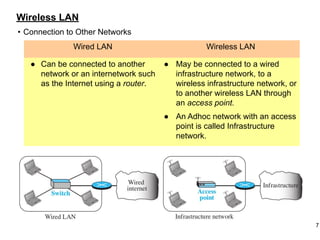
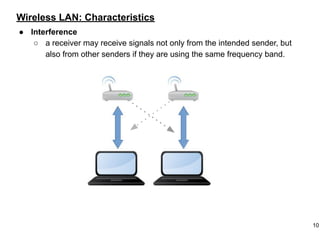
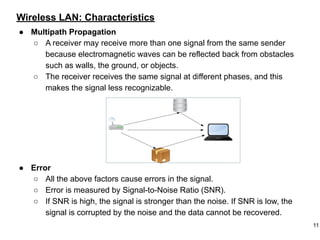
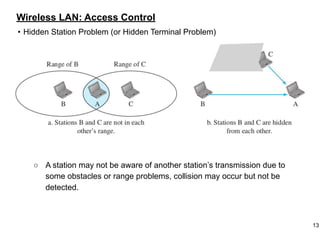
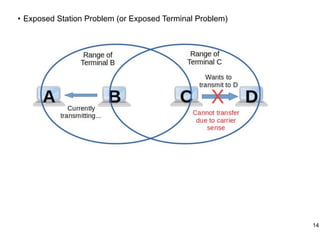
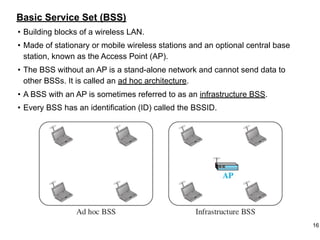
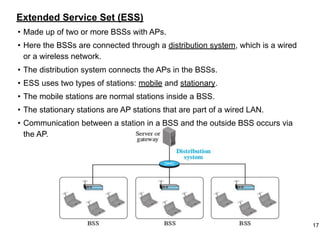
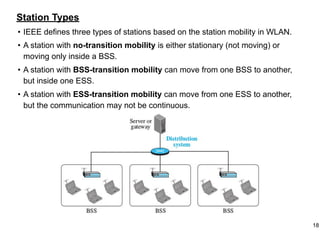
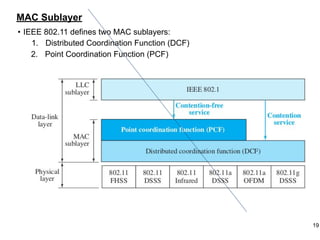
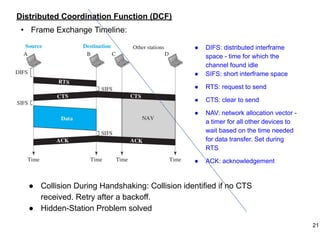
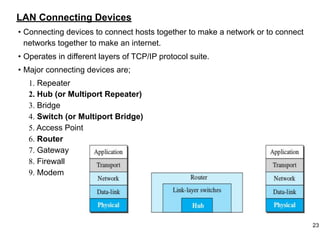
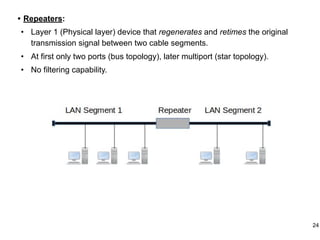
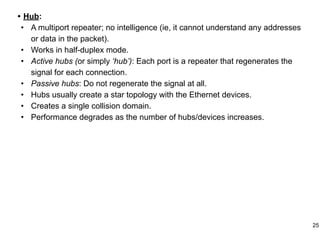
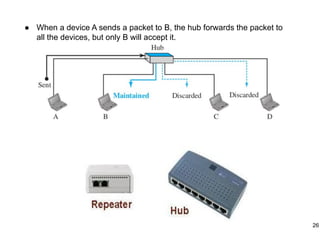
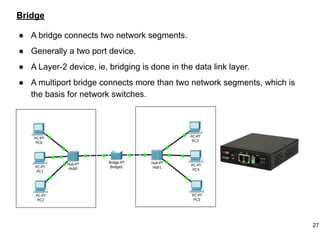
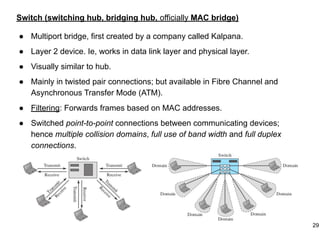
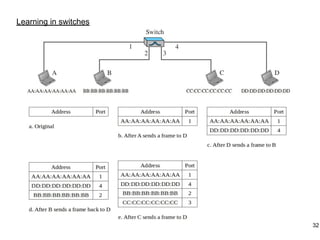
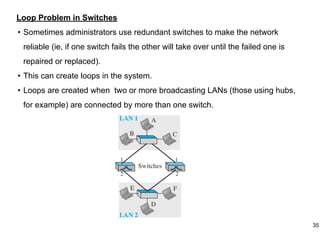
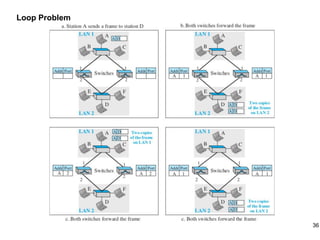
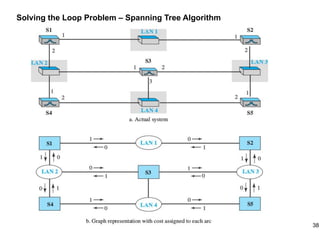
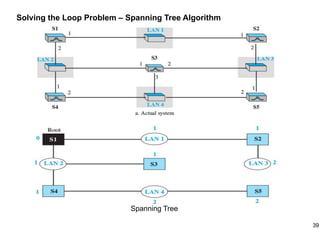
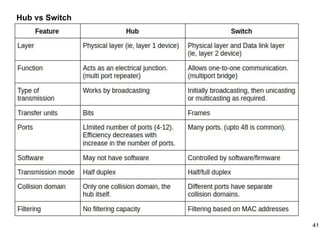
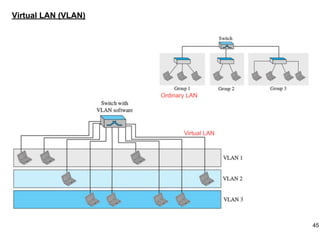
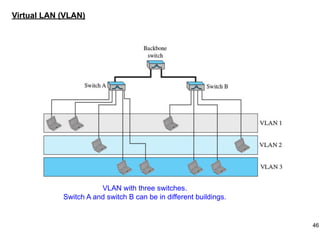
This document provides an overview of computer networks and wireless local area networks (WLANs). It discusses the TCP/IP model and layers, Ethernet protocols, wired and wireless LAN architectures and their differences. Wireless LAN characteristics like attenuation, interference and multipath propagation are described. The document also covers wireless LAN access control using CSMA/CA, the IEEE 802.11 project, services like BSS and ESS. Key components of a WLAN like the MAC sublayer, DCF, PCF, and common LAN connecting devices are summarized.