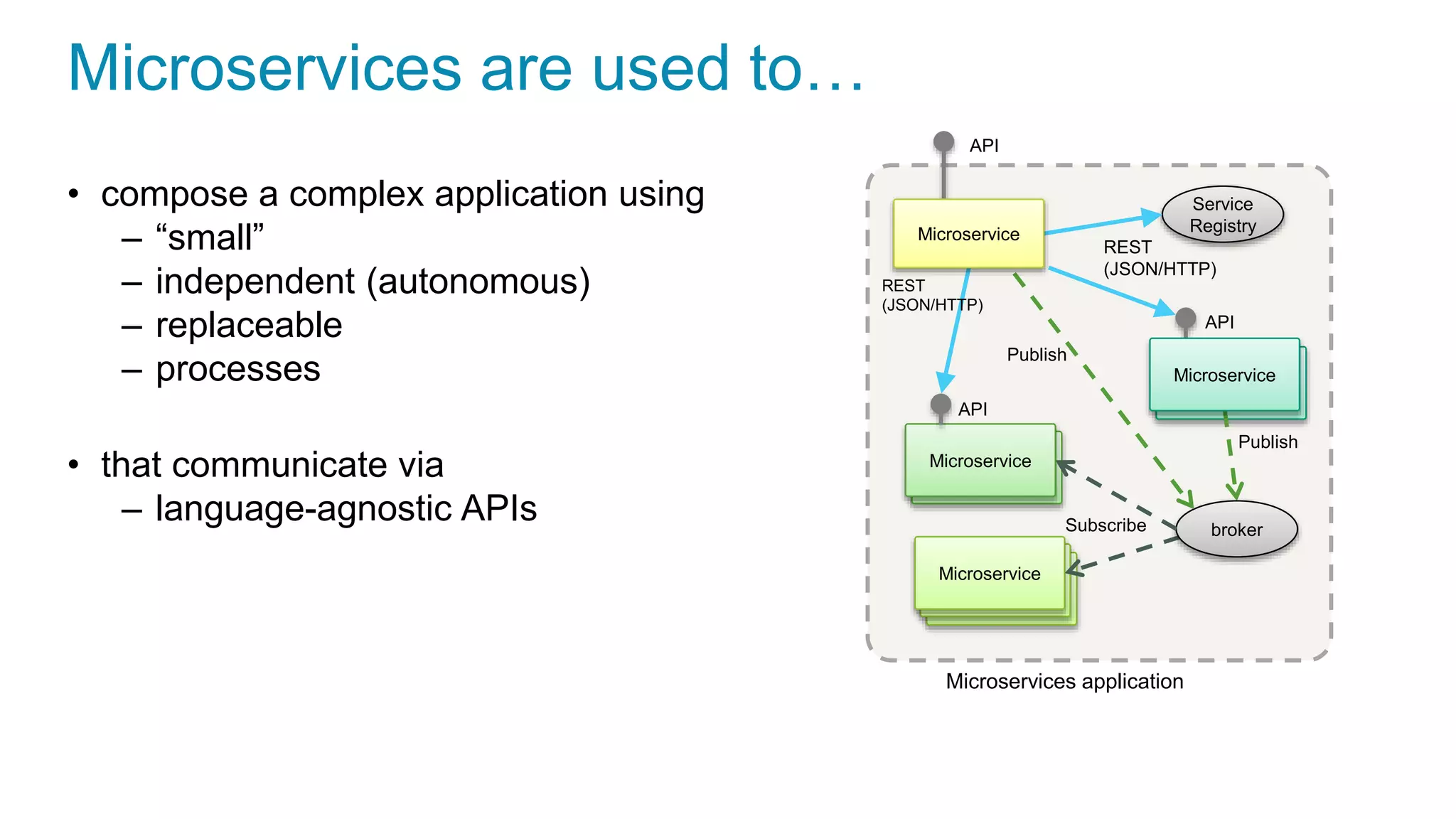
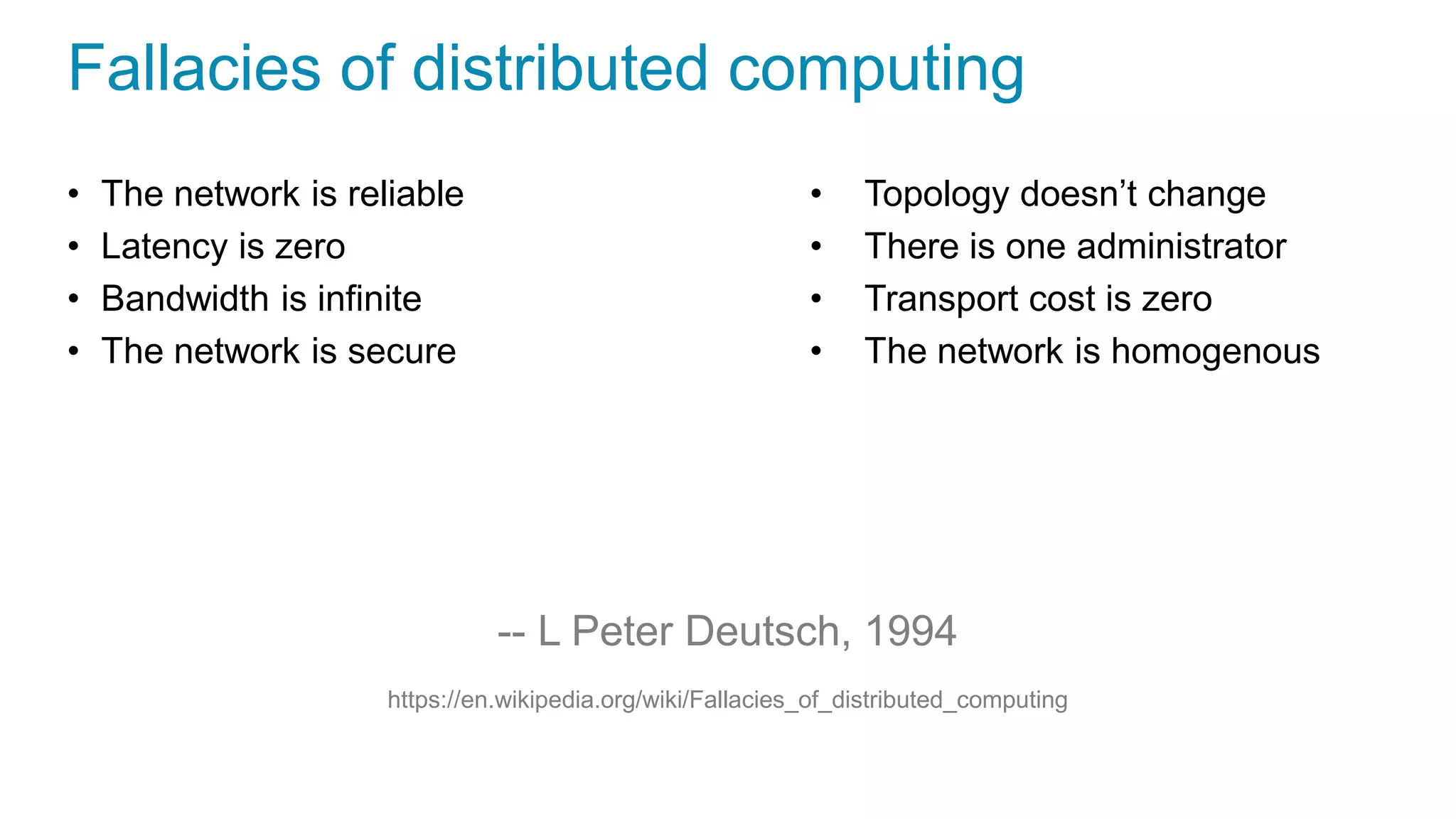
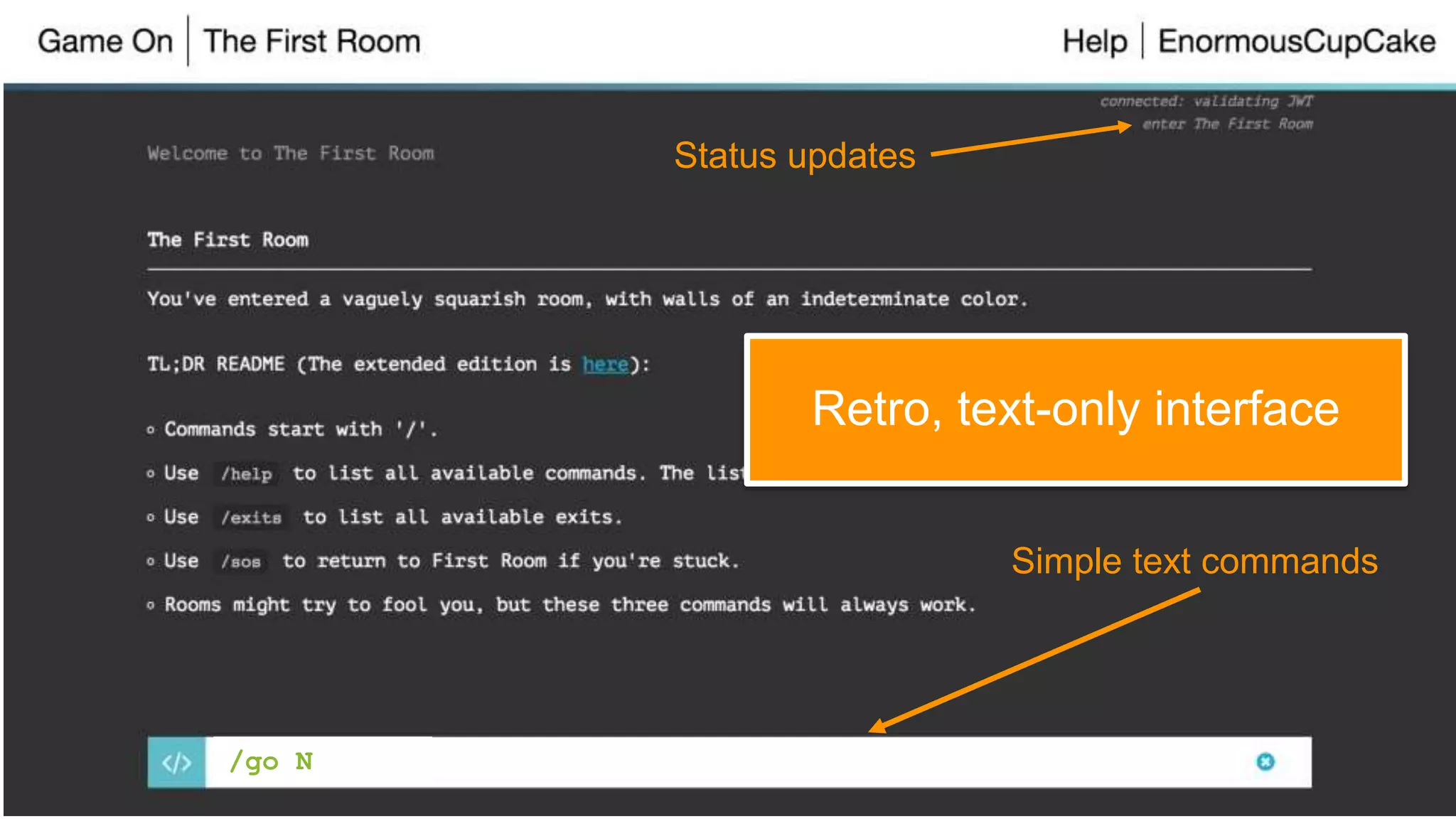
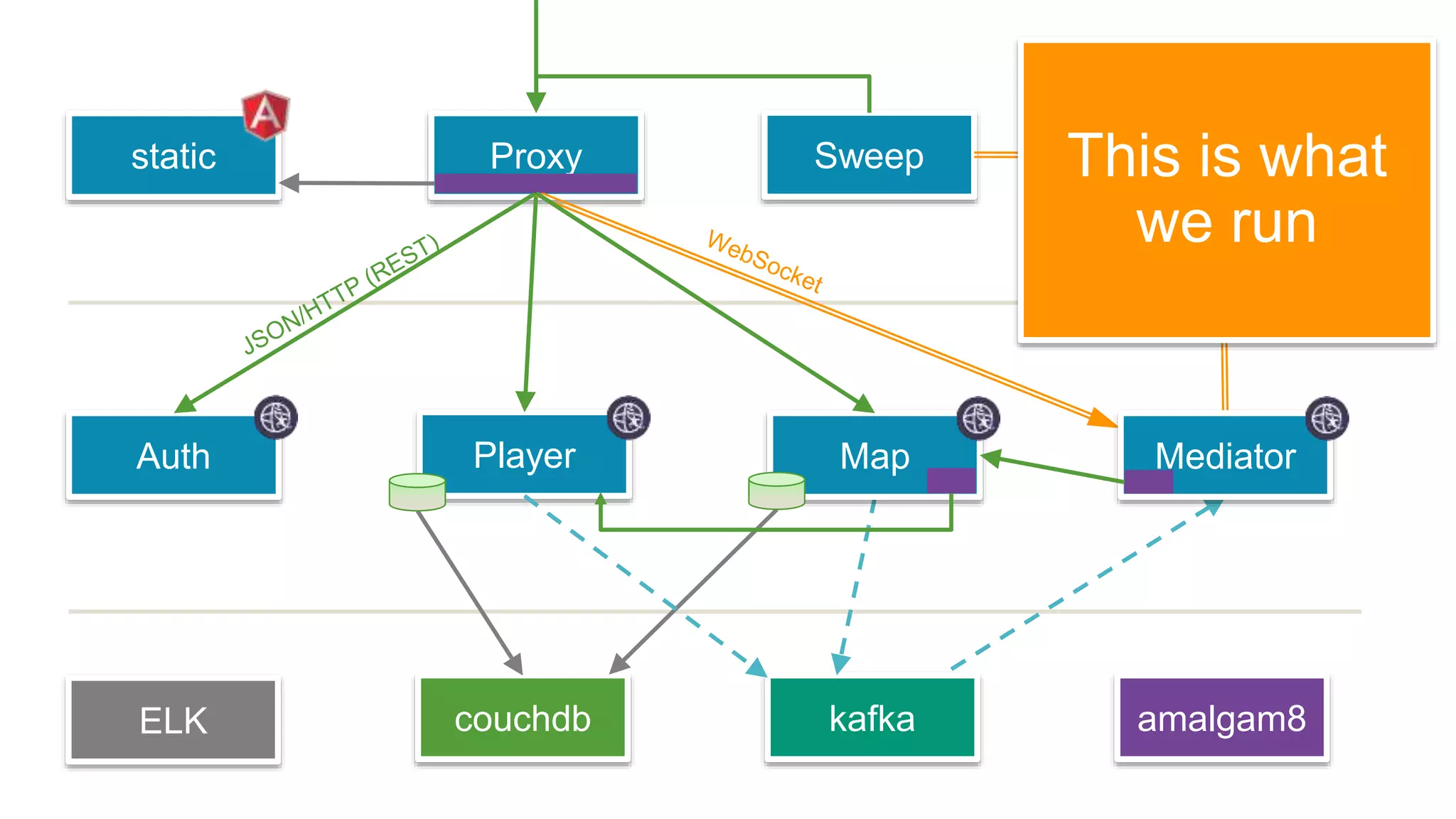
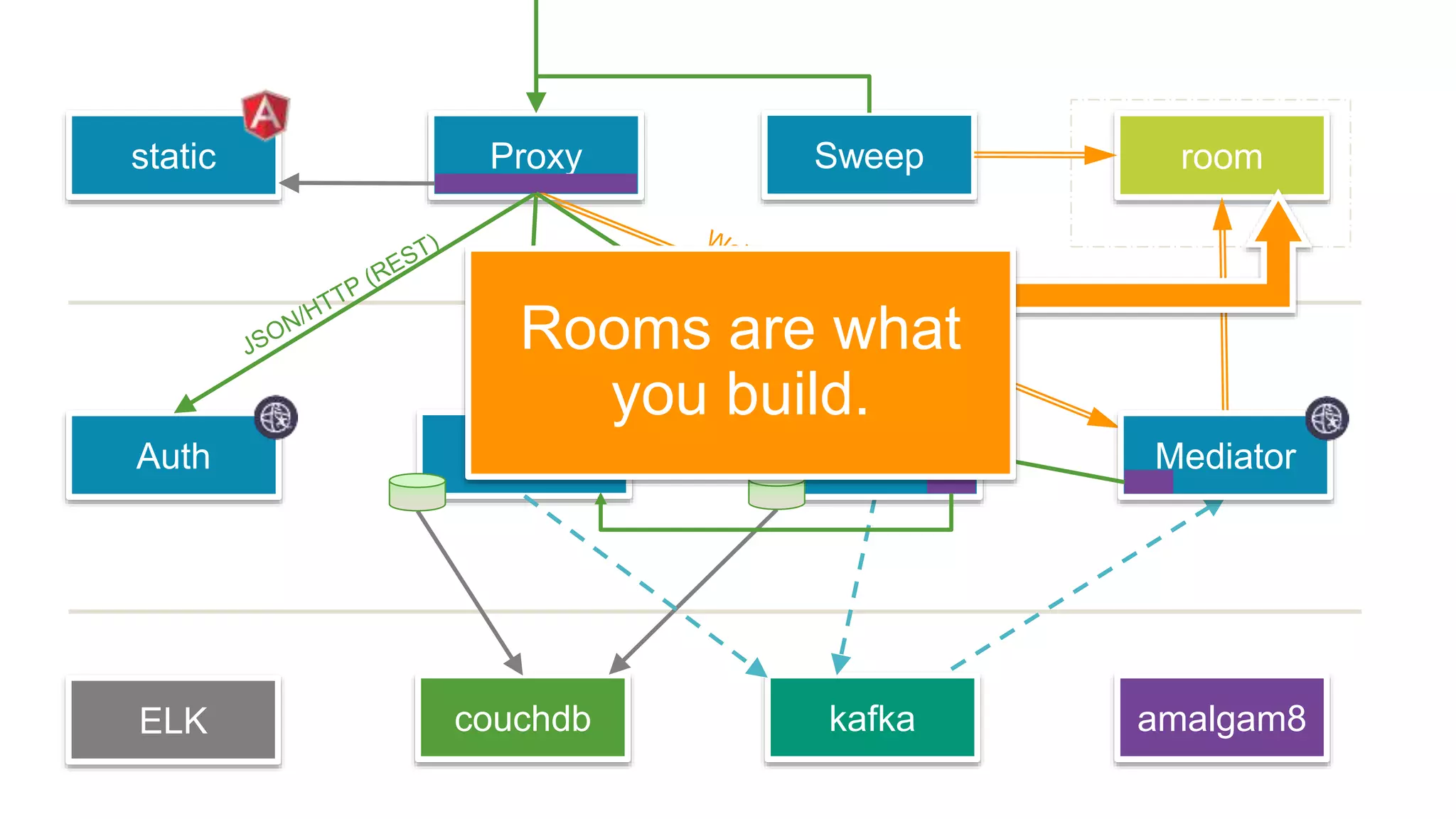
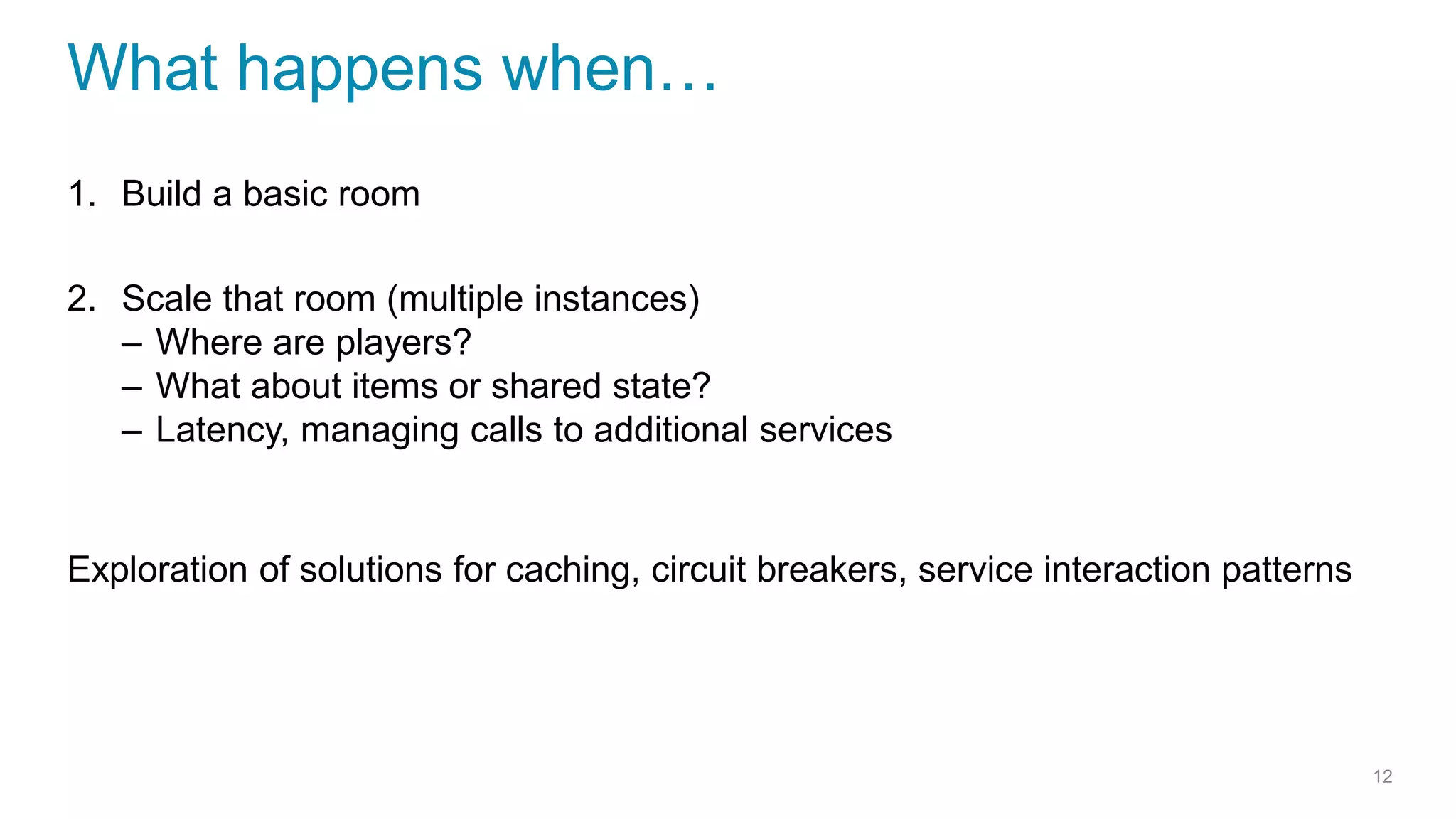
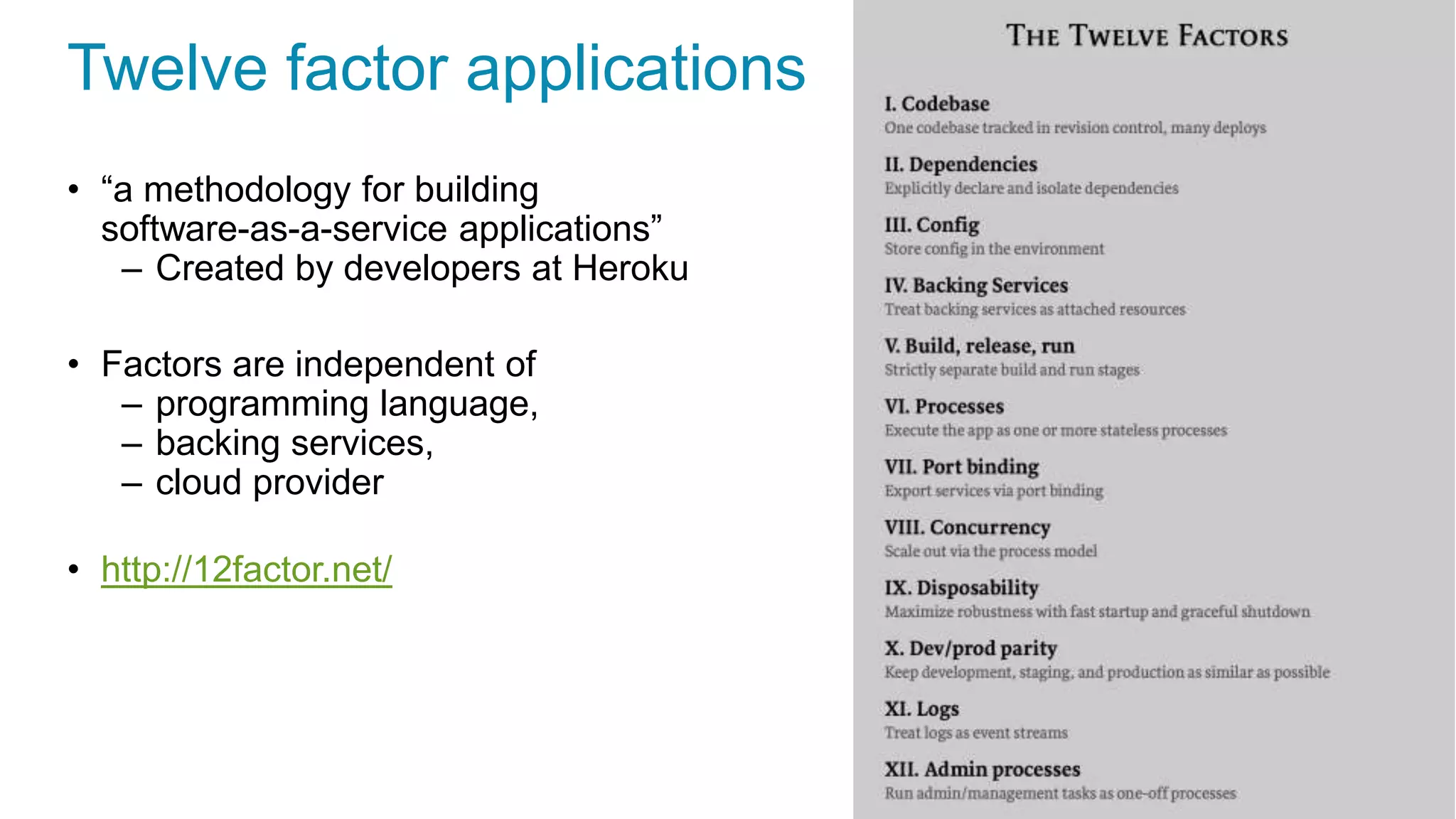
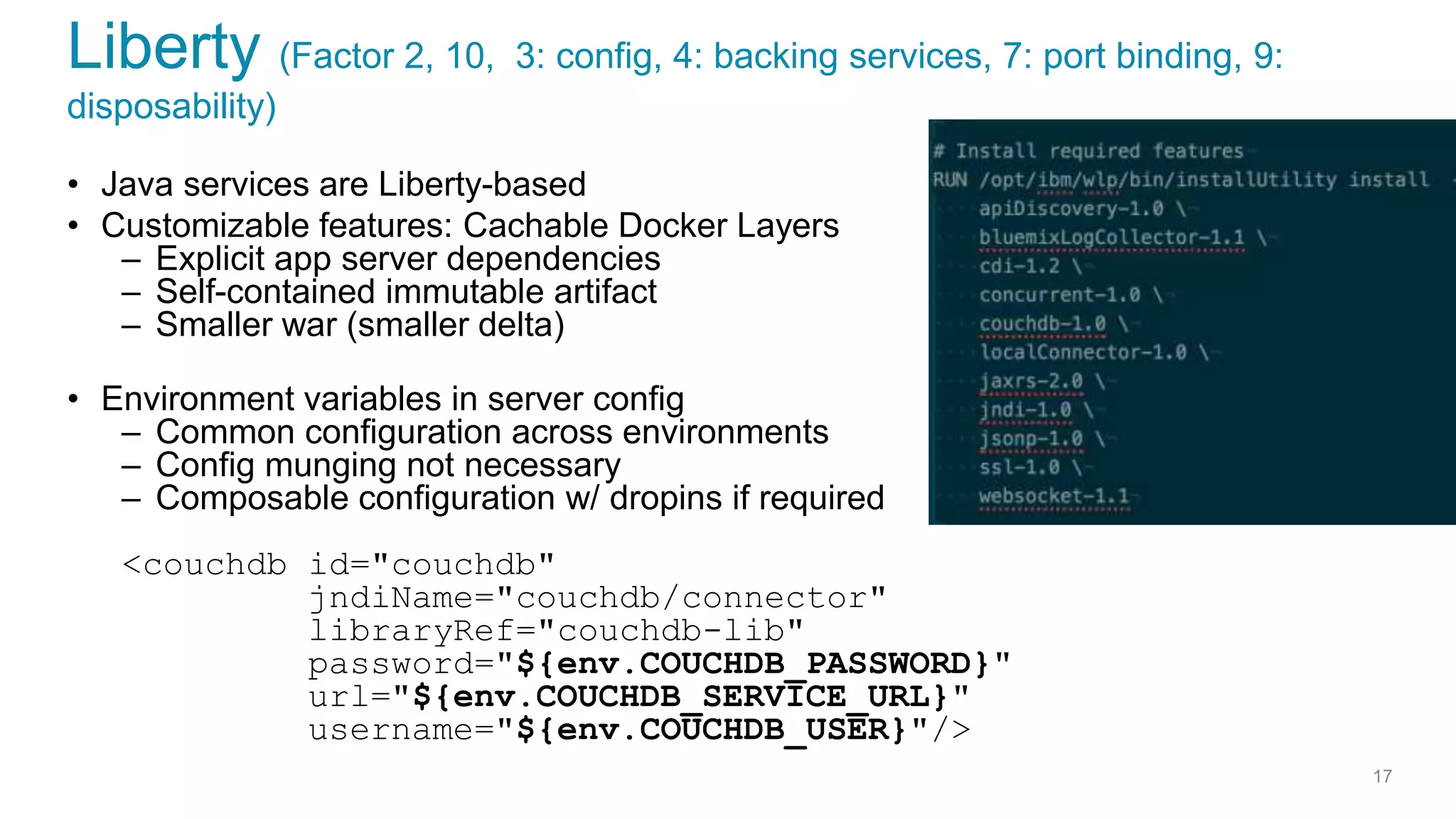
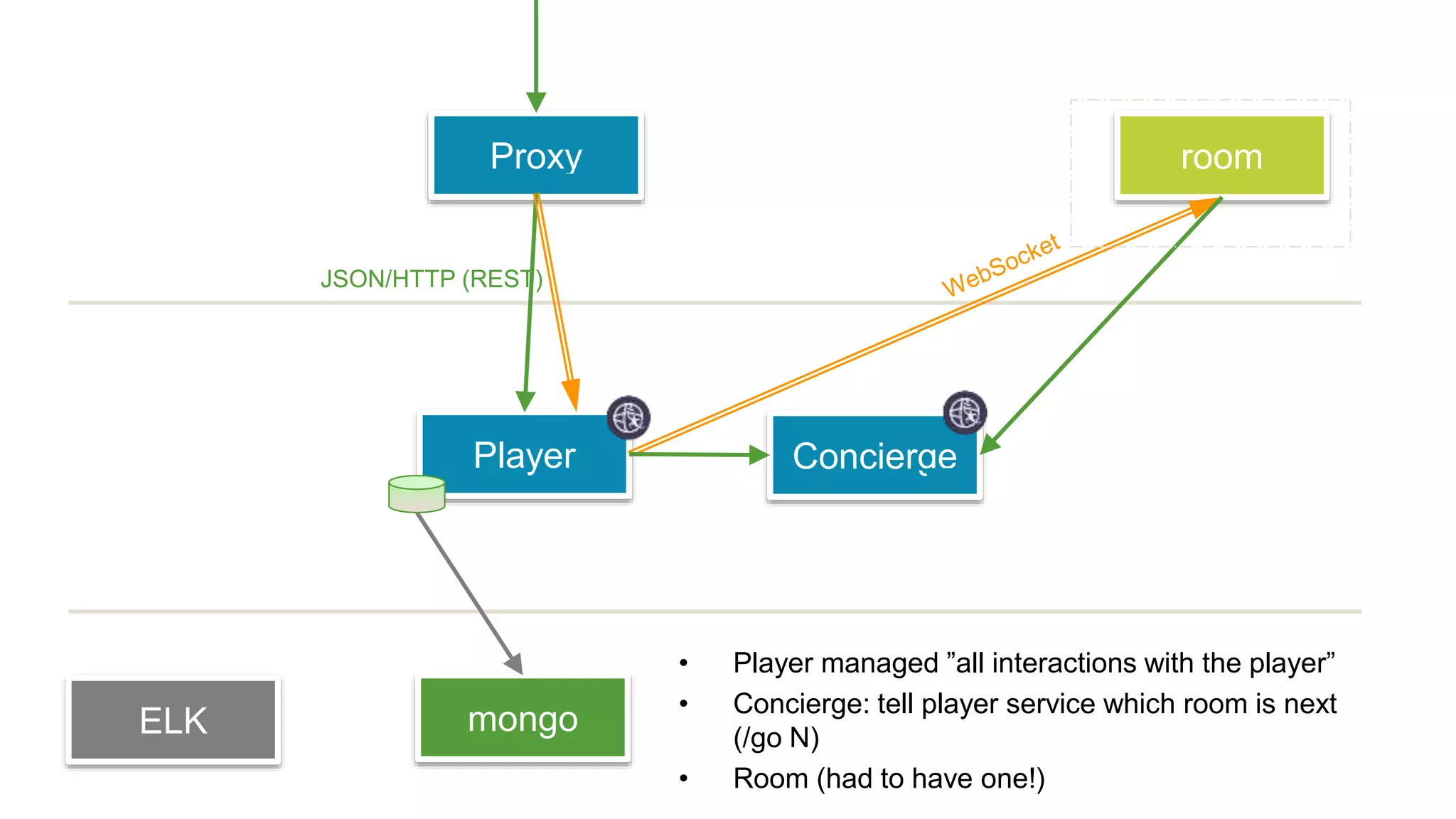
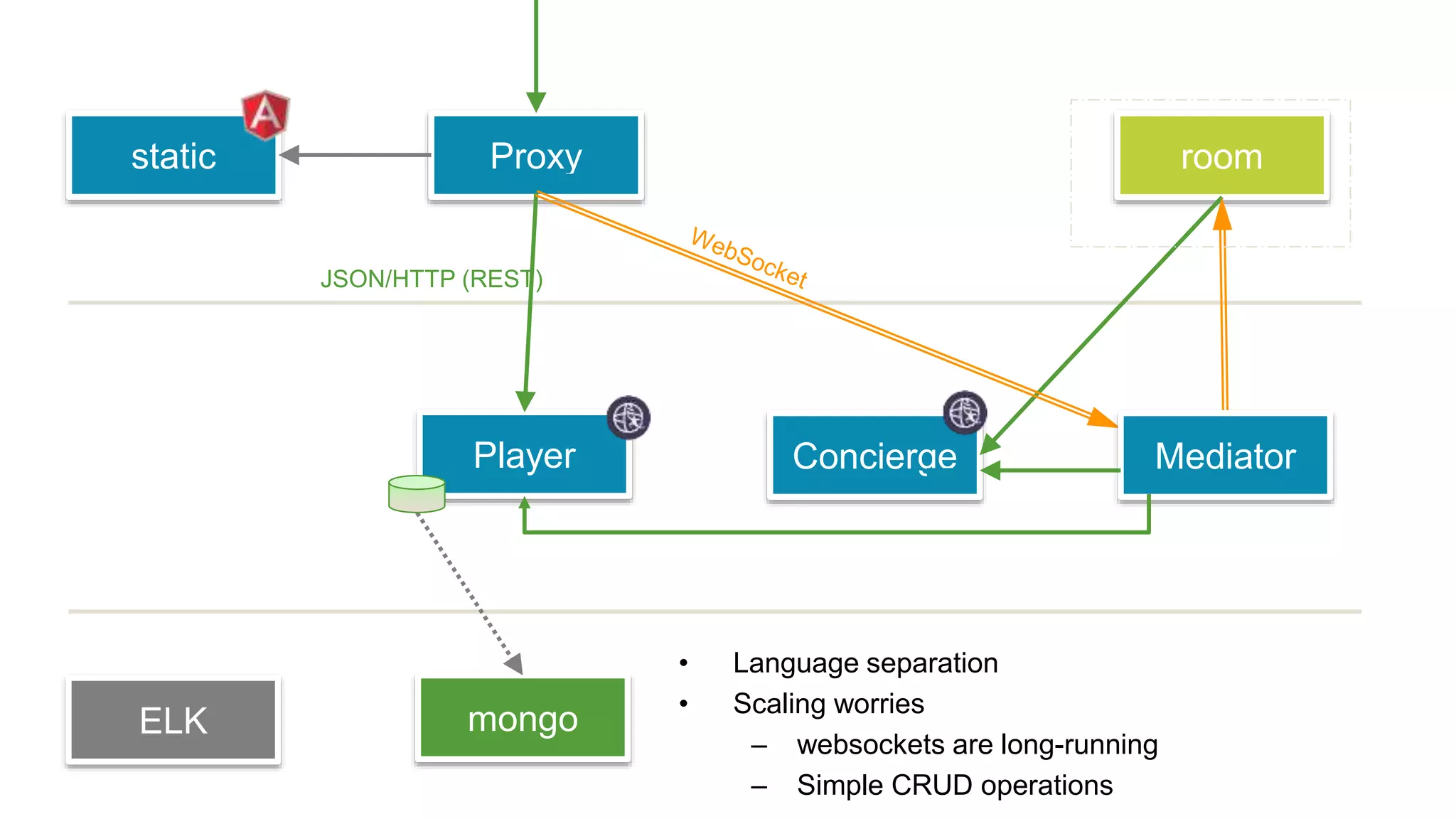
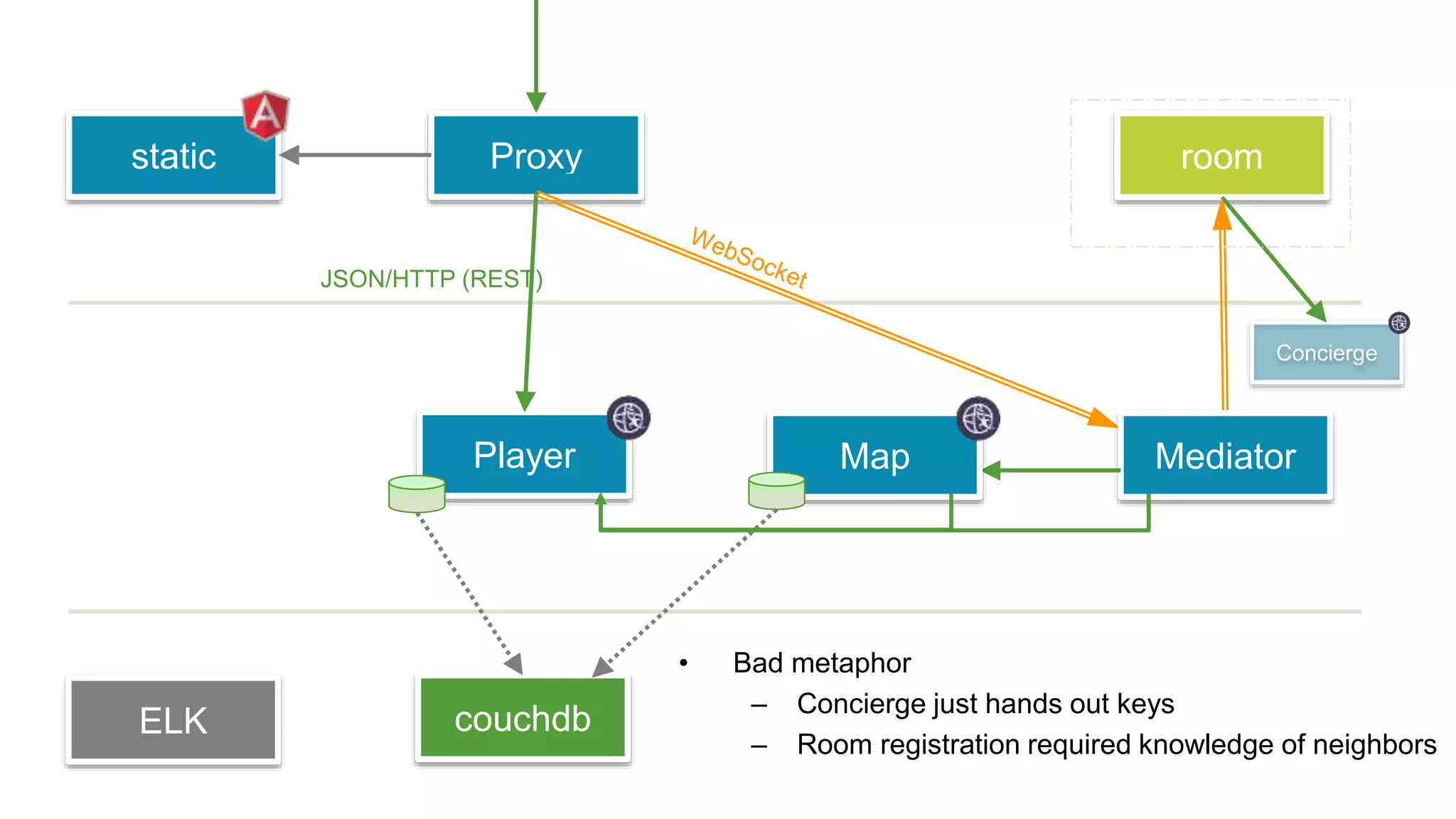
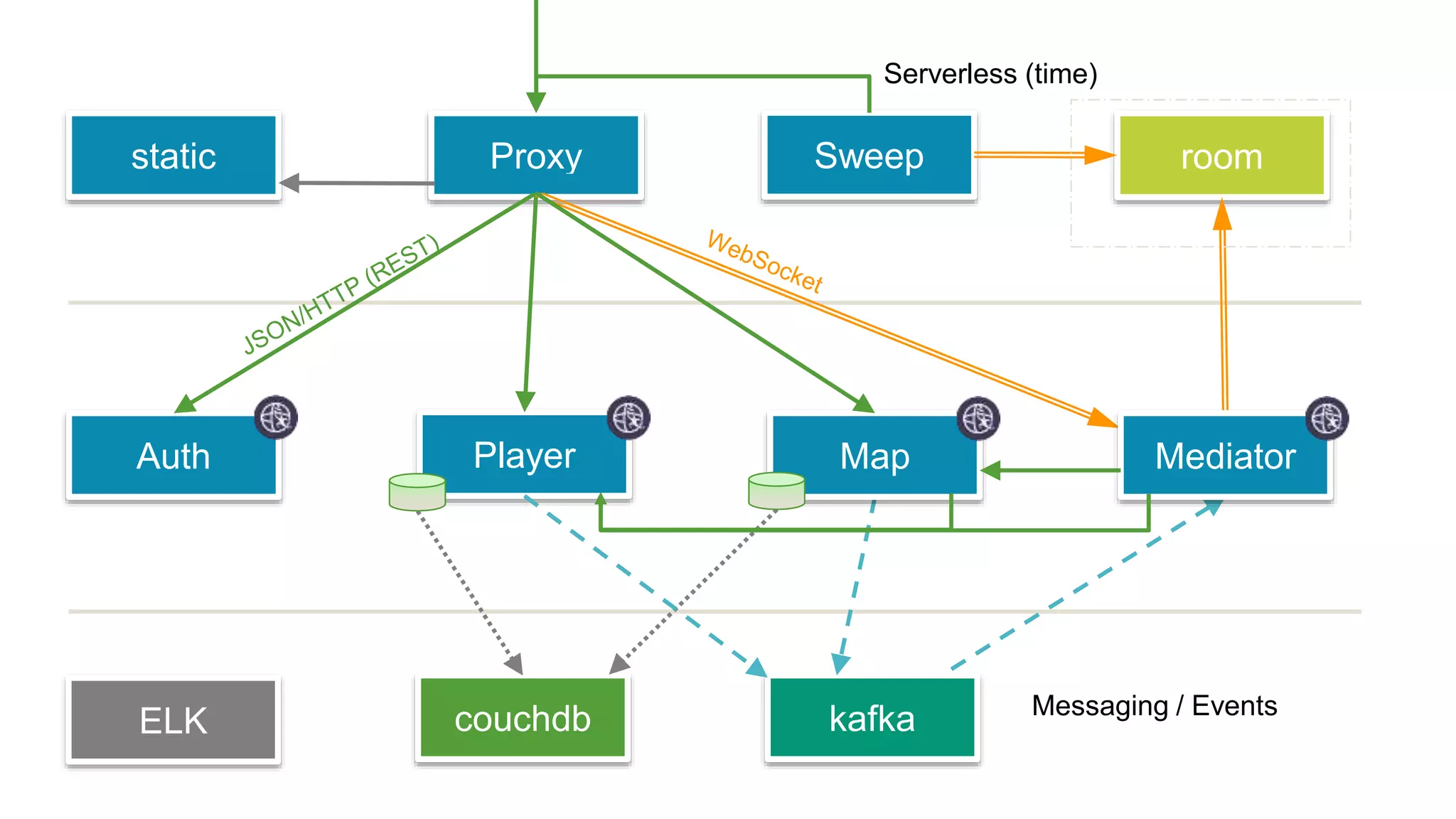
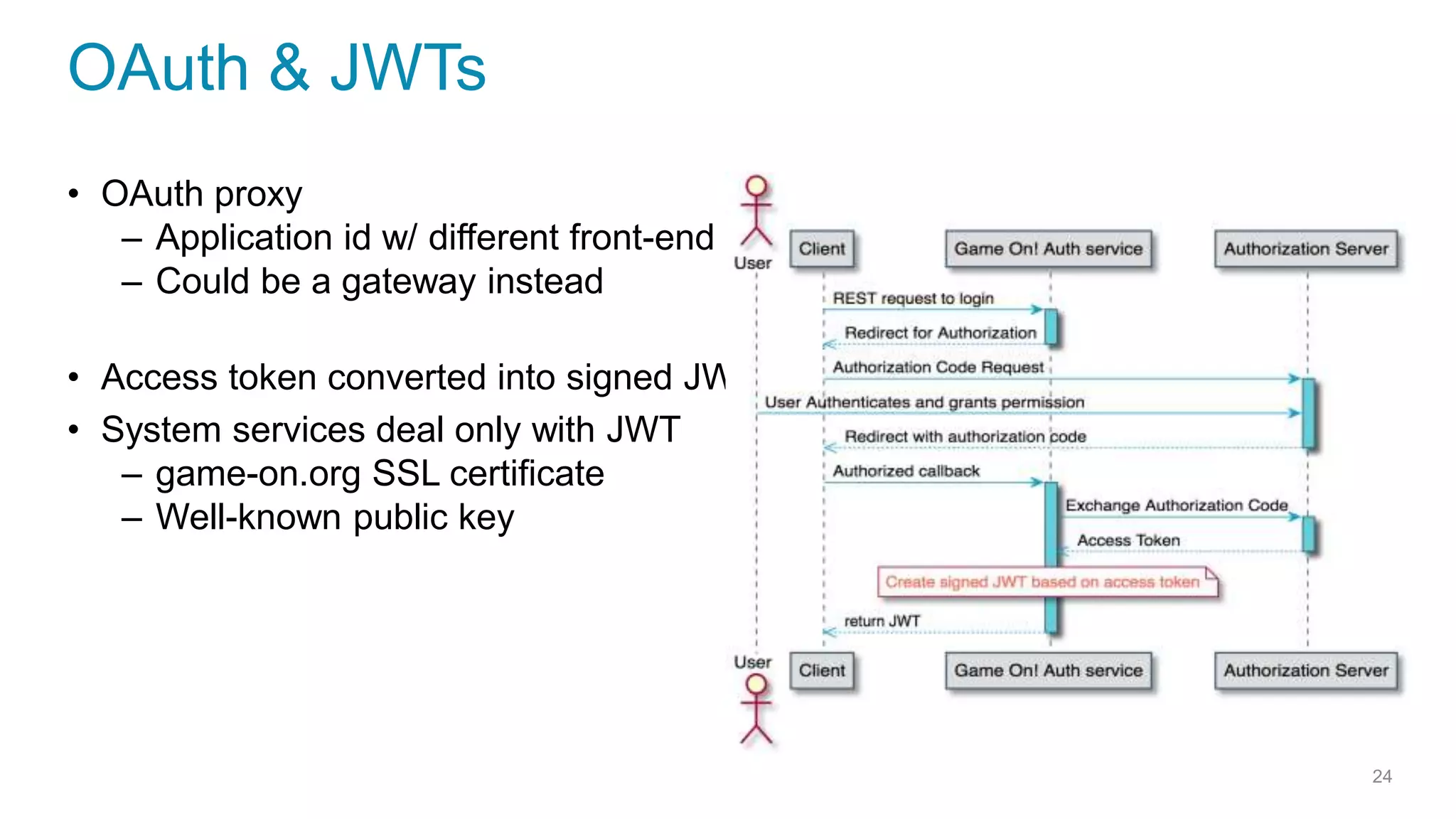
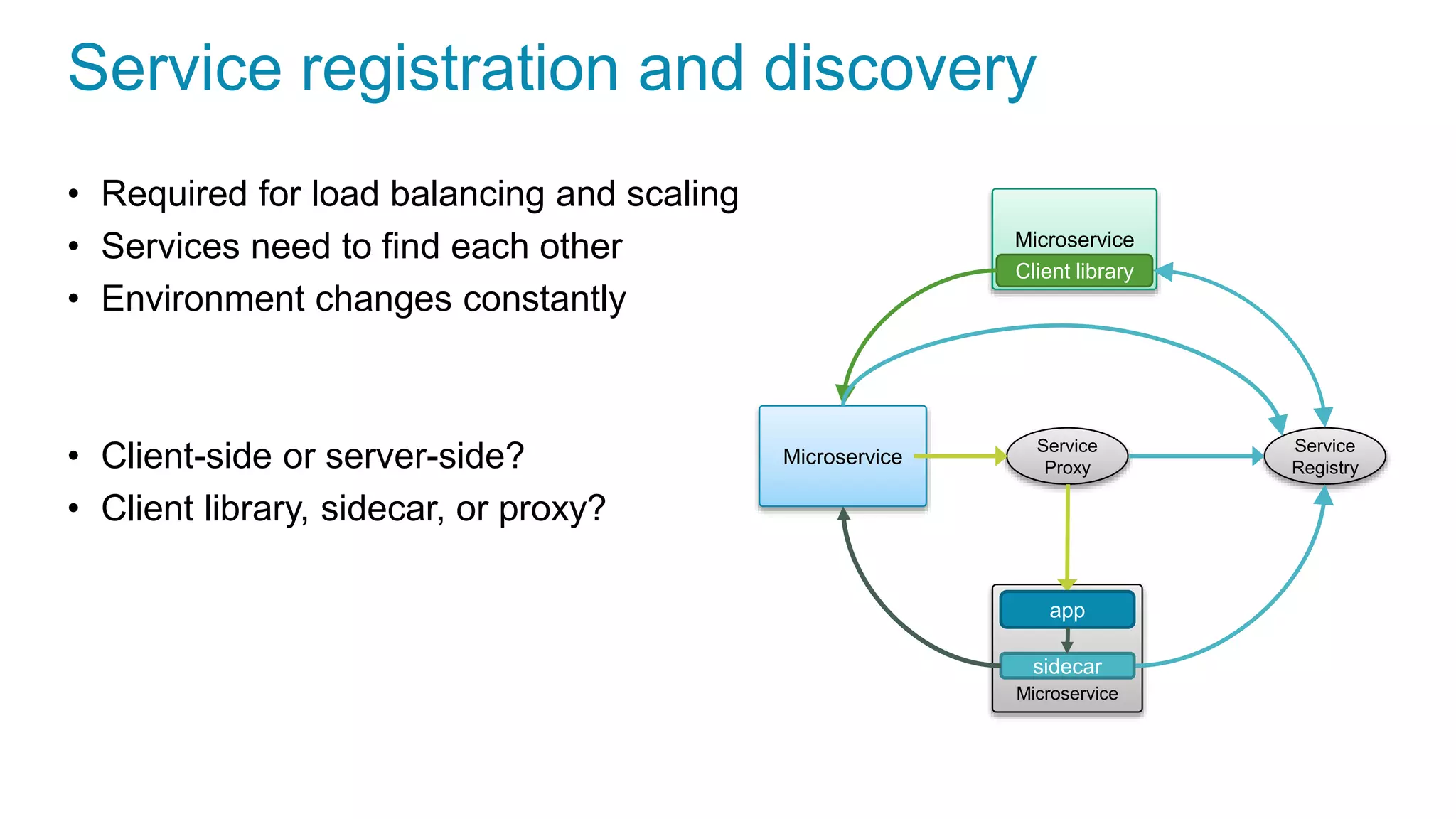
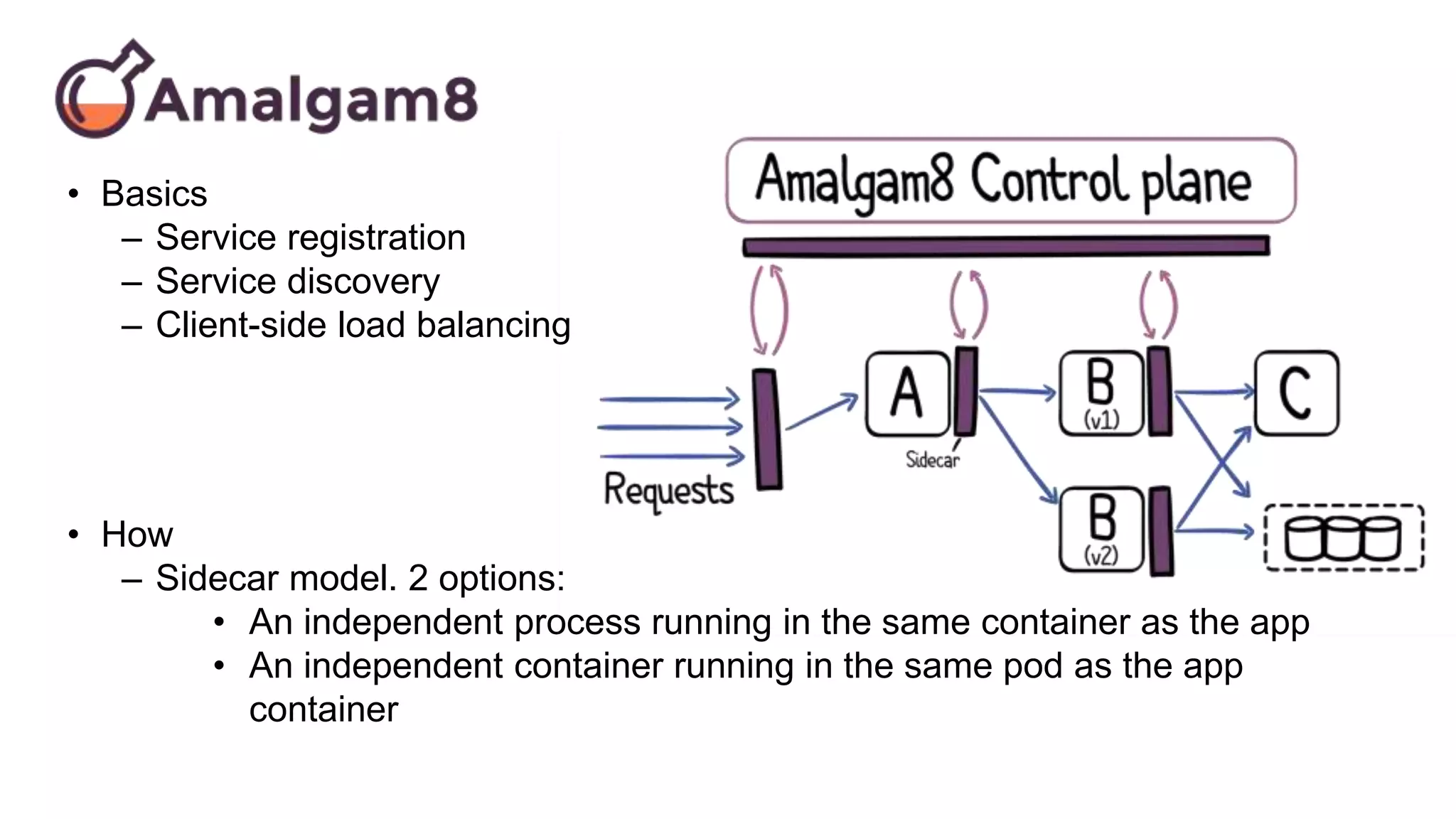
This document discusses using microservices to build a text-based adventure game. It introduces microservices concepts like independent processes that communicate via APIs. Reasons for using microservices include accommodating different technologies, facilitating rapid growth, and reducing risk. The document then outlines building a basic room service and exploring solutions for scaling it, handling shared state, and managing calls between services. It also discusses security approaches like OAuth, JSON Web Tokens, and hashed message authentication codes. Finally, it covers service discovery and registration concepts needed for load balancing and scaling microservices applications.