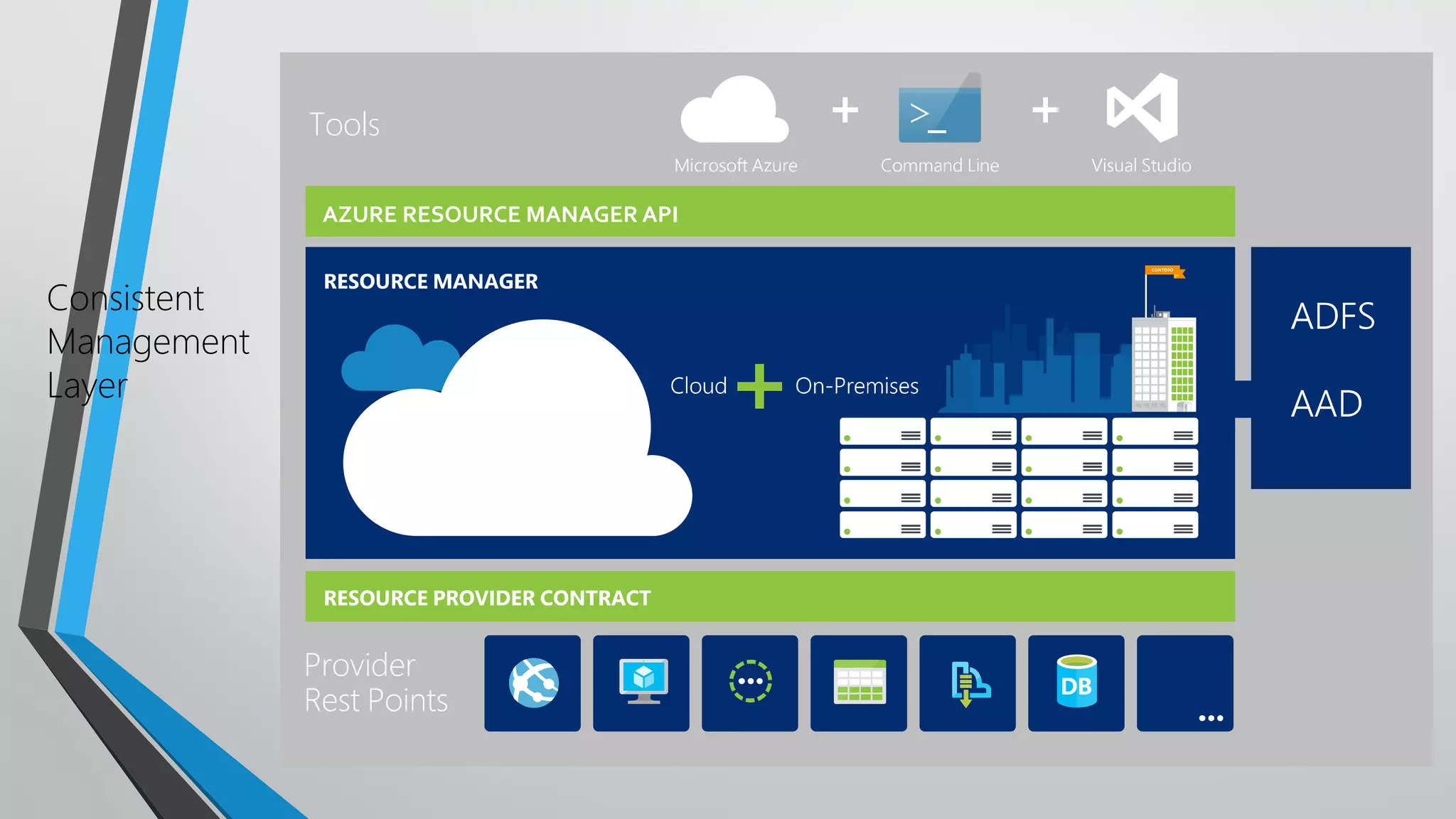
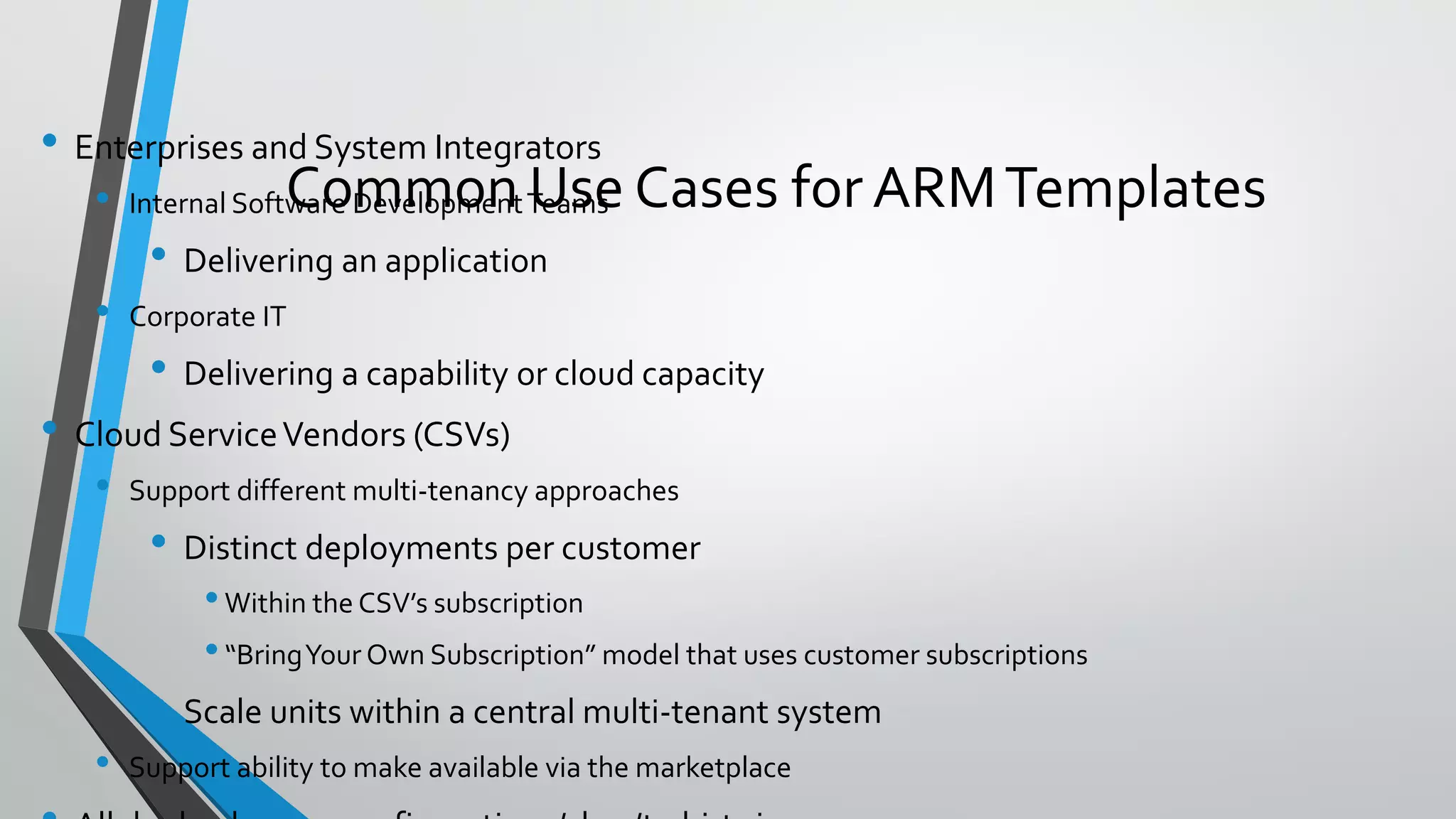
This document discusses Azure Resource Manager templates, which provide a declarative and automated way to deploy resources in Azure. Some key points:
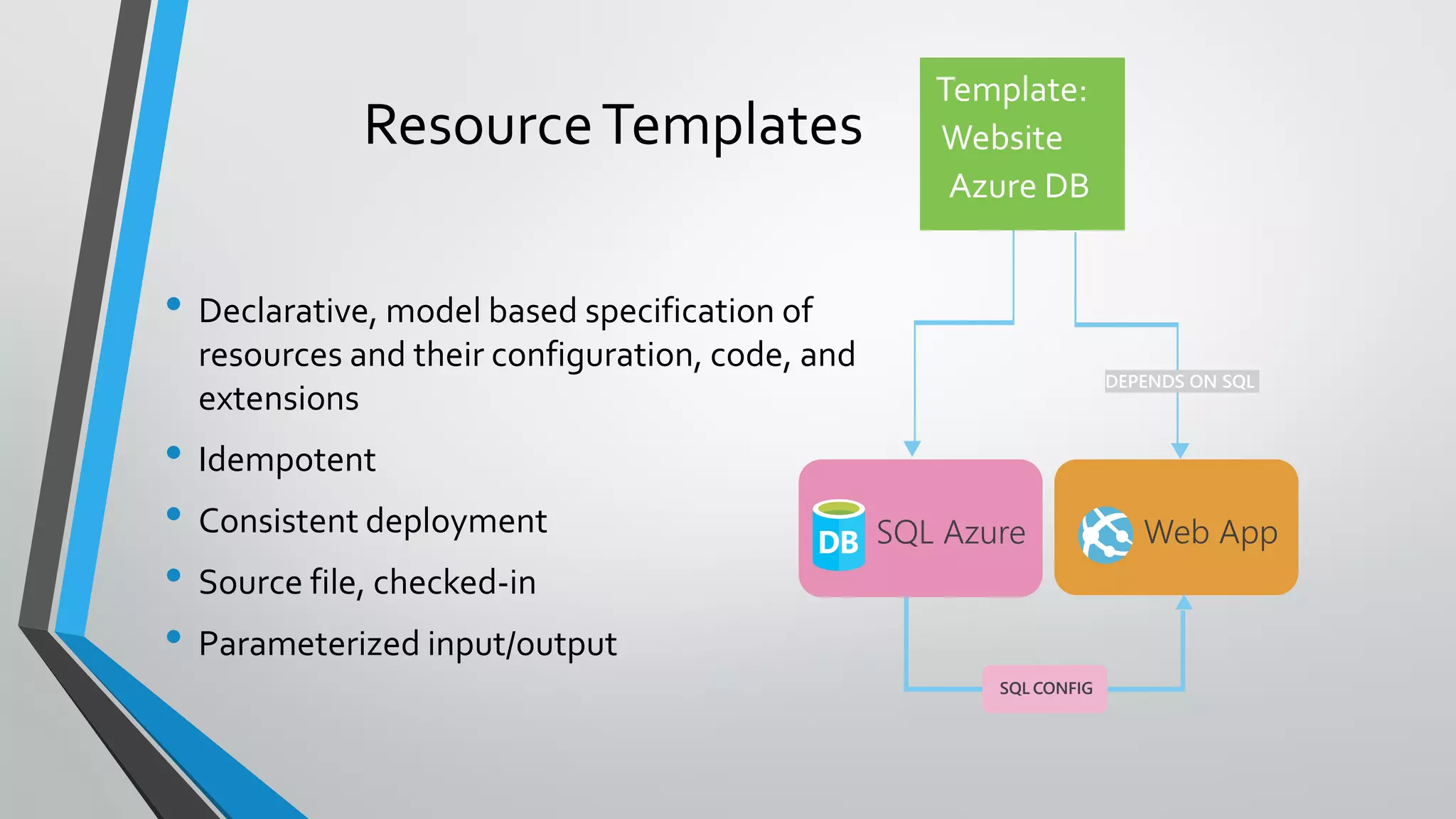
- ARM templates define the deployment of Azure resources through a JSON file, allowing deployments to be automated, repeatable, and easy to manage.
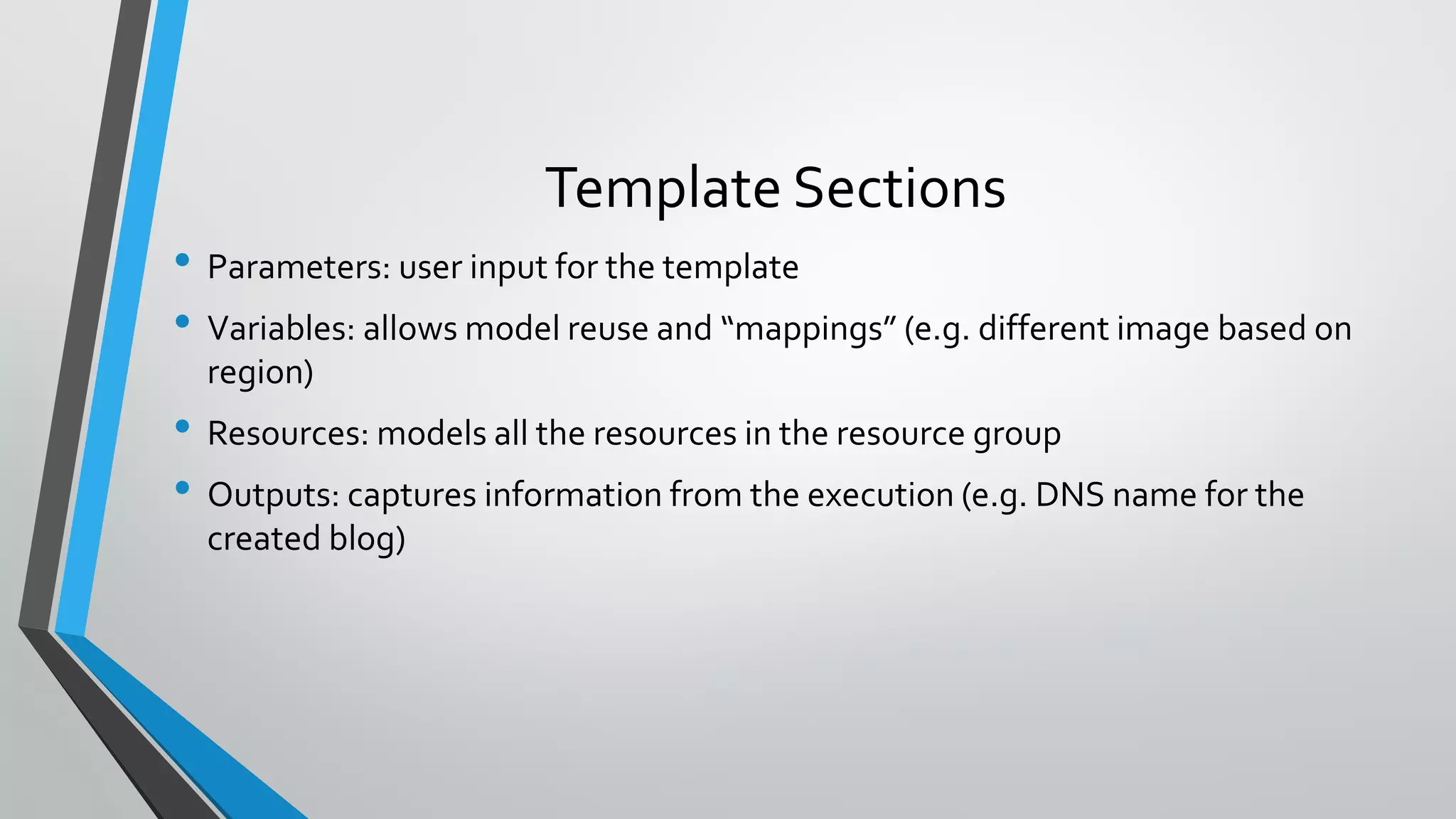
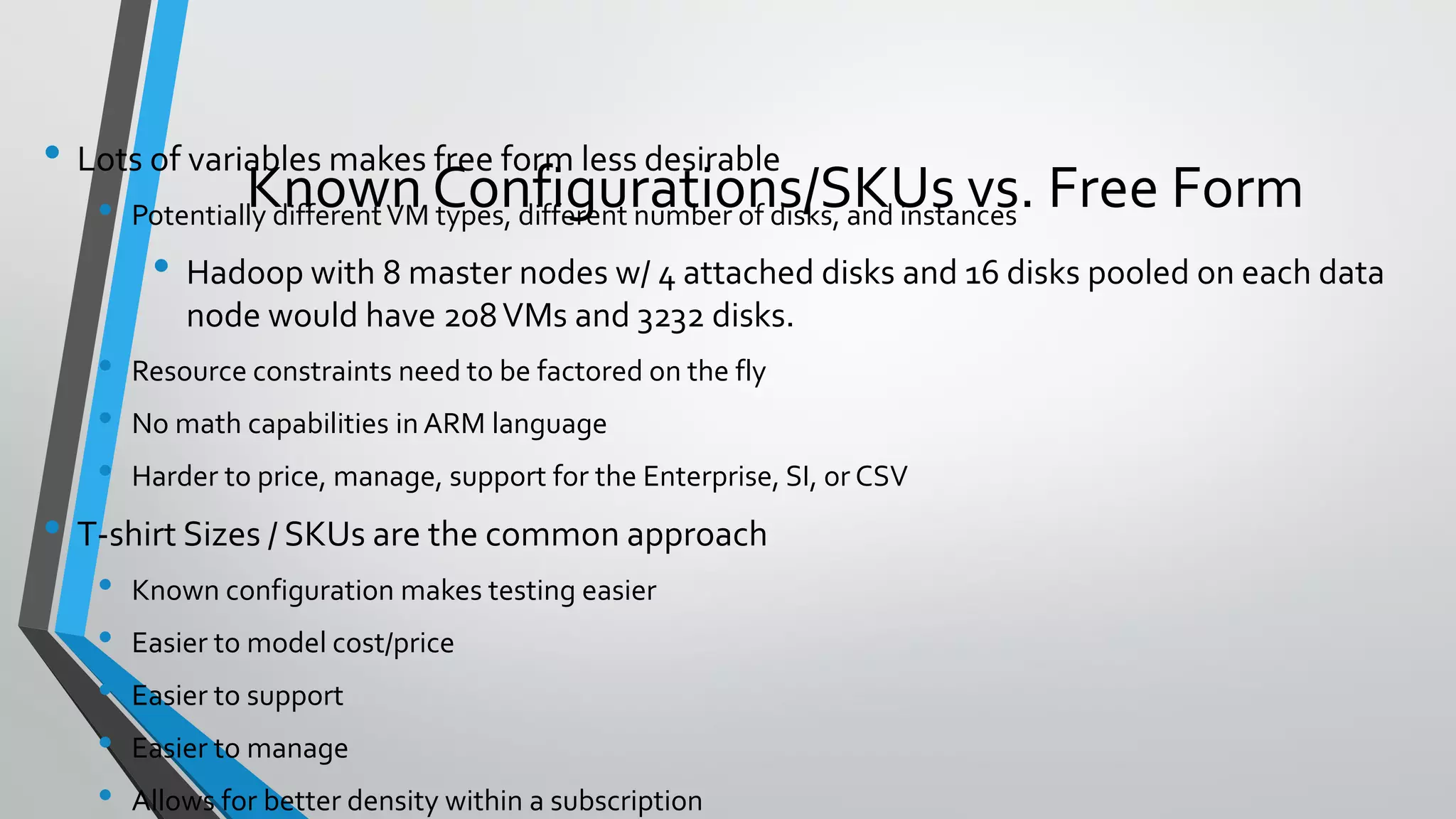
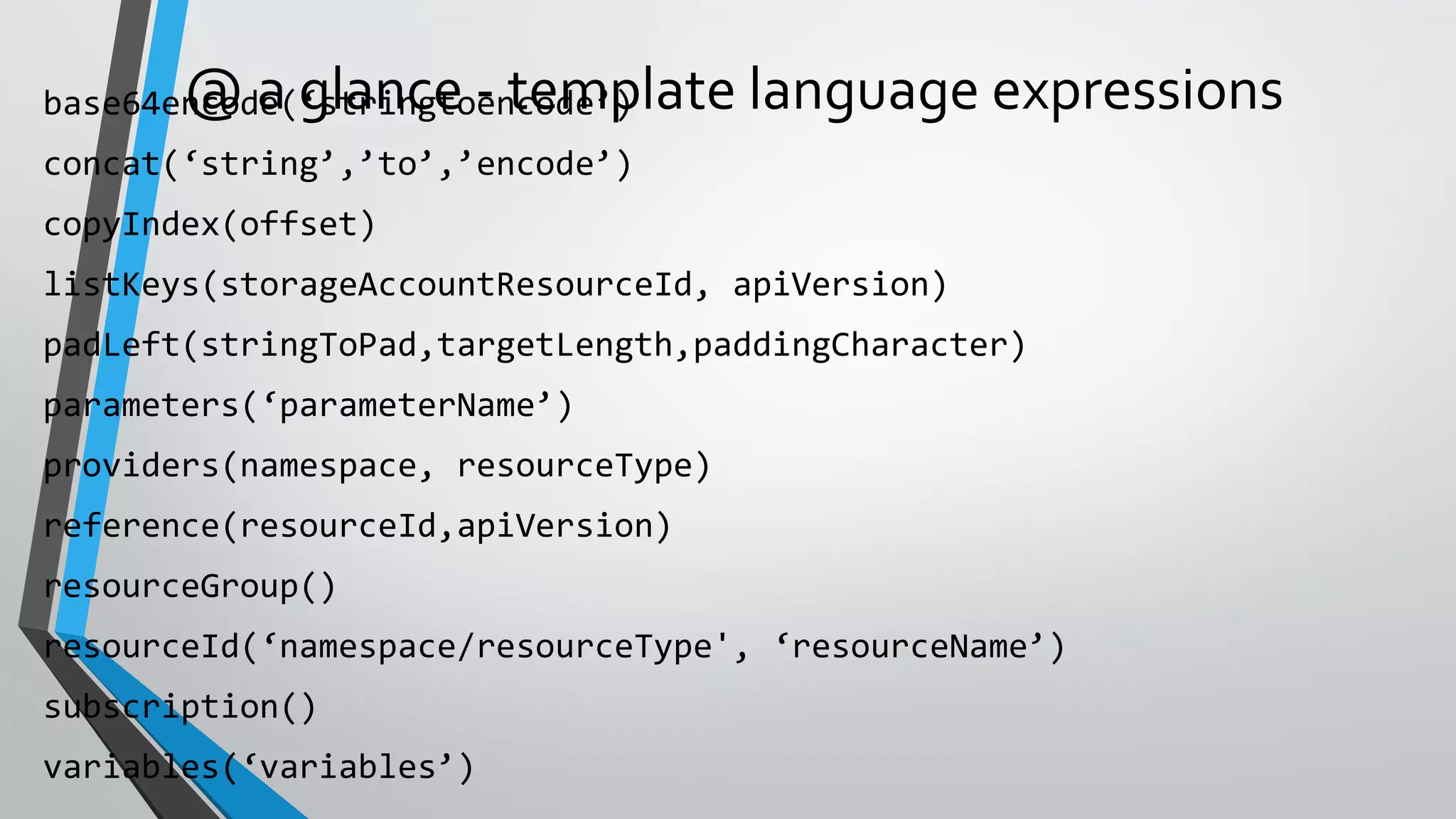
- Templates use parameters for user input, variables for reuse, and outputs to capture deployment results. Expressions allow dynamic values.
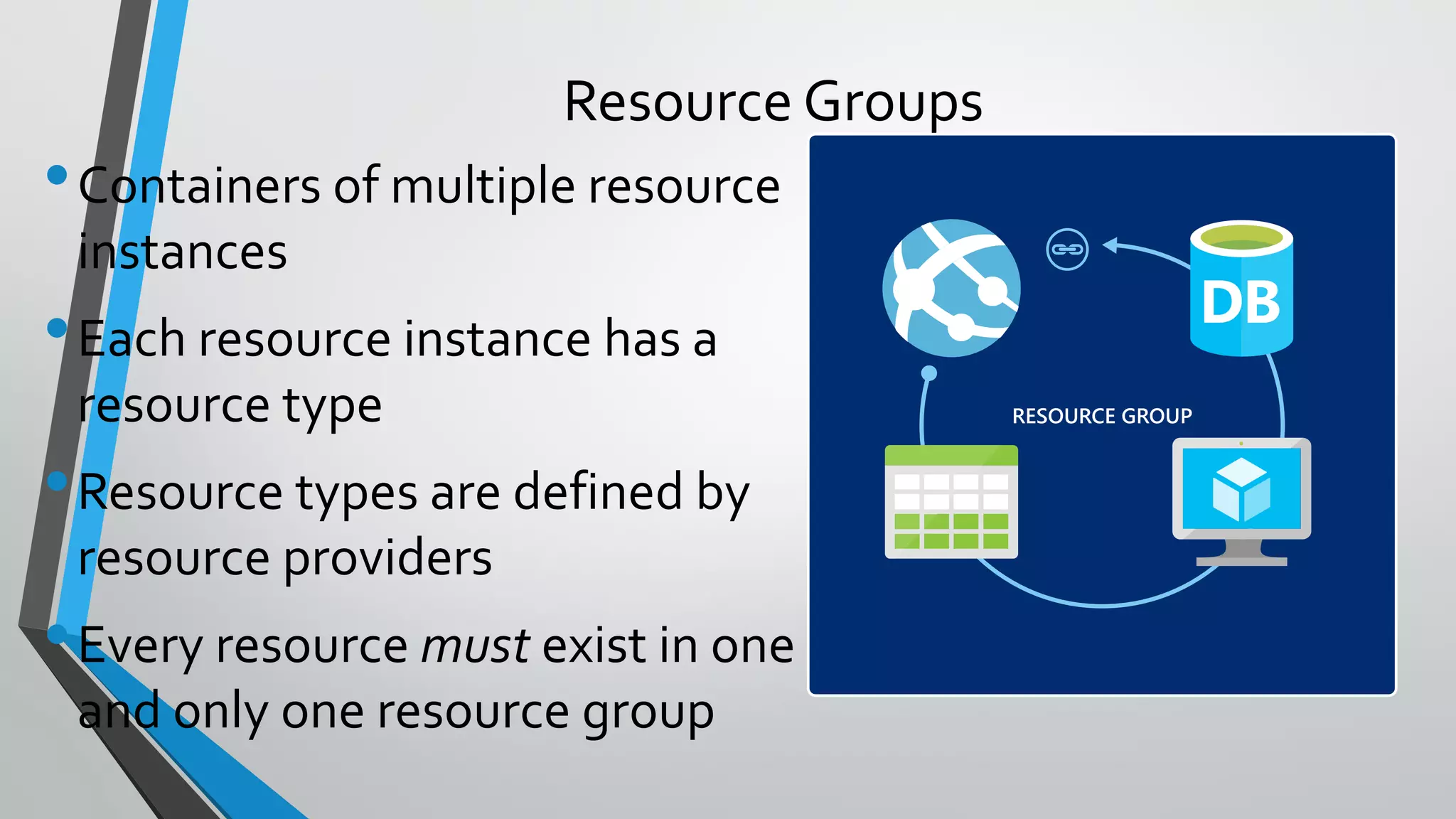
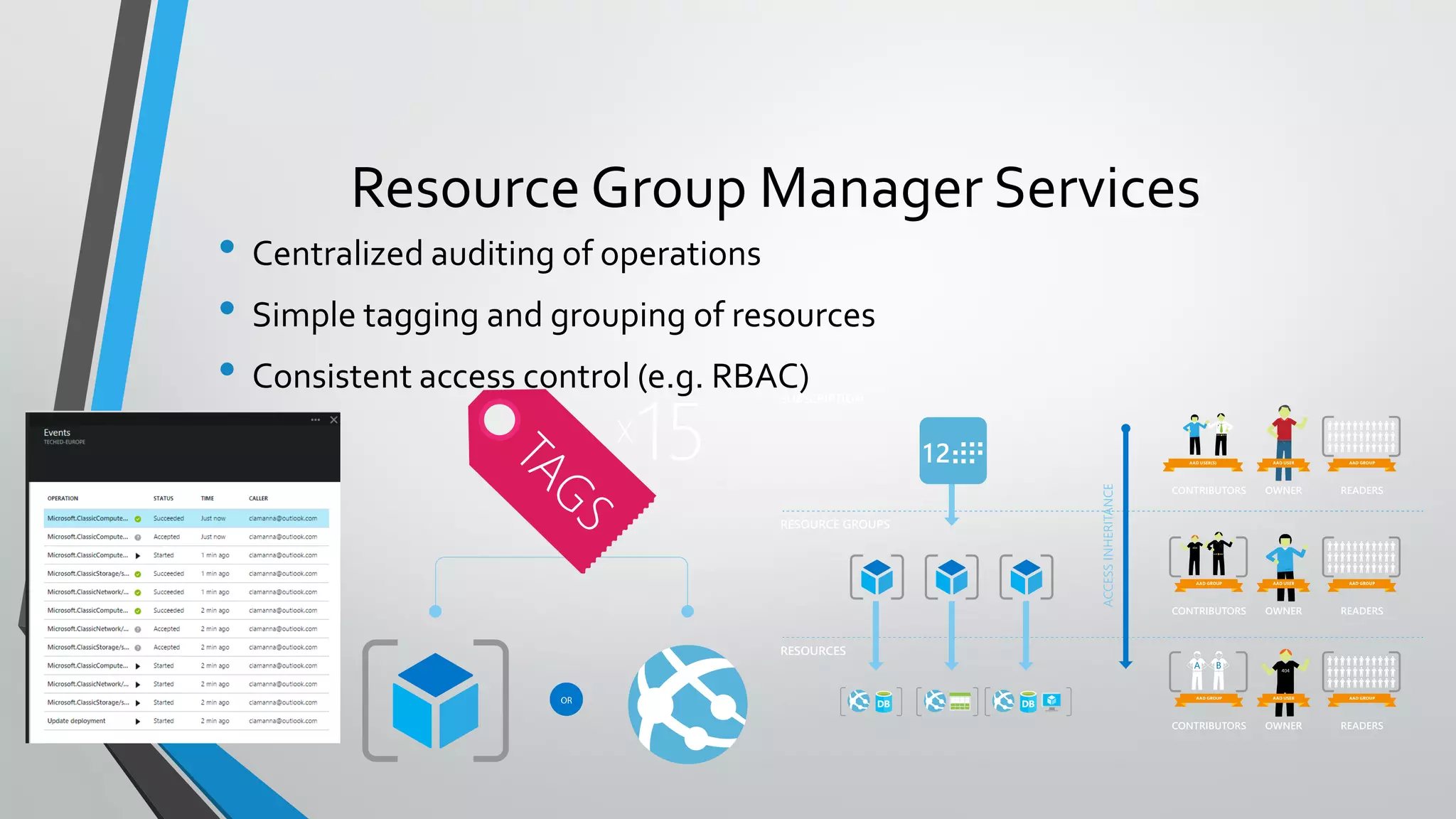
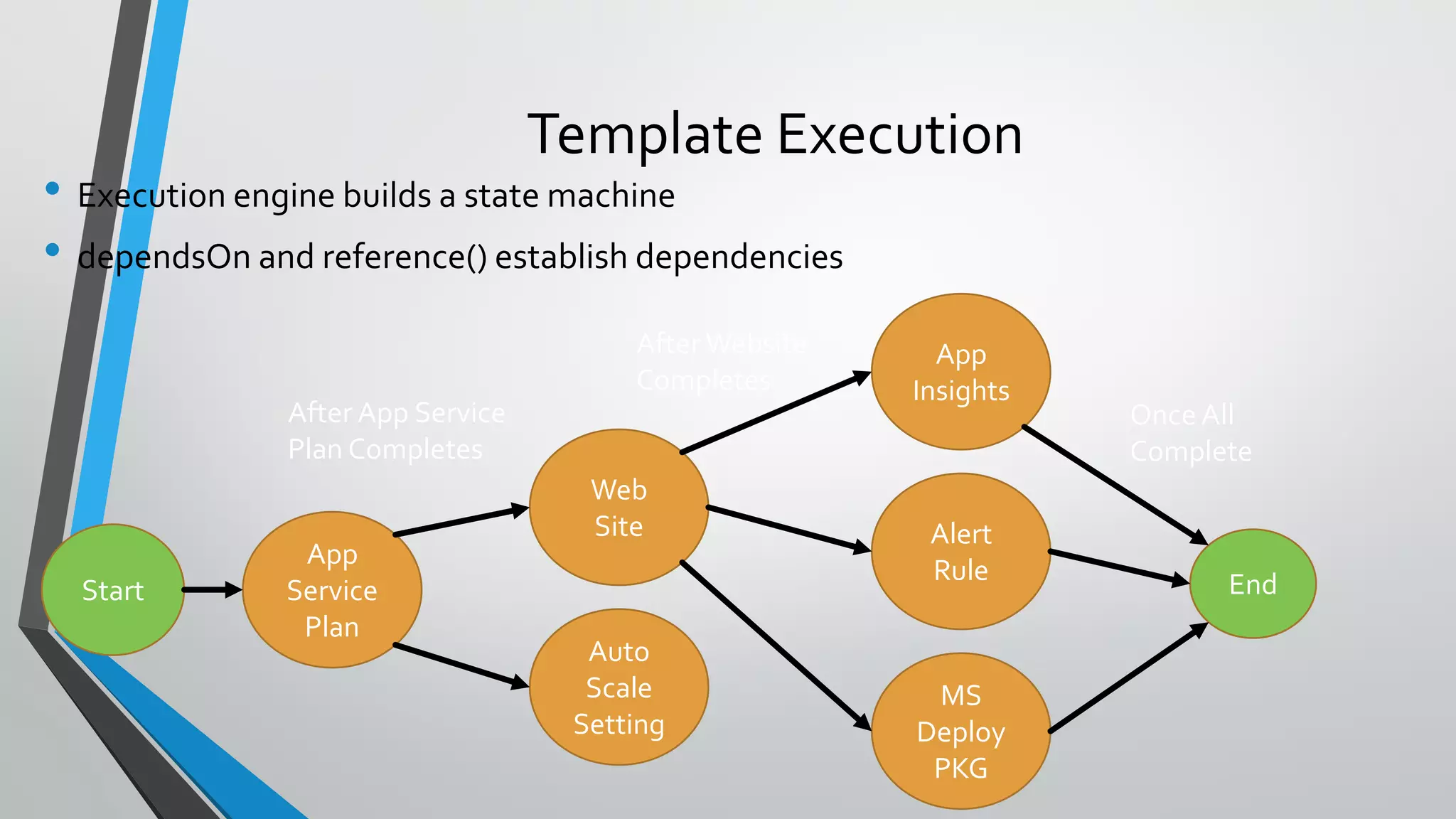
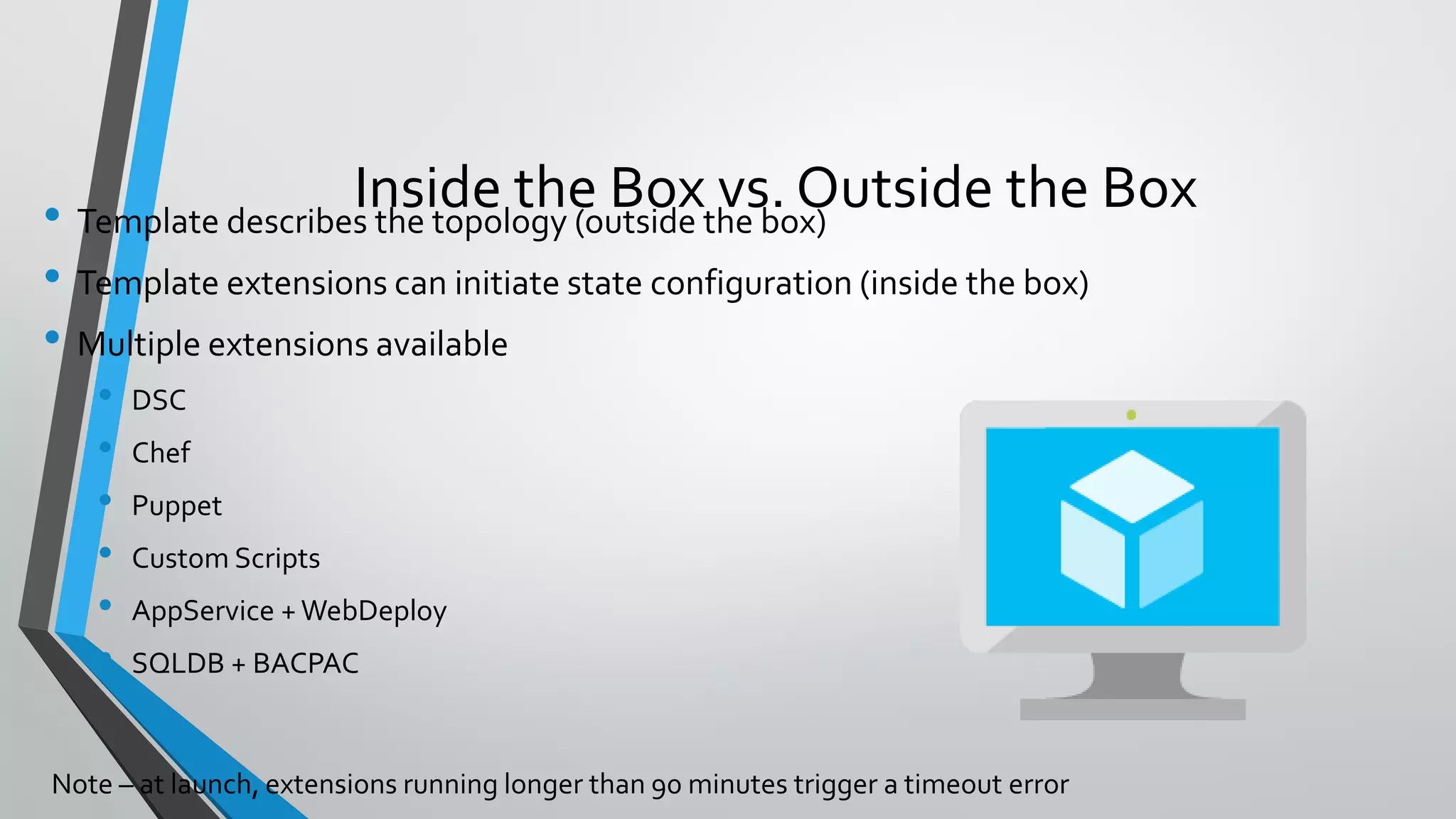
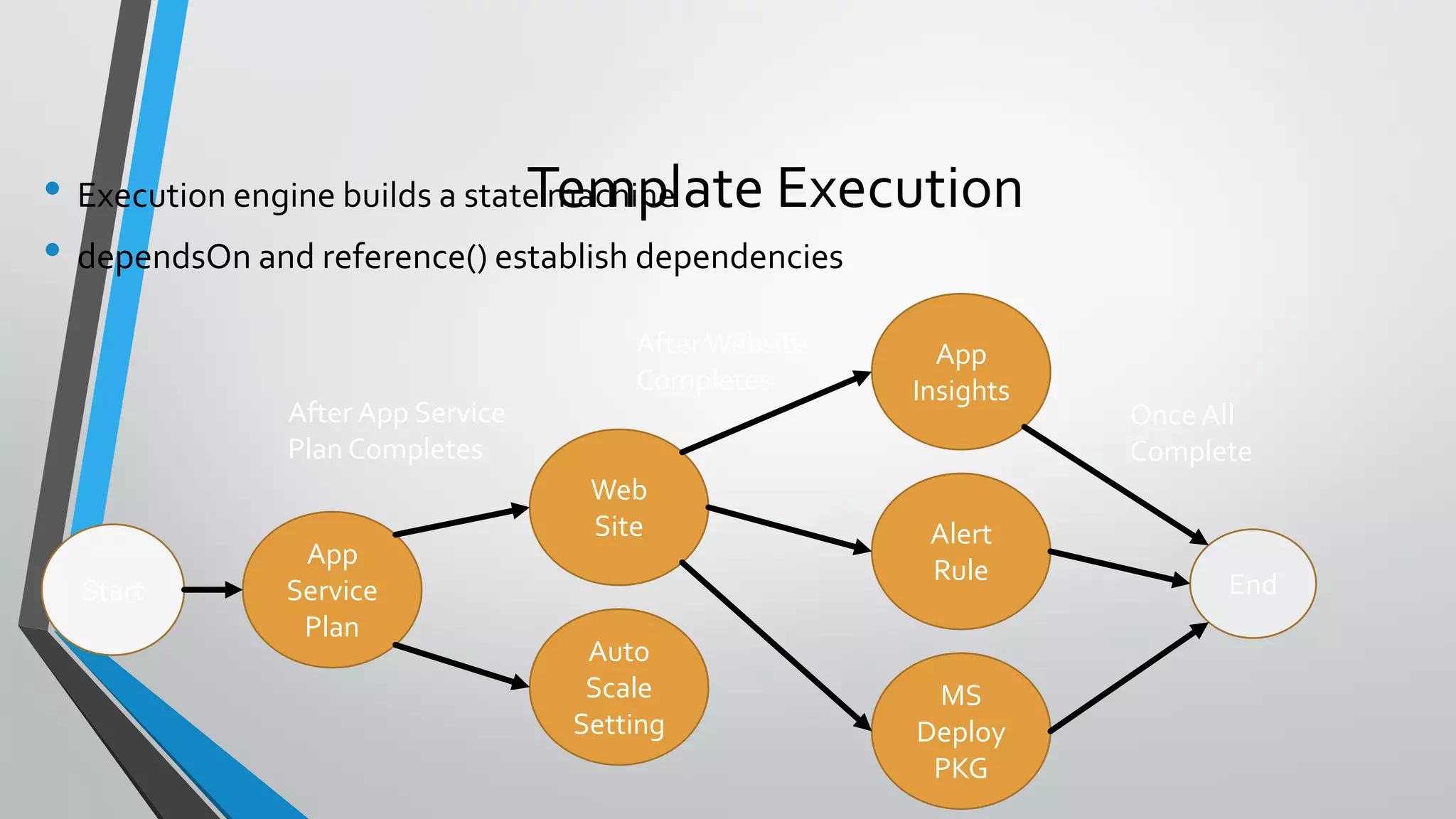
- Template execution establishes dependencies between resources through functions like dependsOn and reference.
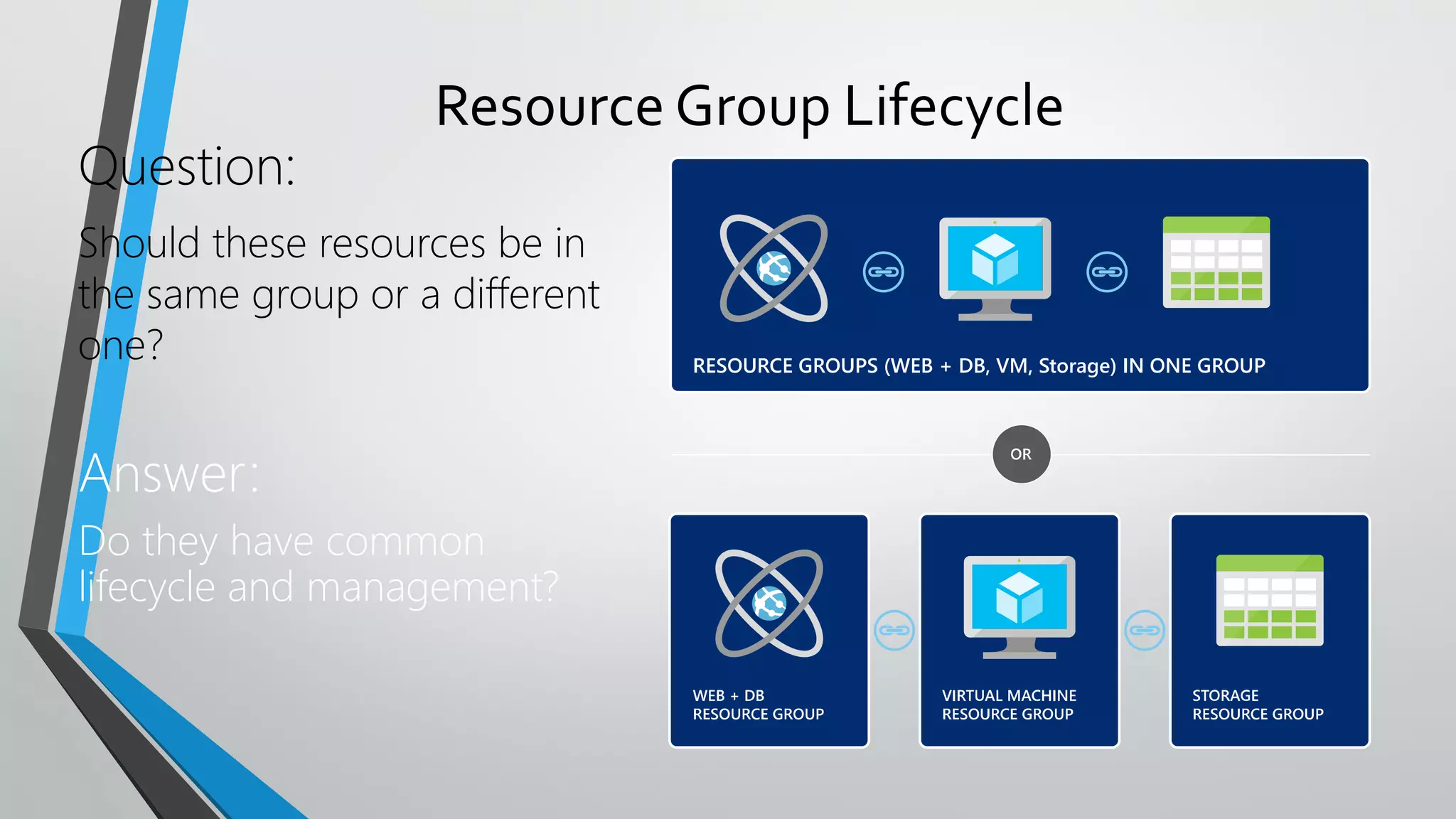
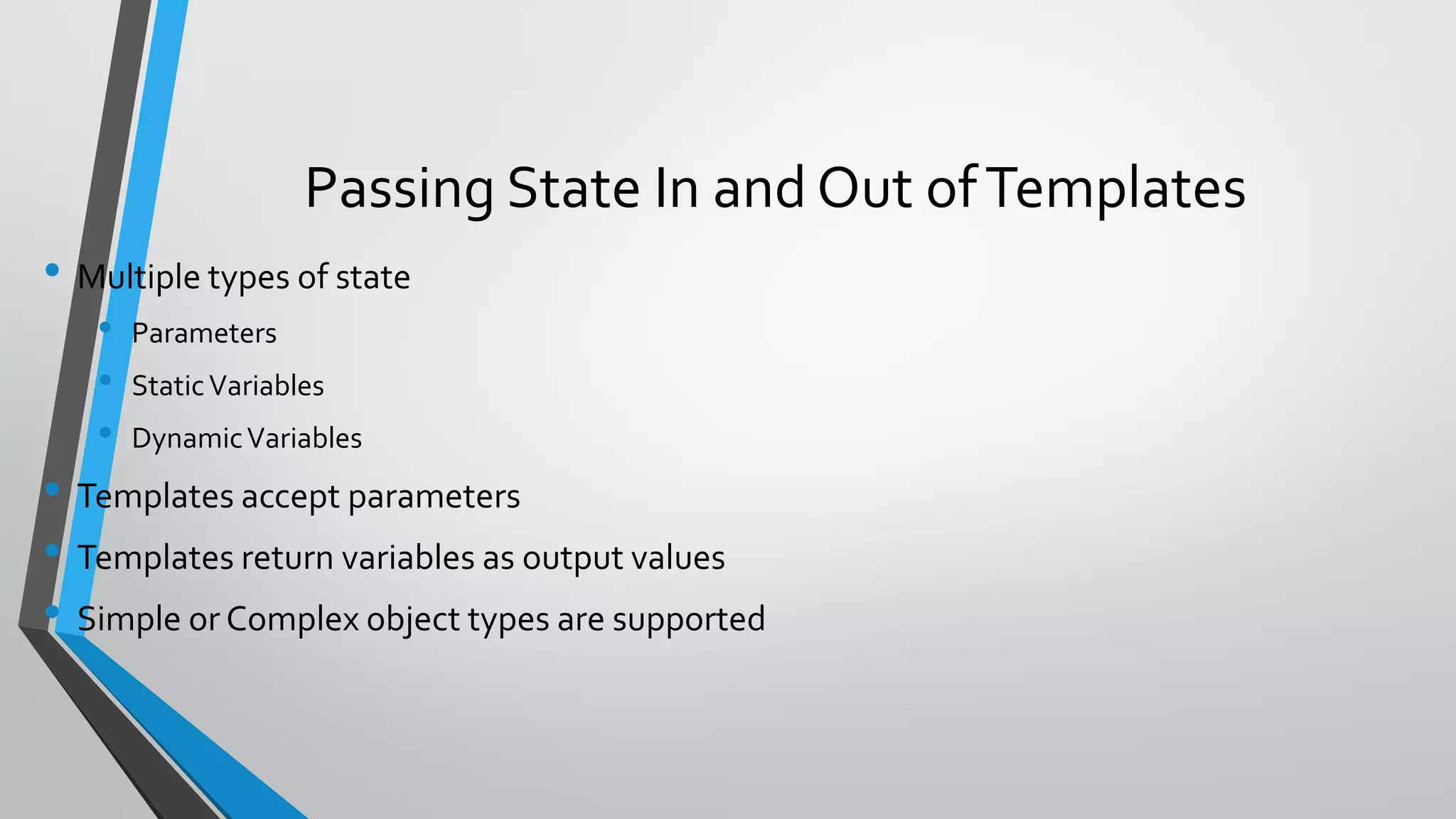
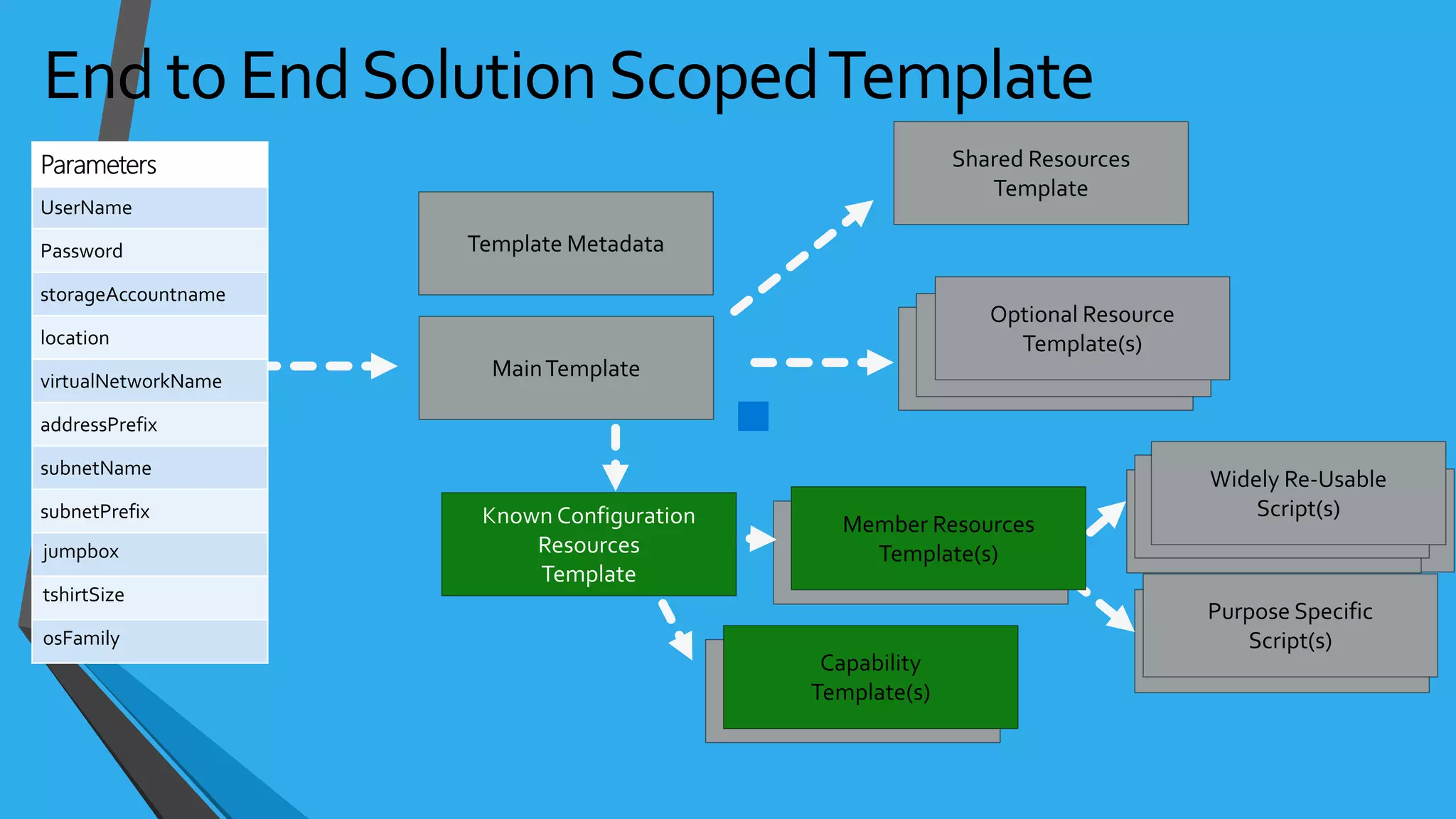
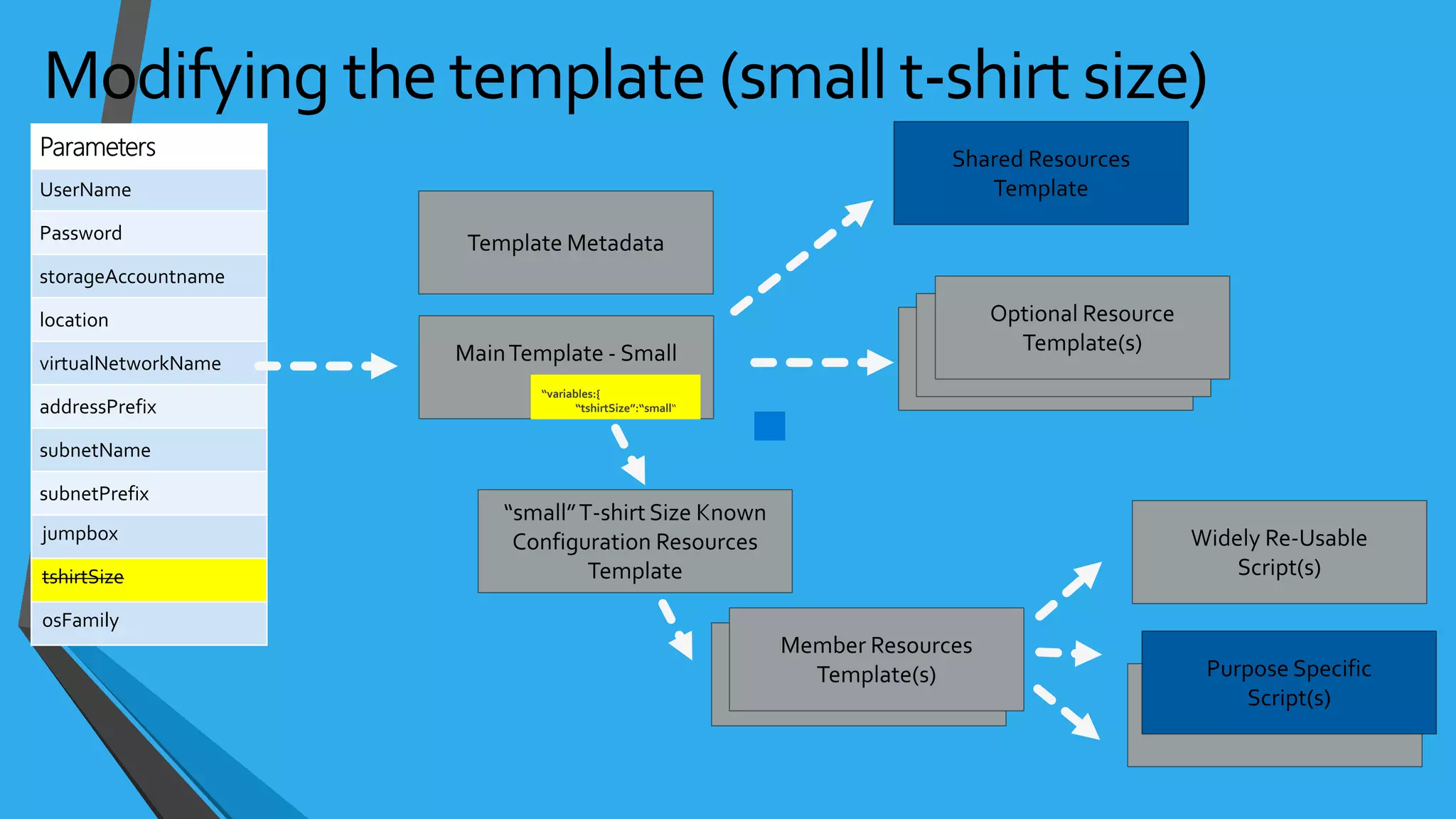
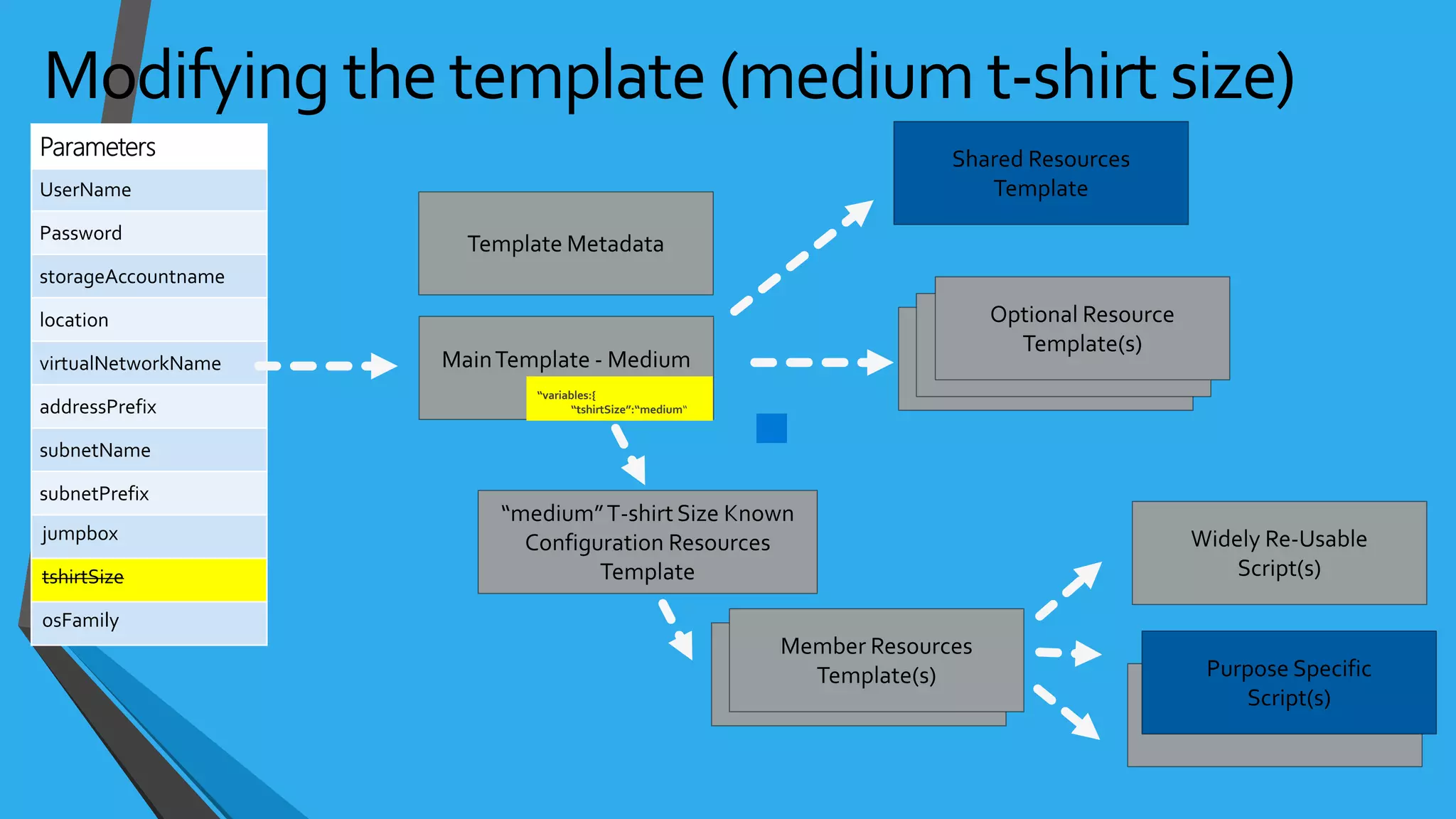
- Templates can be linked to decompose deployments and allow reuse of common configurations. State can be passed between templates through parameters, variables, and outputs.






![• Functions are delimited by “[{dsl keyword}]”
• E.g. “name”: “[concat(‘foo’, parameters(‘p1’))]
• Basic functions:
• concat() -- “[concat(‘foo’,’bar’)]” = foobar
• variable() – “[variable(‘foo’)]” = variables “foo” value
• reference() – “[reference(‘VM1’). IpAddress]”
• parameters() – “[parameters(‘blogName’)]”
Template DSL](https://image.slidesharecdn.com/cnamazurezecloudresourcemanager-160120170505/75/Cnam-azure-ze-cloud-resource-manager-17-2048.jpg)

![{ "apiVersion": "2015-05-01-preview",
"type": "Microsoft.Compute/virtualMachines",
"name": "[concat(parameters('vmNamePrefix'), copyindex())]",
"location": "[parameters('location')]",
"copy": {
"name": "virtualMachineLoop",
"count": "[parameters('numberOfInstances')]"
},
"dependsOn": [
"[concat('Microsoft.Network/networkInterfaces/', 'nic', copyindex())]"
],
"properties": {
"hardwareProfile": {
"vmSize": "[parameters('vmSize')]"
},
"osProfile": {
"computername": "[concat('vm', copyIndex())]",
"adminUsername": "[parameters('adminUsername')]",
"adminPassword": "[parameters('adminPassword')]"
},
"storageProfile": {
"osDisk": {
"name": "[concat(parameters('vmNamePrefix'),'-osDisk',copyindex())]",
"osType": "[parameters('osType')]",
"caching": "ReadWrite",
"image": {
"uri": "[variables('userImageName')]"
},
"vhd": {
"uri":
"[concat(variables('osDiskVhdContainer'),parameters('vmNamePrefix'),copyindex(),'osDisk.vhd'
)]"
}
• Resource loops deploy n instances
• Fixed or parameter
driving instance count
• Concat + Parameter Prefix +
CopyIndex() for dynamic naming
Deploying Multiple Instances](https://image.slidesharecdn.com/cnamazurezecloudresourcemanager-160120170505/75/Cnam-azure-ze-cloud-resource-manager-24-2048.jpg)
![• Provides the ability to link multiple templates
• Can be used to facilitate decomposition
• Template URIs can be dynamic
• Allows for re-use
Template Linking
{ "name": "cluster-nodes",
"type":
"Microsoft.Resources/deployments",
"apiVersion": "2015-01-01",
"dependsOn": [
"[concat('Microsoft.Resources/deployments/',
'shared')]"
],](https://image.slidesharecdn.com/cnamazurezecloudresourcemanager-160120170505/75/Cnam-azure-ze-cloud-resource-manager-25-2048.jpg)
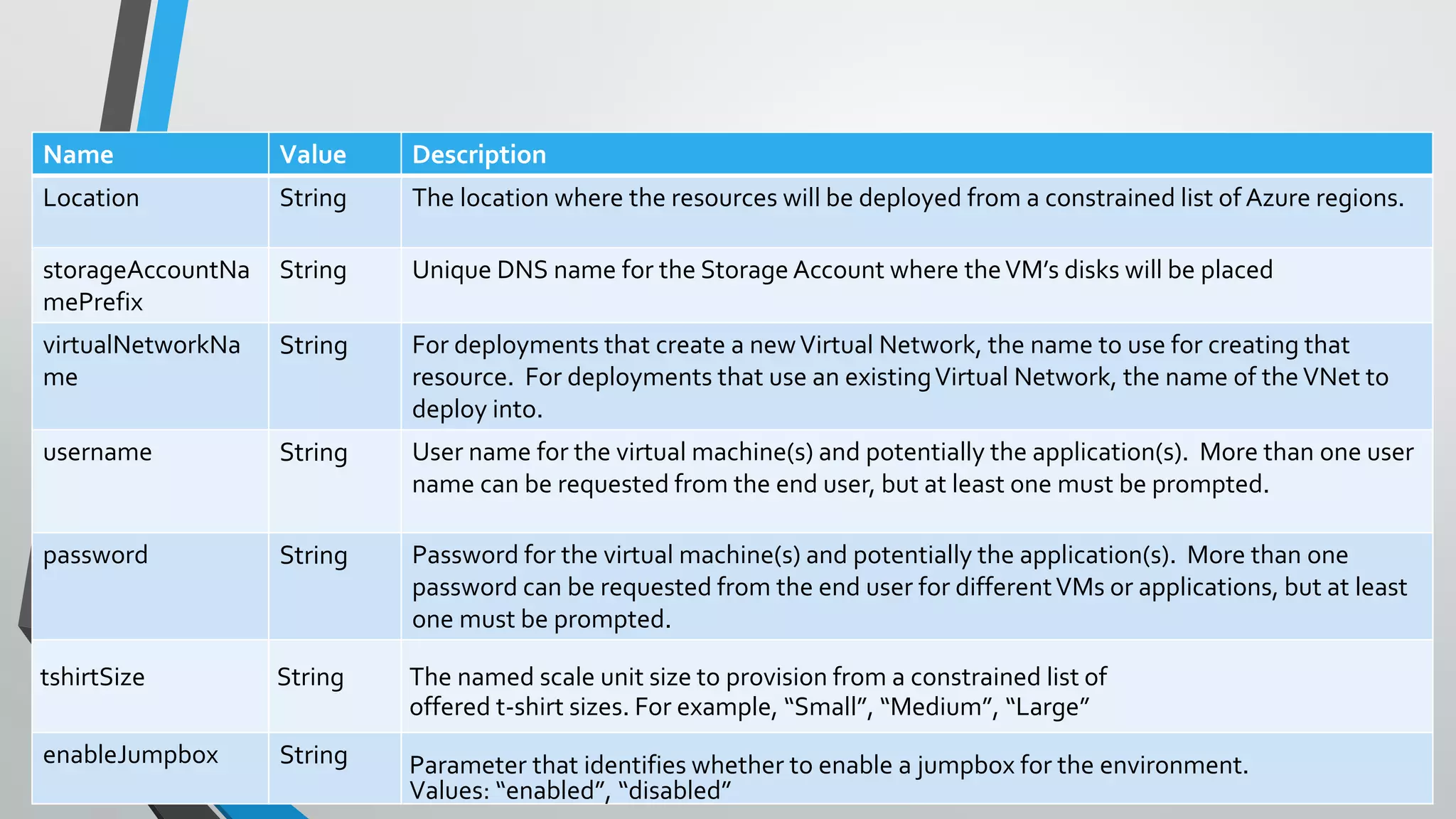
![•Easier to pass a number of related values with a
single variable
•Object.Property approach provides additional
context when reading the template
Examples
Passing State - Complex Objects
"networkSettings": {
"vnetName": "[parameters('virtualNetworkName')]",
"addressPrefix": "10.0.0.0/16",
"subnets": {
"dmz": {
"name": "dmz",
"prefix": "10.0.0.0/24",
"vnet": "[parameters('virtualNetworkName')]"
},
"data": {
"name": "data",
"prefix": "10.0.1.0/24",
"vnet": "[parameters('virtualNetworkName')]"
}
"osSettings": {
"imageReference": {
"publisher": "Canonical",
"offer": "UbuntuServer",
"sku": "14.04.2-LTS",
"version": "latest"
}
"tshirtSizeSmall": {
"vmSize": "Standard_A1",
"diskSize": 1023,
"vmTemplate": "[concat(variables('templateBaseUrl'),
'database-2disk-resources.json')]",
"vmCount": 2,
"storage": {
"name": "[parameters('storageAccountNamePrefix')]",
"count": 1,
"pool": "db",
"map": [0,0],
"jumpbox": 0
}
},
"availabilitySetSettings": {
"name": "pgsqlAvailabilitySet",
"fdCount": 3,
"udCount": 5
}](https://image.slidesharecdn.com/cnamazurezecloudresourcemanager-160120170505/75/Cnam-azure-ze-cloud-resource-manager-28-2048.jpg)
![• A template can return values to its caller via the outputs section
• These values can then be used by the caller
Passing State – Output variables
"outputs": {
"masterip": {
"value":
"[reference(concat(variables('nicName'),0)).ipConfigurations[0].properties.privat
ress]",
"type":"string"
}}
"masterIpAddress": {
"value":
"[reference('master-node').outputs.masterip.value]"
} }](https://image.slidesharecdn.com/cnamazurezecloudresourcemanager-160120170505/75/Cnam-azure-ze-cloud-resource-manager-29-2048.jpg)
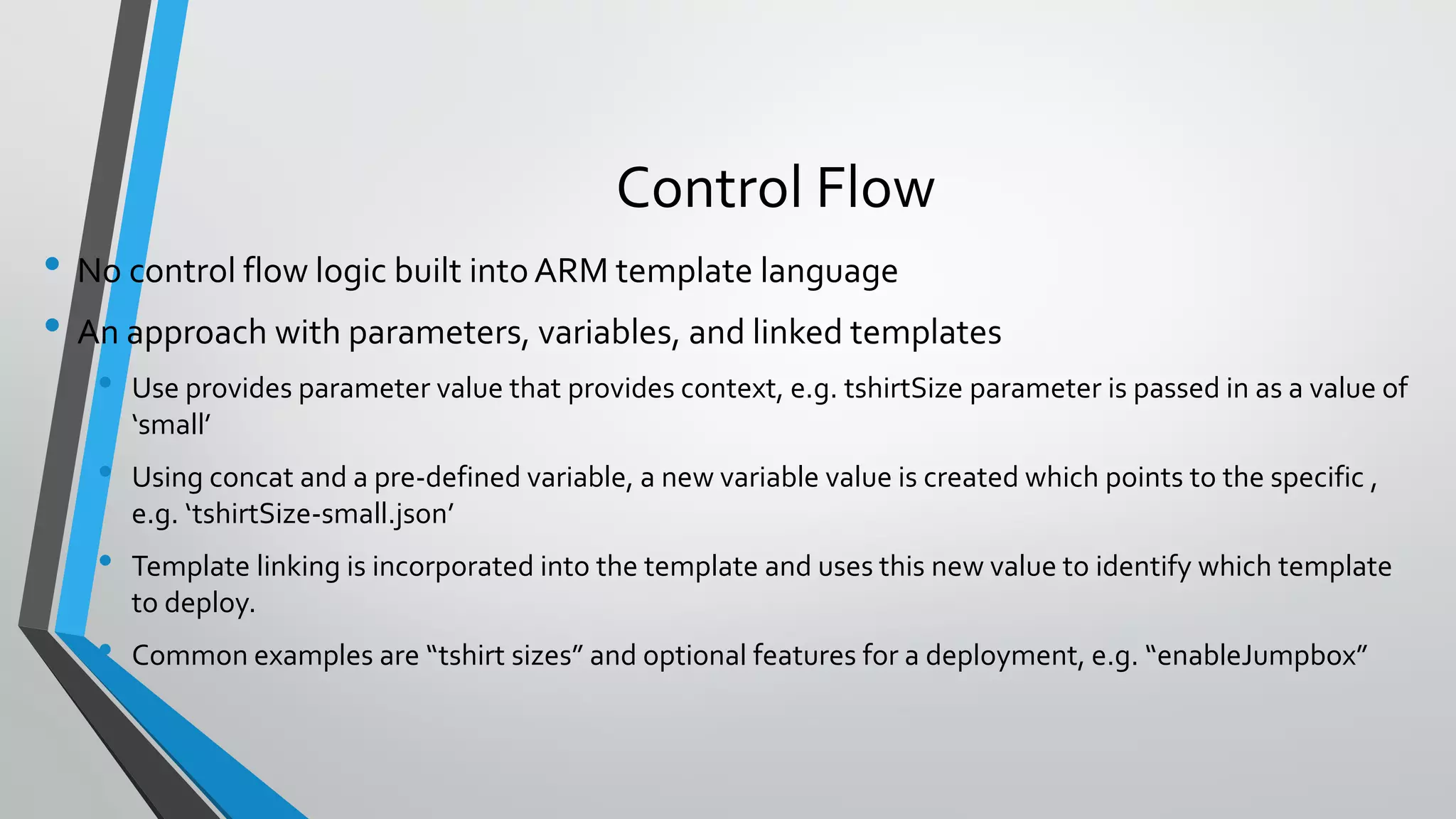
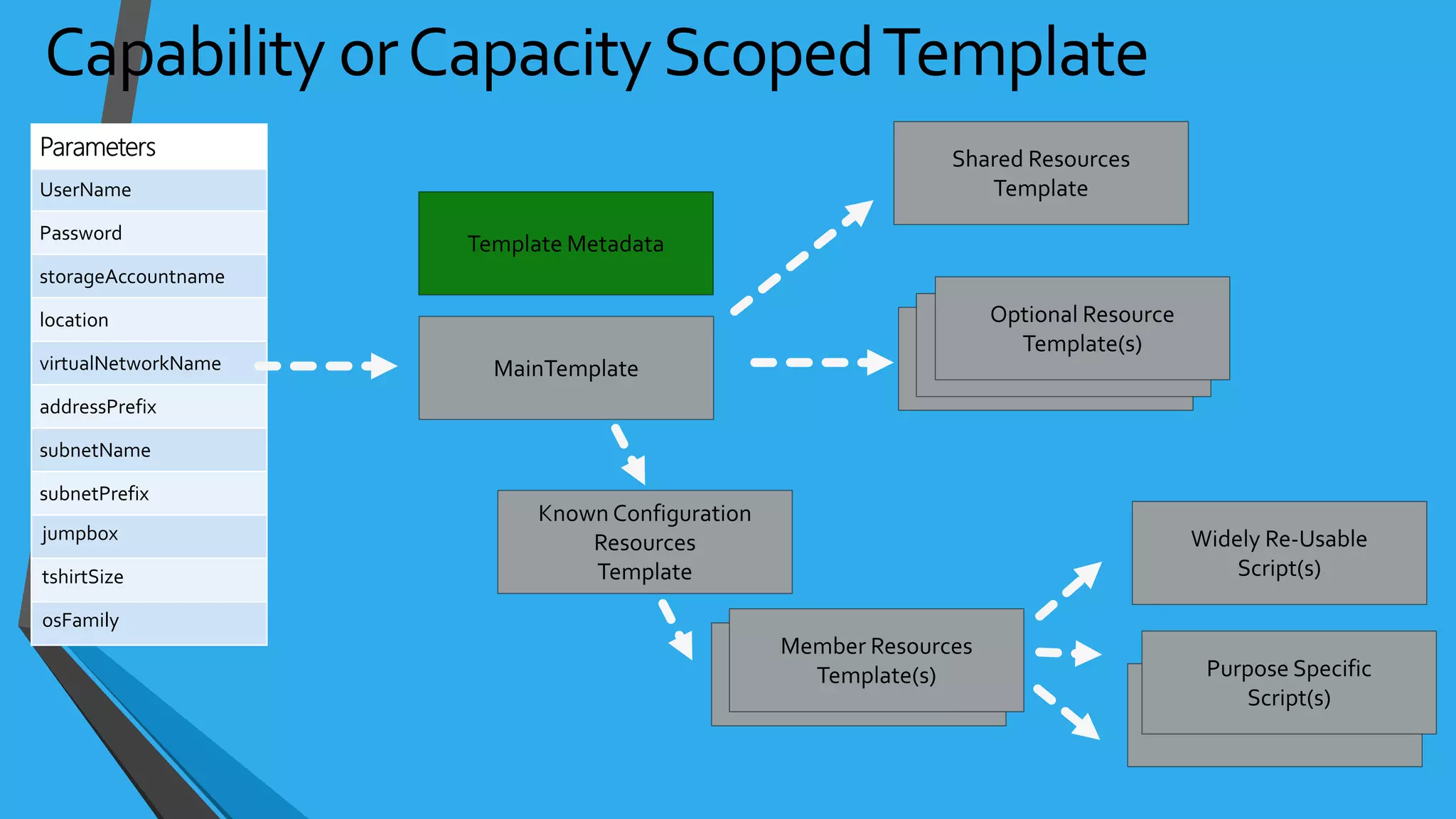
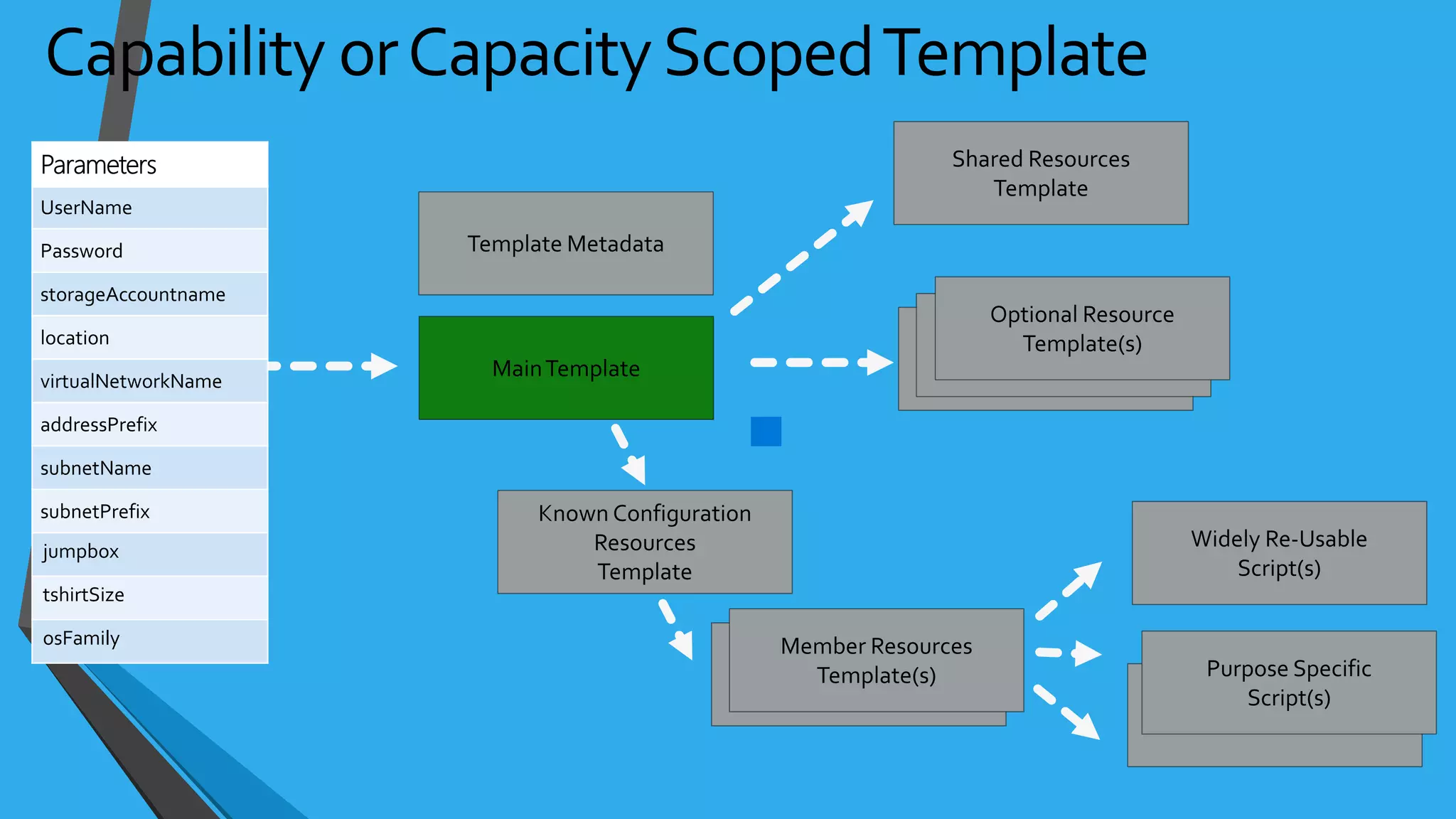
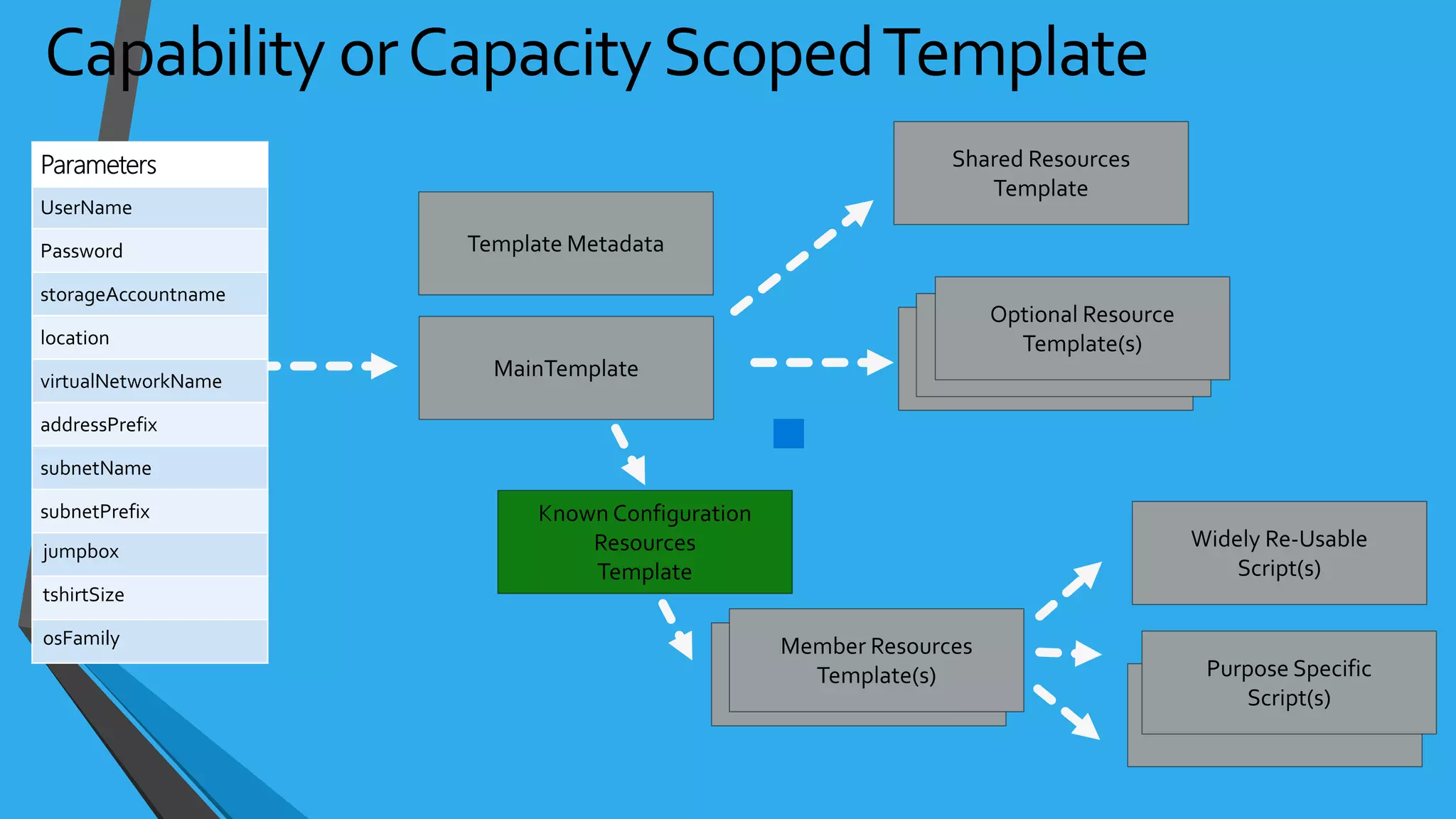
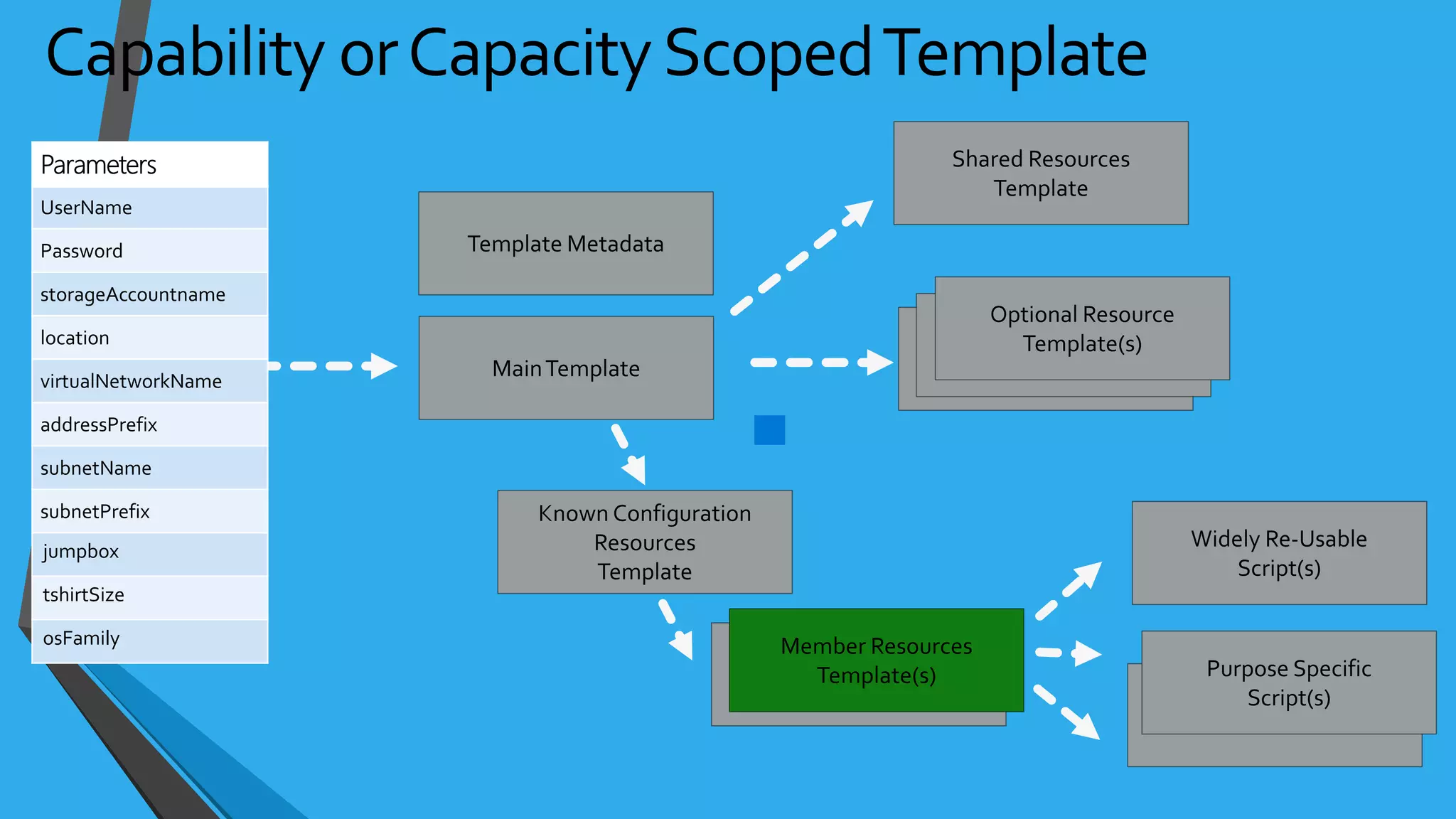
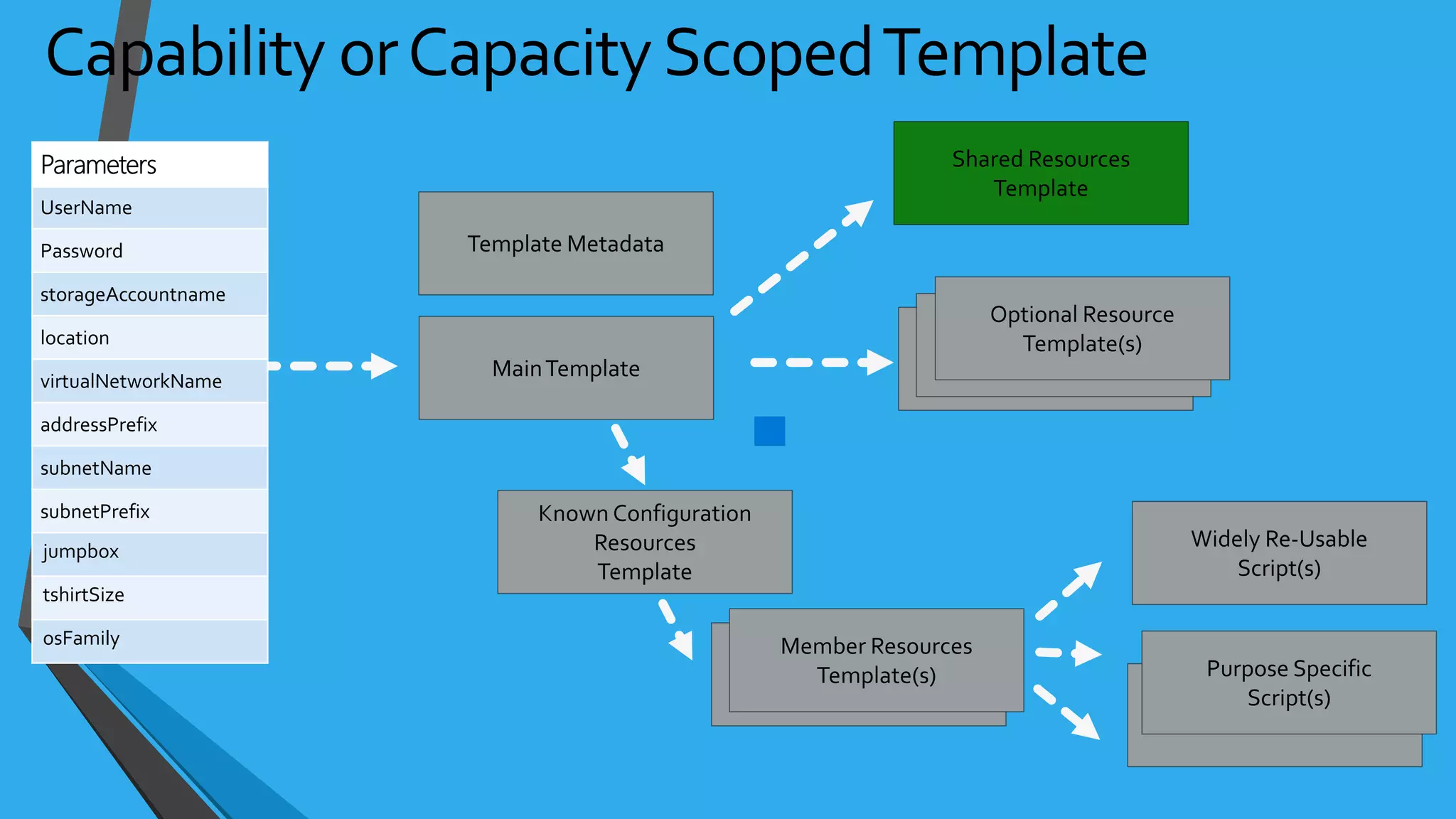
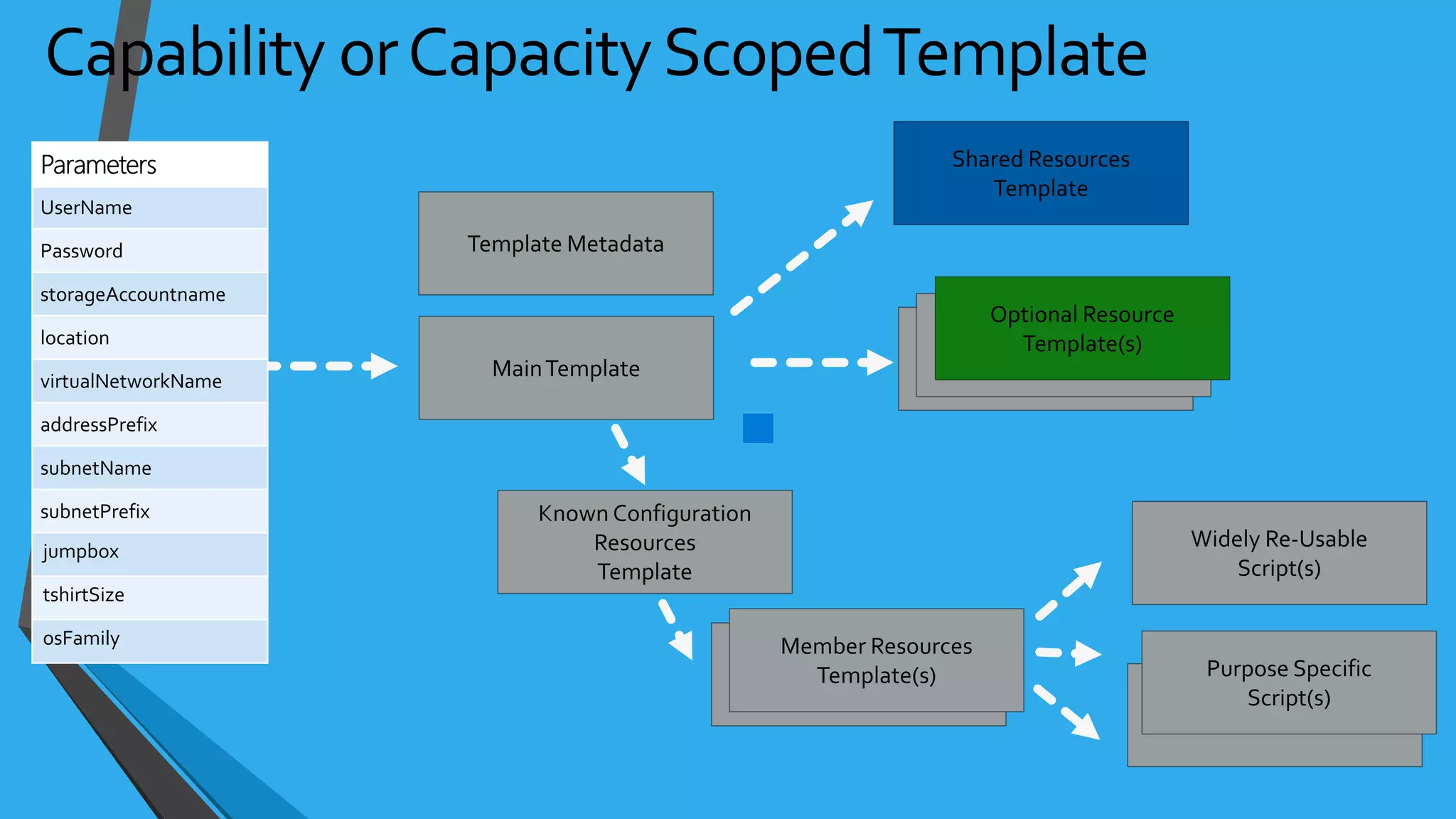
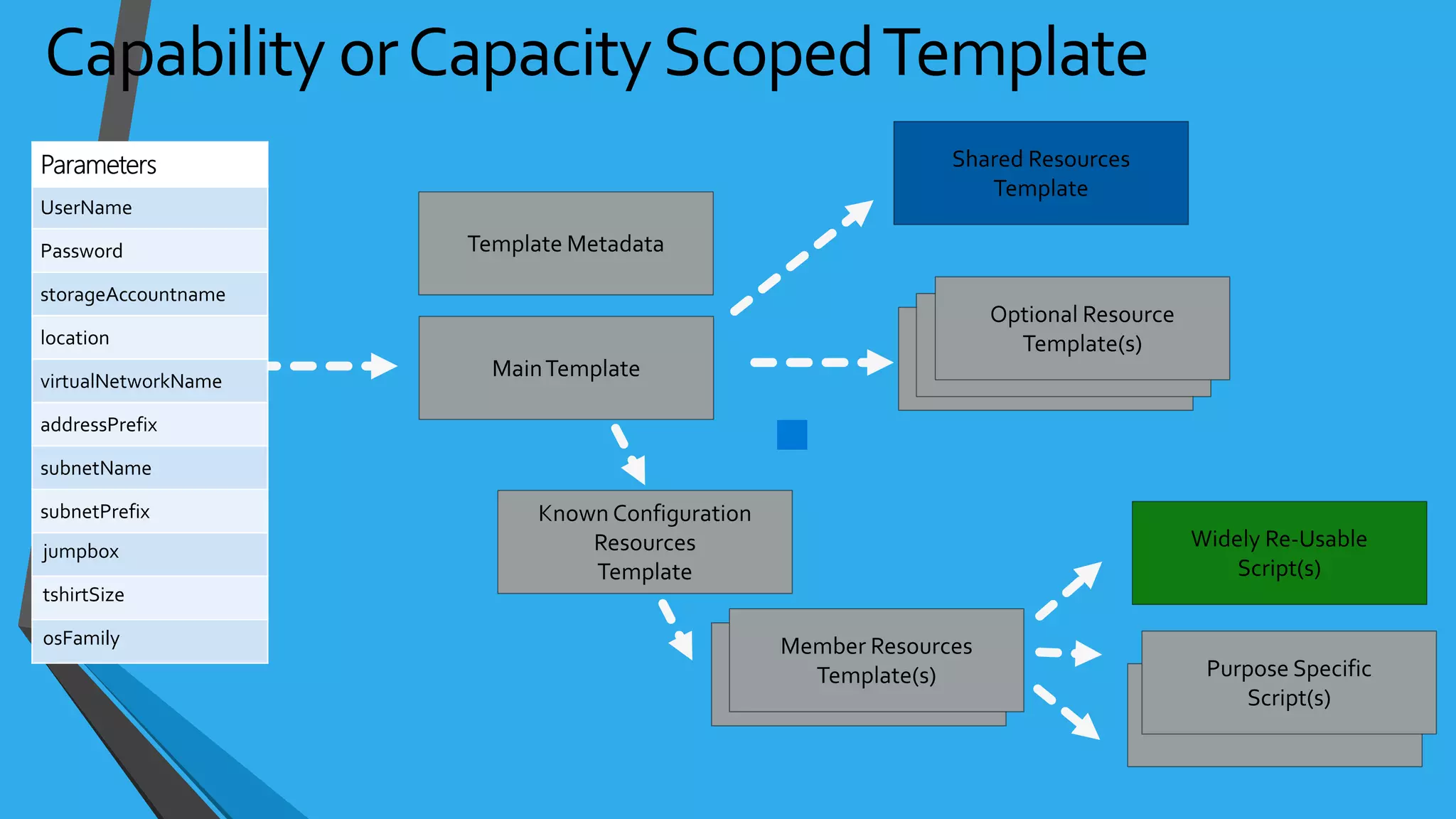
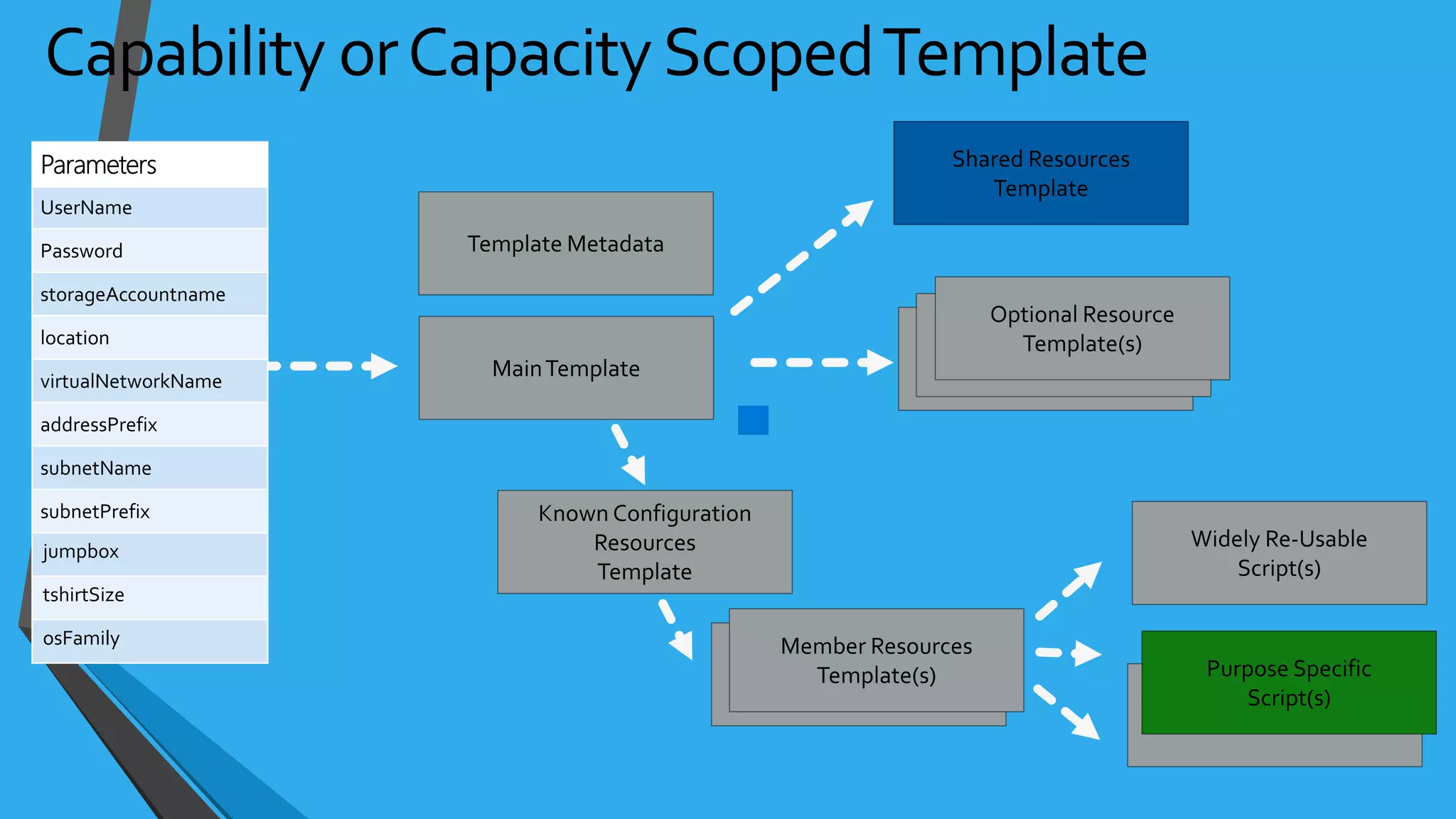





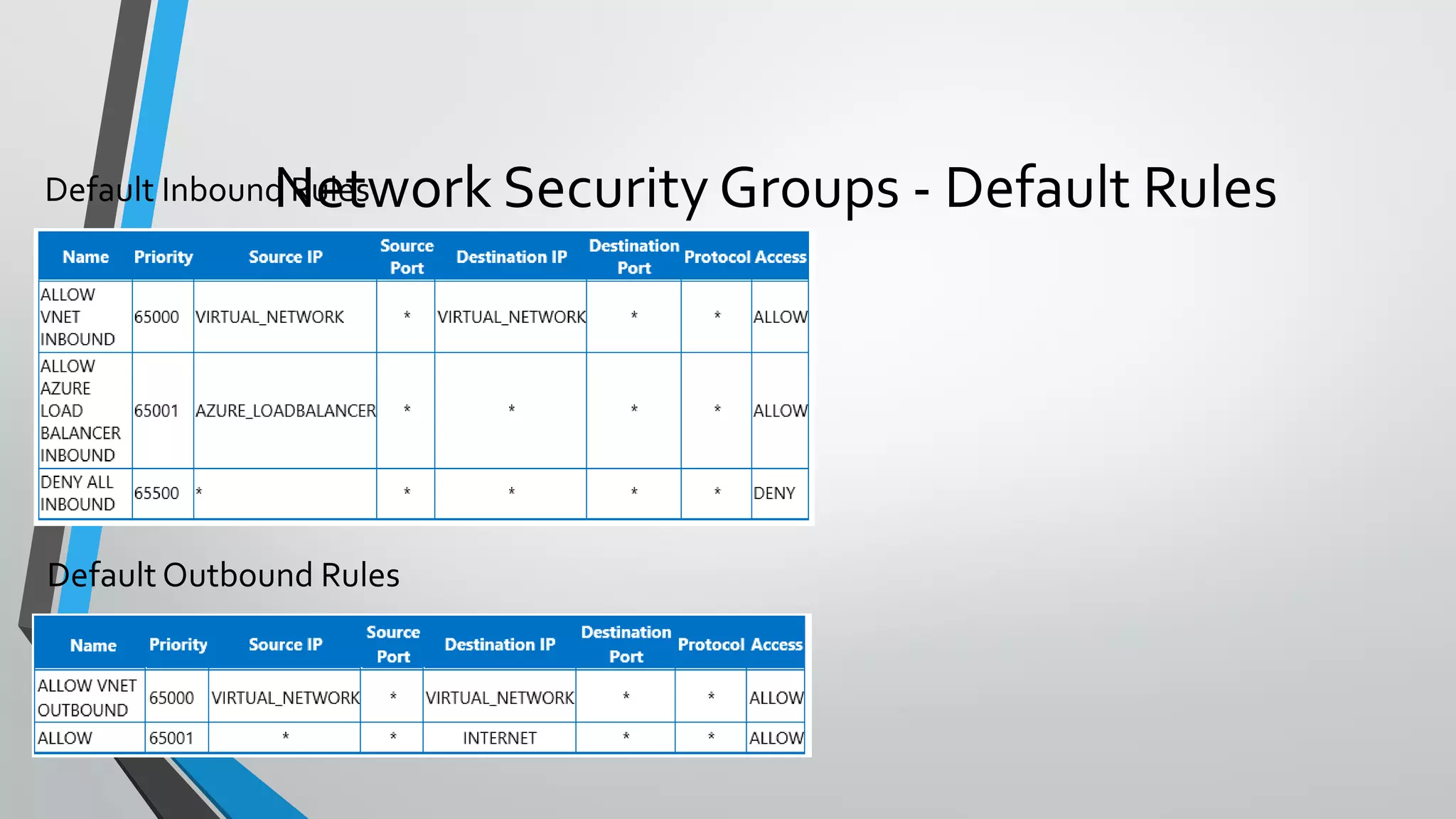
![NSG Examples{
"apiVersion": "2015-05-01-preview",
"type": "Microsoft.Network/networkSecurityGroups",
"name": "[parameters('FENSGName')]",
"location": "[parameters('location')]",
"properties":
{
"securityRules": [
{
"name": "rdp_rule",
"properties":
{
"description": "Allow RDP",
"protocol": "Tcp",
"sourcePortRange": "*",
"destinationPortRange": "3389",
"sourceAddressPrefix": "Internet",
"destinationAddressPrefix": "*",
"access": "Allow",
"priority": 100,
"direction": "Inbound"
}
},
{
"name": "web_rule",
"properties": {
"description": "Allow WEB",
"protocol": "Tcp",
"sourcePortRange": "*",
"destinationPortRange": "80",
"sourceAddressPrefix": "Internet",
"destinationAddressPrefix": "*",
"access": "Allow",
"priority": 101,
"direction": "Inbound"
}
}
]
}
}
{
"apiVersion": "2015-05-01-preview",
"type": "Microsoft.Network/networkSecurityGroups",
"name": "[parameters('AppNSGName')]",
"location": "[parameters('location')]",
"properties": {
"securityRules": [{
"name": "Allow_FE",
"properties": {
"description": "Allow FE Subnet",
"protocol": "Tcp",
"sourcePortRange": "*",
"destinationPortRange": "443",
"sourceAddressPrefix": "10.0.0.0/24",
"destinationAddressPrefix": "*",
"access": "Allow",
"priority": 100,
"direction": "Inbound"
}
},
{
"name": "Block_RDP_Internet",
"properties": {
"description": "Block RDP",
"protocol": "tcp",
"sourcePortRange": "*",
"destinationPortRange": "3389",
"sourceAddressPrefix": "Internet",
"destinationAddressPrefix": "*",
"access": "Deny",
"priority": 101,
"direction": "Inbound"
}
},
{
"name": "Block_Internet_Outbound",
"properties": {
"description": "Block Internet",
"protocol": "*",
"sourcePortRange": "*",
"destinationPortRange": "*",](https://image.slidesharecdn.com/cnamazurezecloudresourcemanager-160120170505/75/Cnam-azure-ze-cloud-resource-manager-54-2048.jpg)