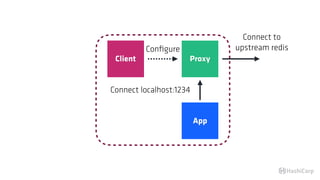
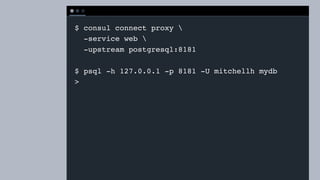
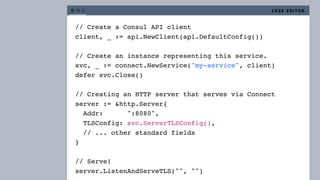
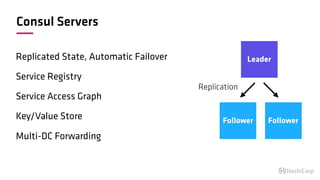
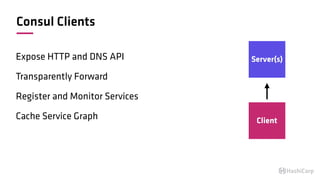
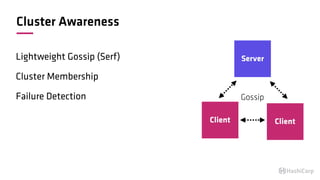
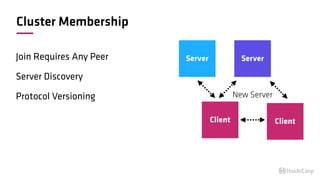
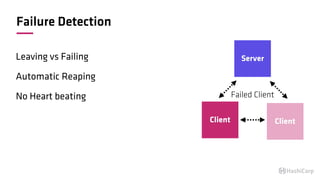
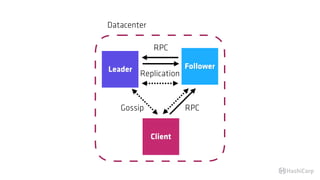
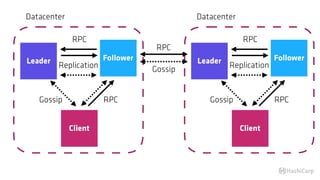
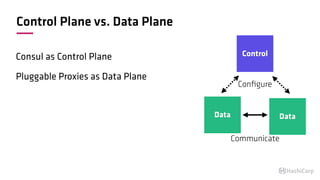
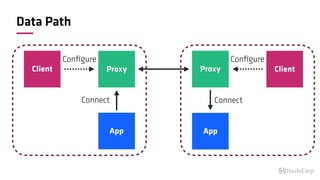
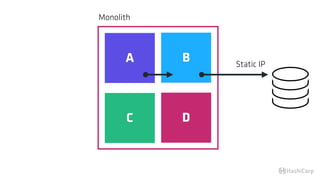
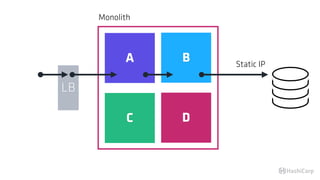
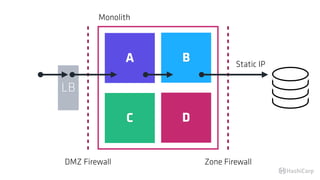
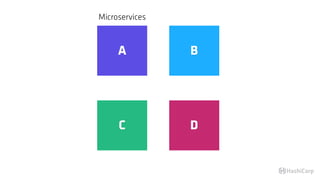
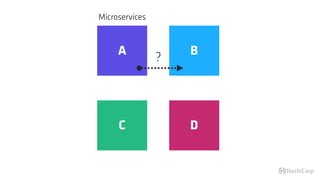
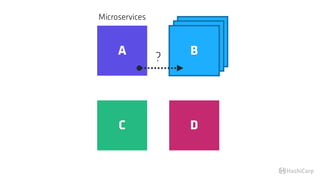
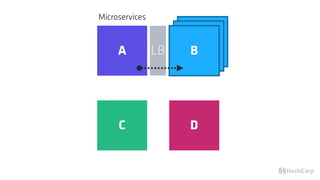
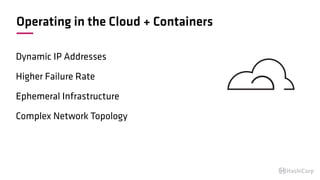
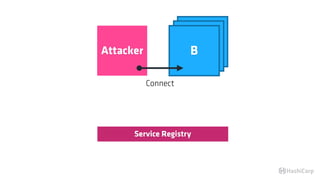
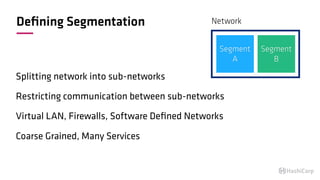
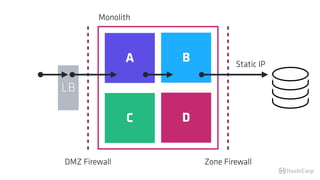
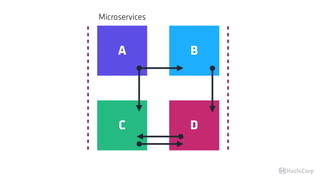
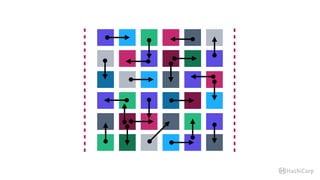
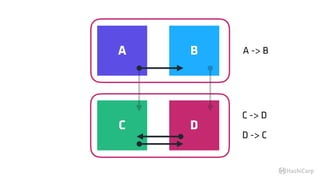
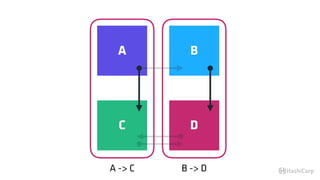
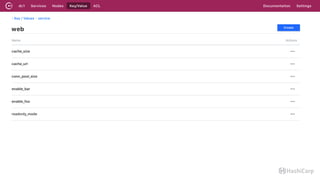
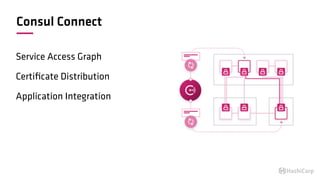
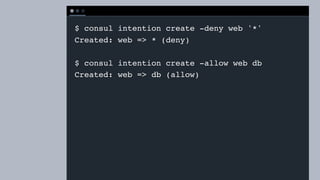
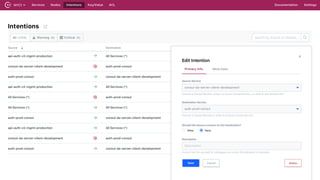
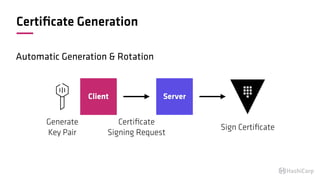
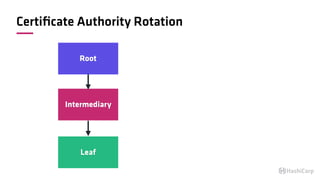
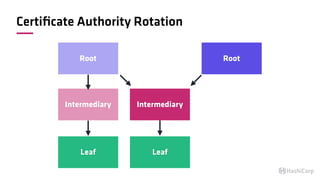
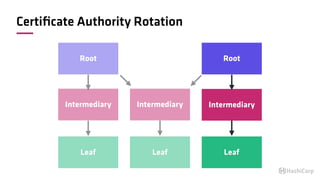
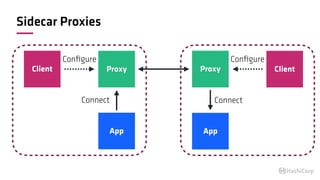
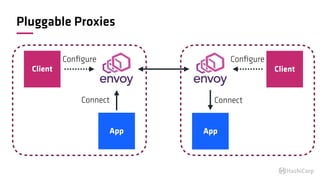
The document discusses the implementation of service mesh for microservices using various tools such as Consul, Nomad, and Vault. It highlights key features like service discovery, secure service communication, and configuration management, facilitating seamless interaction among microservices. Additionally, it covers the architecture, deployment strategies, and operational challenges associated with microservices infrastructure.





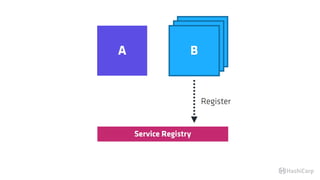
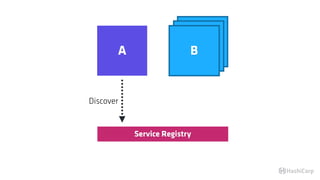
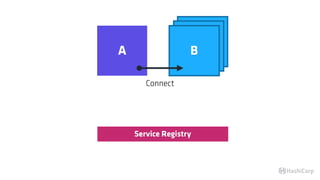





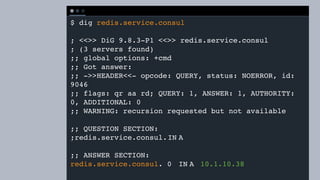
![T E R M I N A L
$ curl http://localhost:8500/v1/catalog/service/redis
[
{
"ID": "52f73400-a352-80d2-9624-e70cc9996762",
"Node": "consul-client-2",
"Address": "10.0.1.83",
"Datacenter": "dc1",
"ServiceName": "redis",
"ServiceTags": [
"global",
"cache"
],
"ServiceAddress": "10.0.1.83",
"ServicePort": 24815,
"ModifyIndex": 31,
…](https://image.slidesharecdn.com/consulconnect-181003145143/85/Consul-Service-Mesh-for-Microservices-35-320.jpg)
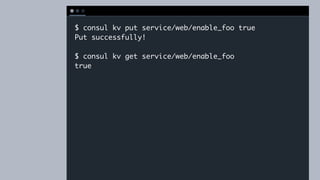




![{
"service": "web",
"connect": {
"proxy": {
"config": {
"upstreams": [{
"destination_name": "redis",
"local_bind_port": 1234
}]
}
}
}
}
C O D E E D I T O R](https://image.slidesharecdn.com/consulconnect-181003145143/85/Consul-Service-Mesh-for-Microservices-55-320.jpg)