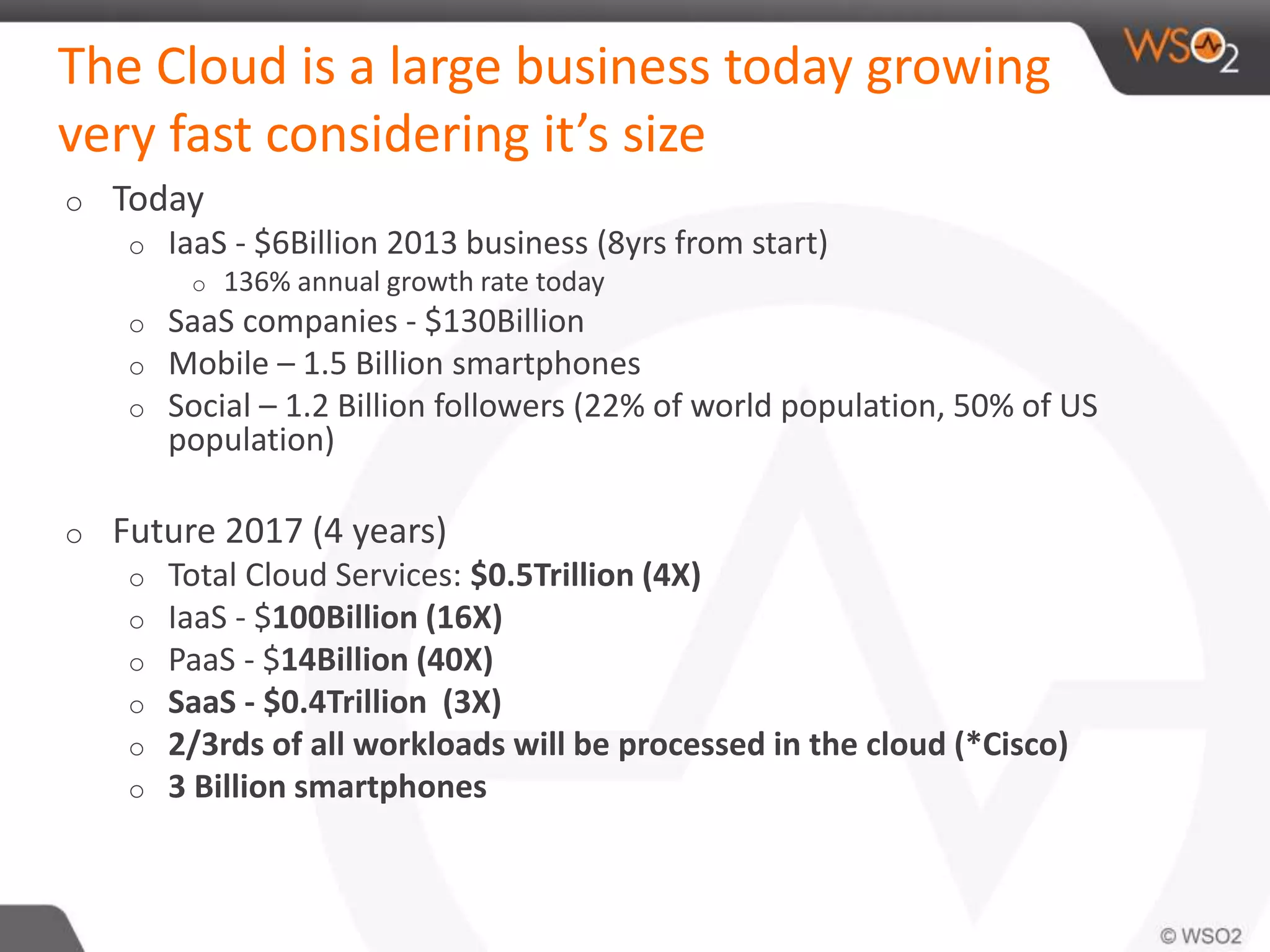
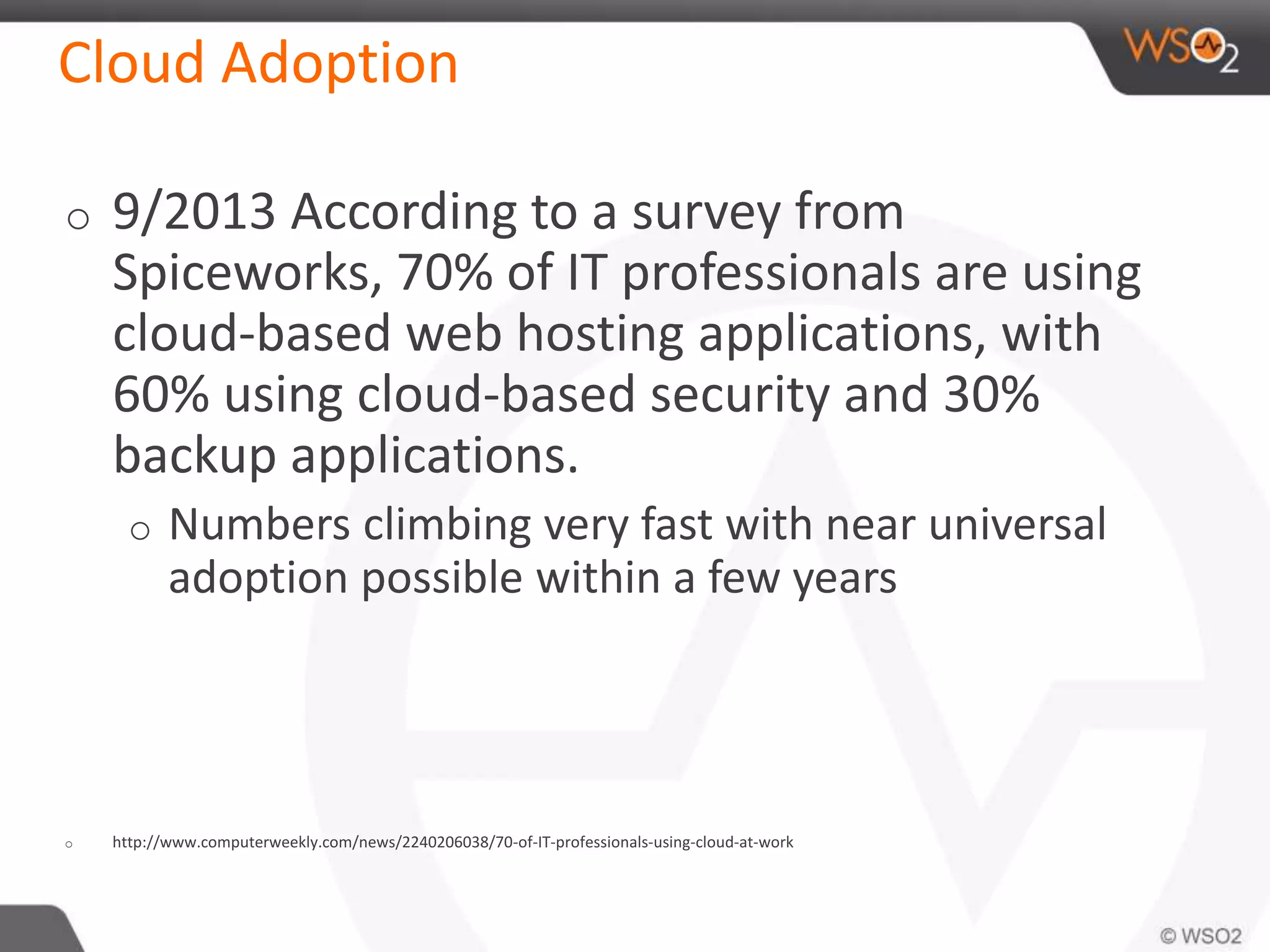
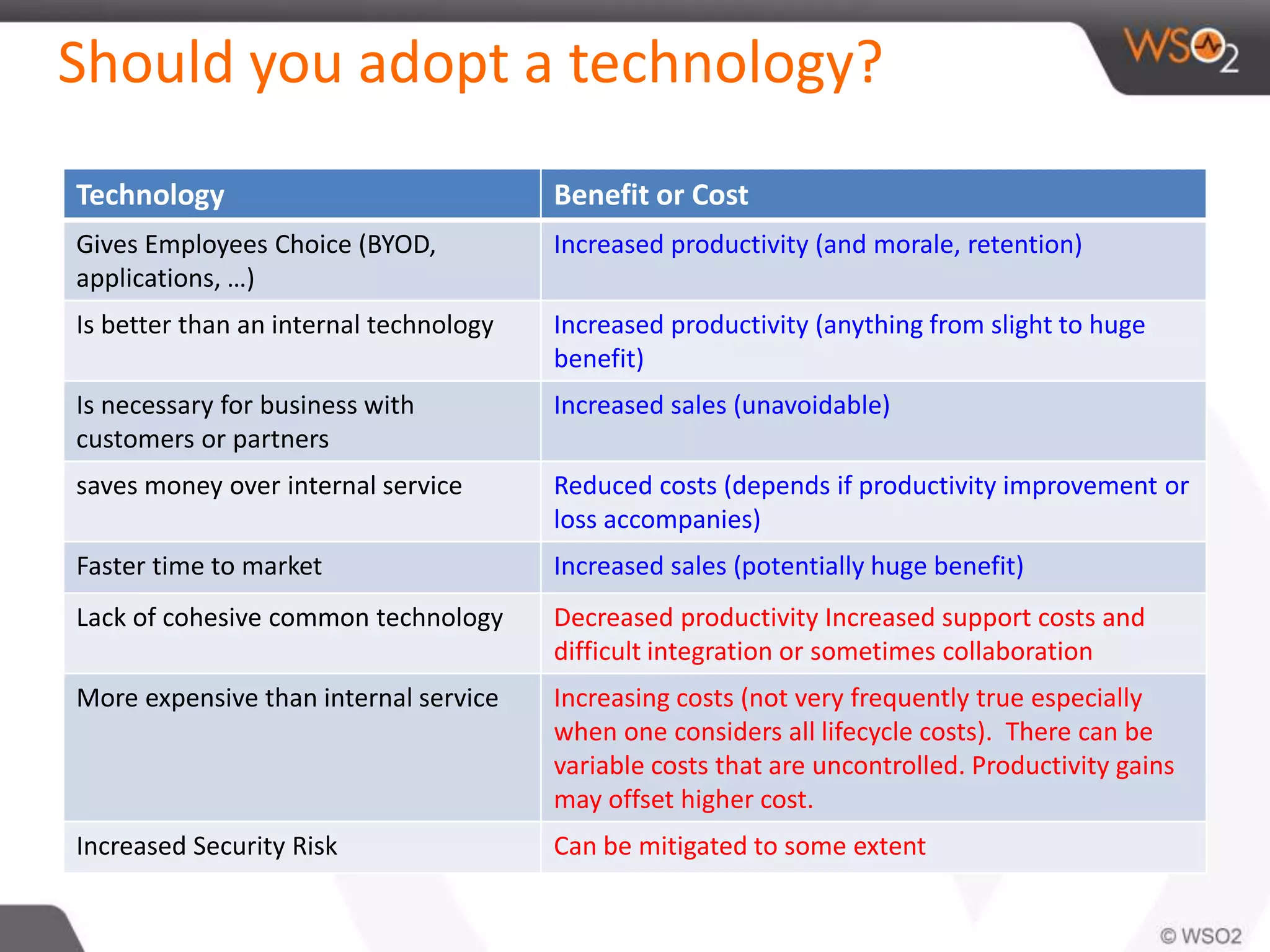
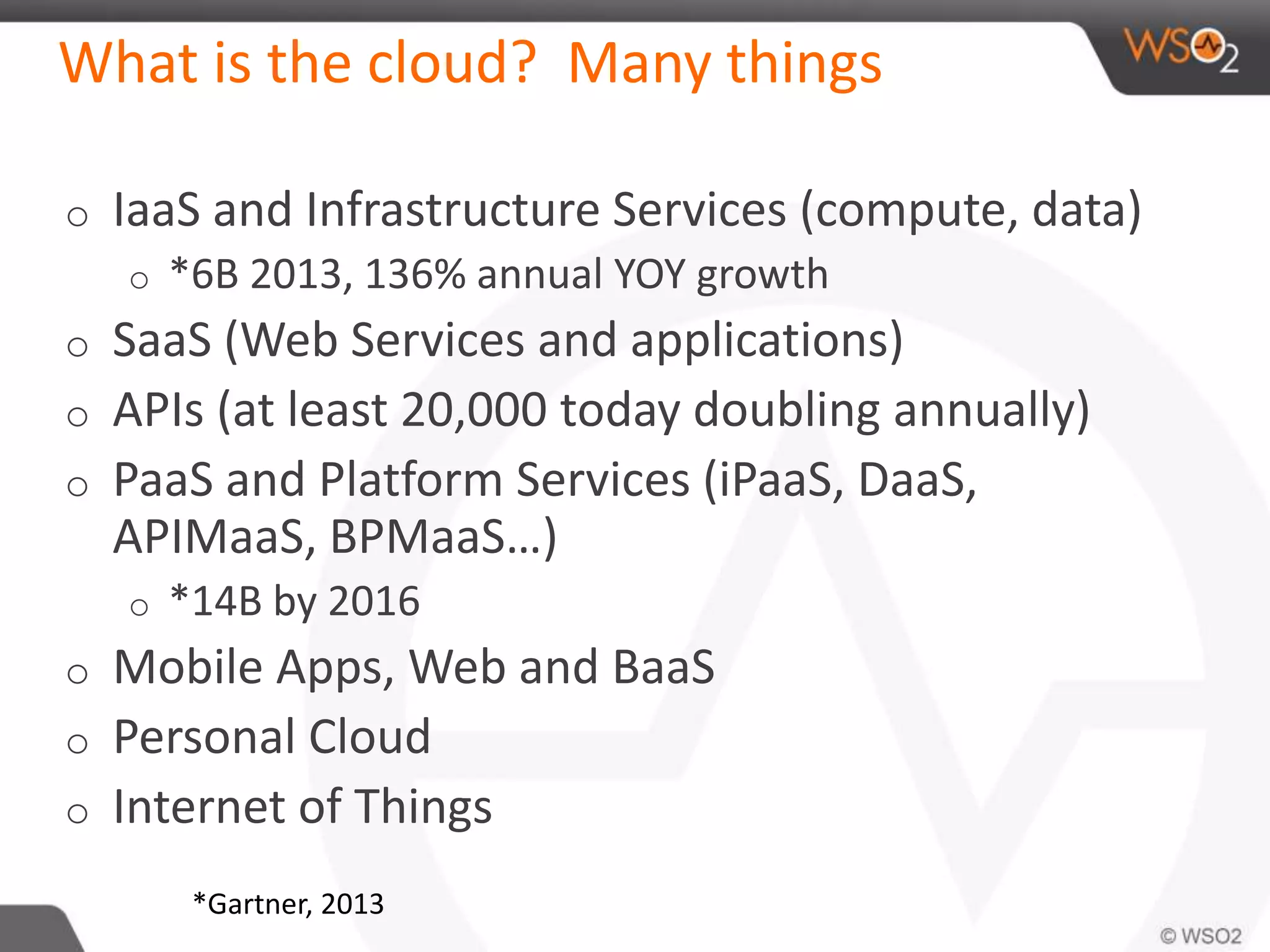
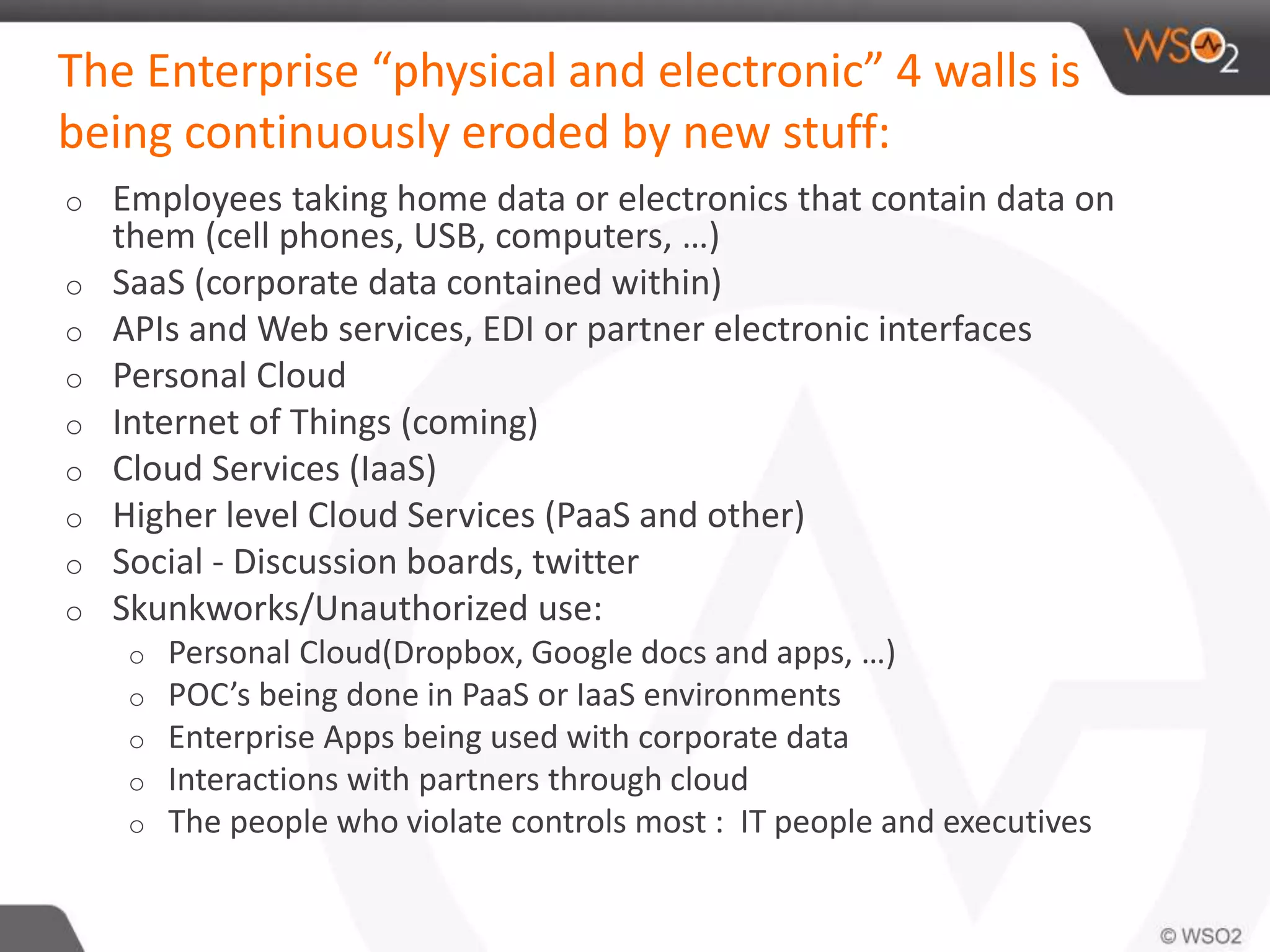
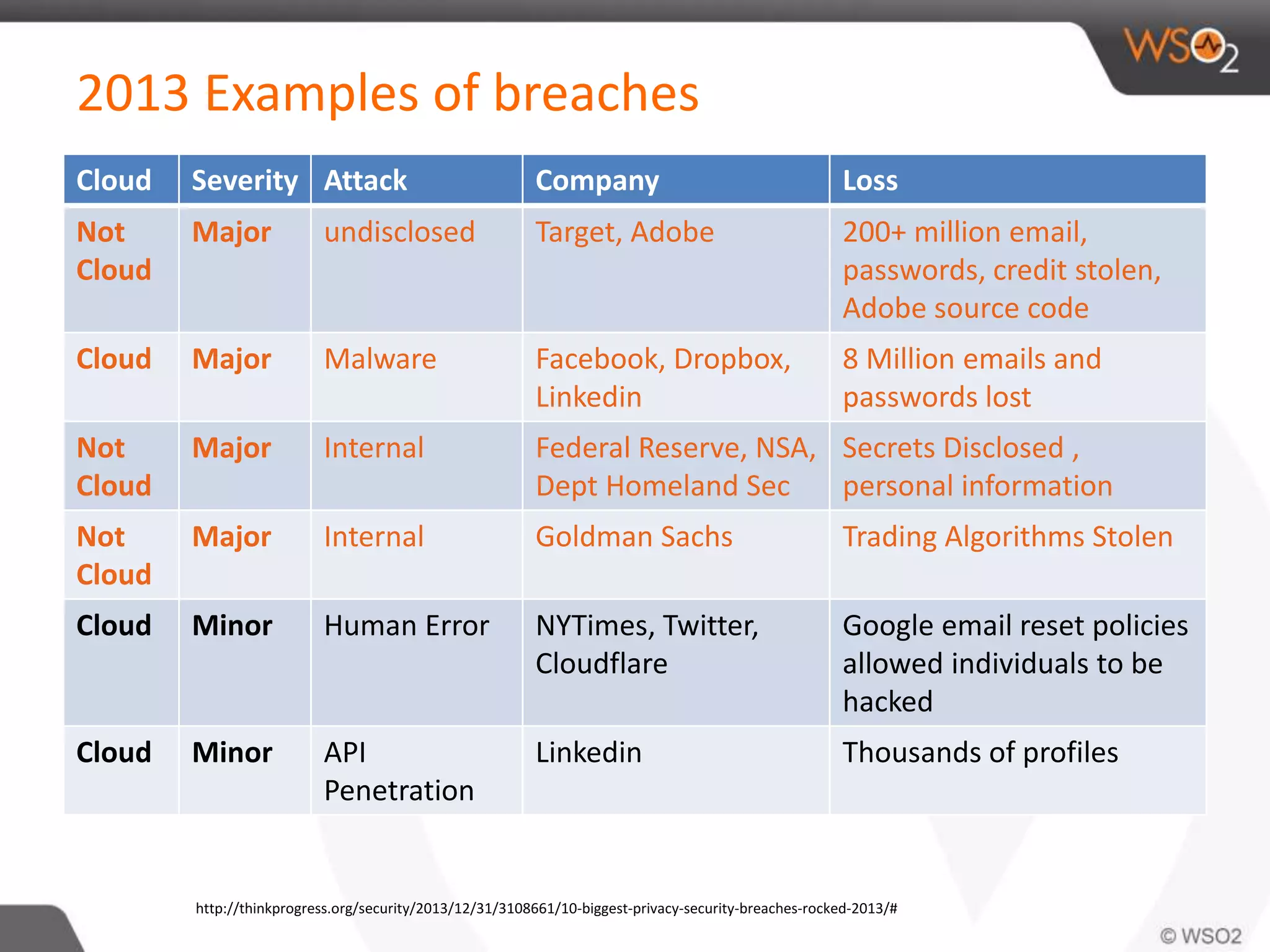
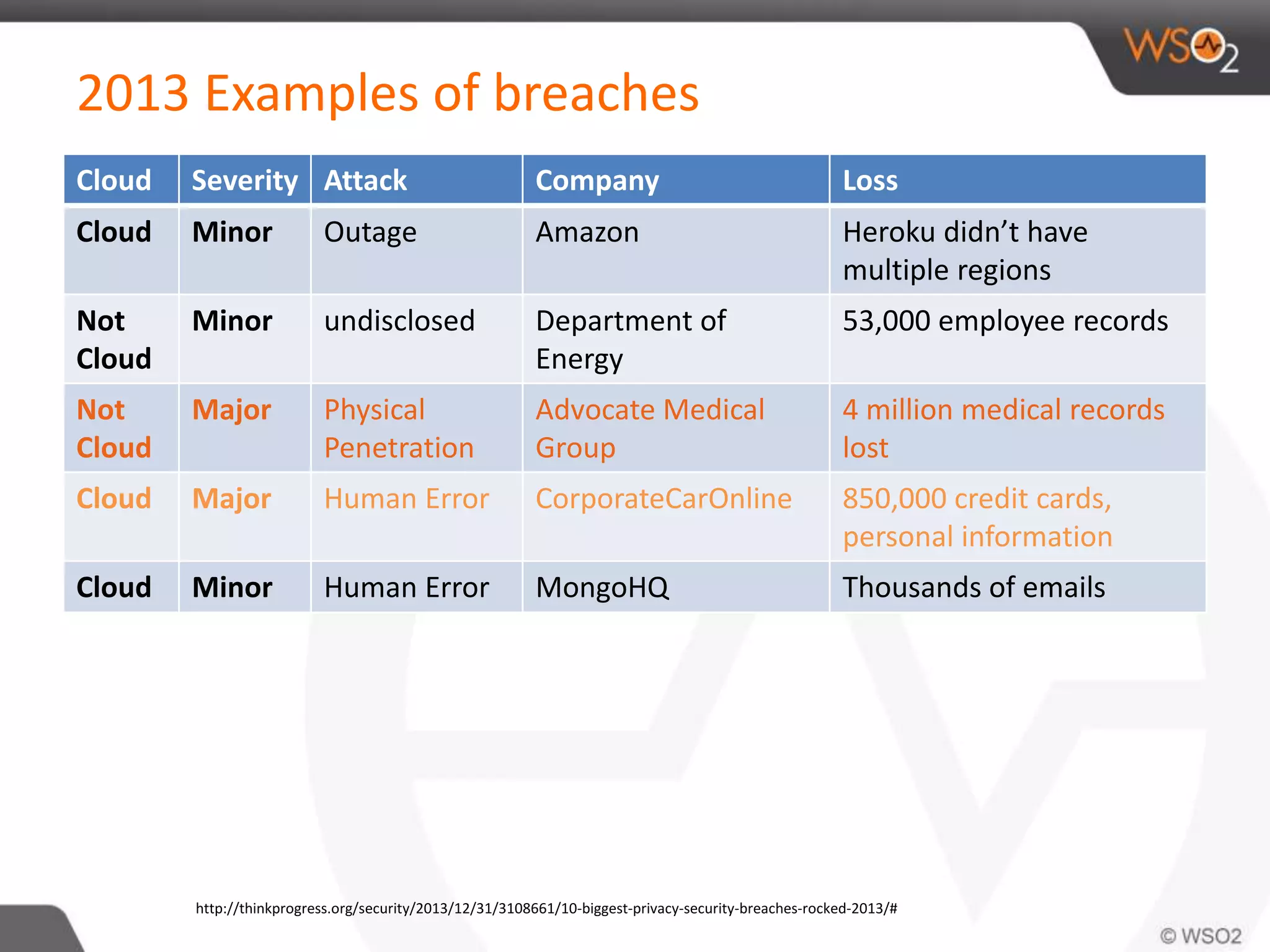
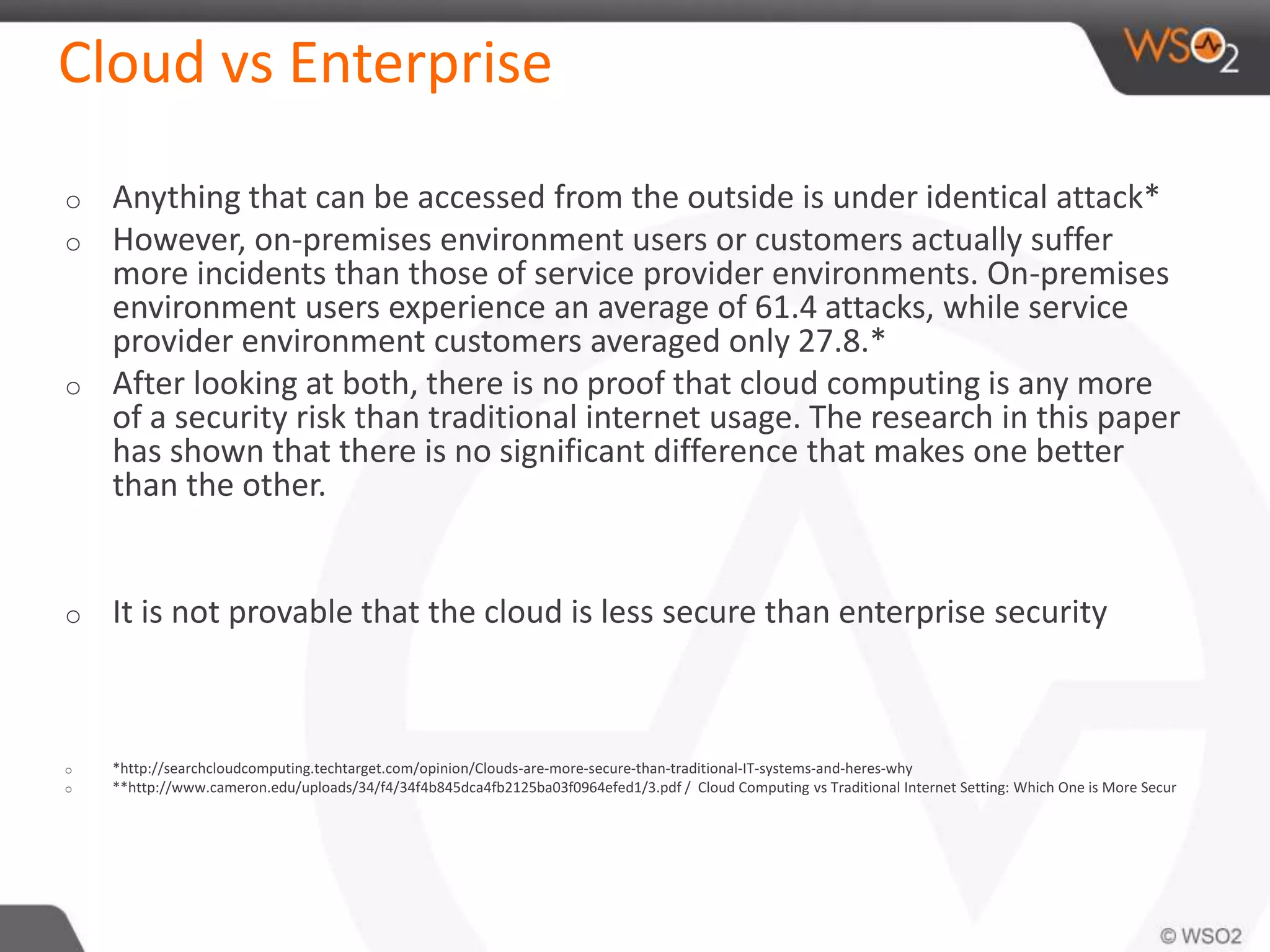
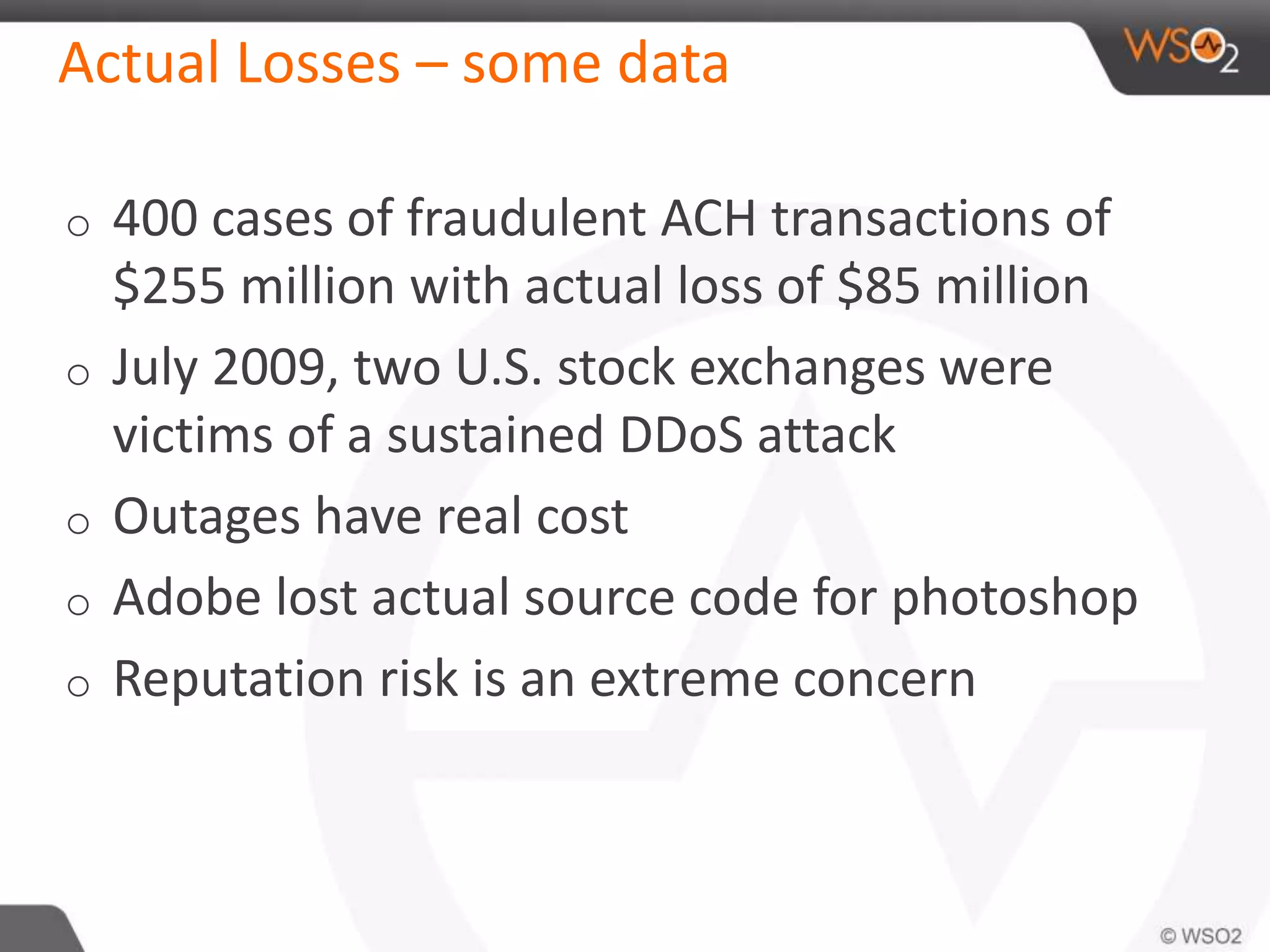
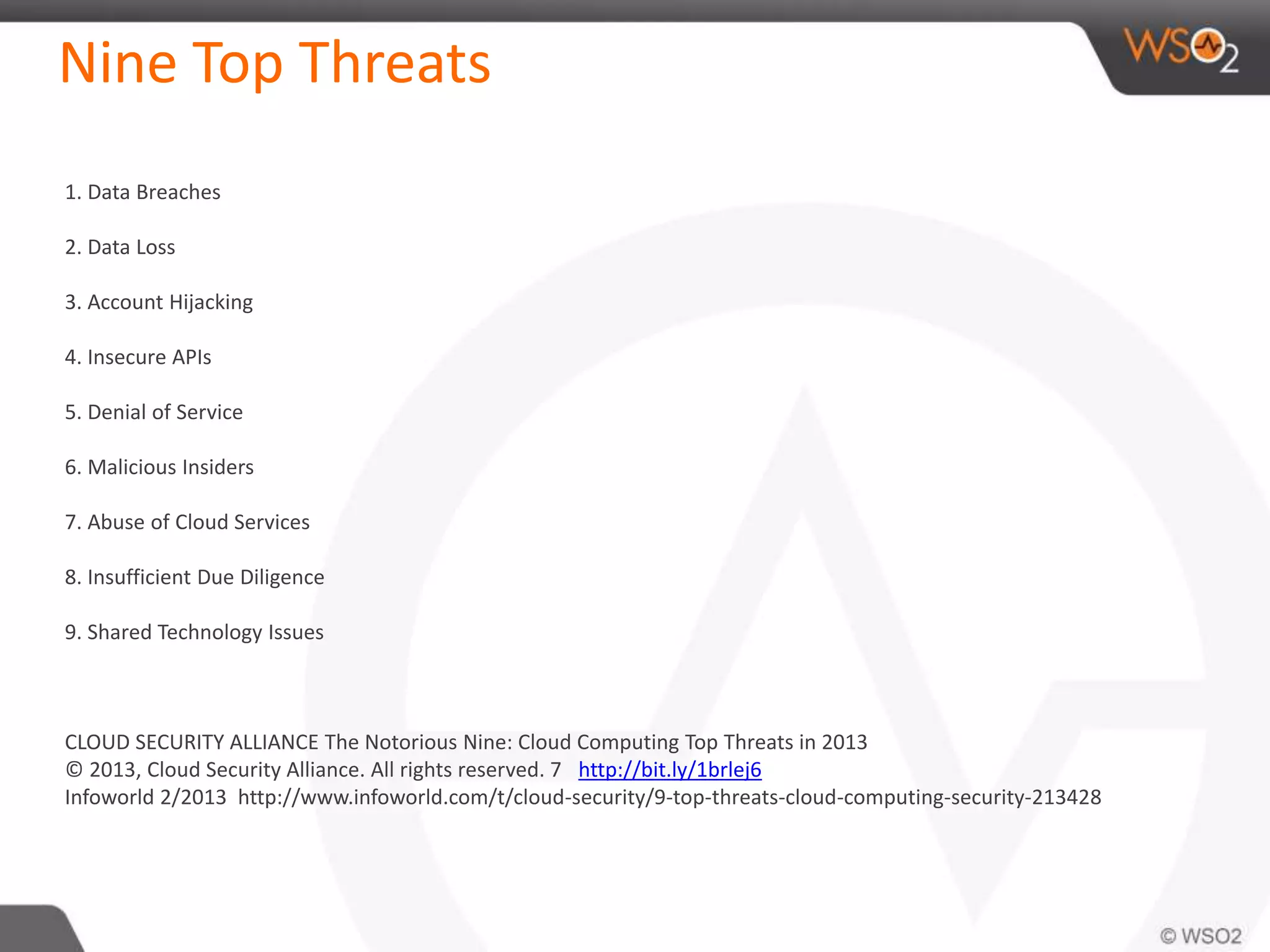
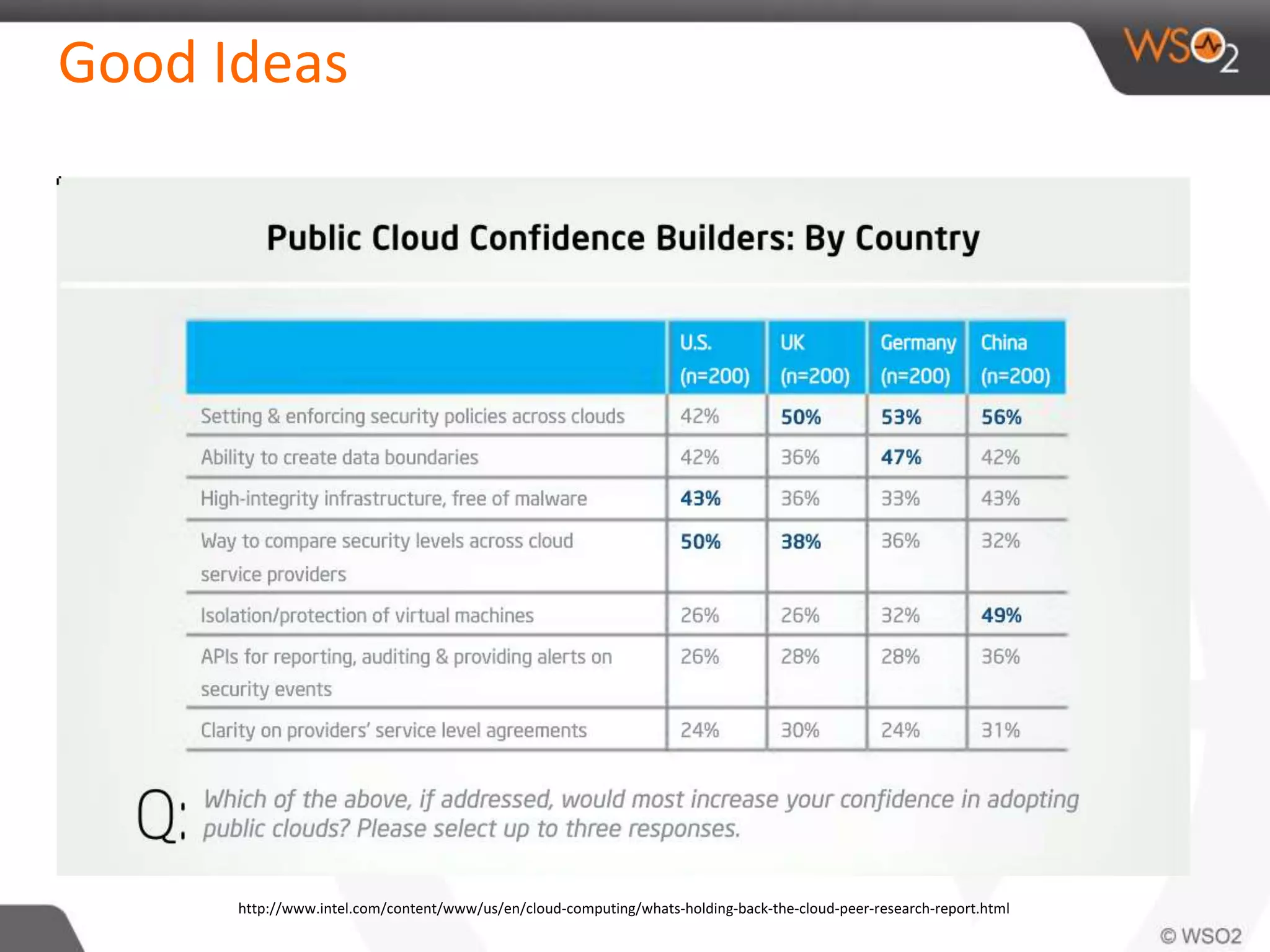
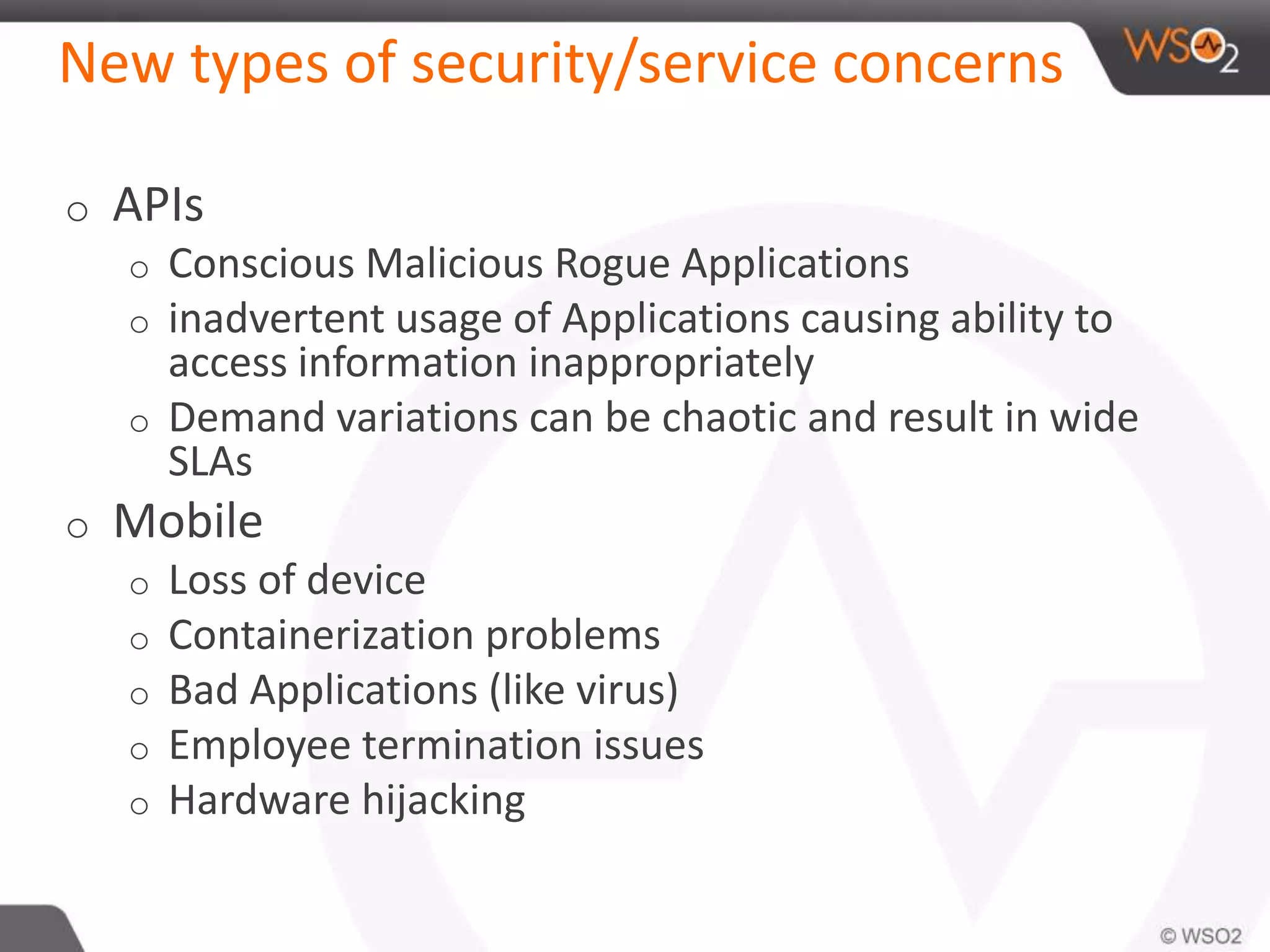
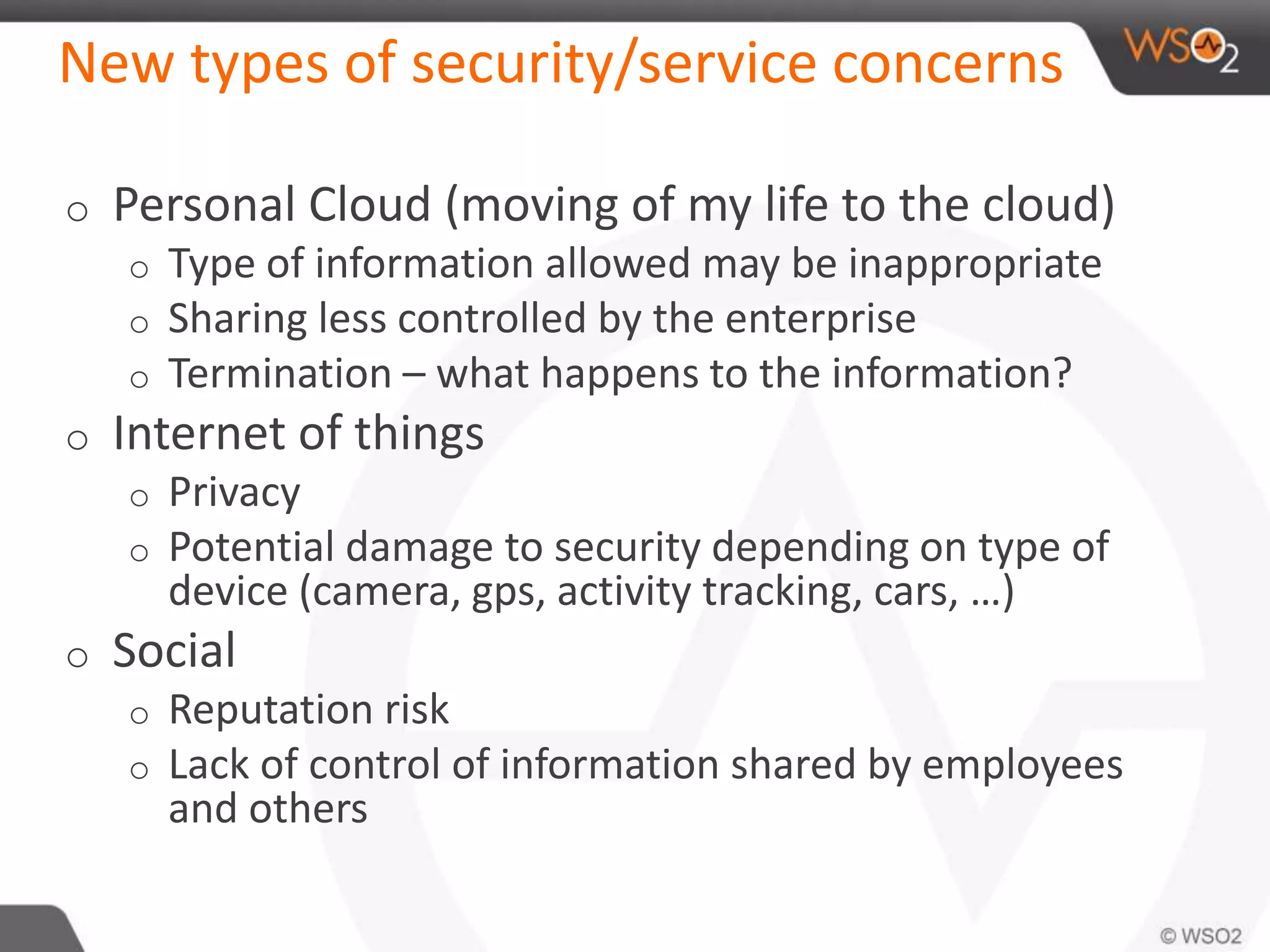
The document discusses cloud security and technology adoption. It argues that cloud security is not inherently riskier than traditional enterprise security, citing statistics showing more breaches occur within enterprises. The cloud is growing rapidly due to cost savings and agility benefits. While security concerns remain, cloud providers are improving practices like multi-factor authentication. Overall risks are similar between cloud and non-cloud, including data breaches, loss, and hijacking. The cloud introduces some new concerns around APIs, mobile access, and sharing of customer data.