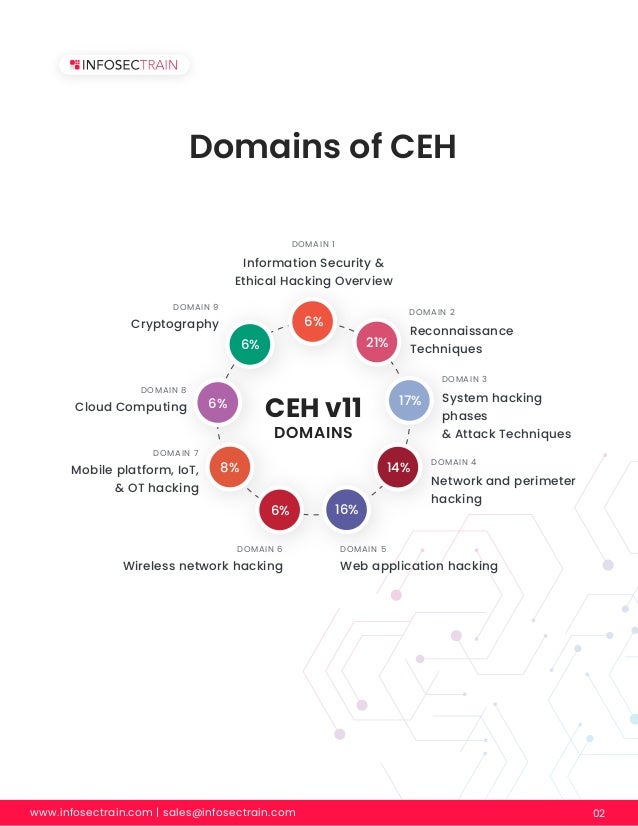
The document provides an overview of the Certified Ethical Hacker (CEH) certification, emphasizing the role of ethical hackers in identifying and addressing vulnerabilities within systems to prevent cybercrimes. It outlines various domains of ethical hacking, including reconnaissance techniques, system hacking, network and web application hacking, and highlights the significant job opportunities available in the field. Additionally, it discusses the importance of ethical hacking in safeguarding sensitive information and enhancing organizational security.