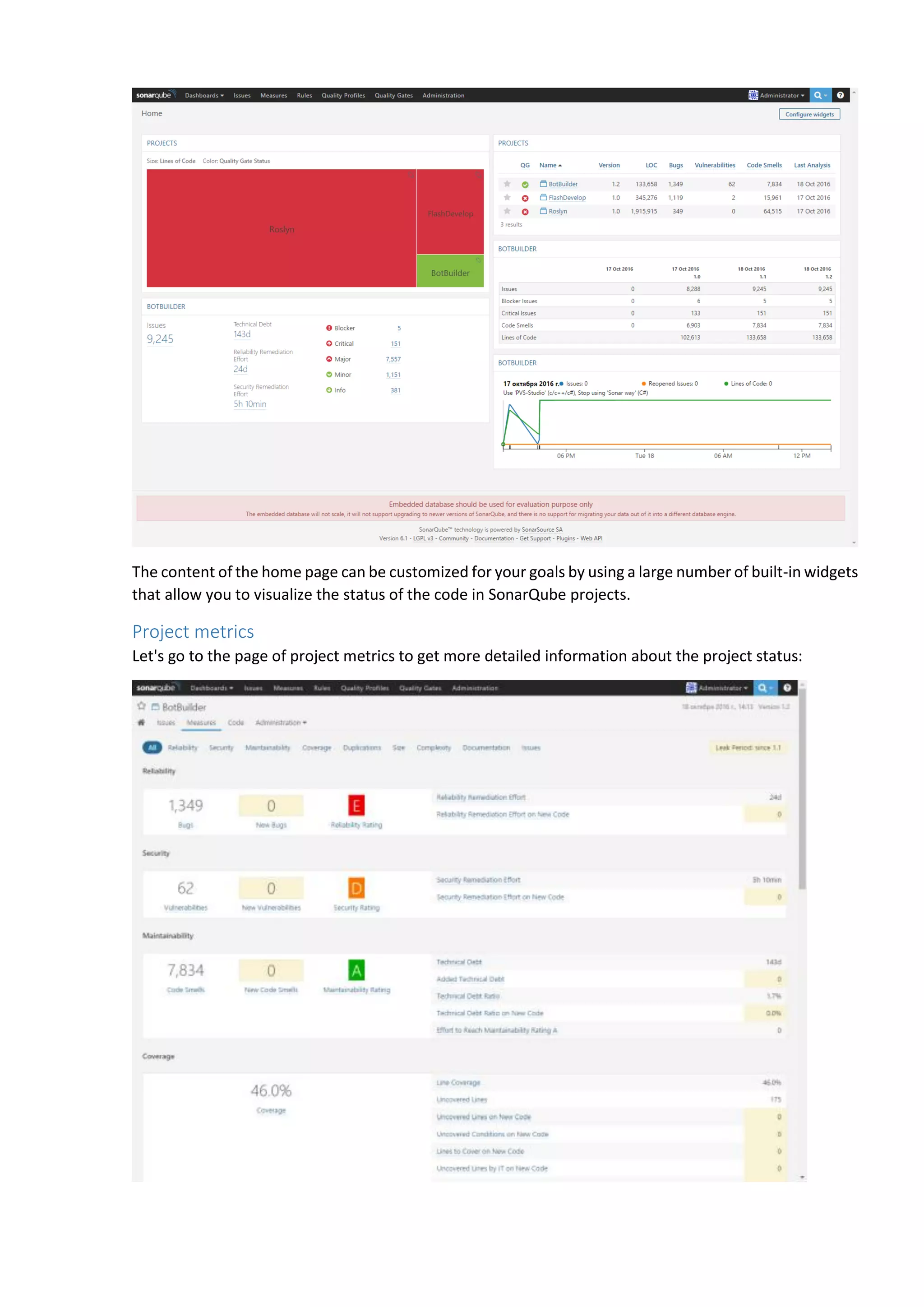
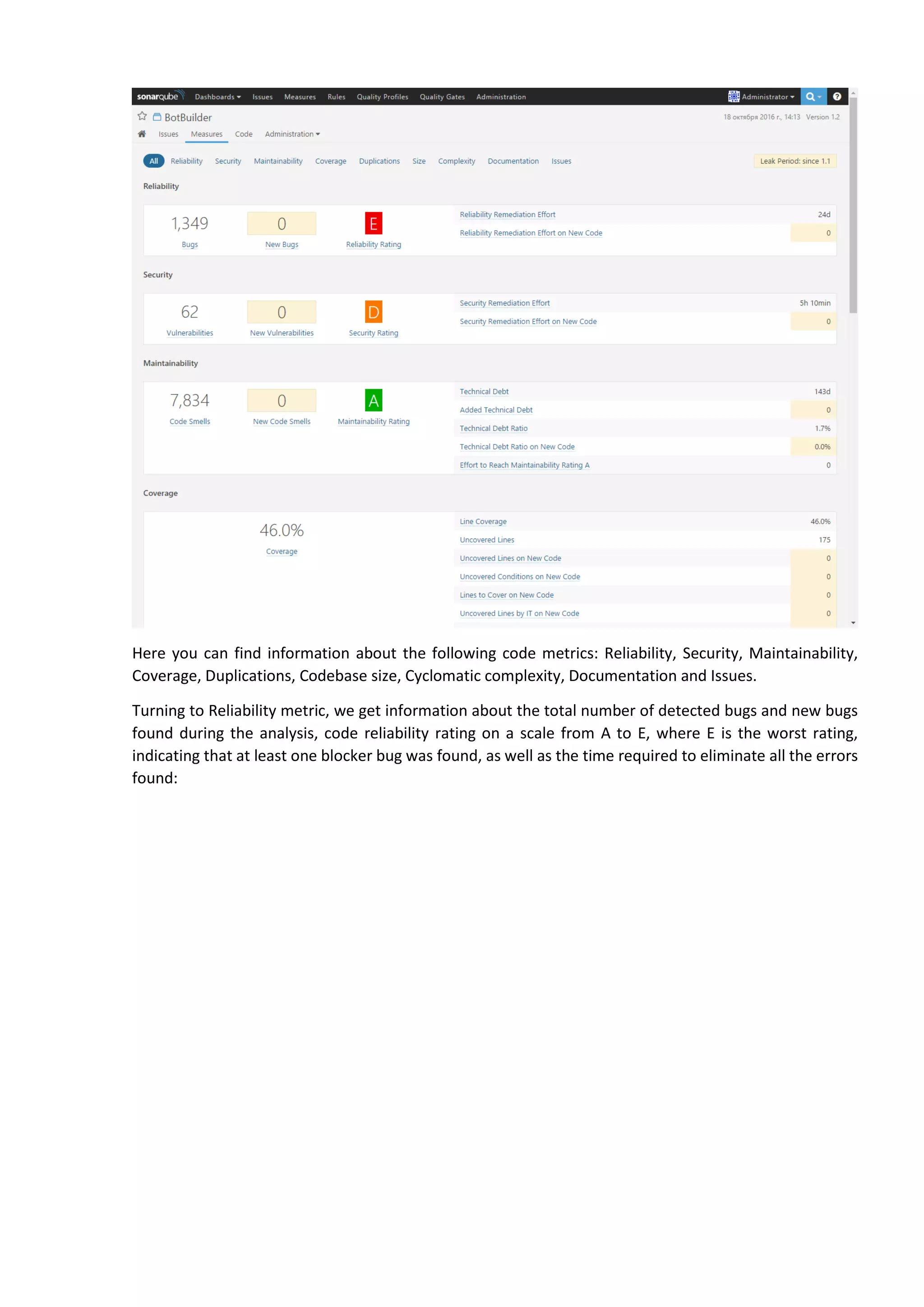
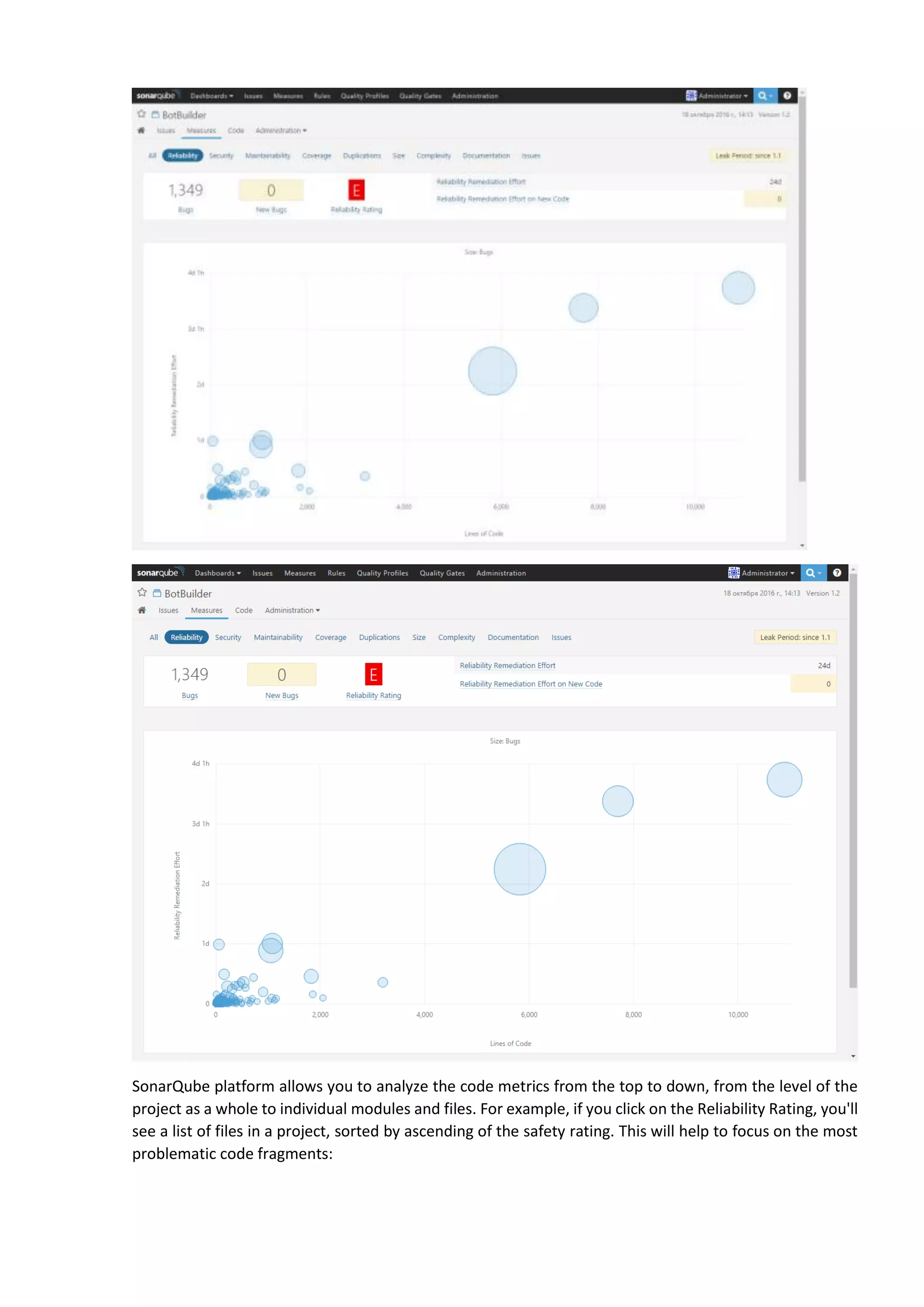
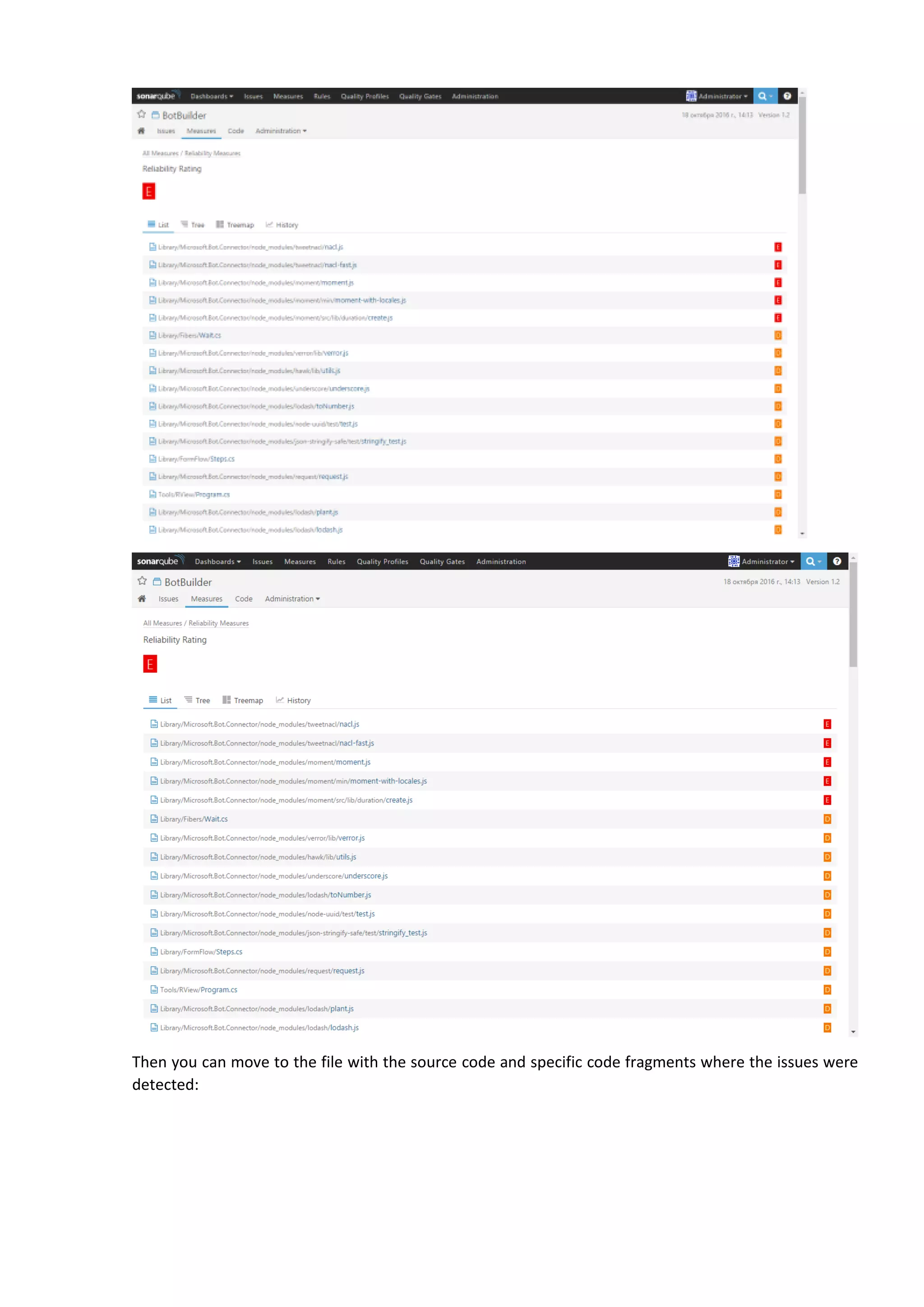
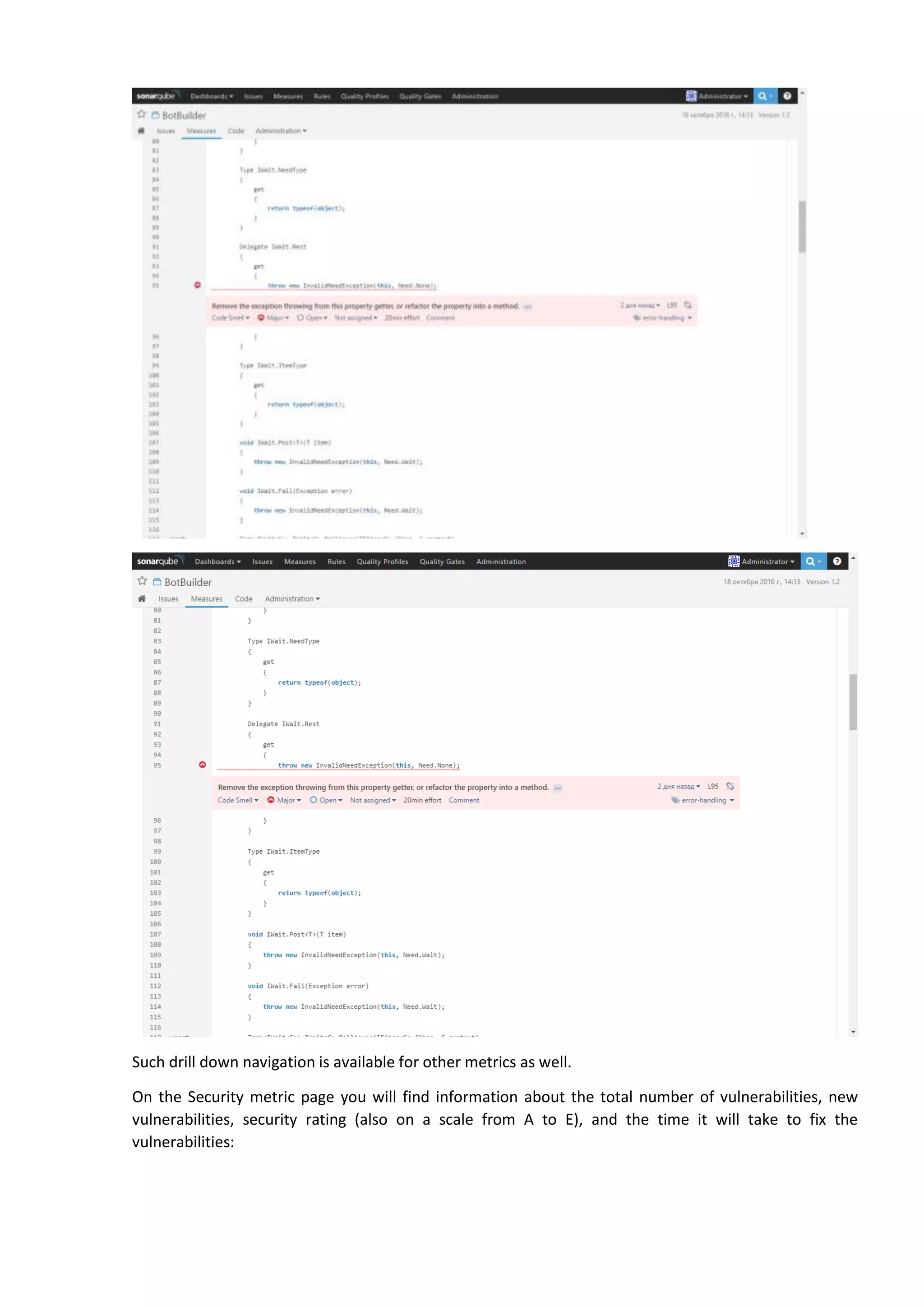
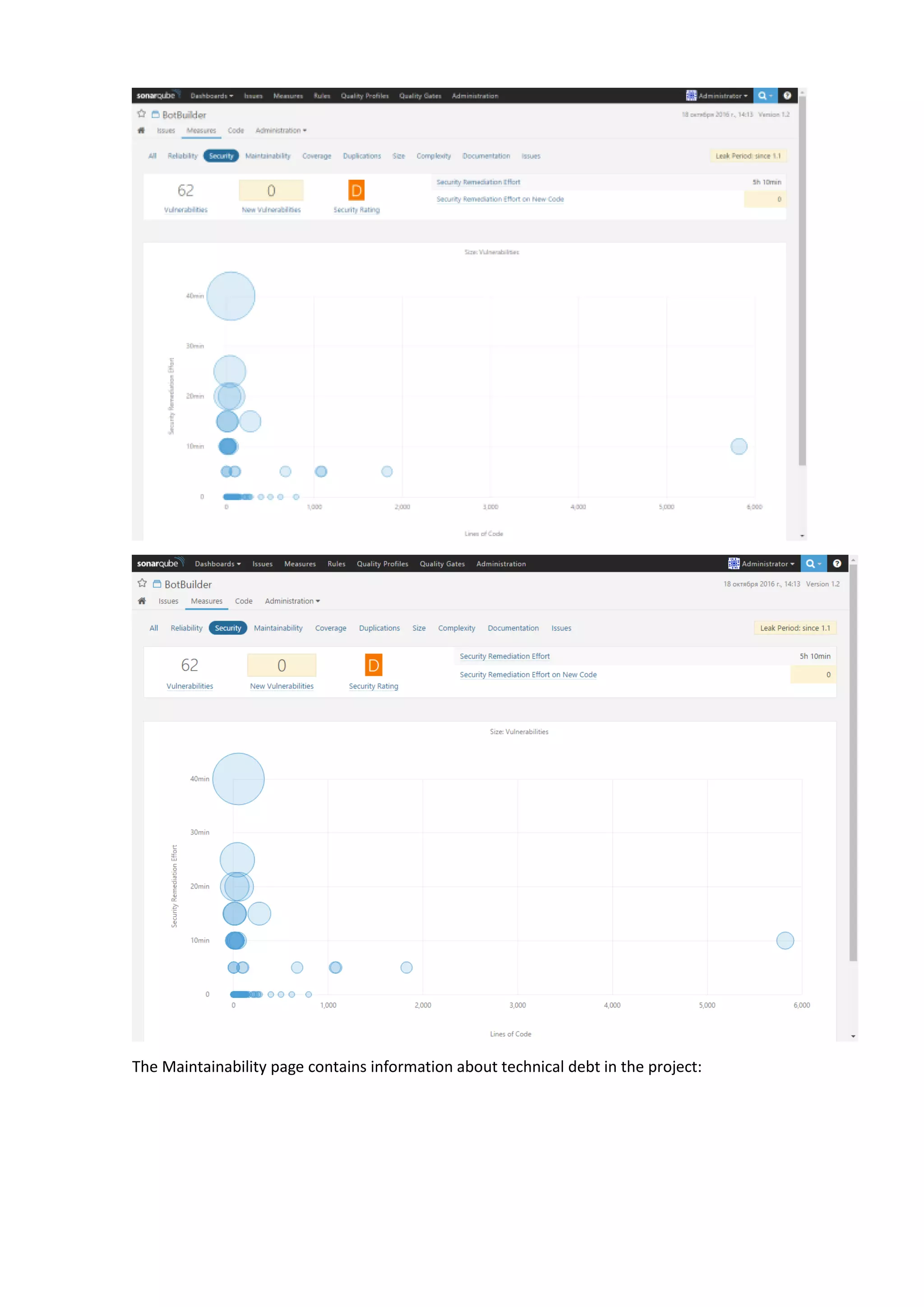
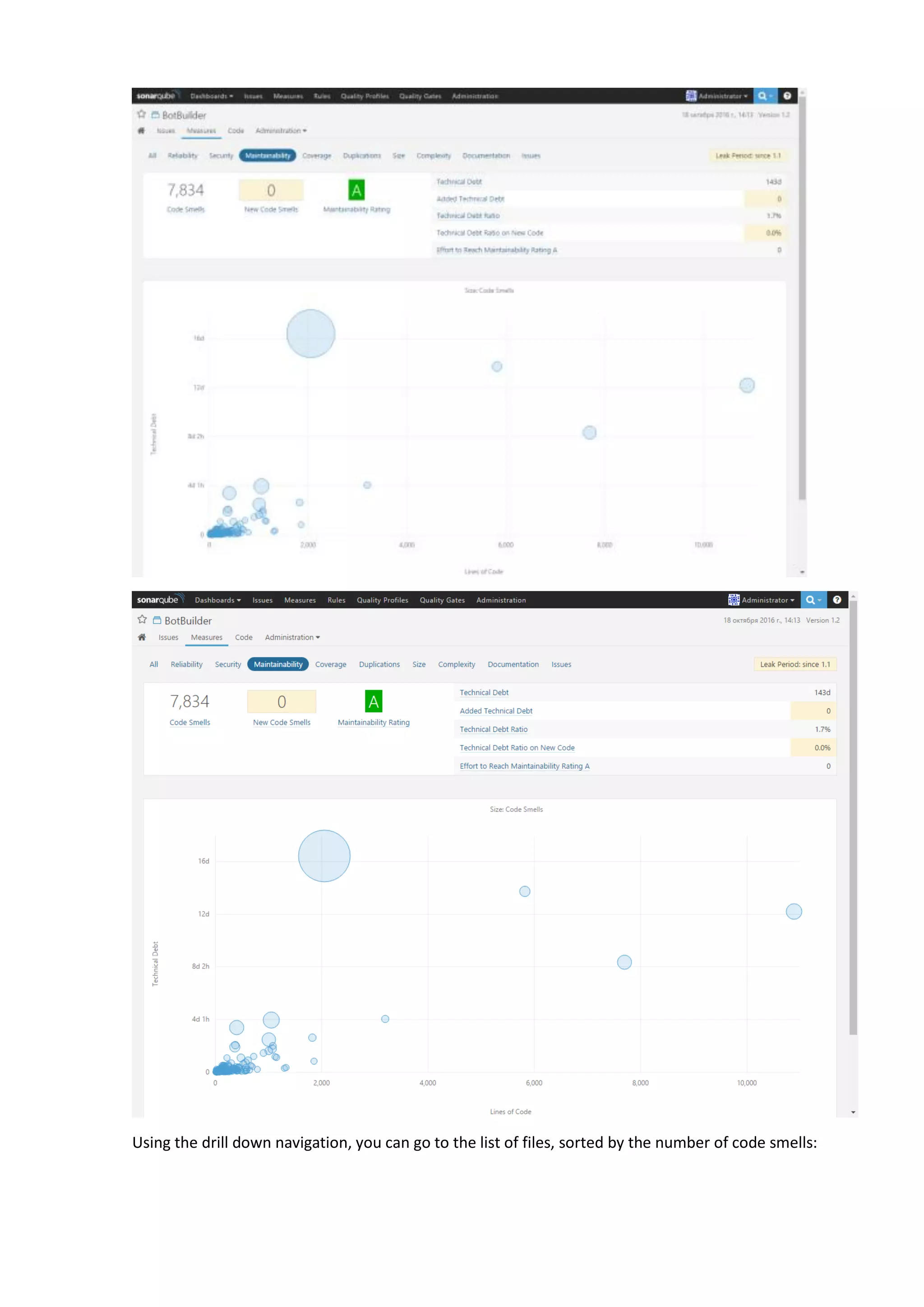
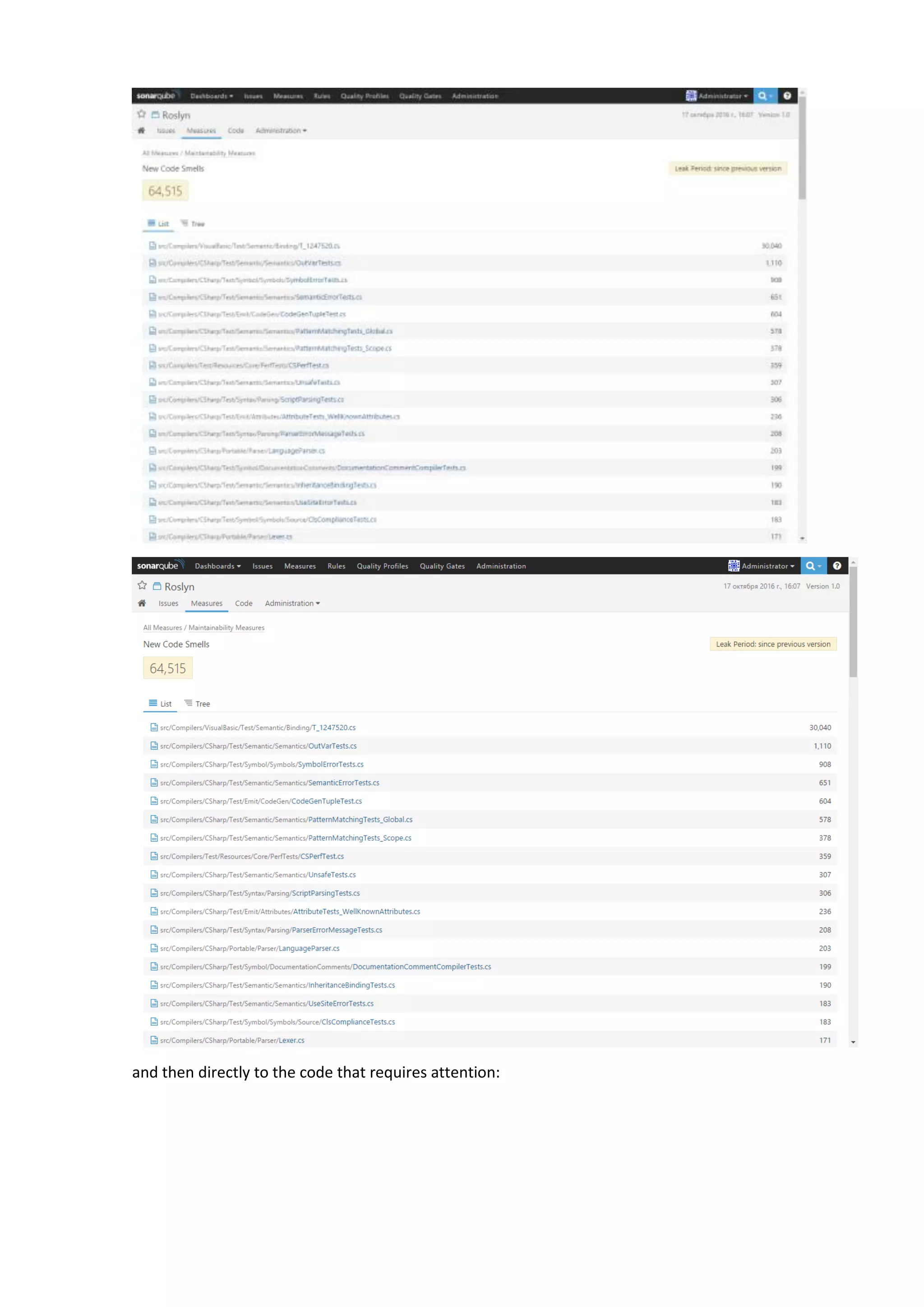
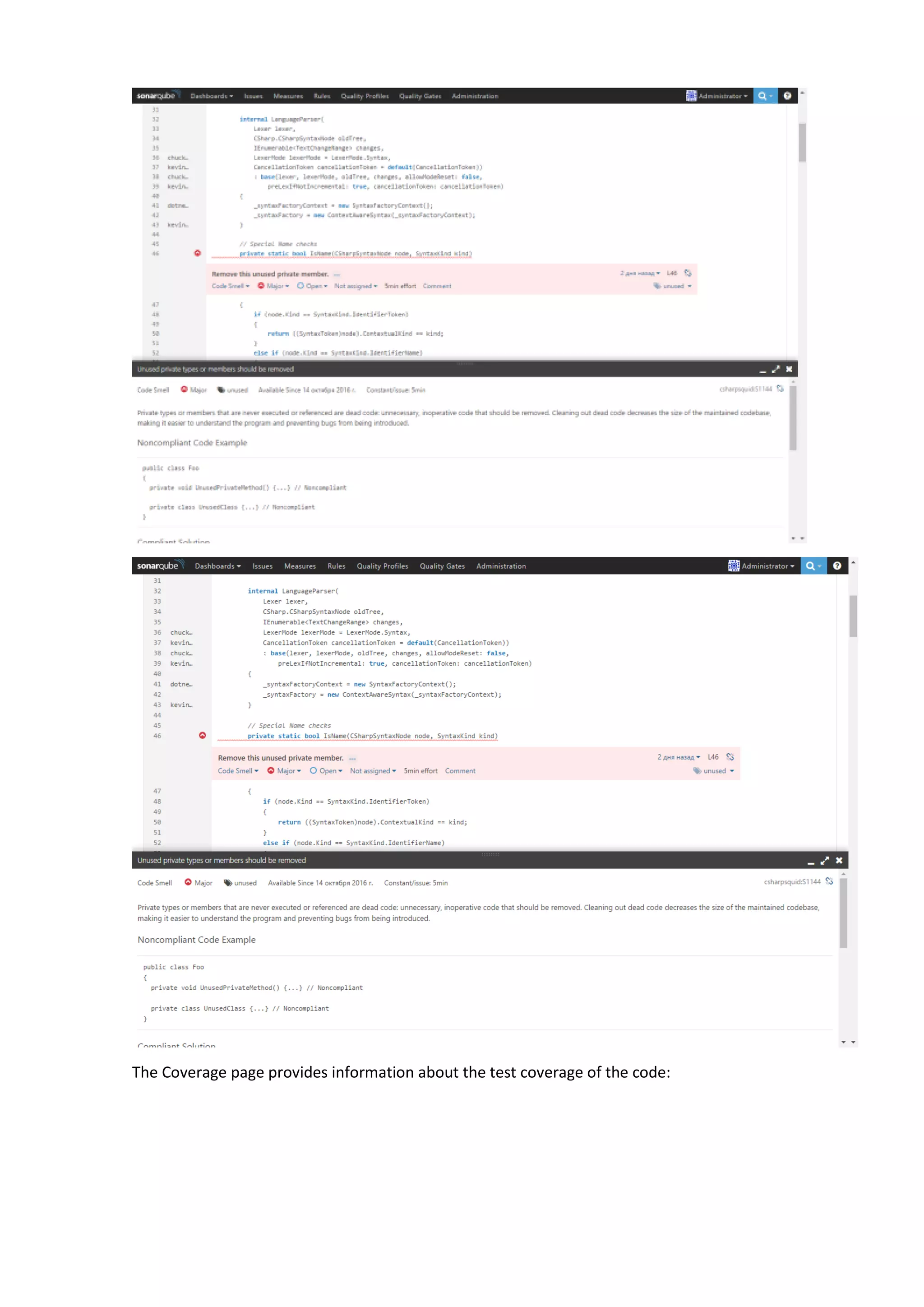
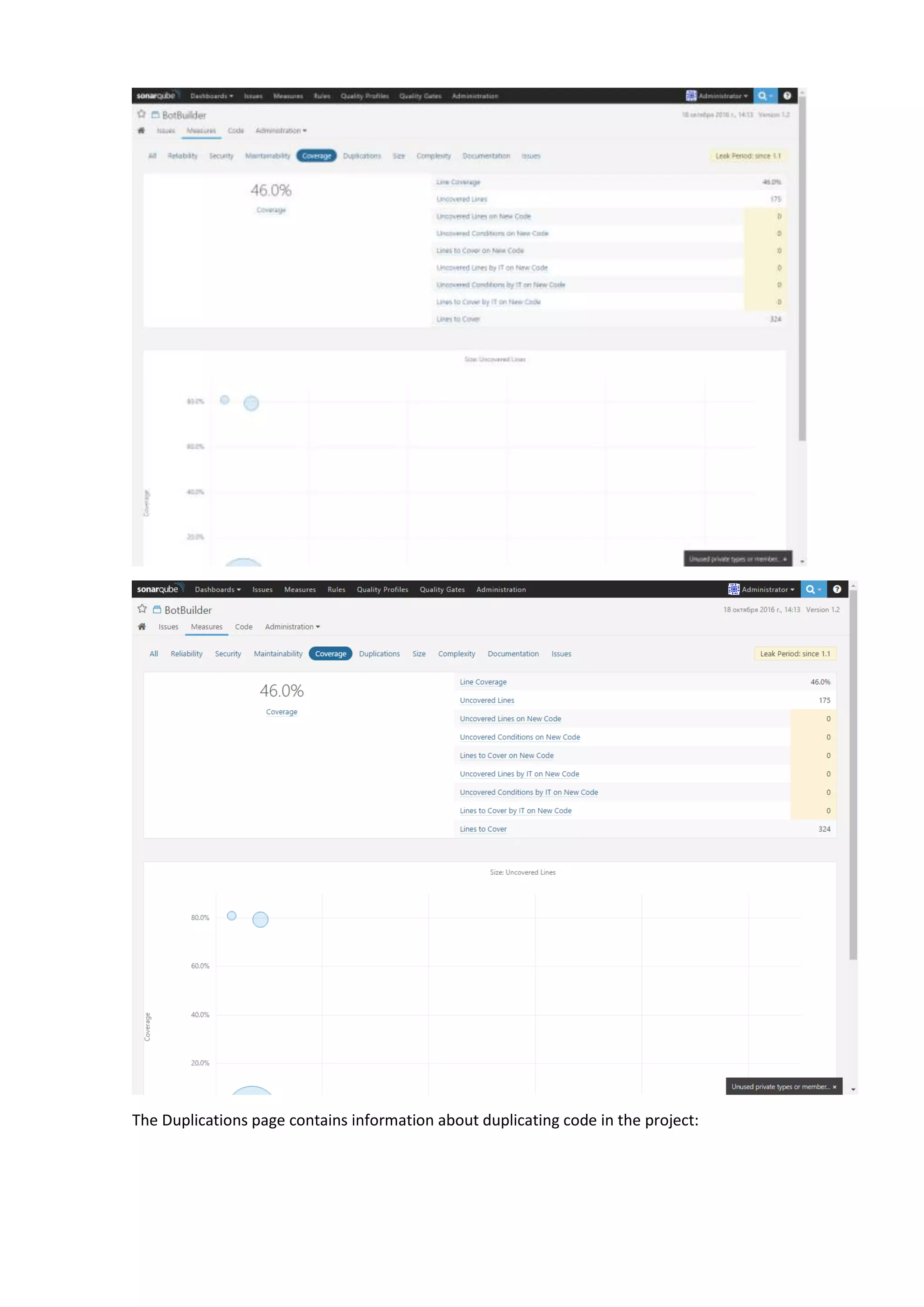
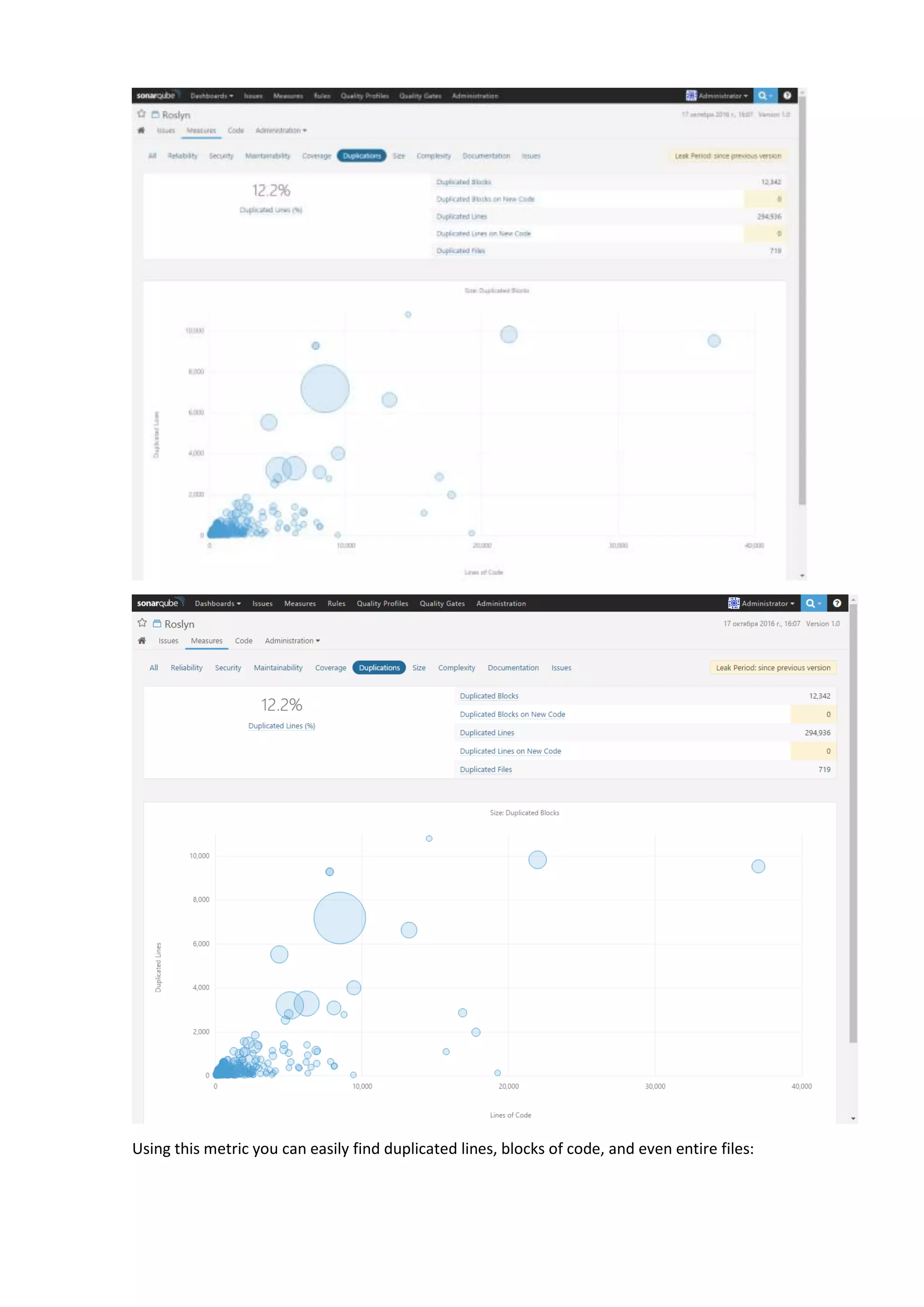
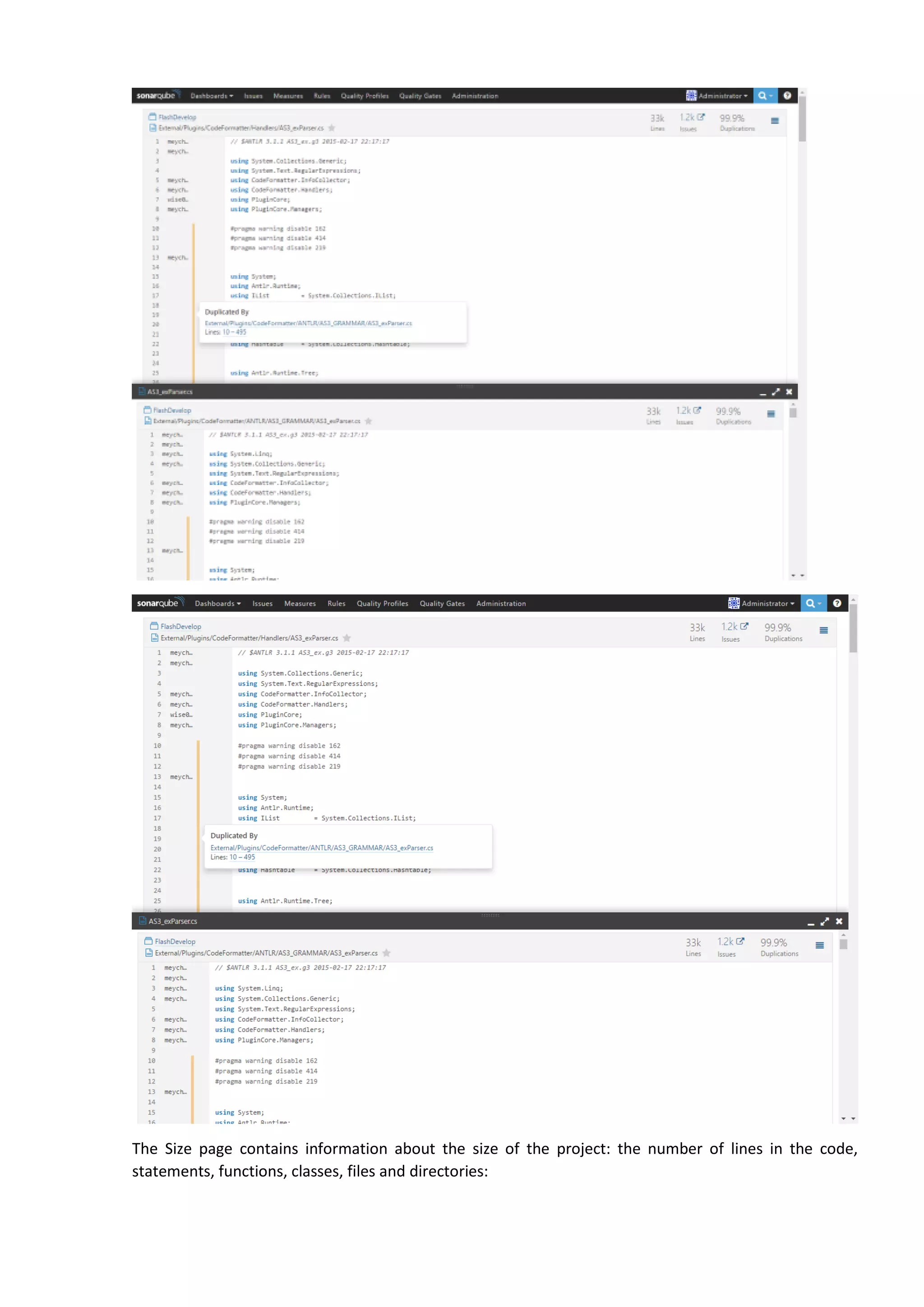
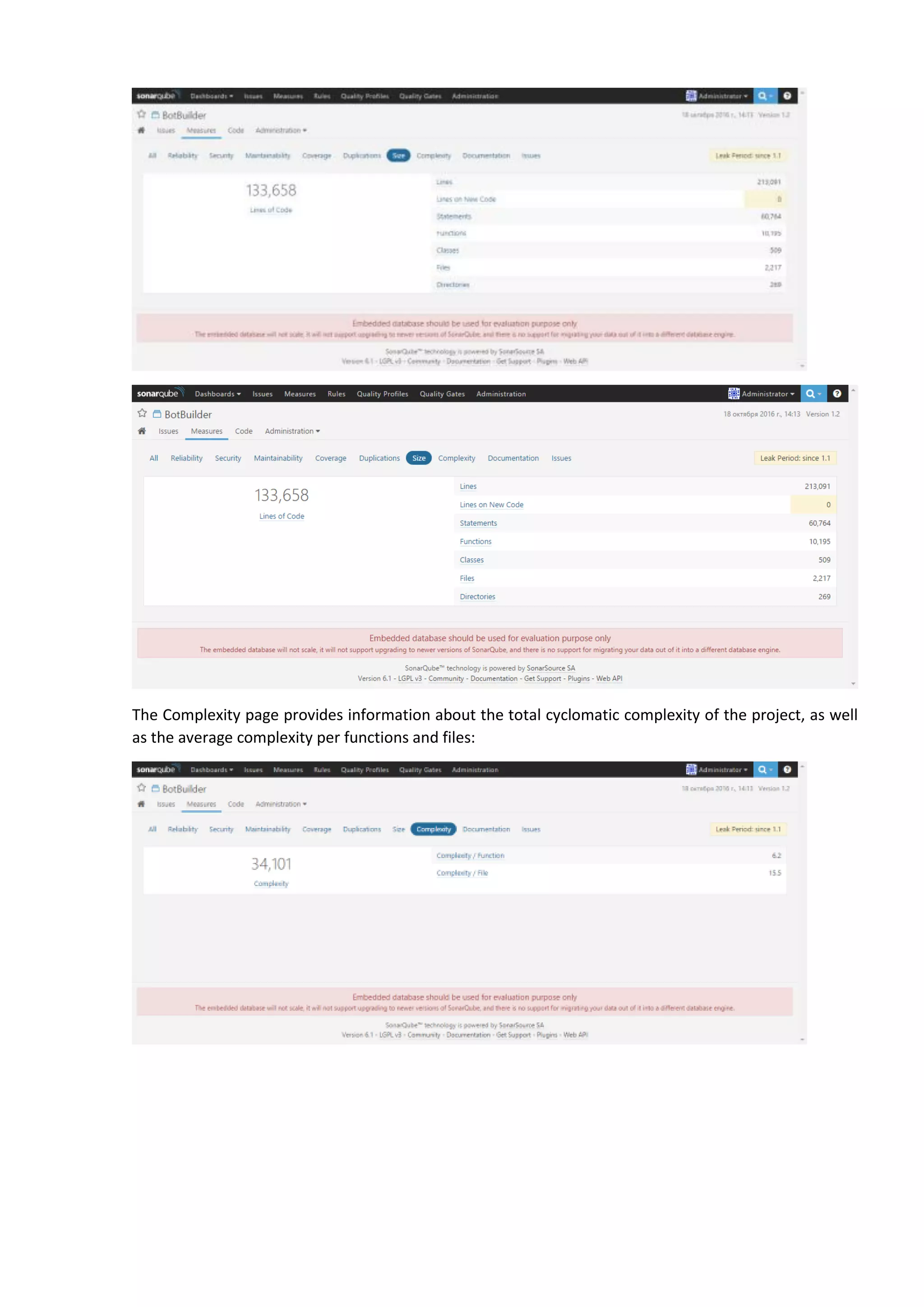
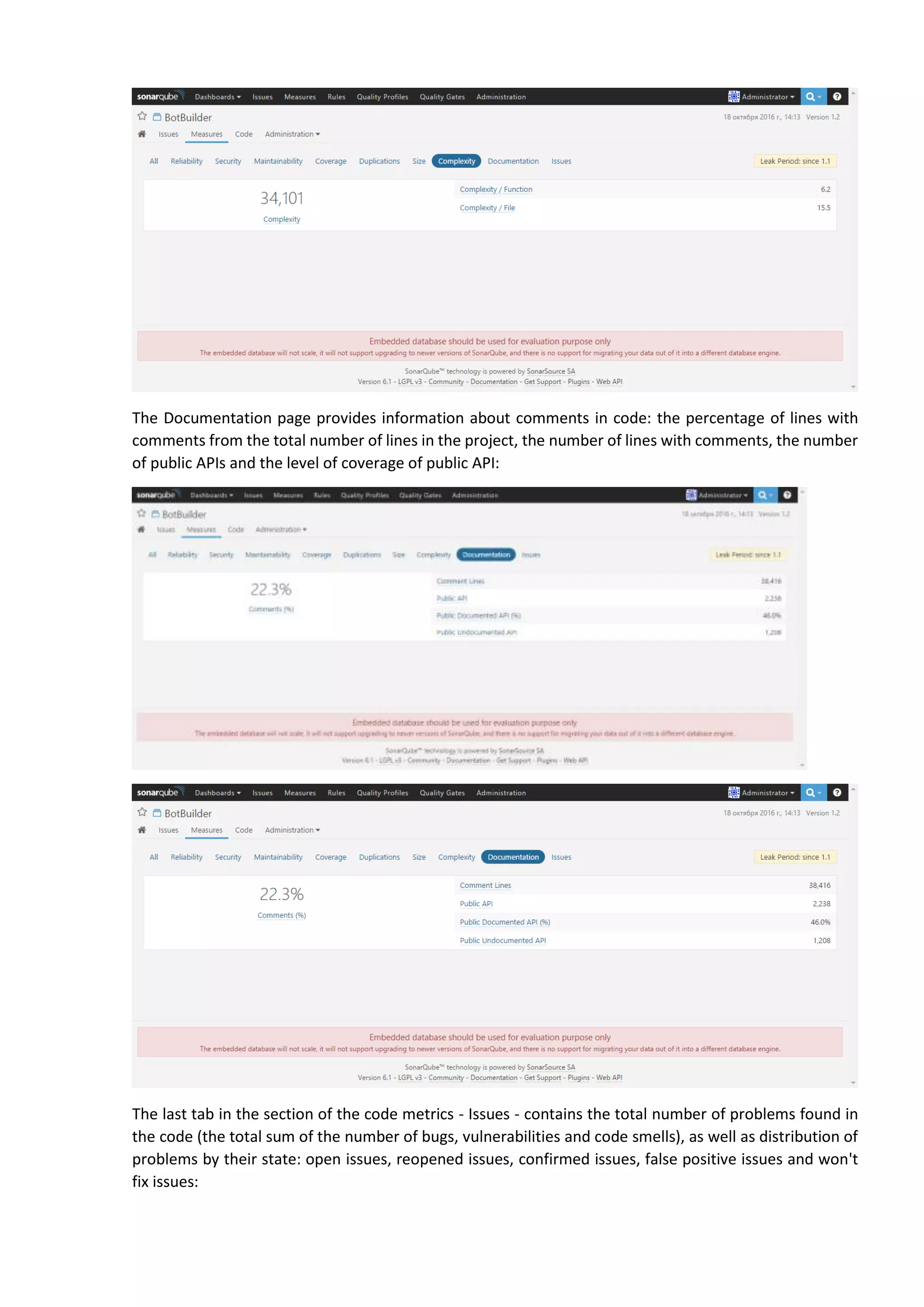
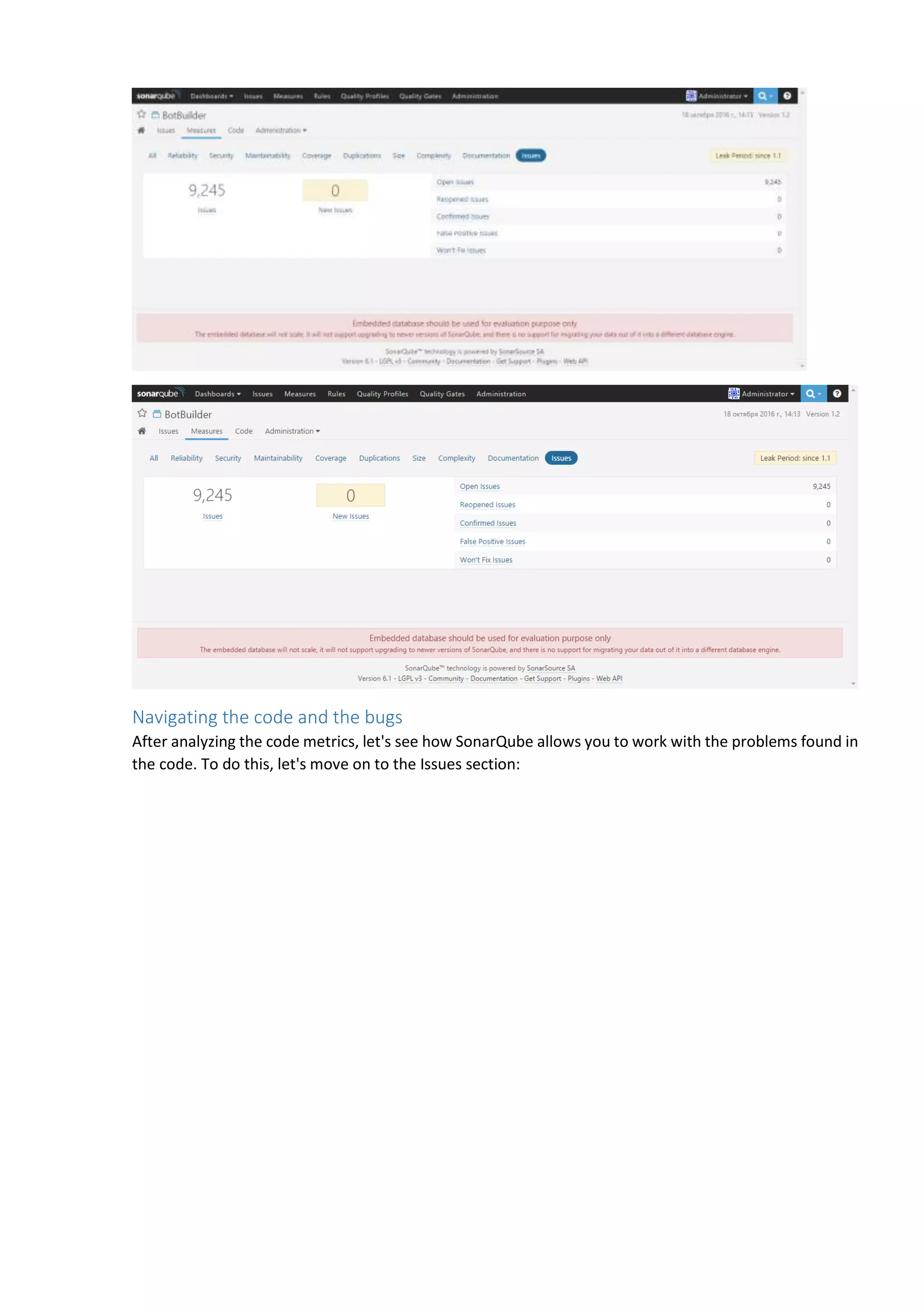
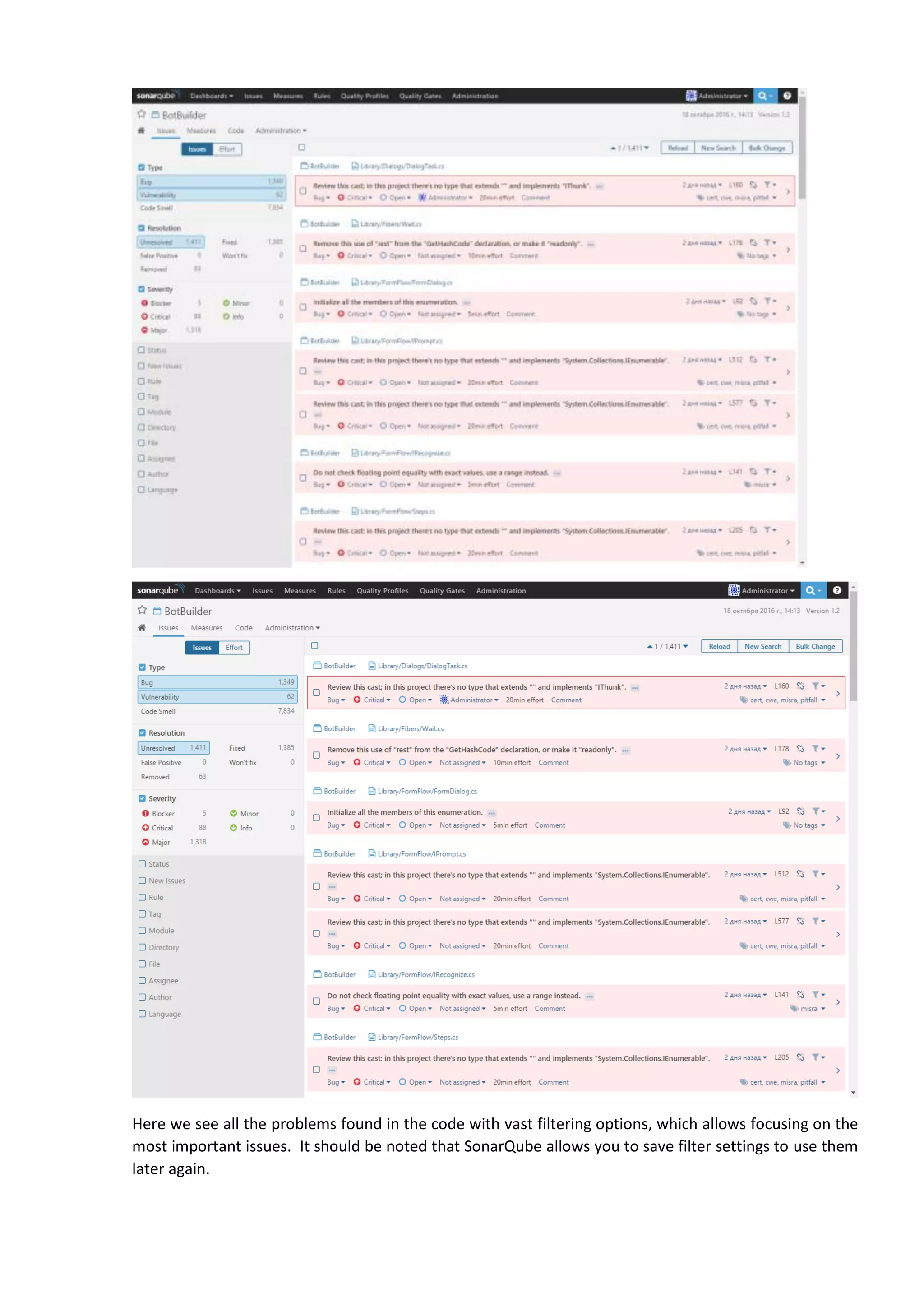
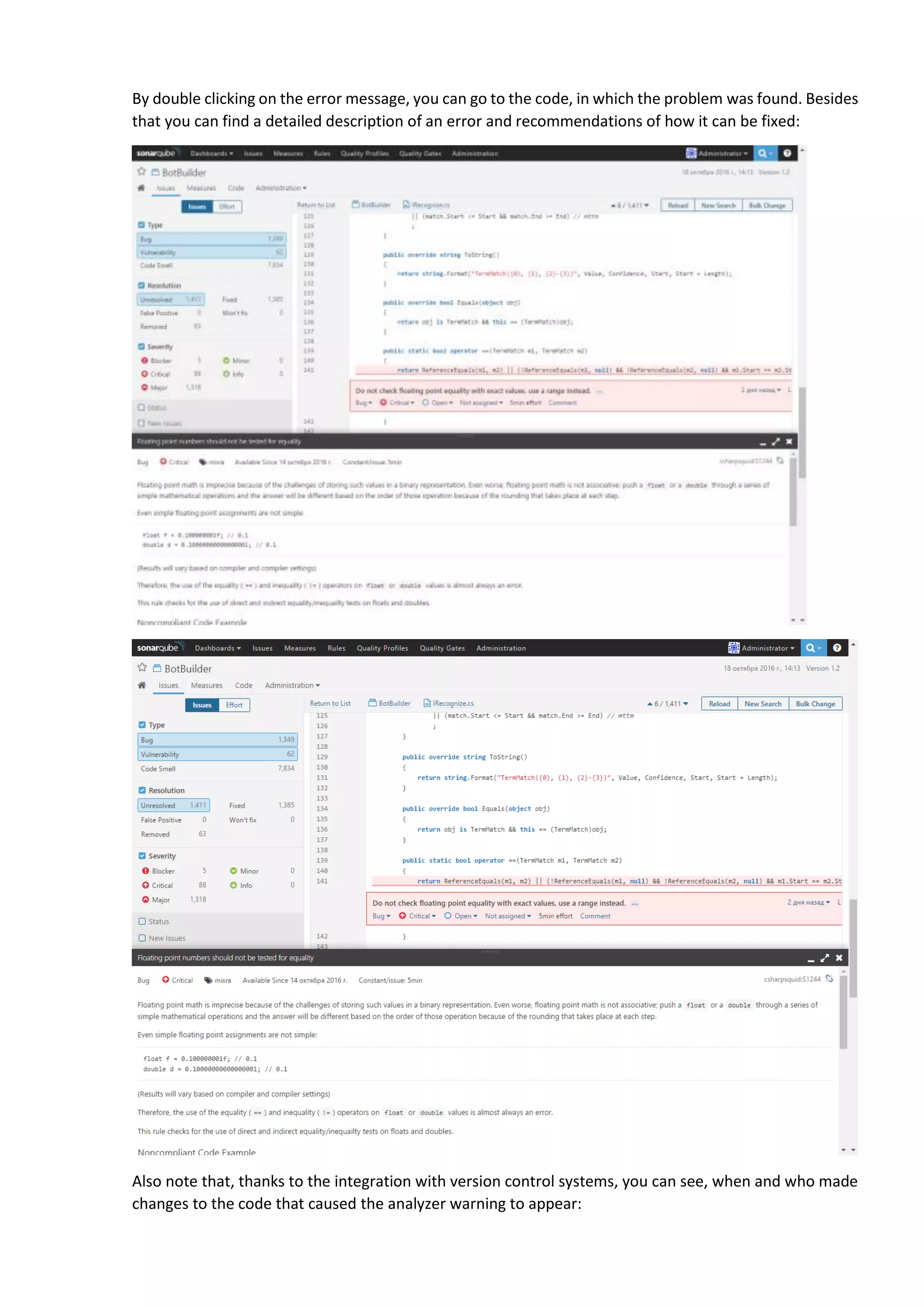
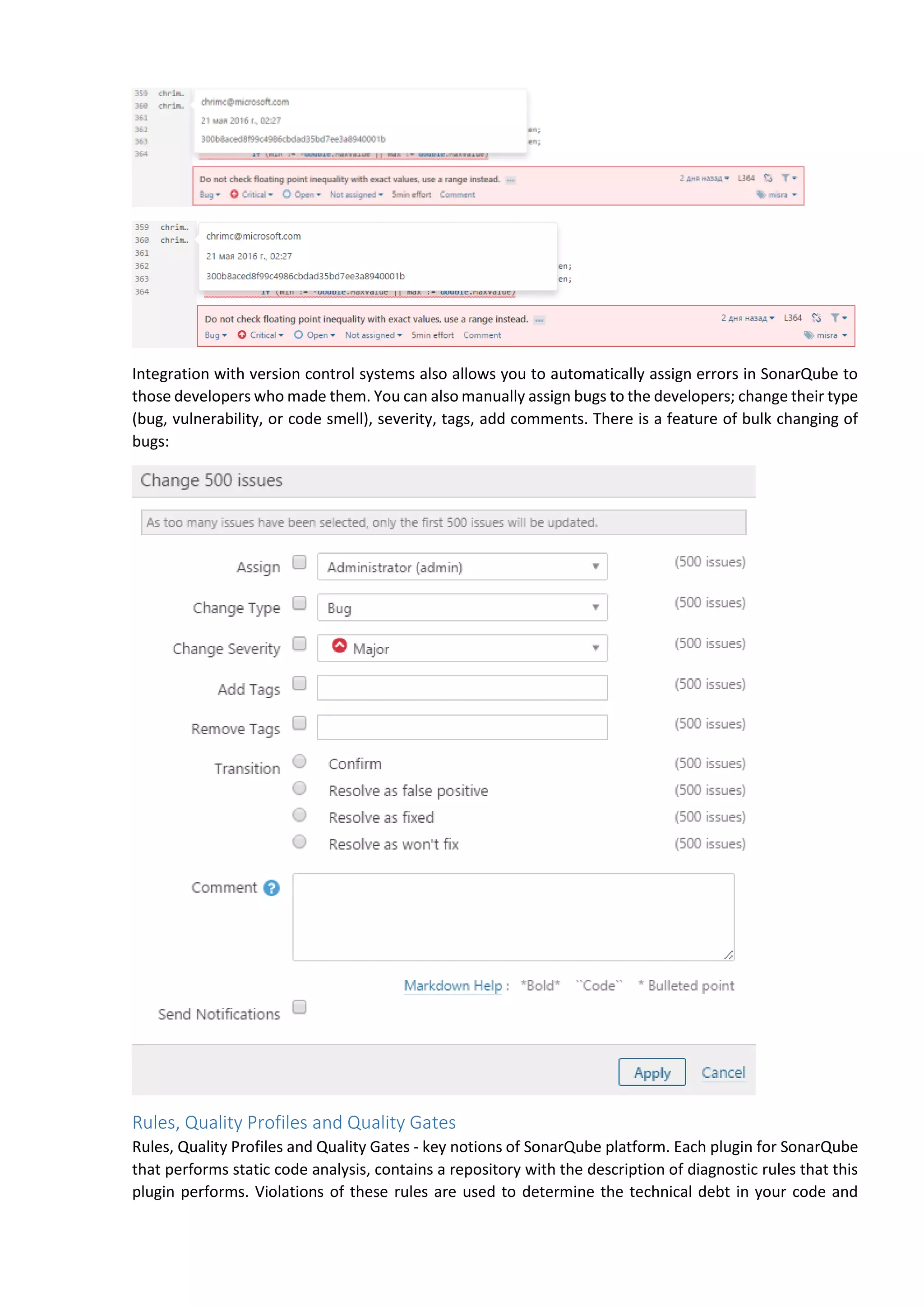
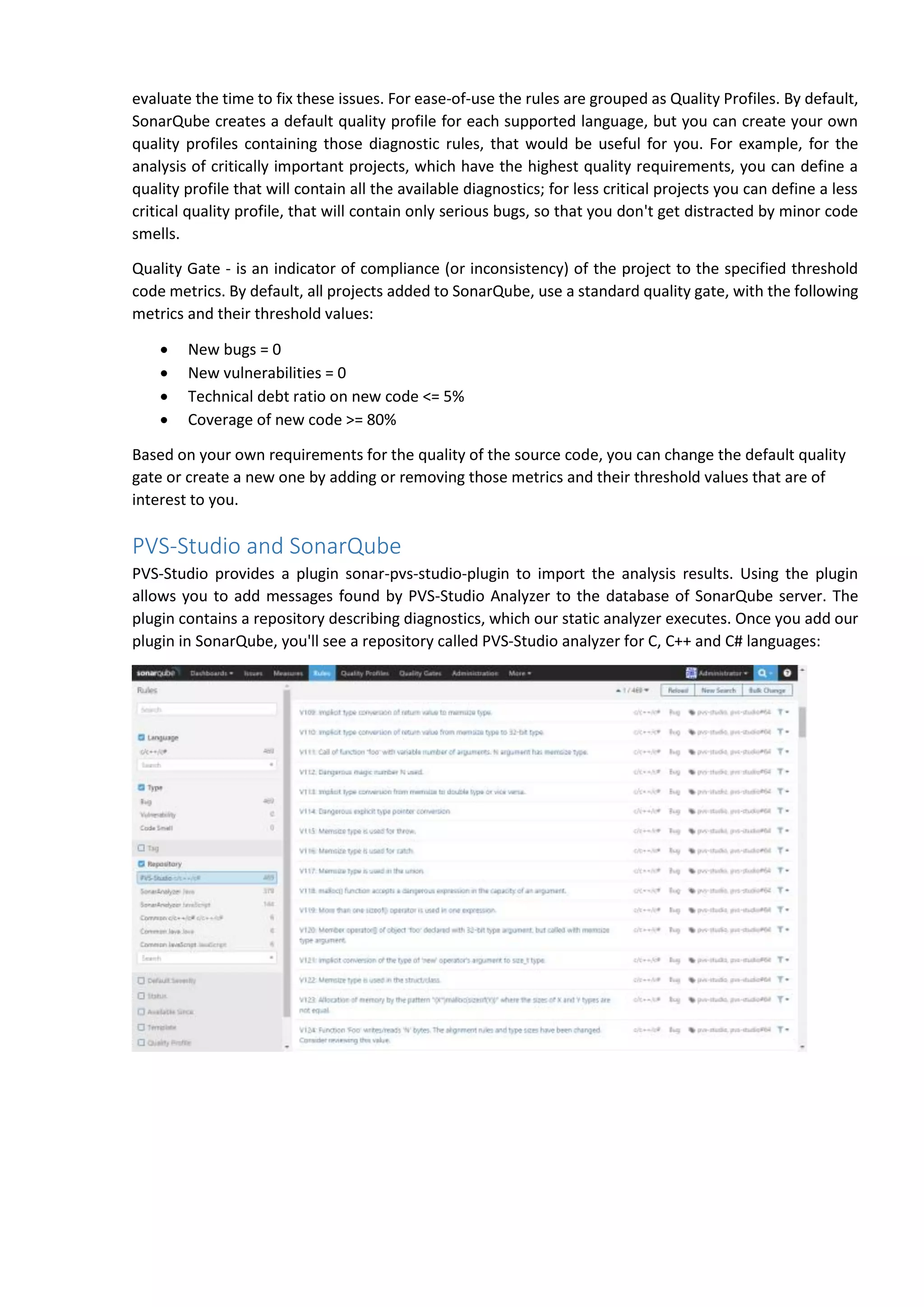
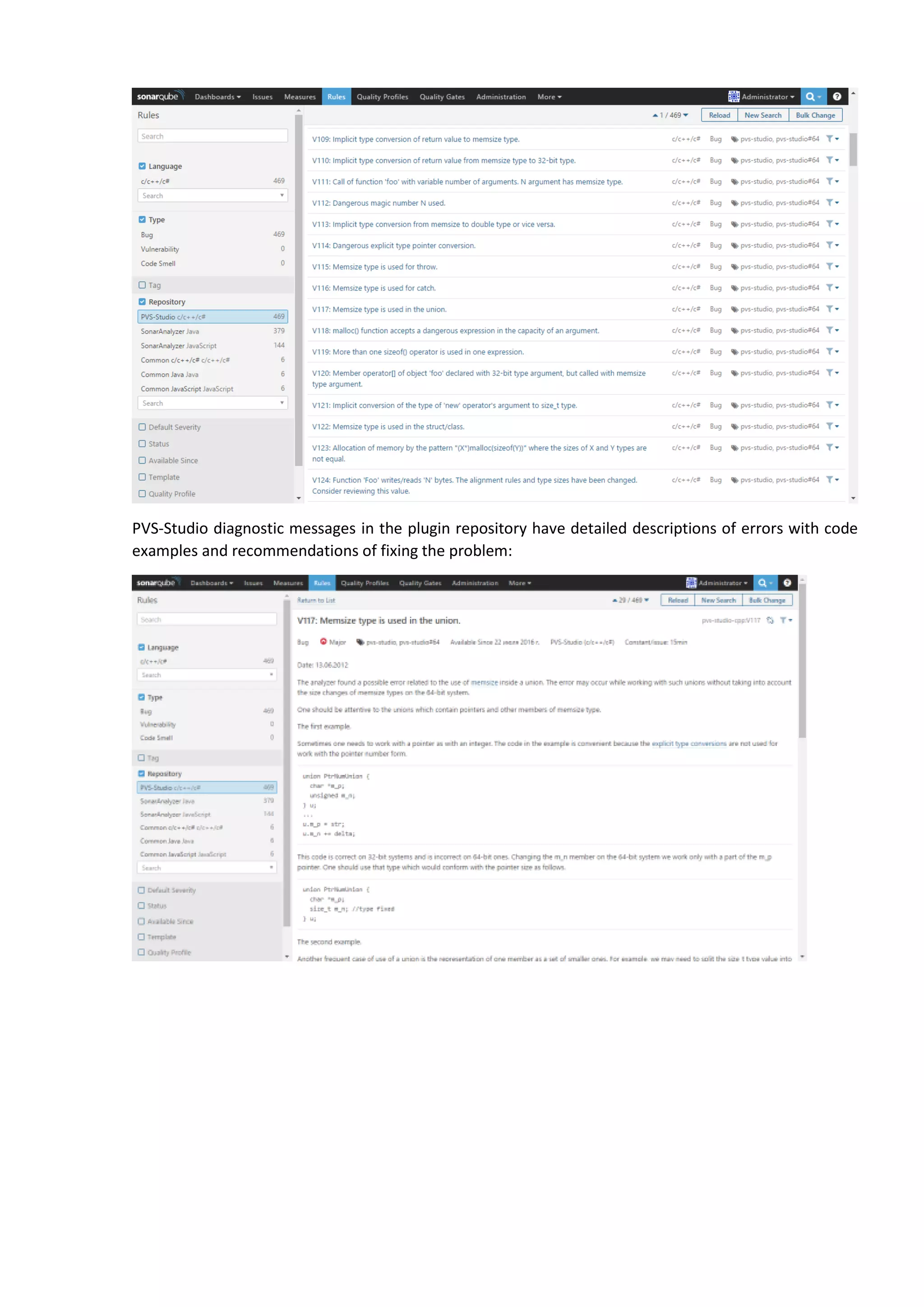
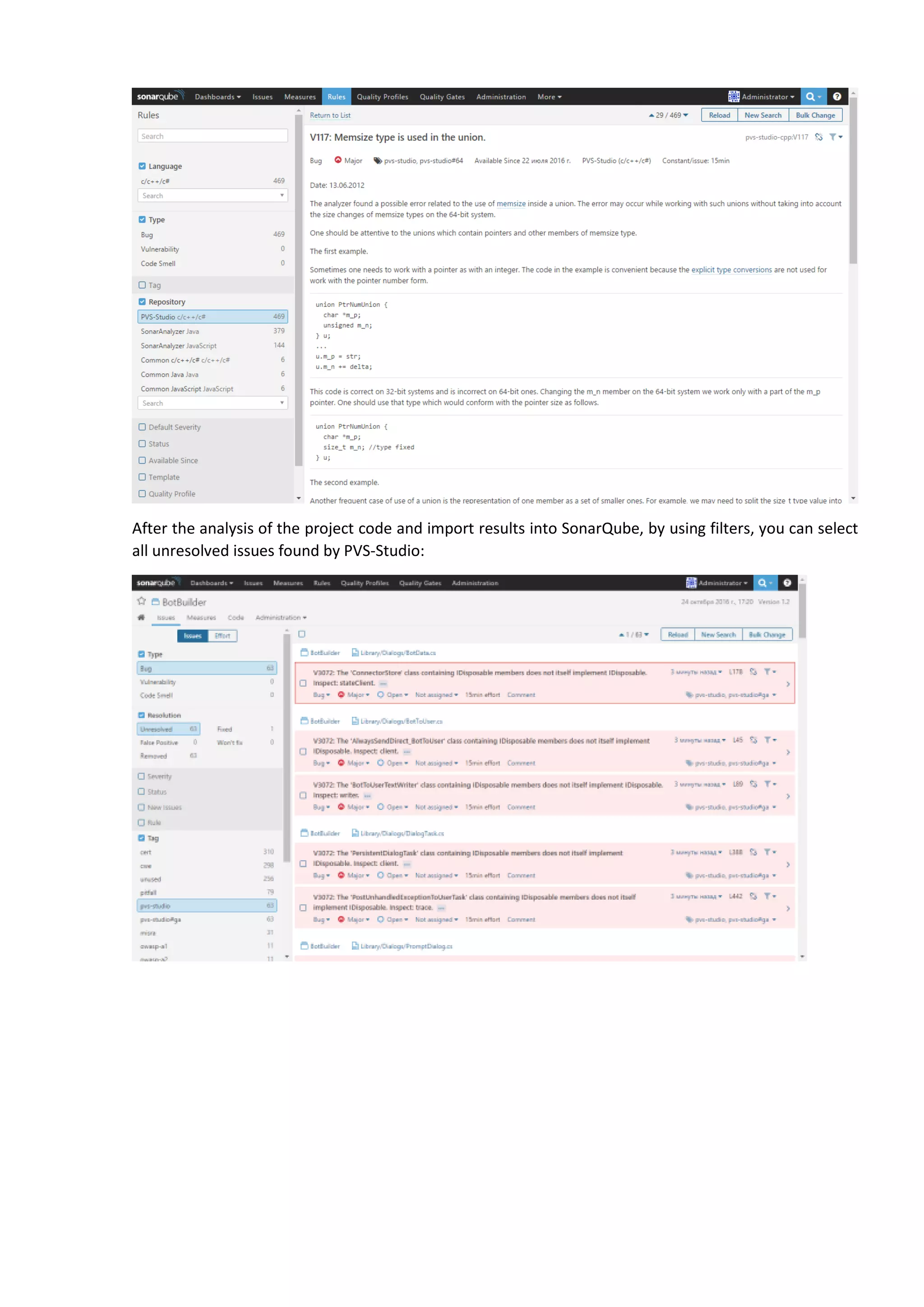
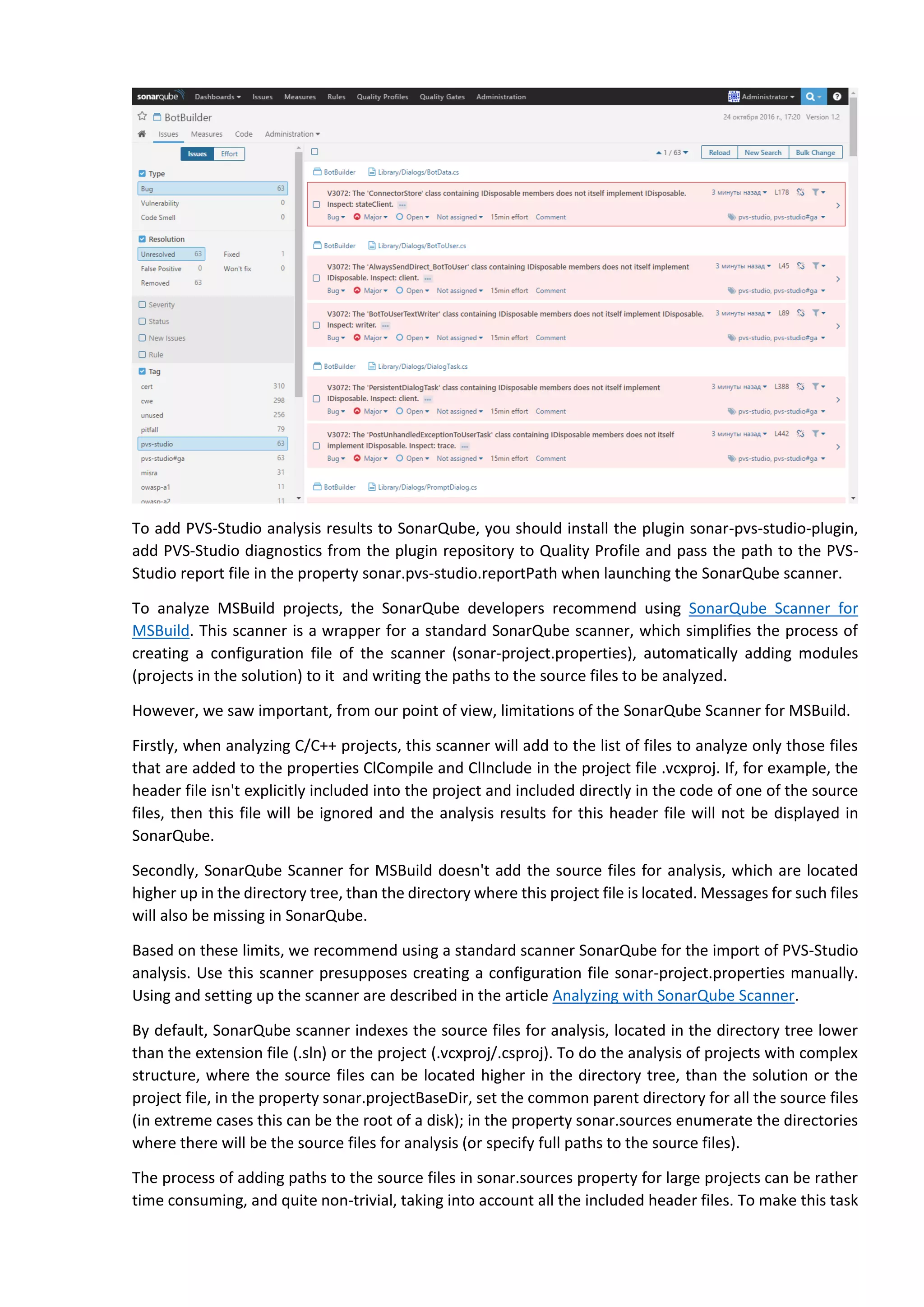
The document discusses the SonarQube platform for continuous analysis and measurement of code quality. Some key features of SonarQube include supporting multiple programming languages, providing metrics on code quality issues like bugs, duplications, test coverage, and technical debt. It integrates with build systems and IDEs and allows customizing dashboards and quality profiles. The author implemented SonarQube for a customer to provide centralized monitoring of metrics for a large, long-term project.