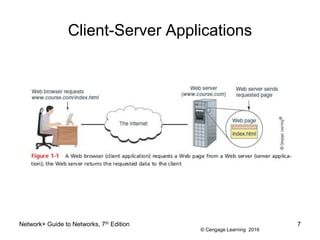
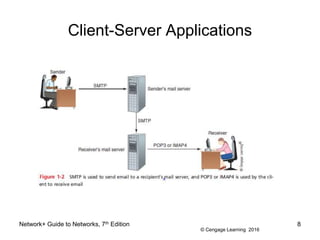
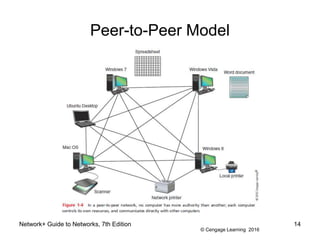
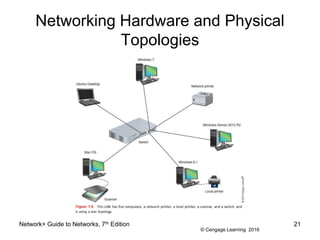
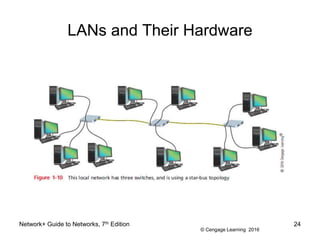
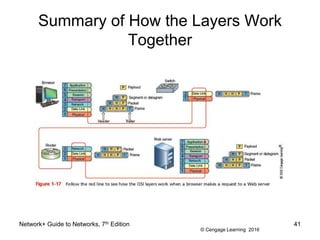
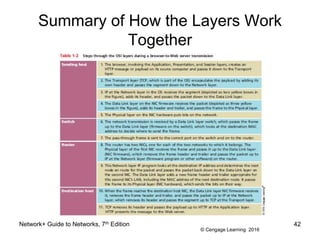
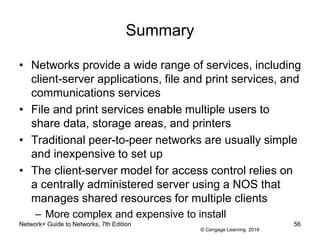
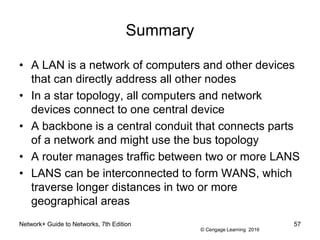
The document provides information about presentations that cover chapter objectives from a Network+ Guide to Networks textbook. It states that the presentations include the objectives listed at the beginning of each chapter and figures from the chapters. Instructors can customize the presentations for their class needs and additional images can be found on the instructor companion site.