This document proposes a reputation-based trust management framework called CloudArmor to address trust issues in cloud computing. It describes three key challenges of trust management in clouds: 1) preserving privacy of sensitive user information, 2) protecting cloud services from malicious users providing misleading feedback, and 3) guaranteeing availability of trust management services given the dynamic cloud environment. The proposed framework includes a protocol to verify credibility of feedback while preserving privacy, an adaptive credibility model to measure feedback credibility and identify malicious users, and an availability model to manage availability of the decentralized trust management service.
![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 04 Issue: 07 | July -2017 www.irjet.net p-ISSN: 2395-0072
© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal | Page 1828
Cloud Armor: An Overview of Trusty Supporting Reputation Based
management for Cloud Services
Anand1, Anitha G2
1 PG Student, University BDT college of Engineering, Visveswaraya Technological University,
Hadadi Road, Davangere, Karnataka, India
2Associate Professor Dept CS &E, University BDT college of Engineering, Hadadi Road, Davangere,
Karnataka,India,
-----------------------------------------------------------------------------***----------------------------------------------------------------------------
Abstract - Trust management is one of the most challenging
issues for the adoption and growth of cloud computing. The
highly dynamic, distributed, and non-transparent nature of
cloud services introduces several challenging issues such as
privacy, security, and availability. Preserving consumers’
privacy is not an easy task due to the sensitive information
involved in the interactions between consumers and the
trust management service. Protecting cloud servicesagainst
their malicious users (e.g., such users might give misleading
feedback to disadvantage a particular cloud service) is a
difficult problem. Guaranteeing the availability of the trust
management serviceisanothersignificantchallengebecause
of the dynamic nature of cloud environments. In this article,
we describe the design and implementation of CloudArmor,
a reputation-based trust management framework that
provides a set of functionalities to deliver Trust as a Service
(TaaS), which includes i) a novel protocol to prove the
credibility of trust feedbacks and preserve users’ privacy, ii)
an adaptive and robust credibility model for measuring the
credibility of trust feedbacks to protect cloud services from
malicious users and to compare the trustworthinessofcloud
services, and iii) an availability model to manage the
availability of the decentralized implementation of the trust
management service.
Key Words: Trust as a Service (TaaS), Level Agreements
(SLAs), Compliance Level Agreements (CLAs).
1. INTRODUCTION
The significantly intense, flowed and not apparent cloud
nature of organizations made the trust organizationincloud
conditions an enormous test. Asdemonstrated byexaminers
at Berkeleys, belief and assurance are situated the oneoften
obstacles of fundamental for the gathering of dispersed
figuring. Without a doubt, Benefit Level Understandings
(service level arguments) single are missing to set up
assurance between cloud purchasers and providers in
perspective of its foggy andclashingstipulations.Customers'
feedback is a good source to assess the general reliability of
cloud organizations. A couple of examiners have seen the
significance of trust organization and proposed answers for
assess and manage confide in perspective of reactions
assembled from individuals. When in doubt, itisnotunusual
that a cloud advantage experiences vindictivepractices(e.g.,
plot or Sybil strikes) from their customers.itwanderfocuses
by improving trust organization in cloud conditions by
proposing different ways to deal with certification the
legitimacy of assurance reactions. In particular, we perceive
the going with fundamental problems of the assurance
organization in cloud circumstances.
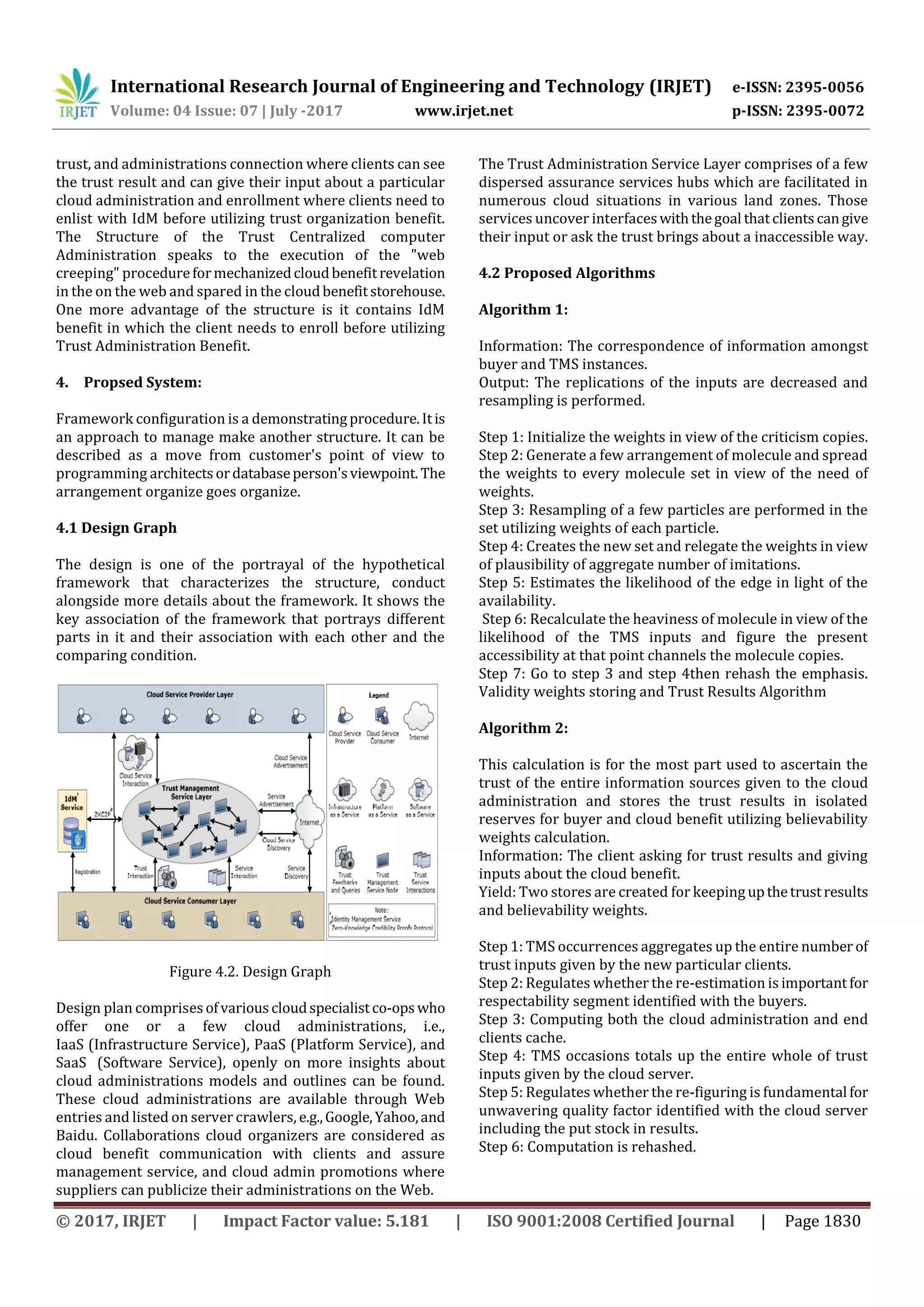
2. Literature Survey
[1] S. M. Khan and K. W. Hamlen, “Hatman: Intra-Cloud
Trust Management for Hadoop,” in Proc. CLOUD’12,
2012.
Enormous progress in hardware, networking, middleware,
and virtual machine technologies have led to an emergence
of new, globally distributed computing platforms that
provide computation facilities and storage as services
accessible from anywhere via the Internet. At the fore ofthis
movement, cloud computing has been widely heralded as a
new, promising platform for delivering information
infrastructure and resources as IT services . Customers can
access these services in a pay-as-you go fashionwhilesaving
huge capital investment in theirownITinfrastructure.Thus,
cloud computing is now a pervasive presence of enormous
importance to the future of e-commerce.
Data integrity and privacy have emerged as major concerns
for prospective users of clouds. A survey byFujitsuResearch
Institute reveals that 88% of prospective customers are
worried about who has access to their data in the cloud and
demand more trustworthiness. Such surveys reveal an
urgent need to meaningfully addresstheseconcernsforreal-
world cloud systems
[2] S. Pearson, “Privacy, Security and Trust in Cloud
Computing,” in Privacy and Security for Cloud
Computing, ser. Computer Communications and
Networks, 2013, pp. 3–42.
The telecommunication industry has been successful in
turning the Internet into a mobile service and stimulating
the creation of a new set of networked, remote services.
Most of these services are currently supported by or run in
cloud computing platforms. Cloud computing represents a
threat to the status quo of the telecommunication industry](https://image.slidesharecdn.com/irjet-v4i7388-170907100911/75/Cloud-Armor-An-Overview-of-Trusty-Supporting-Reputation-based-Management-for-Cloud-Services-1-2048.jpg)

![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 04 Issue: 07 | July -2017 www.irjet.net p-ISSN: 2395-0072
© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal | Page 1831
5. Conclusion
Weghave presented different methods thatxhelp with
recognizing reputationxbased strikes and empowering
customers to enough perceive reliable cloudxorganizations.
In particular, wexdisplay a credibilityxdemonstratethatlnot
simply recognizes misleading trustxreactions fromxplot
attacks also distinguishes Sybildambushes paying little
attention to these strikes happen in a long or brief time
period (i.e., crucialxor coincidentalxattacks exclusively).
Wexfurthermore develop an availabilityxdisplaythatxkeeps
upythe trustzorganization advantage at a pined forxlevel.
Wethave gathered an expensive numberlof customers
trustgreactions givenlon realicloud organizations (i.e.,more
than 10,000frecords)xto assess ourxproposed
procedures.iThe exploratory outcomes exhibitithe
appropriateness ofxour approachianddemonstratetheilimit
ofxperceiving such pernicious practices. Therevare two or
three headingsxfor ourdfutureywork. Wexplan to combine
various trustiorganization systems, for instance,ireputation
and proposal tozextend thestrust happens
exactness.jExecution headway of the trustqorganization
isxanother centralization ofvour futurexresearchtwork.
References
[1] S. M. Khan and K. W. Hamlen, “Hatman: Intra-Cloud
Trust Management for Hadoop,” in Proc. CLOUD’12, 2012.
[2] S. Pearson, “Privacy, Security and Trust in Cloud
Computing,” in Privacy andSecurityforCloudComputing,
ser. Computer Communications and Networks, 2013, pp. 3–
42.
[3] J. Huang and D. M. Nicol, “Trust Mechanisms for Cloud
Computing,”Journal of Cloud Computing, vol. 2, no. 1, pp. 1–
14, 2013.
[4] K. Hwang and D. Li, “Trusted Cloud Computing with
Secure Resources and Data Coloring,” IEEE Internet
Computing, vol. 14,no. 5, pp. 14–22, 2010.
[5] M. Armbrust, A. Fox, R. Griffith, A. Joseph, R. Katz, A.
Konwinski, G. Lee, D. Patterson, A. Rabkin, I. Stoica, and M.
Zaharia, “A View of Cloud Computing,” ommunications of the
ACM, vol. 53,no. 4, pp. 50–58, 2010.
[6] S. Habib, S. Ries, and M. Muhlhauser, “Towards a Trust
Management System for Cloud Computing,” in Proc. of
TrustCom’11, 2011.
[7] I. Brandic, S. Dustdar, T. Anstett, D. Schumm, F. Leymann,
and R. Konrad, “Compliant Cloud Computing (C3):
Architecture and Language Support for User-Driven
Compliance Management in Clouds,” in Proc. Of CLOUD’10,
2010.
[8] W. Conner, A. Iyengar, T. Mikalsen, I. Rouvellou, and K.
Nahrstedt,“A Trust Management Framework for Service-
Oriented Environments,” in Proc. of WWW’09, 2009.
[9] T. H. Noor, Q. Z. Sheng, and A. Alfazi, “Reputation Attacks
Detection for Effective Trust Assessment of Cloud Services,”
in Proc. of TrustCom’13, 2013. [10] T. H. Noor, Q. Z.
Sheng, S. Zeadally, and J. Yu, “Trust Management of Services
in Cloud Environments: Obstacles and Solutions,” ACM
Computing Surveys, vol. 46, no. 1, pp. 12:1–12:30, 2013.](https://image.slidesharecdn.com/irjet-v4i7388-170907100911/75/Cloud-Armor-An-Overview-of-Trusty-Supporting-Reputation-based-Management-for-Cloud-Services-4-2048.jpg)