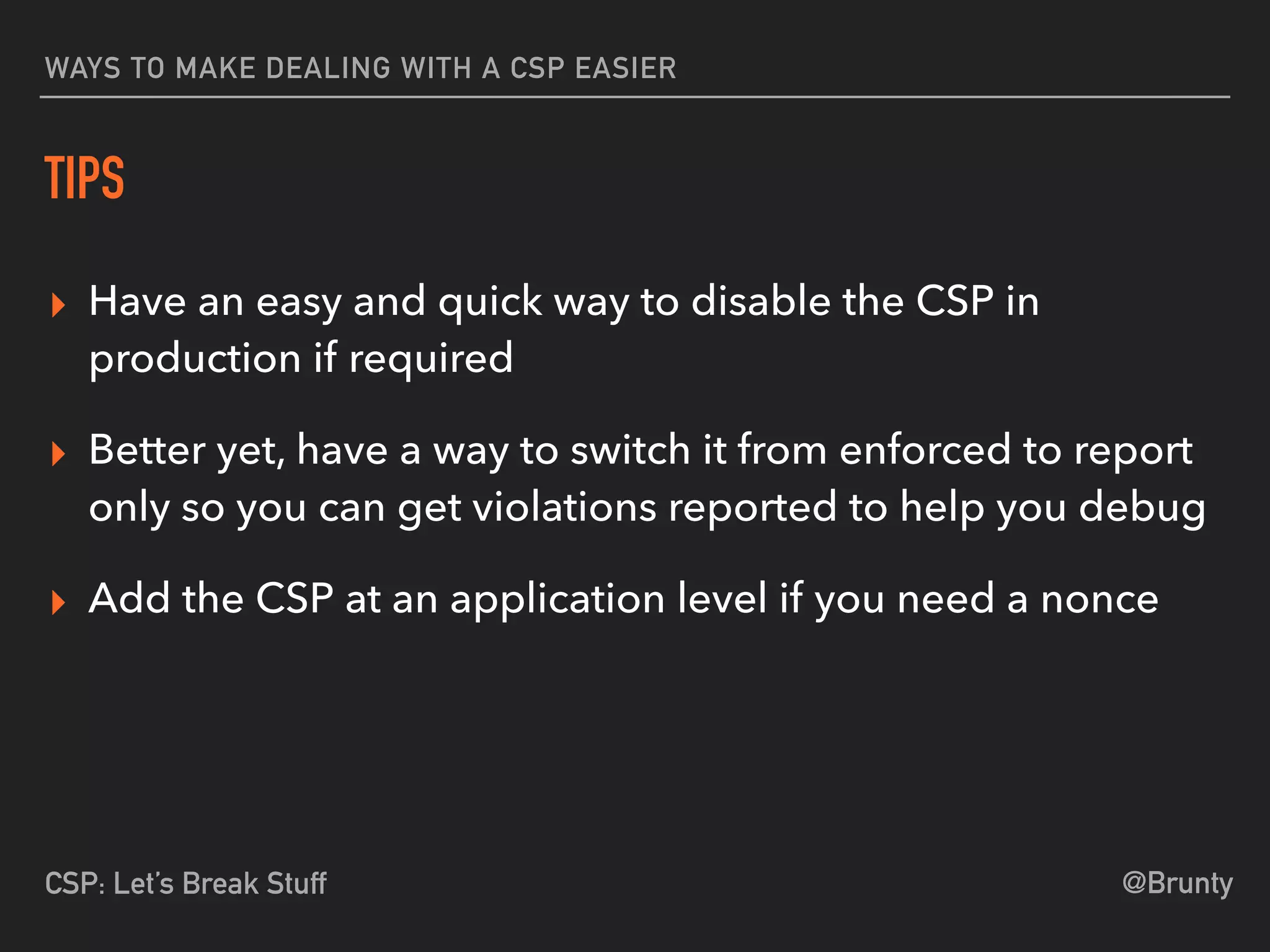
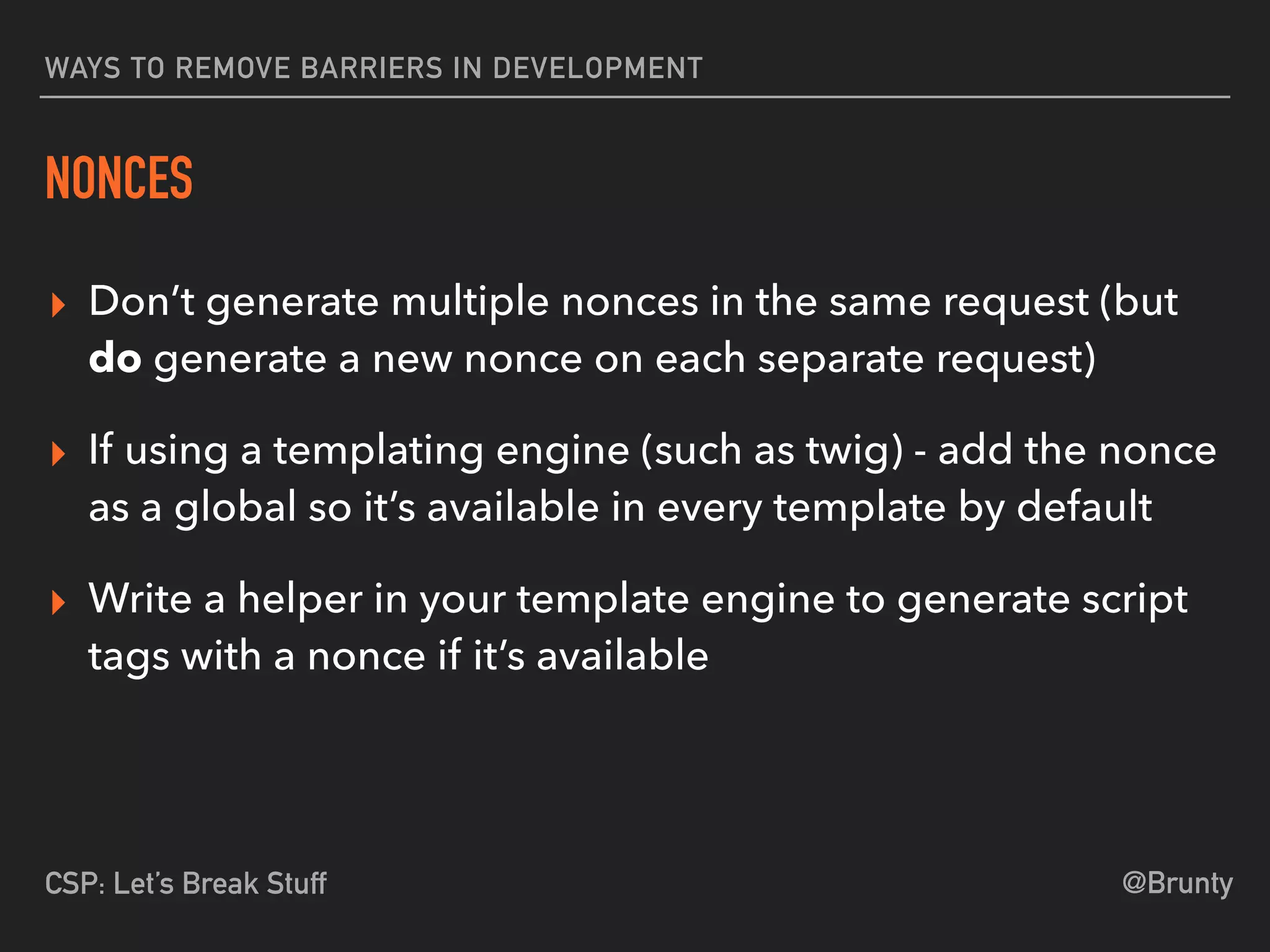
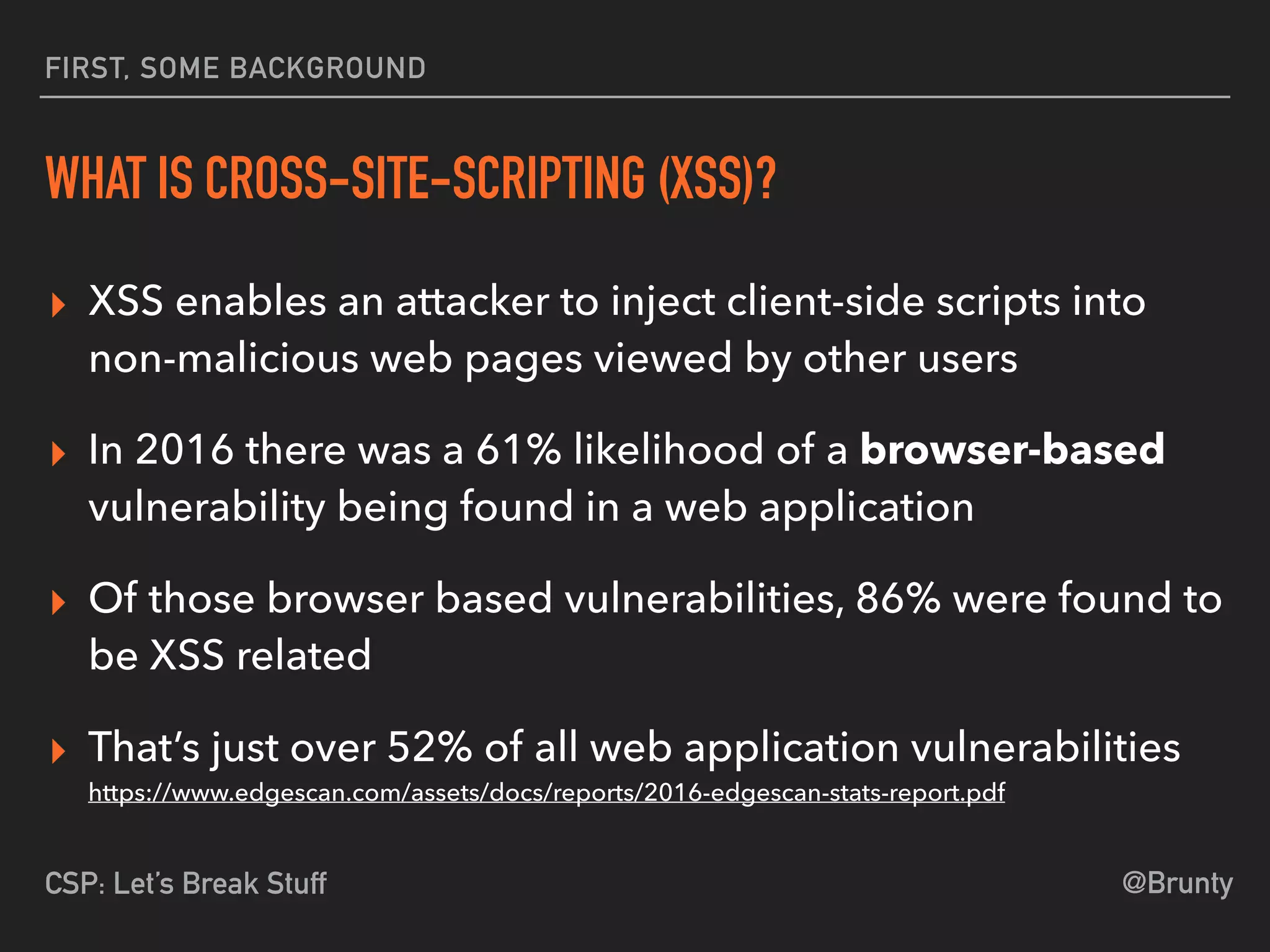
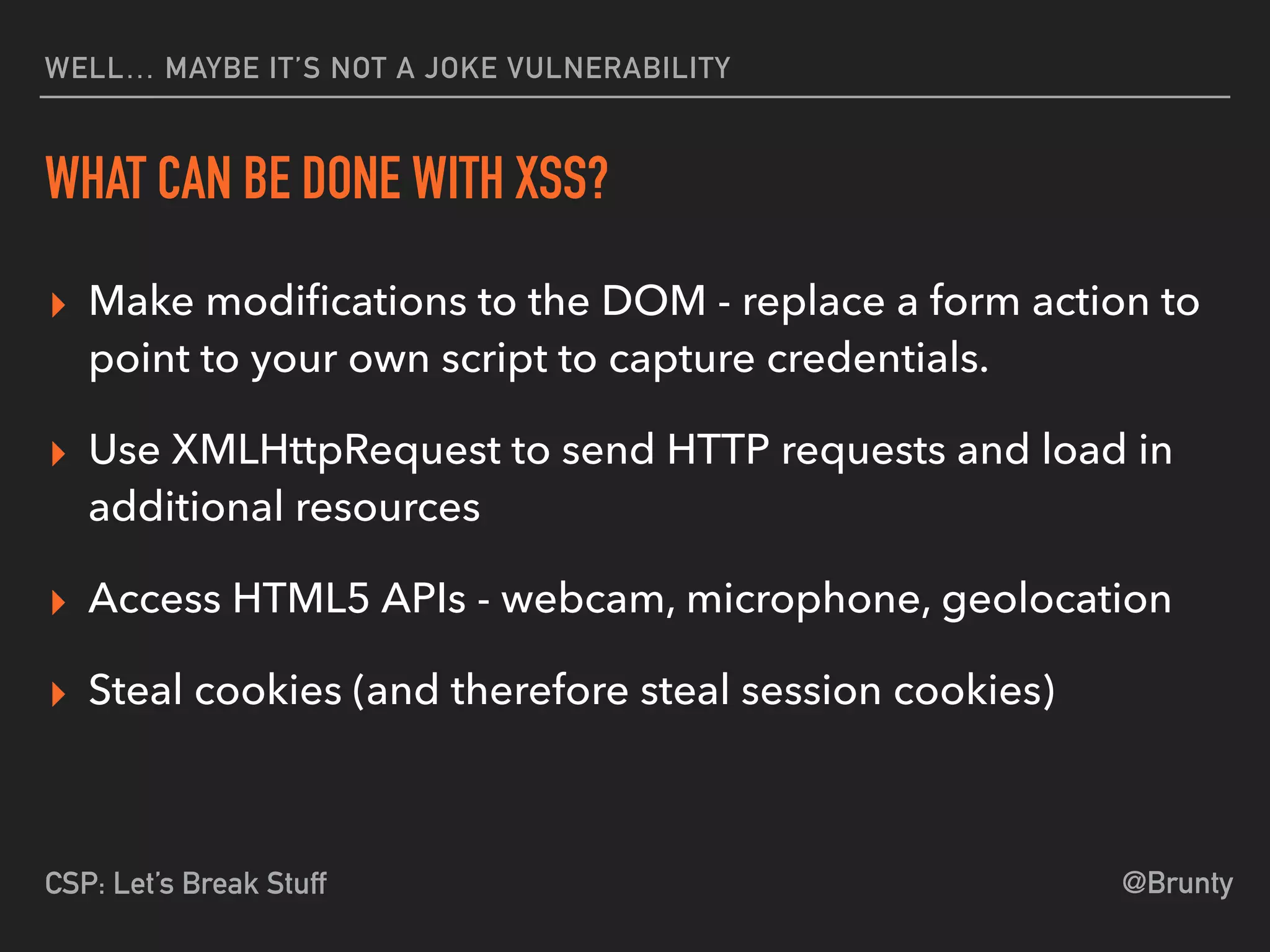
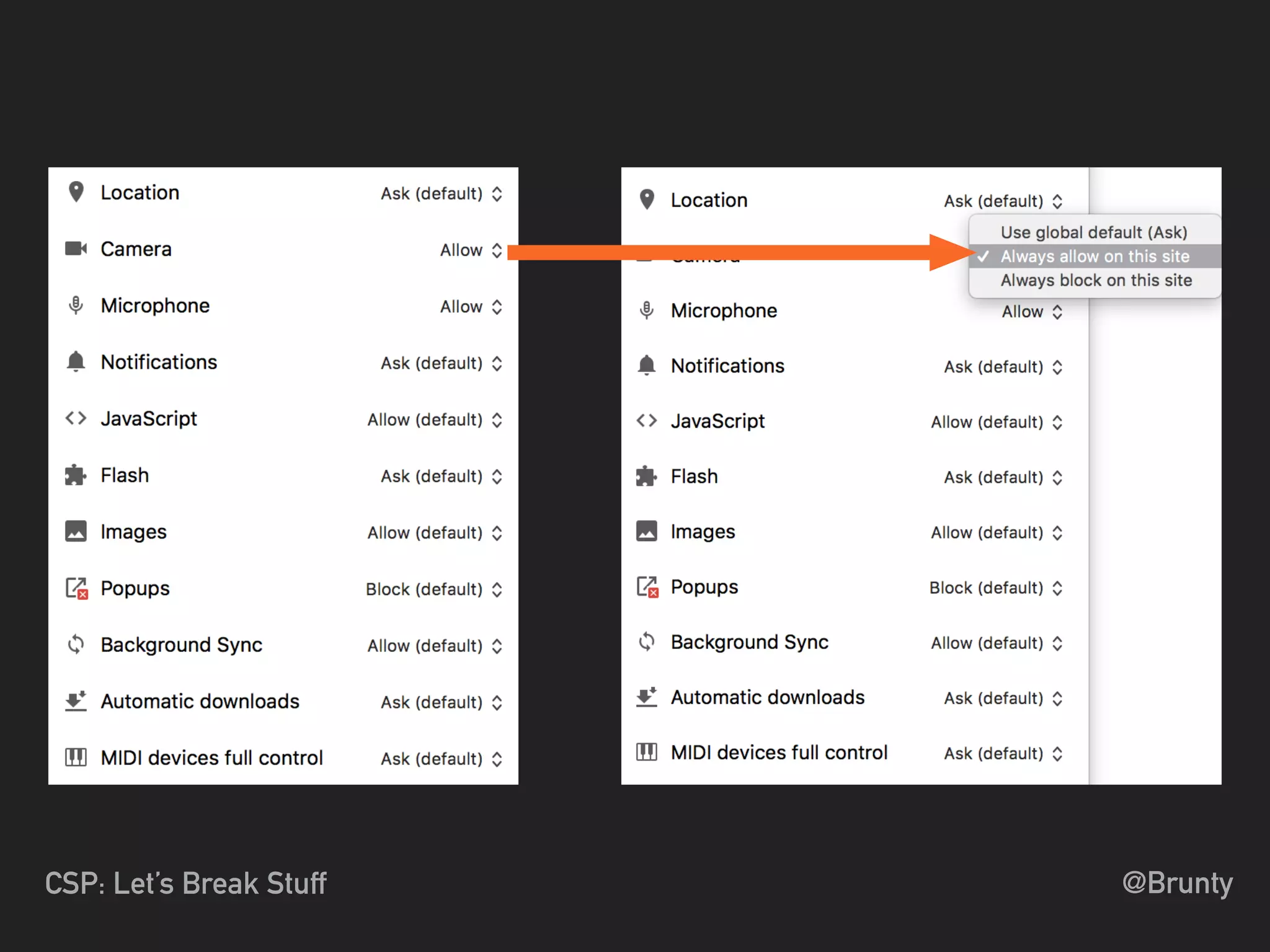
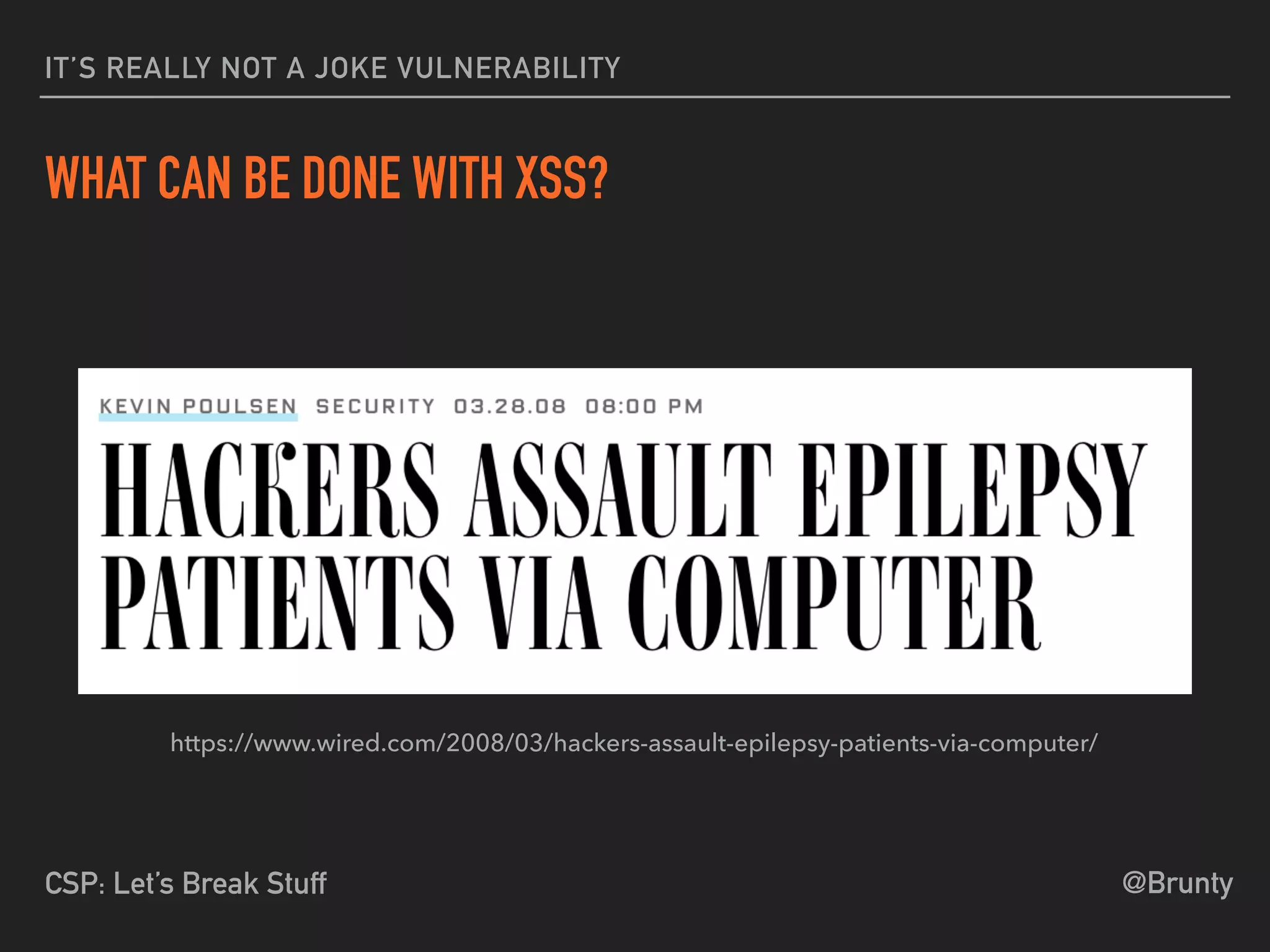
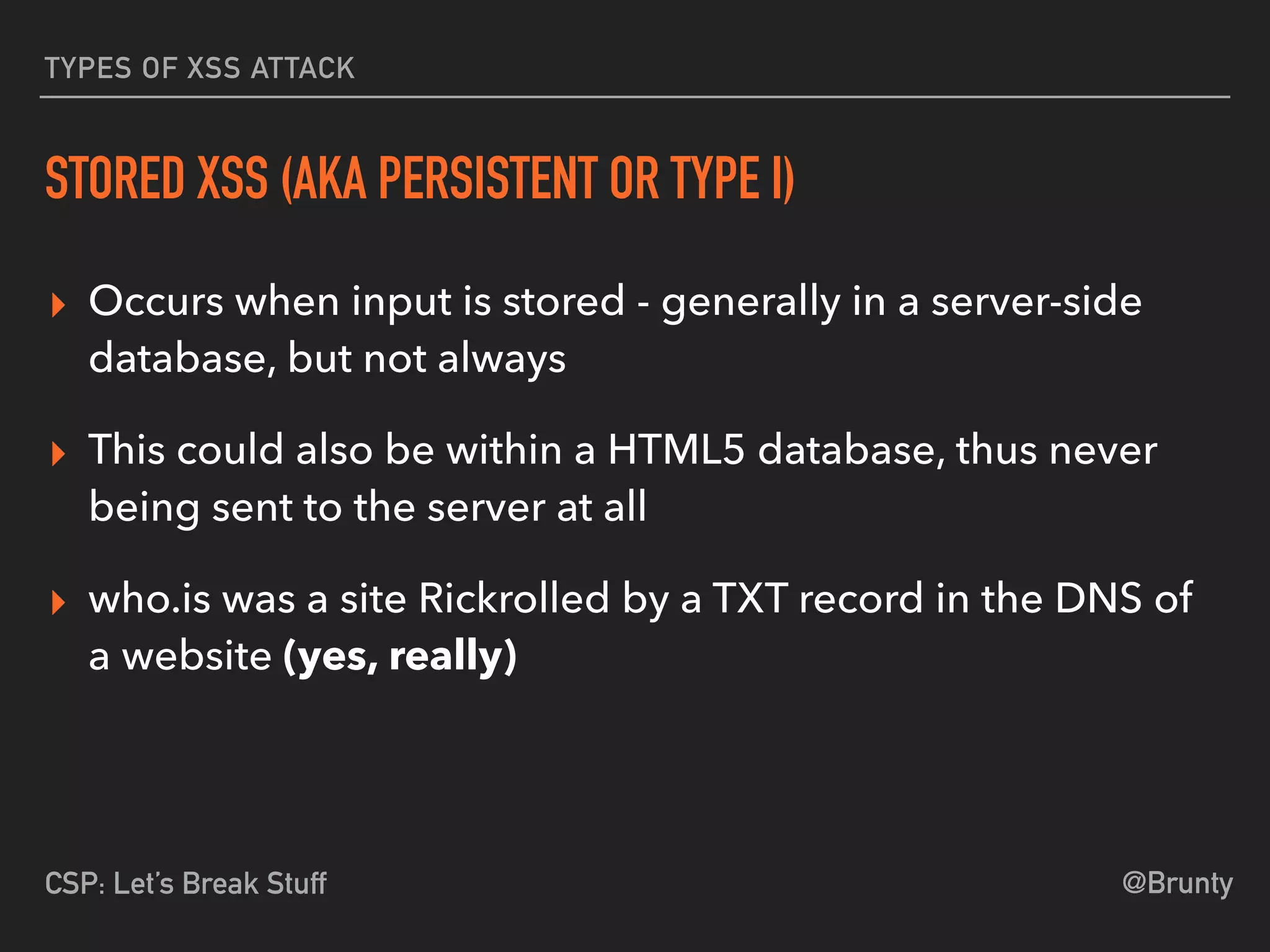
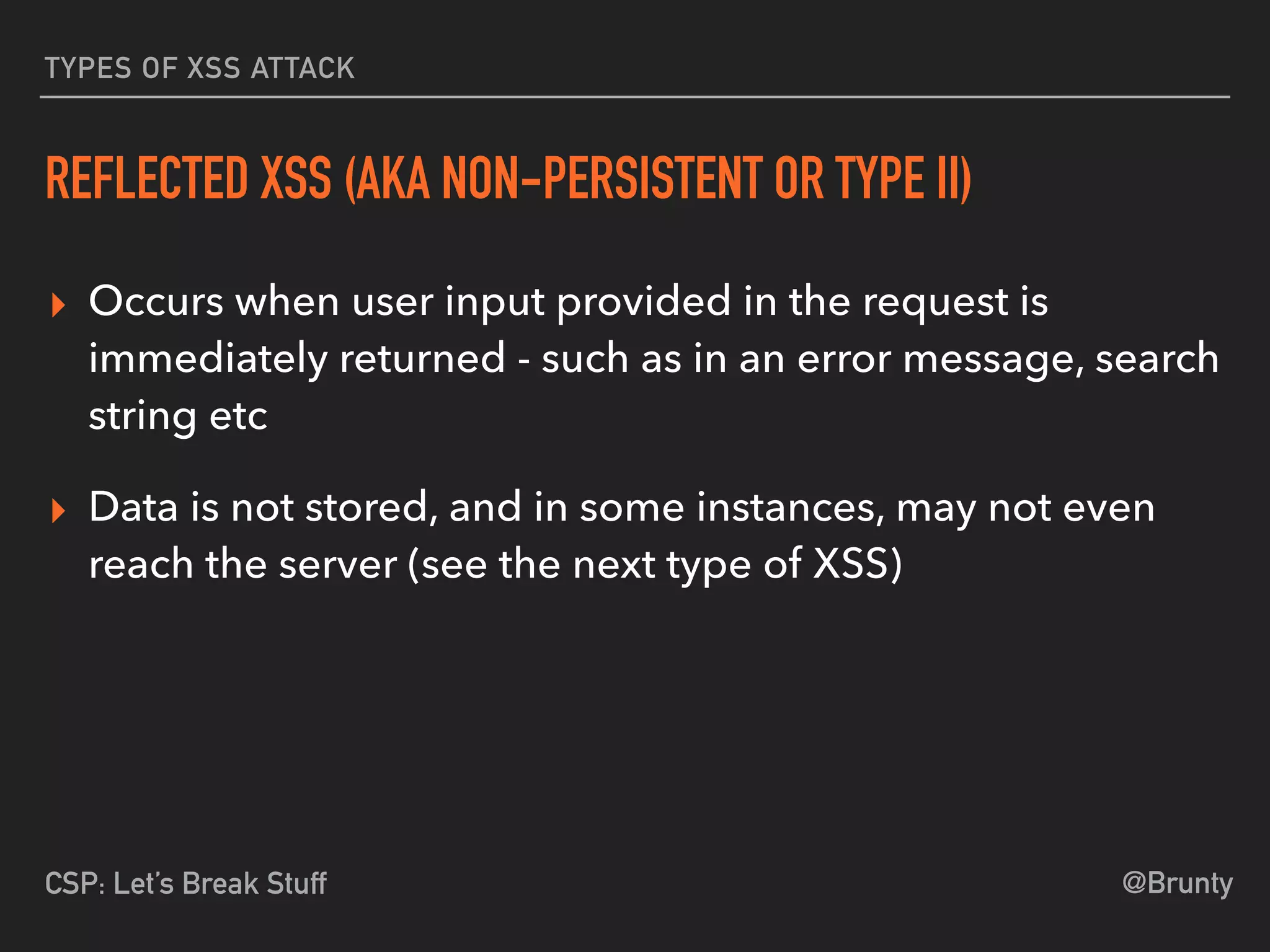
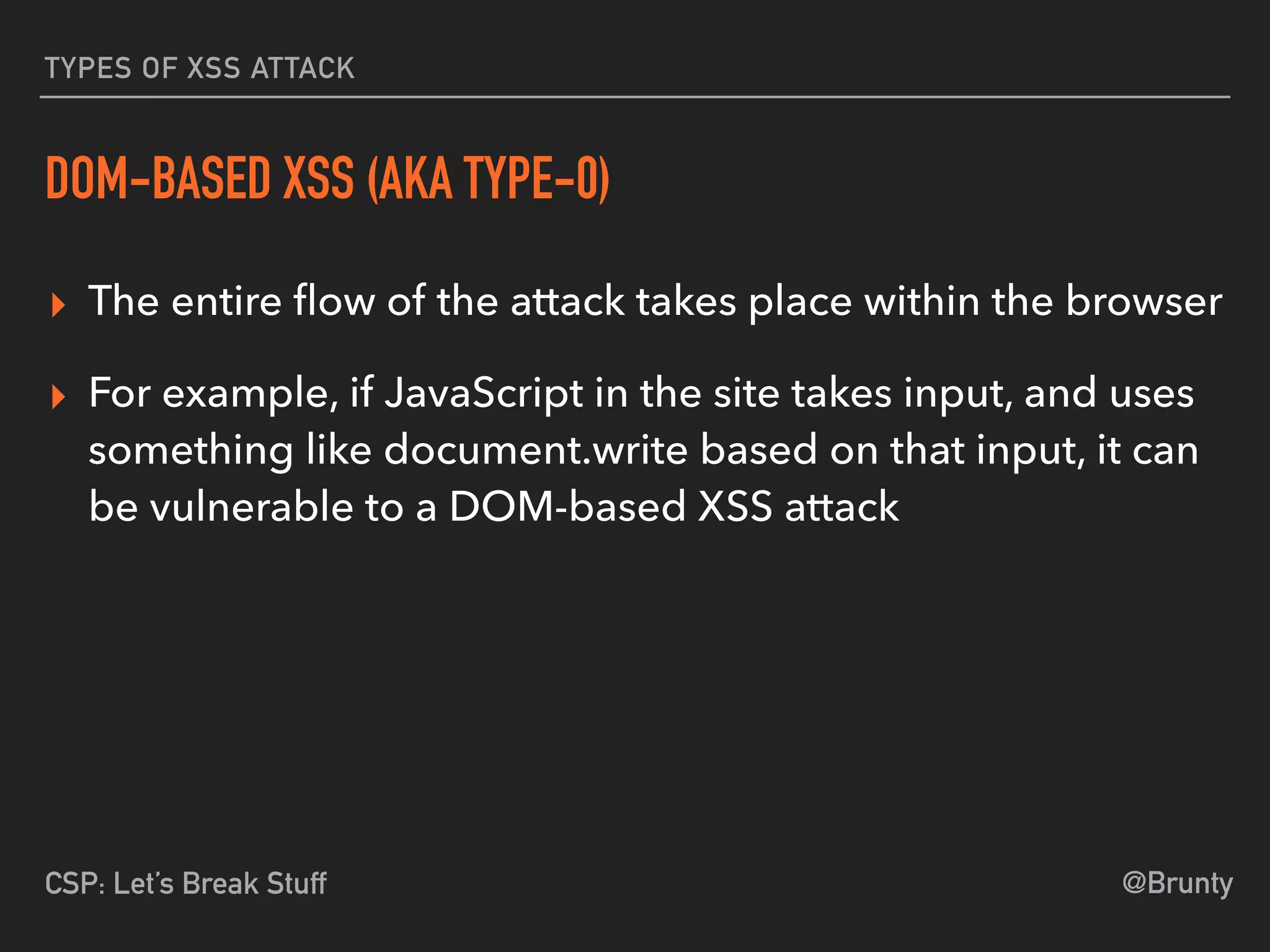
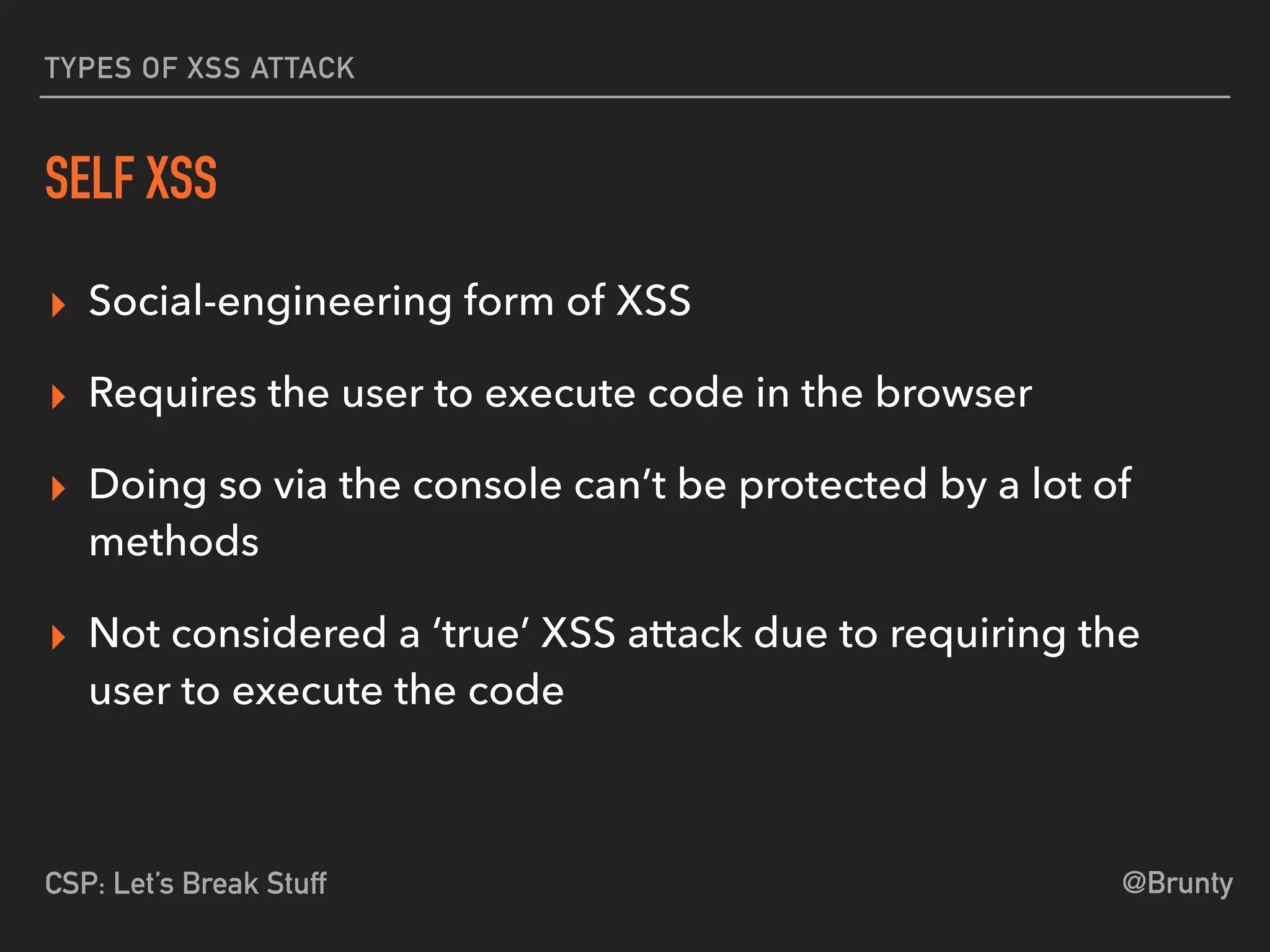
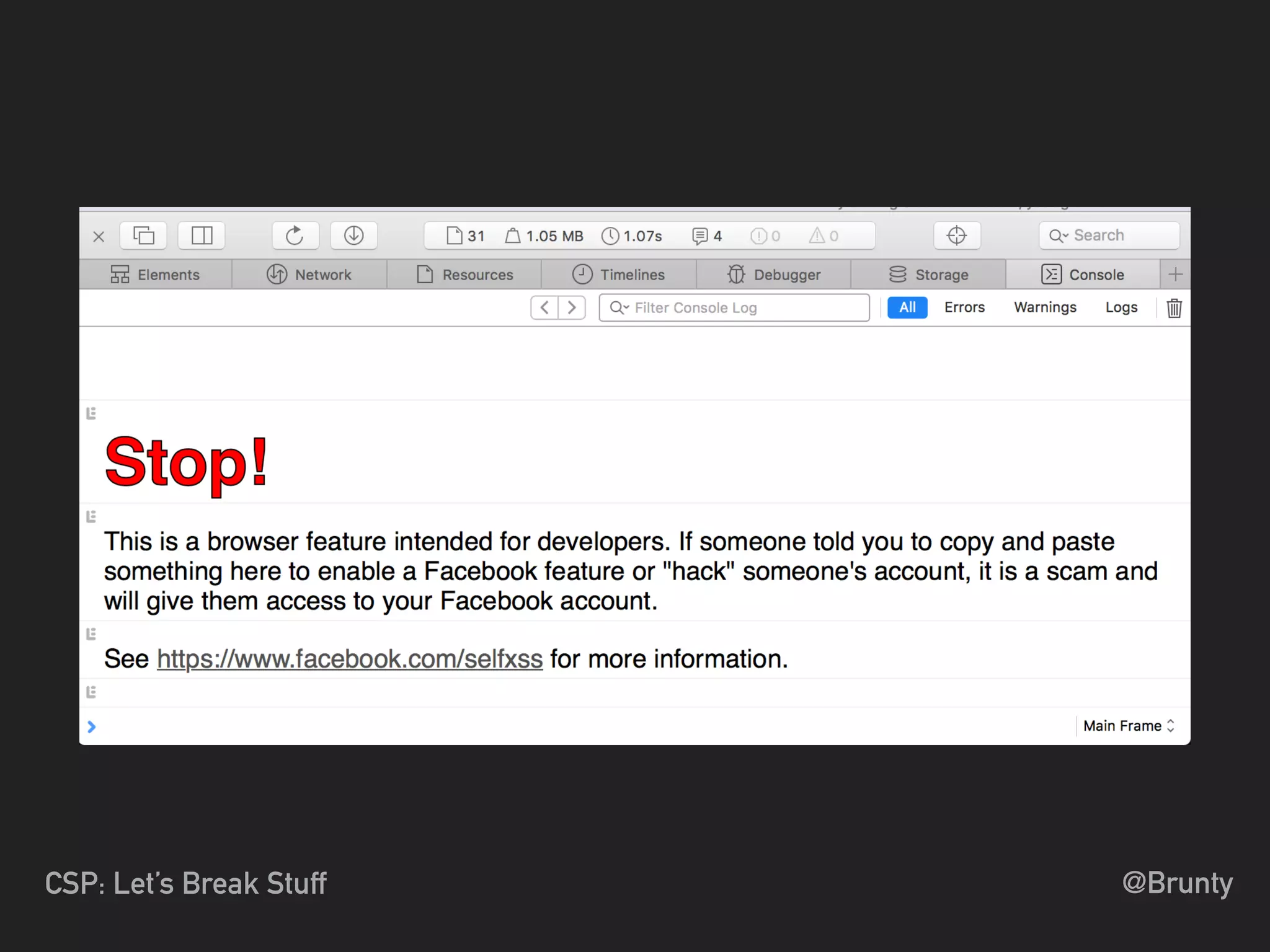
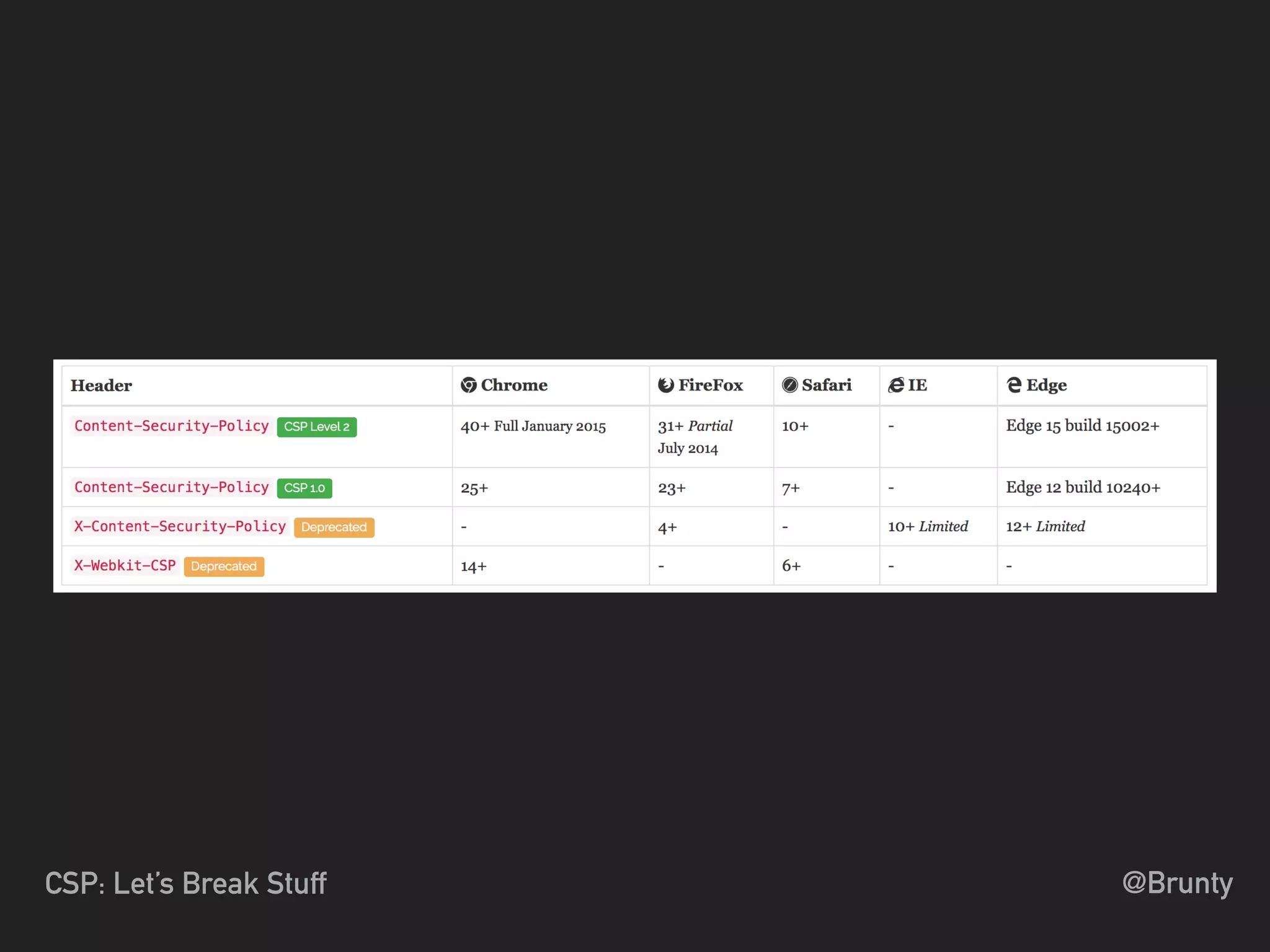
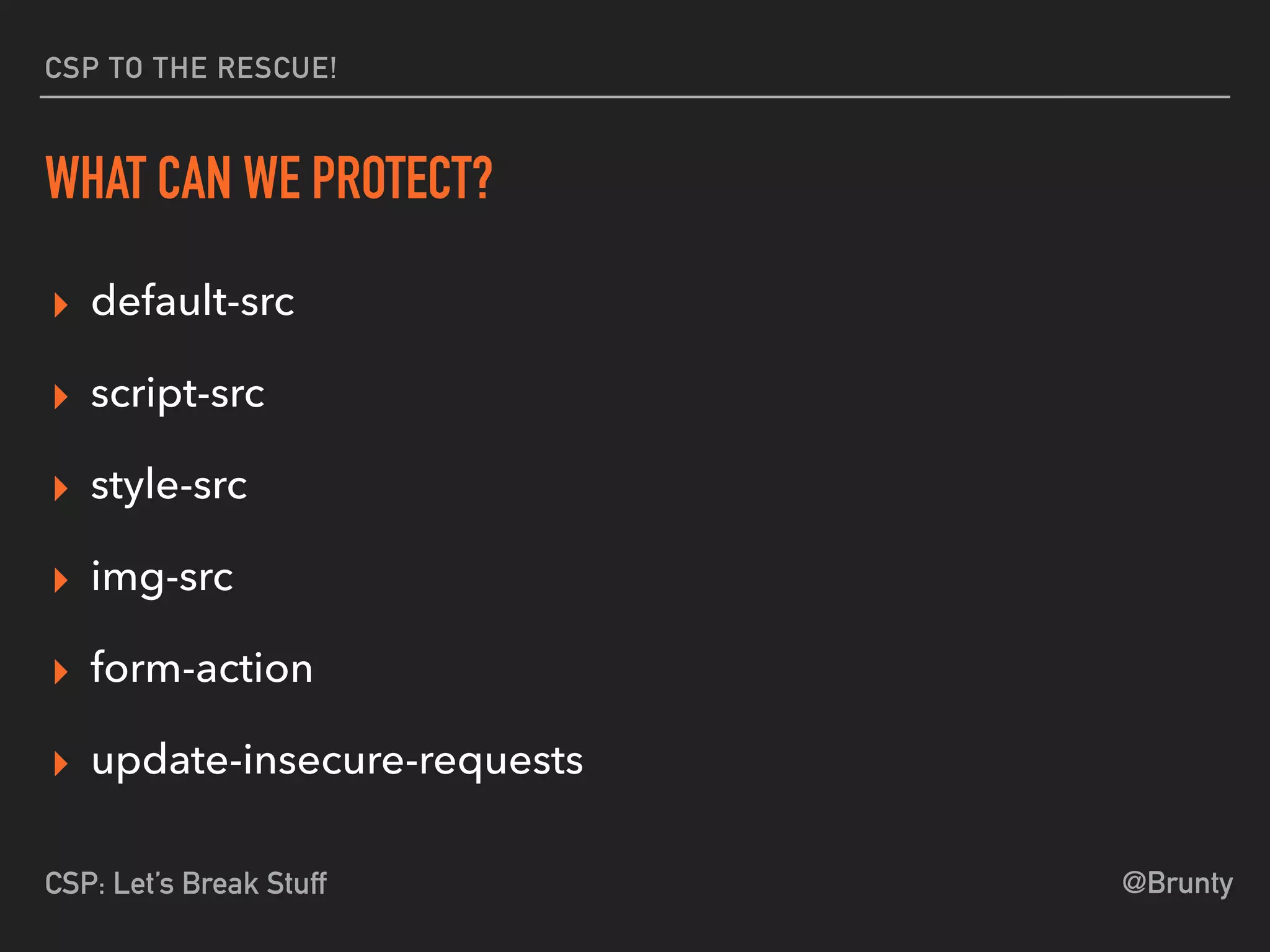
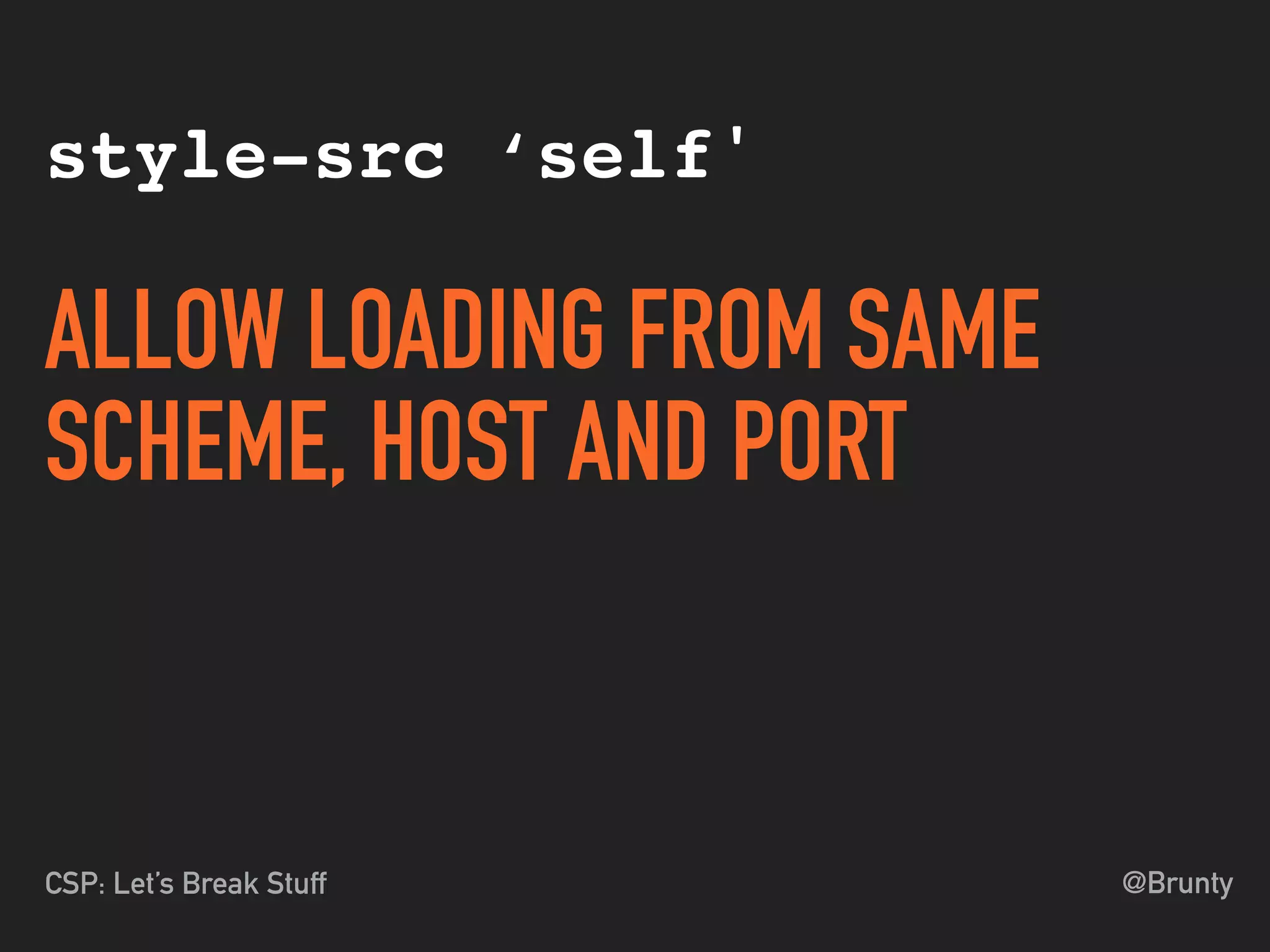
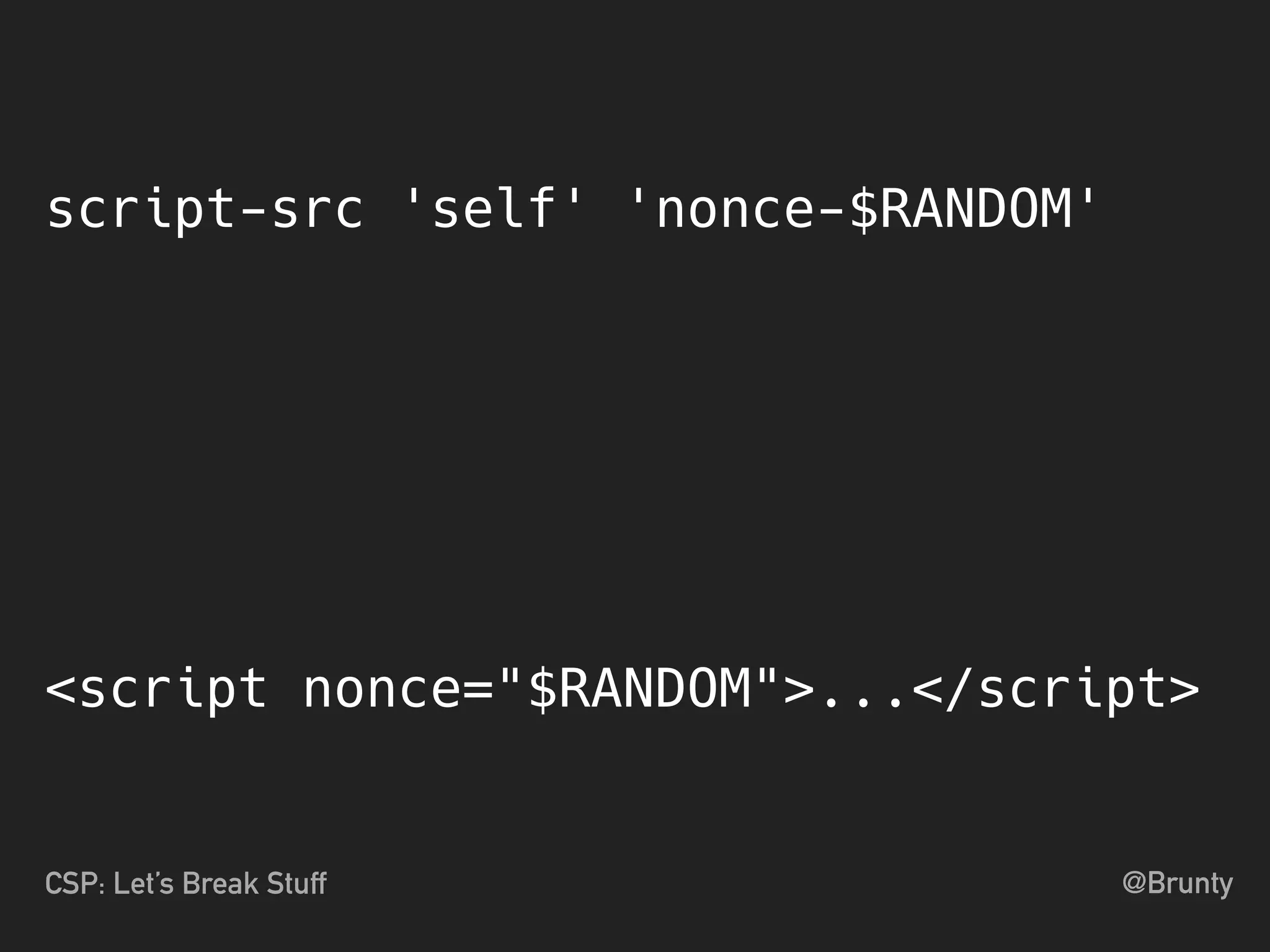
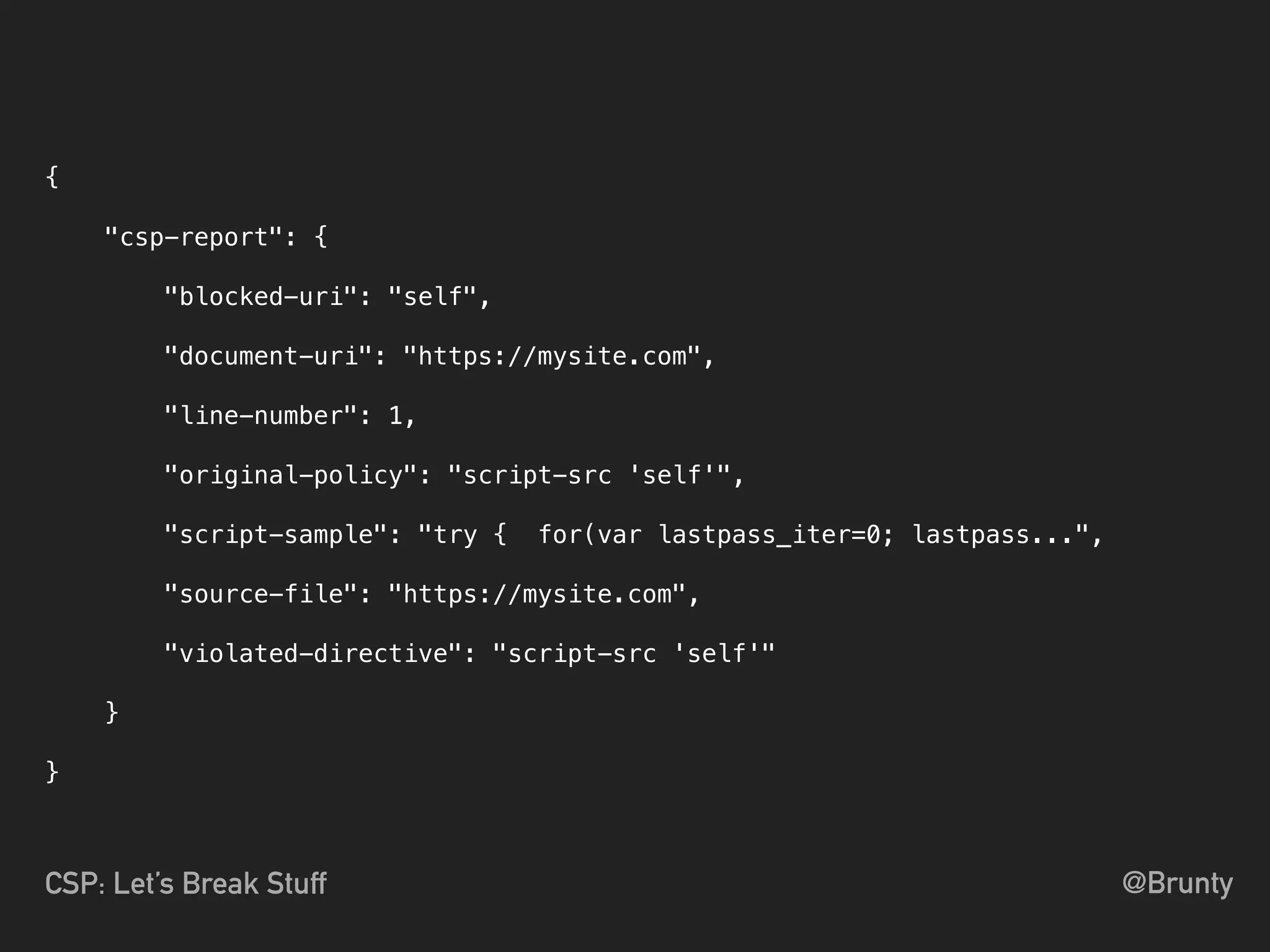
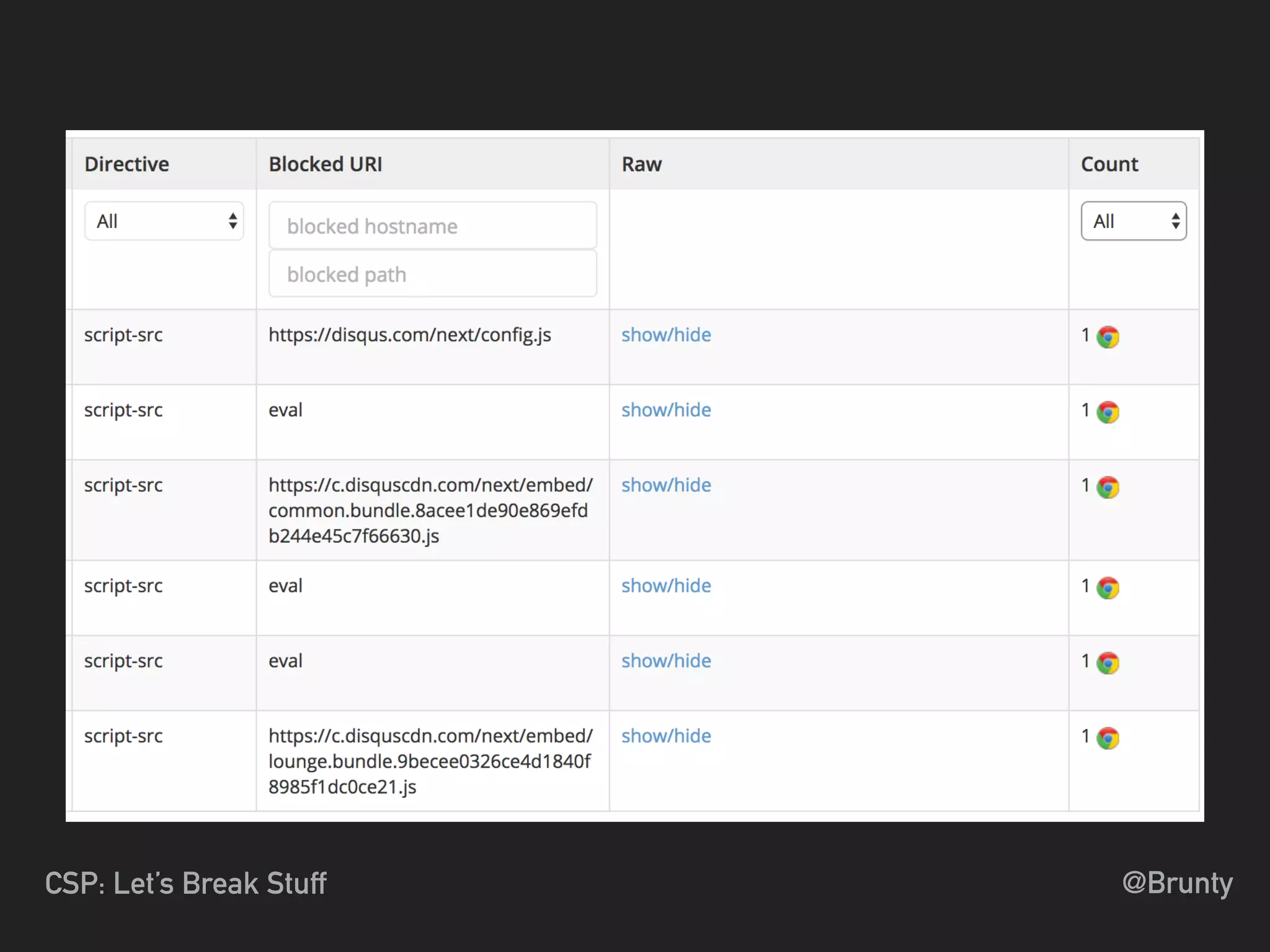
The document discusses the vulnerabilities of cross-site scripting (XSS) in web applications, highlighting its prevalence and potential dangers, including the manipulation of the Document Object Model (DOM) and theft of session cookies. It introduces Content Security Policy (CSP) as a mitigation strategy to regulate resource loading and enhance security against XSS attacks. The document emphasizes the importance of proper CSP configuration and provides resources for further learning.

















![@BruntyCSP: Let’s Break Stuff
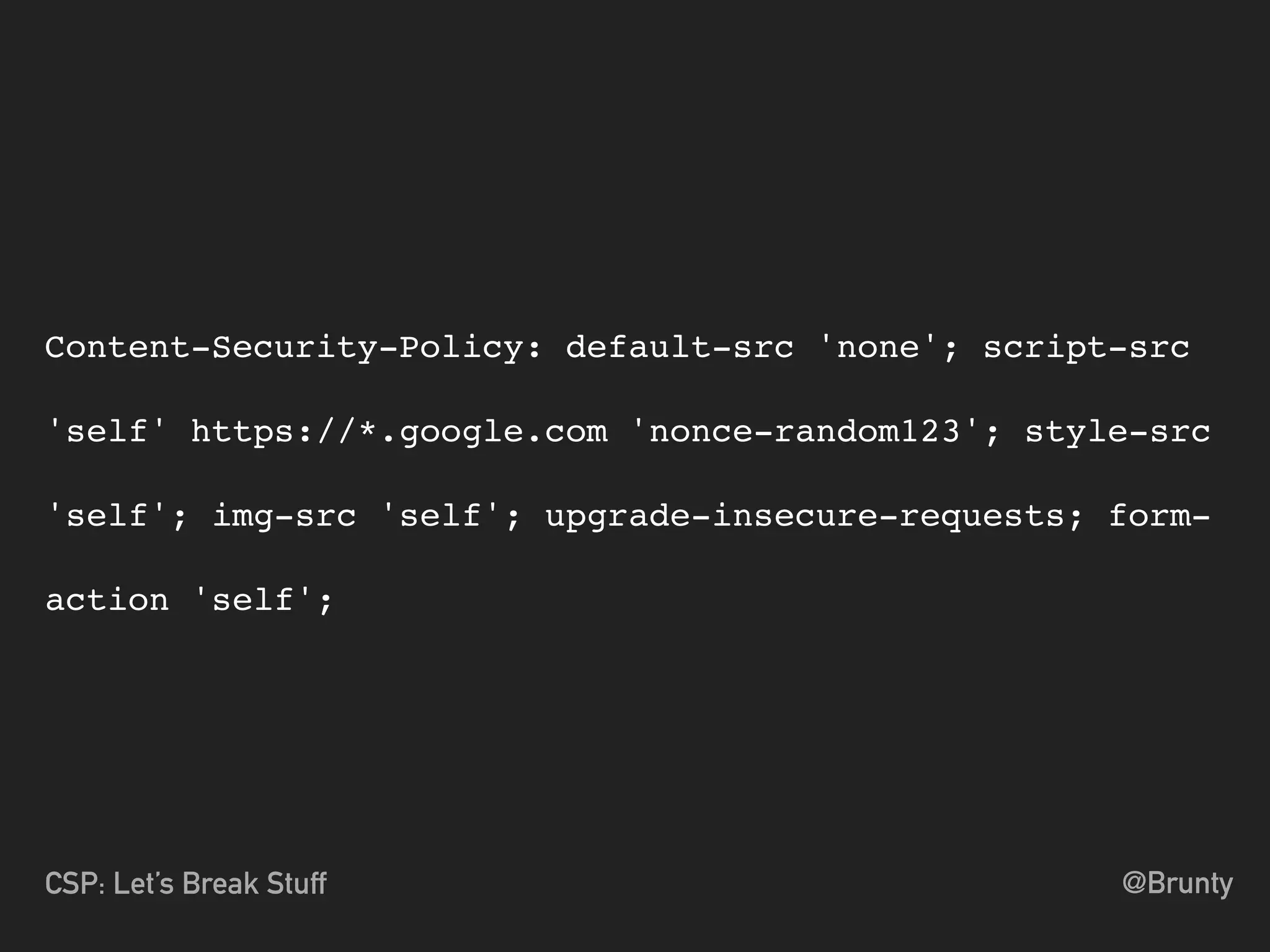
Content-Security-Policy-Report-Only: [policy]; report-
uri https://app.report-uri.io/r/default/csp/reportOnly;](https://image.slidesharecdn.com/cspforphpswbathdigital-171019112502/75/Content-Security-Policies-Let-s-Break-Stuff-for-PHPSW-at-Bath-Digital-38-2048.jpg)