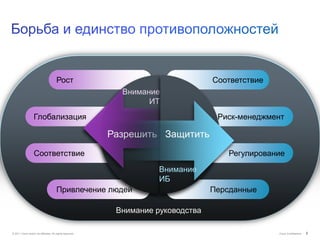
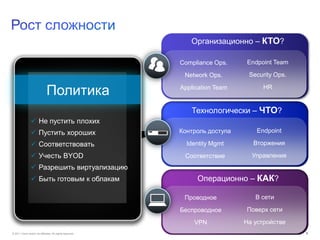
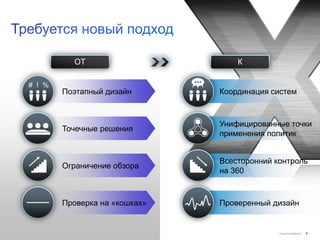
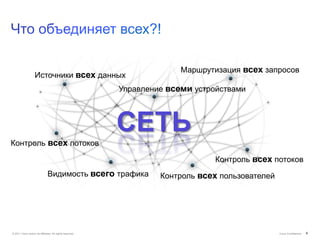
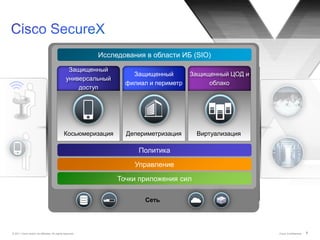
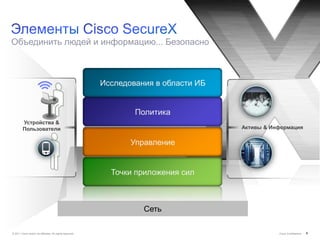
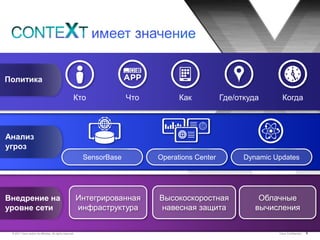
Документ обсуждает подходы Cisco к управлению безопасностью и соответствию требованиям, включая управление идентификацией, контроль доступа и виртуализацию. Он подчеркивает важность унифицированной системы для управления данными и пользователей, а также интеграции в облачные решения. Описаны основные аспекты, связанные с угрозами, операционными затратами и необходимыми навыками для эффективного управления безопасностью.