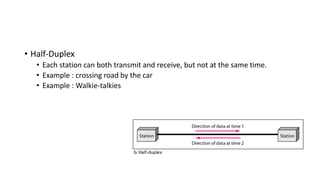
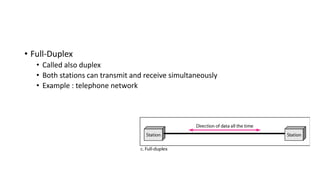
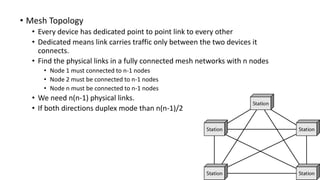
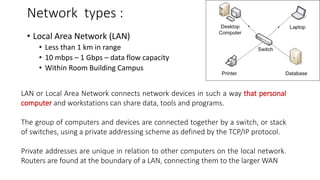
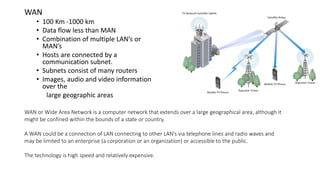
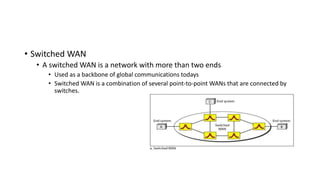
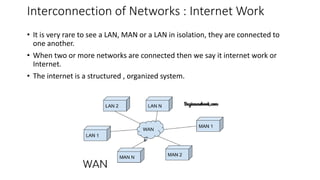
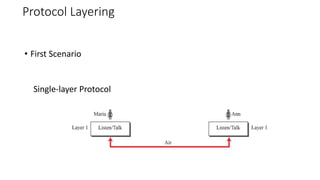
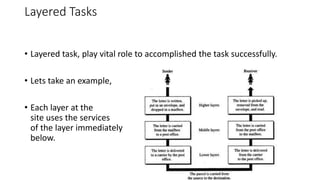
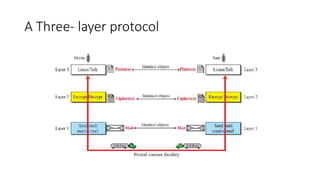
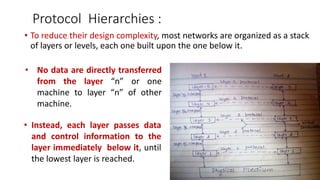
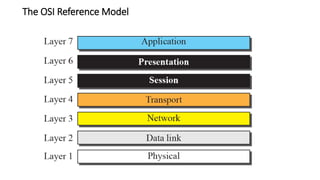
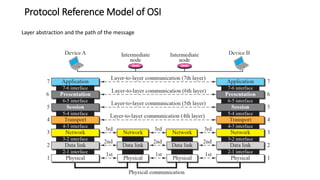
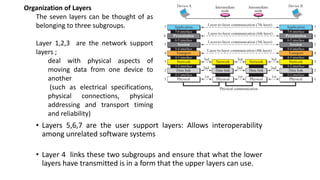
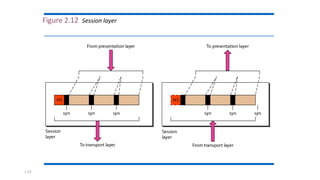
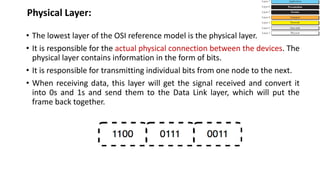
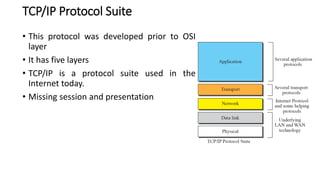
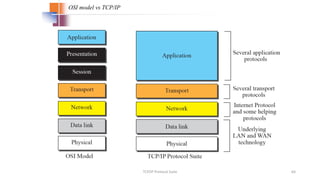
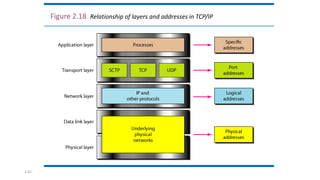
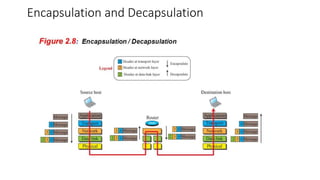
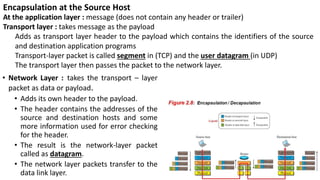
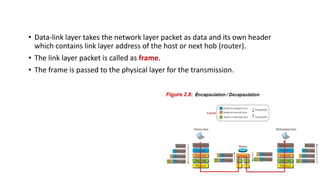
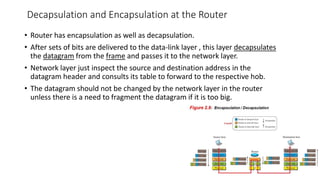
The document provides an overview of data communication and networking concepts. It discusses data communication fundamentals including delivery, accuracy, timeliness and jitter. It describes data communication system components such as messages, senders, receivers, transmission medium and protocols. It also covers data representation, data flow models, network types including LAN, MAN and WAN, wireless networks, internet interconnection and network protocols and standards.