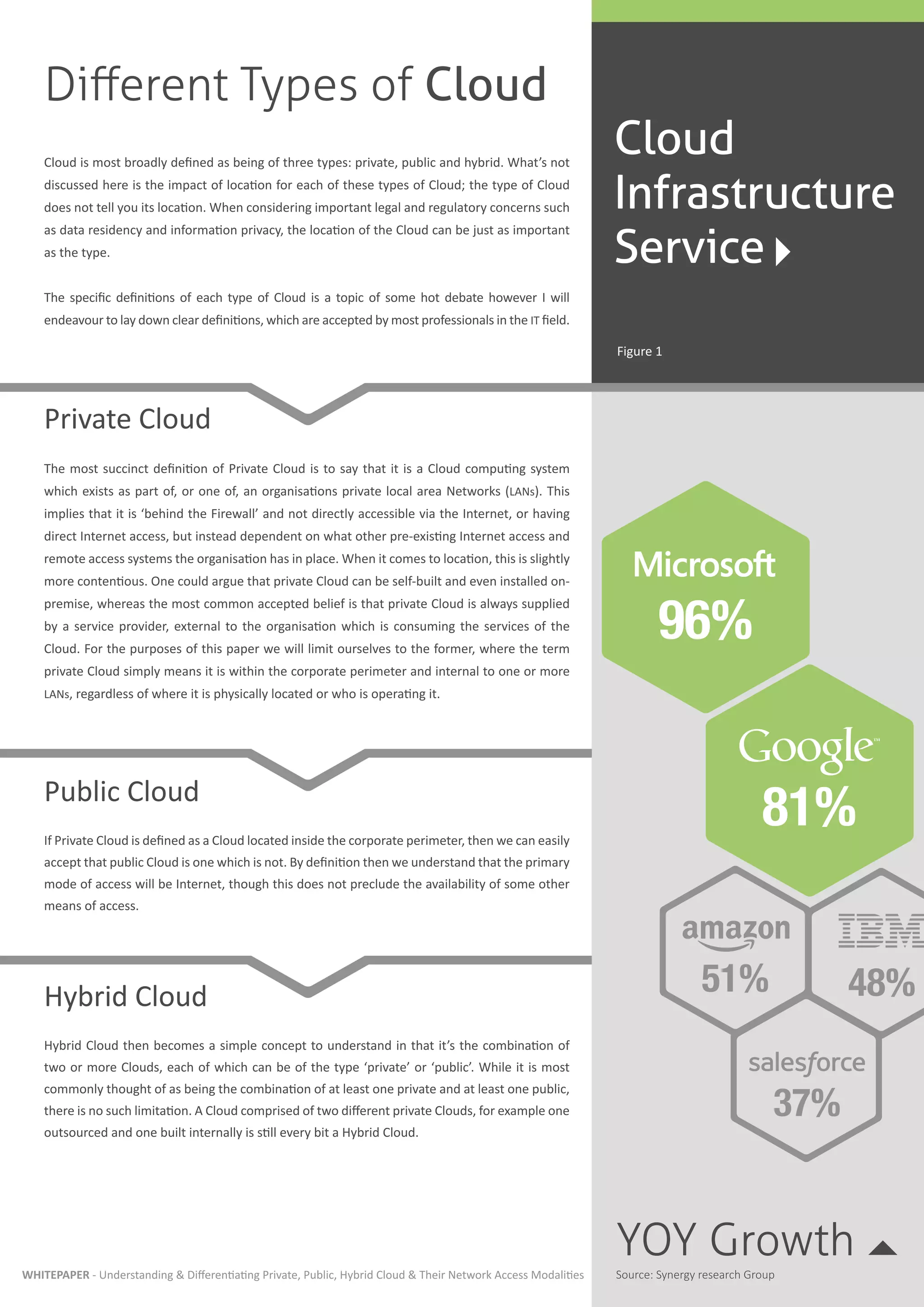
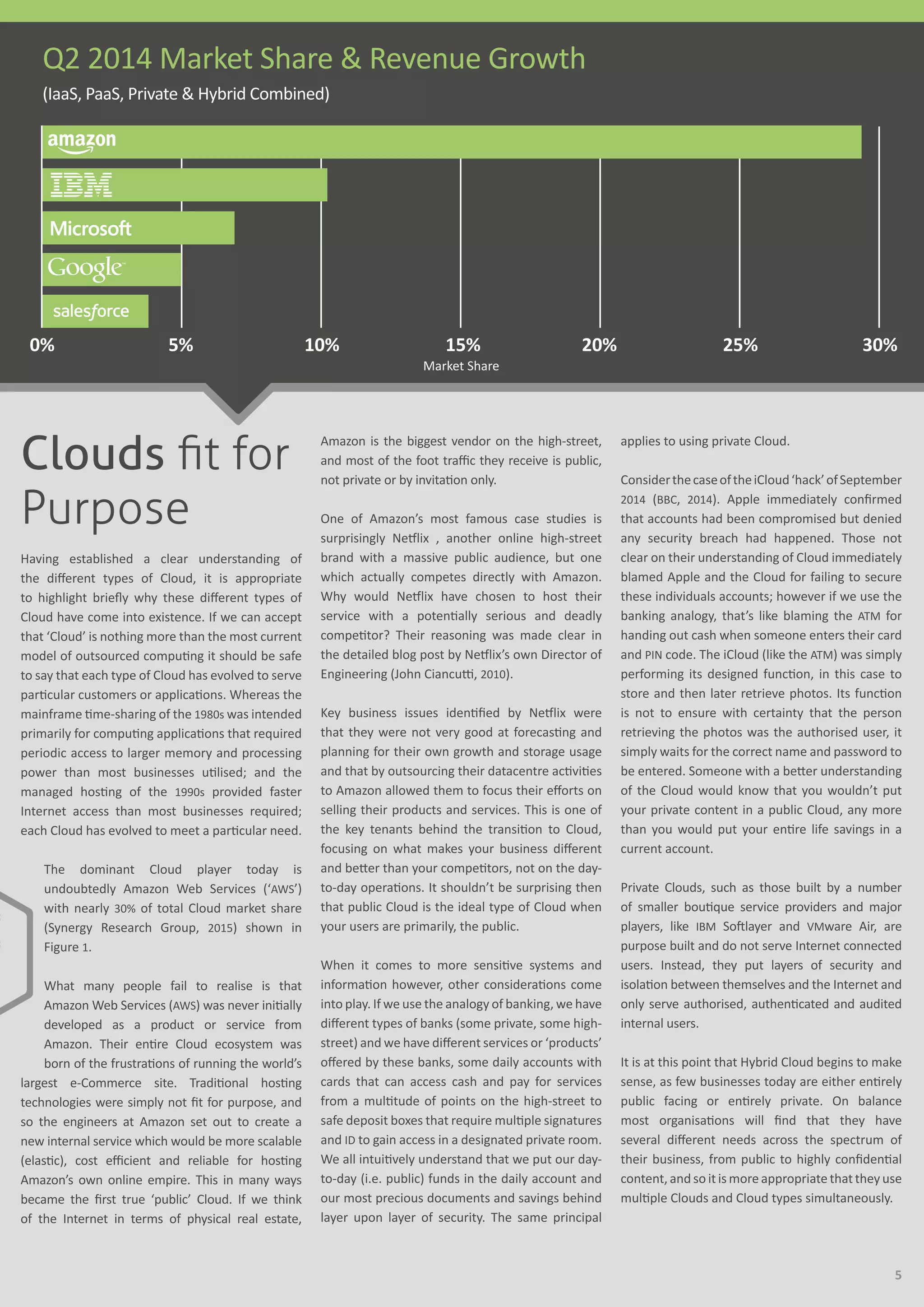
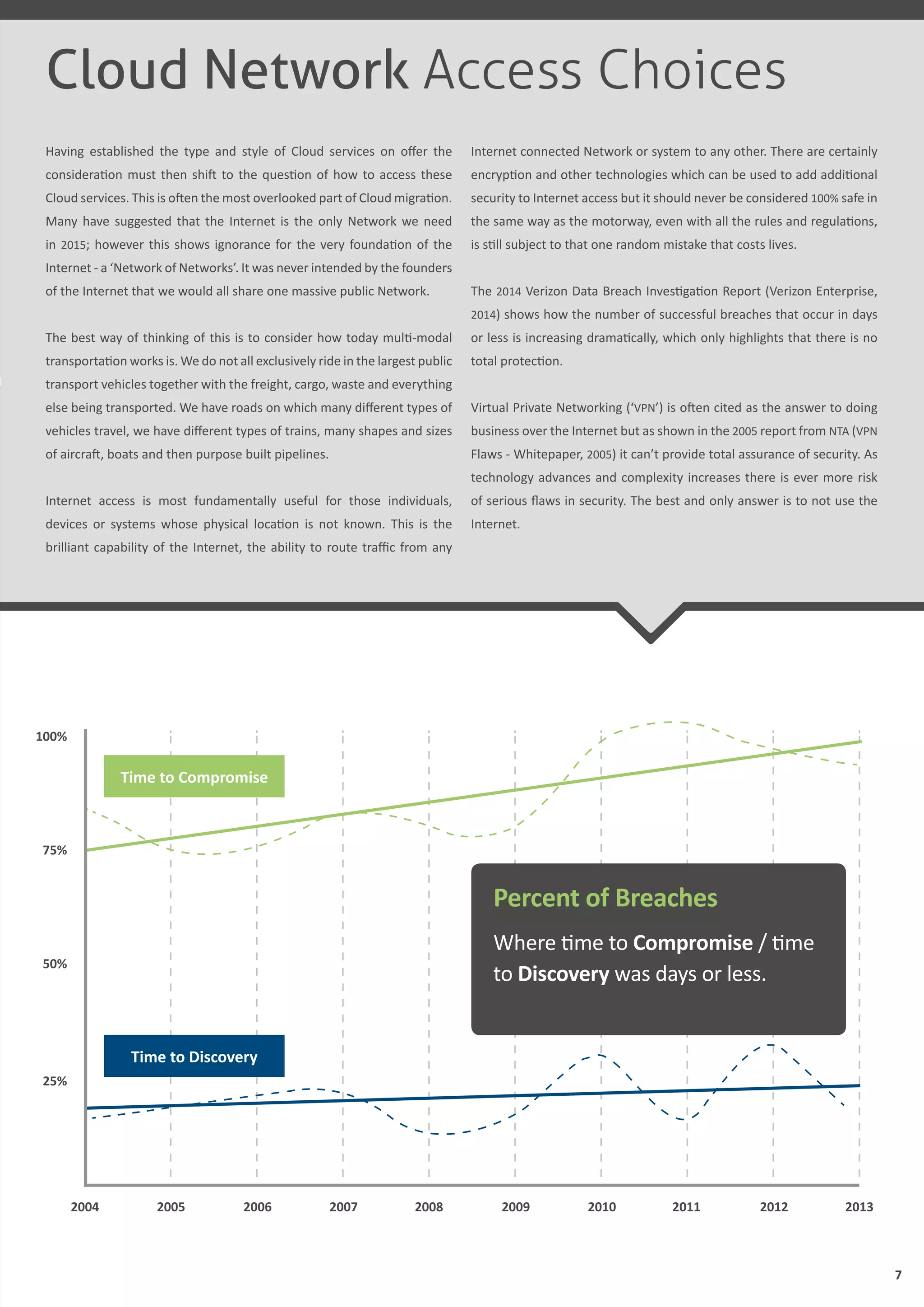
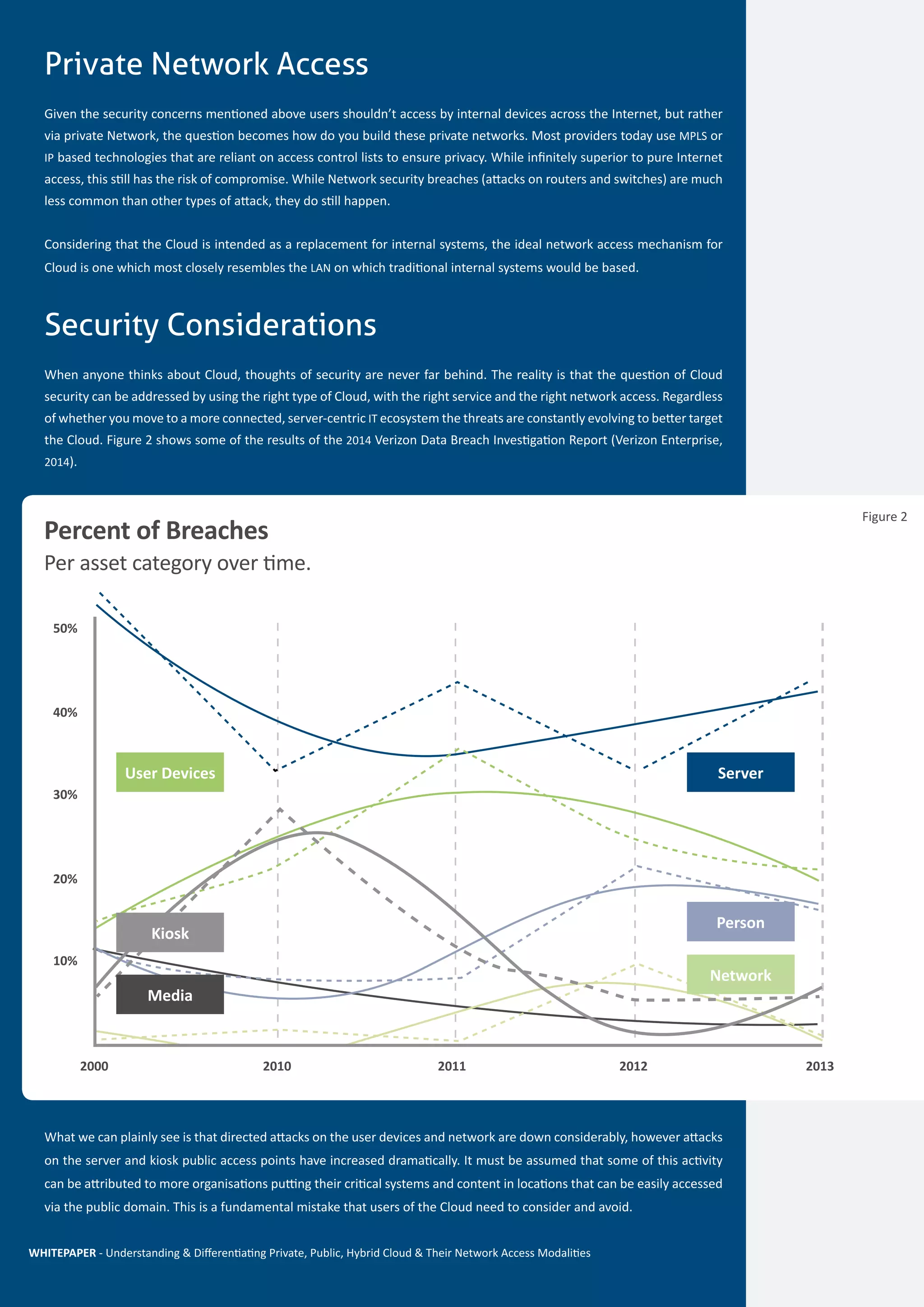
This document discusses different types of cloud computing (private, public, hybrid), cloud service models (SaaS, PaaS, IaaS), and cloud network access choices. It aims to build understanding of the cloud market and impact of network access choices. Private cloud is located within a company's internal network, public cloud is accessed via the internet, and hybrid cloud combines private and public cloud options. Different cloud types and services are suited for different business needs. Network access is an important but often overlooked aspect of cloud strategy.