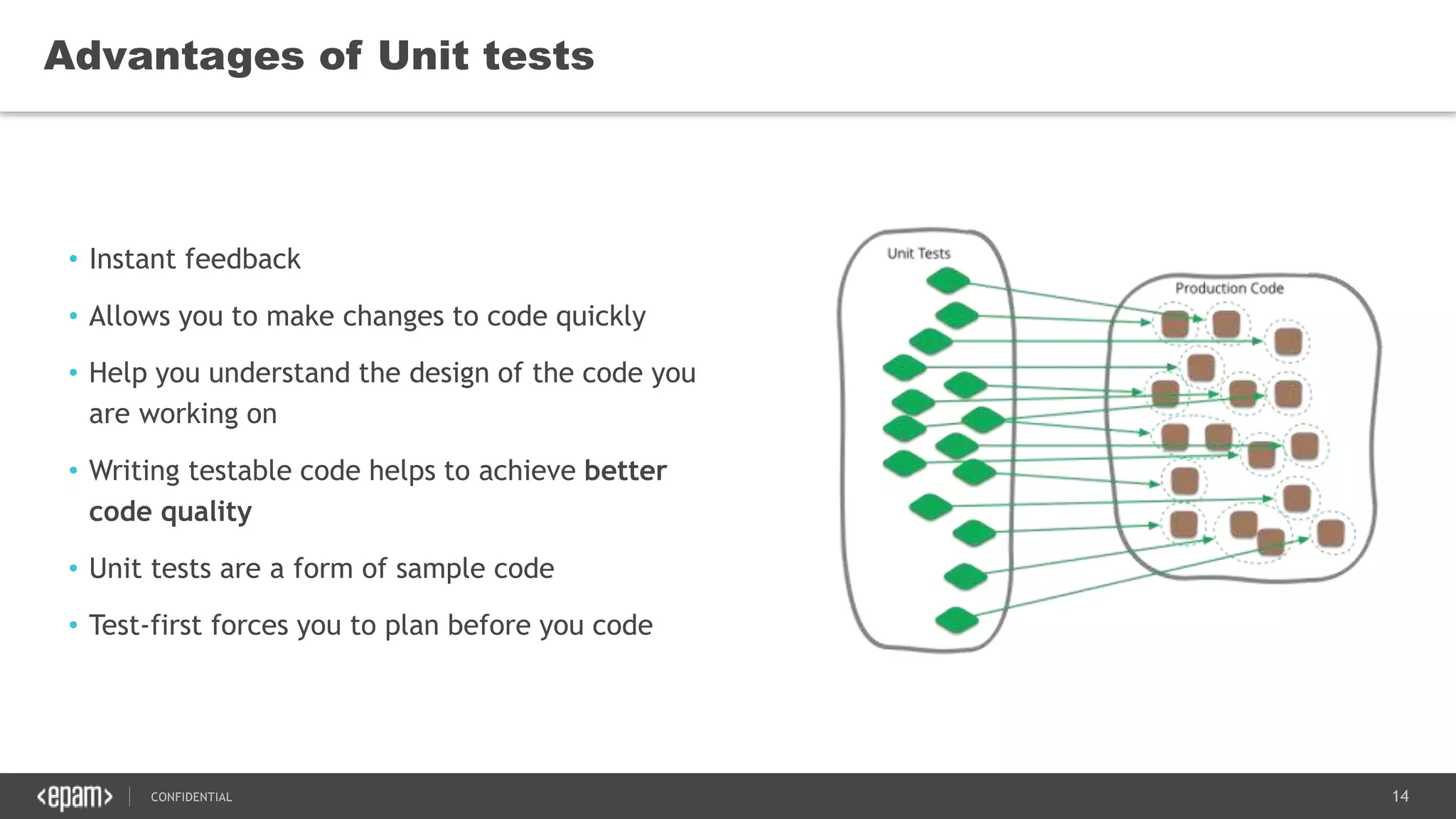
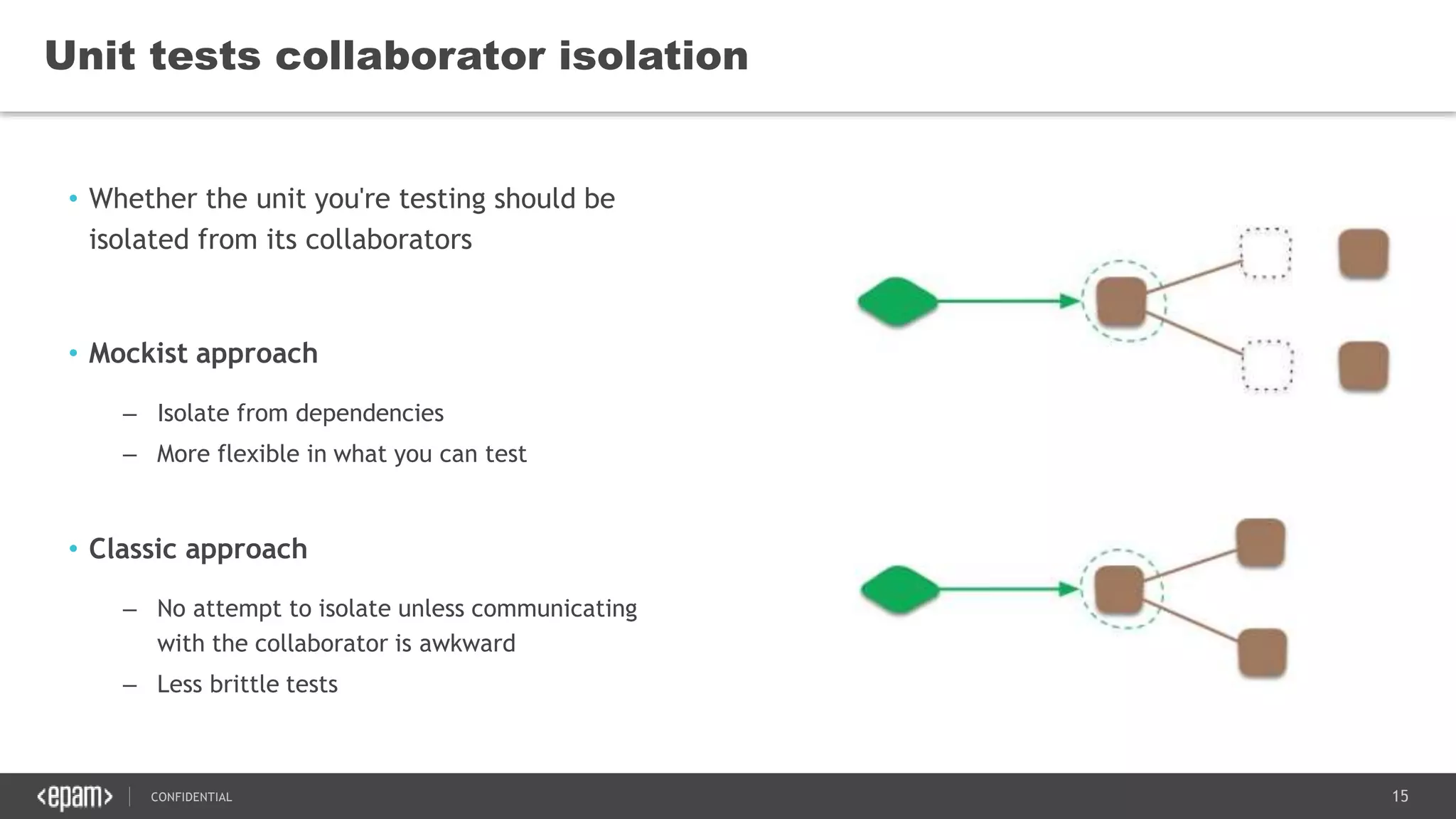
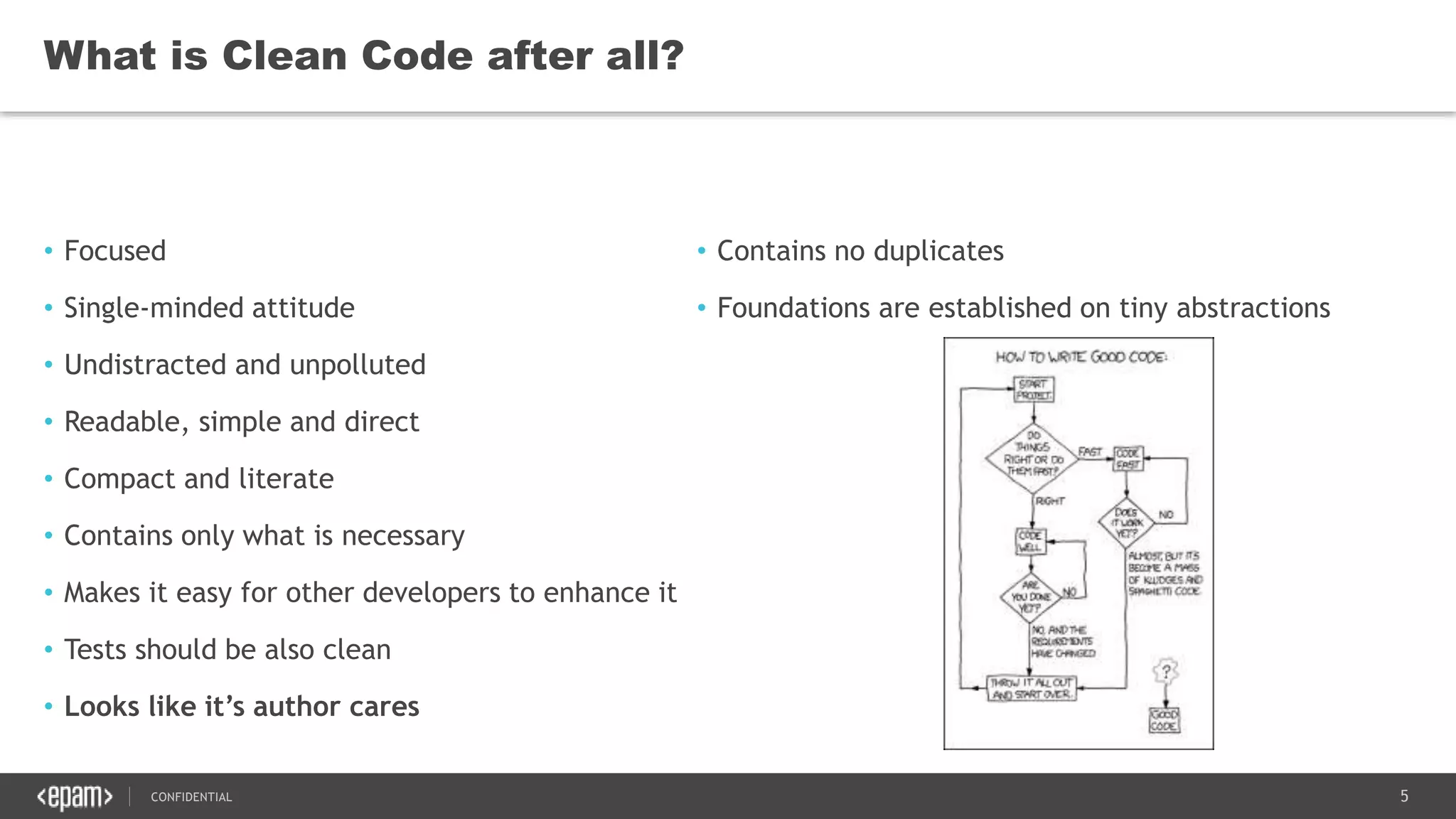
The document discusses principles of clean code and software quality. It summarizes Robert Martin's book "Clean Code" which defines characteristics of clean code such as being focused, readable, and containing only necessary content. It discusses metrics for measuring code quality, such as cyclomatic complexity, and principles for writing clean code, such as following the "Boy Scout Rule" to leave code better than how you found it. Implementation patterns like composed methods are presented, along with advantages of unit testing such as enabling quick changes and understanding design.






![10CONFIDENTIAL
Composed method example
public void add(Object element) {
if (!readOnly) {
int newSize = size + 1;
if (newSize > elements.length) {
Object[] newElements = new Object[elements.length + 10];
for (int index = 0; index < size; index++) {
newElements[index] = elements[index];
elements = newElements;
}
}
elements[size++] = element;
}
}](https://image.slidesharecdn.com/korozsi-201220164317/75/clean-code-uncle-bob-10-2048.jpg)