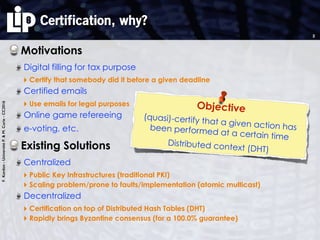
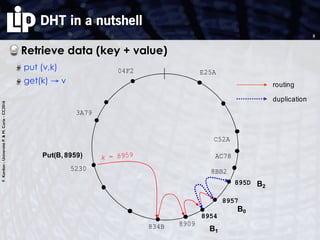
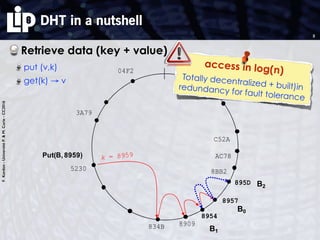
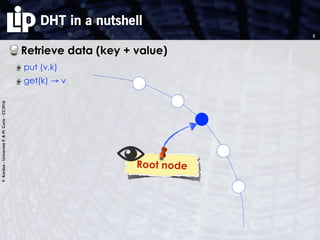
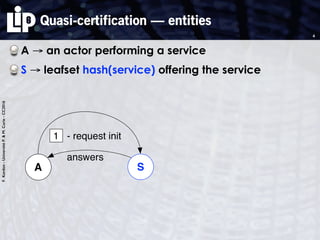
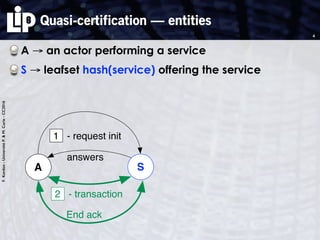
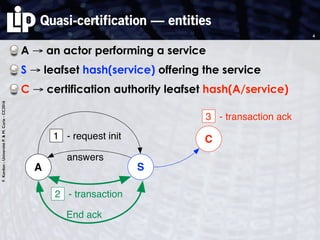
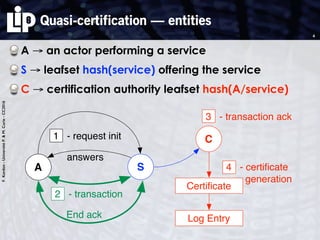
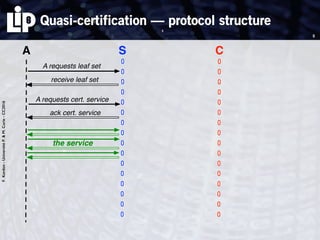
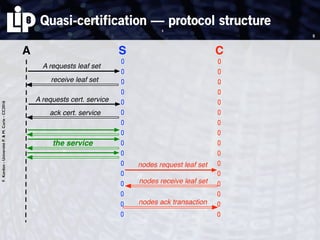
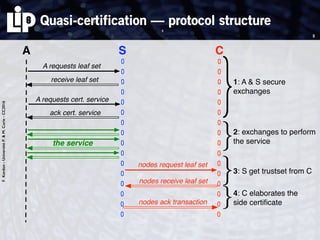
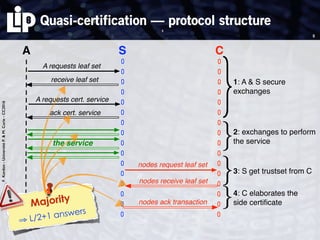
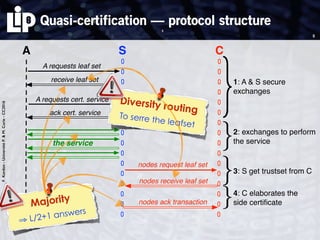
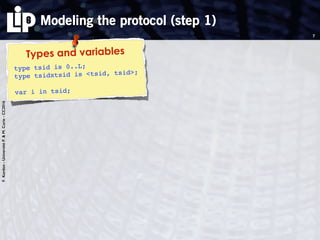
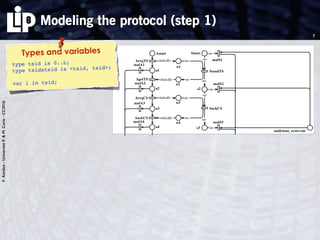
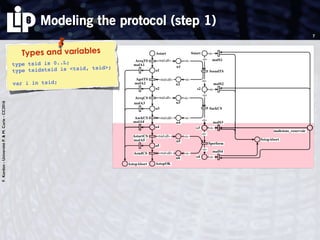
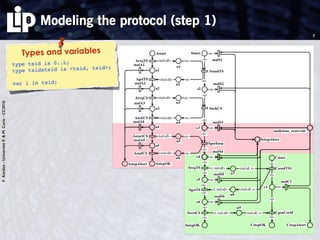
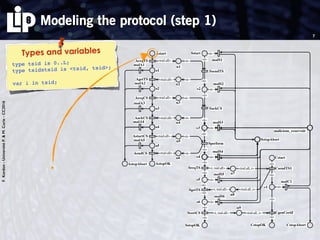
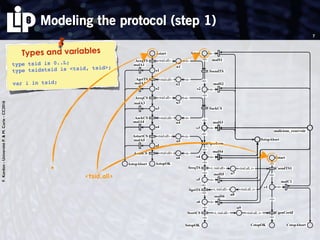
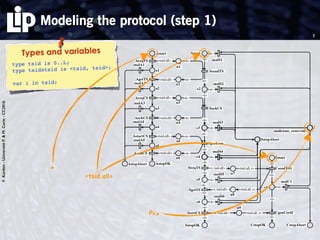
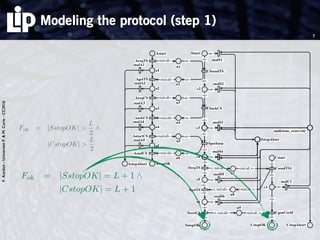
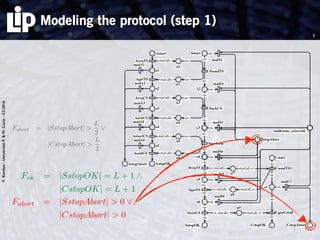
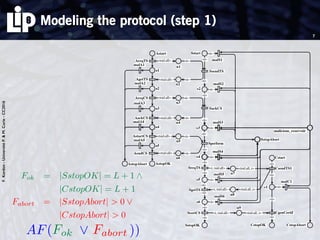
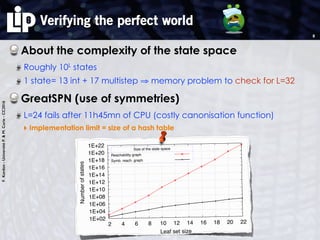
The document discusses building and verifying a quasi-certification entity over distributed hash tables. It motivates the need for certification of digital actions and compares centralized vs decentralized certification solutions. It then describes the key entities and protocol for providing quasi-certification of an action by an actor through distributed consensus using a certification authority and nodes in a distributed hash table leaf set. The protocol is modeled using Petri nets to analyze it in a perfect world without errors.




![F.Kordon-UniversitéP.&M.Curie-CC2016
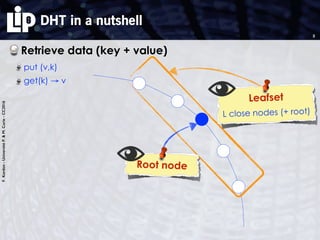
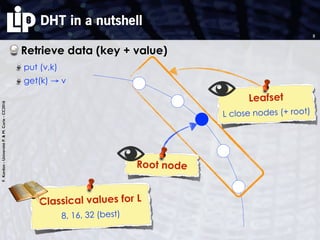
The verification process
Proof (by any method?)
Proven to be undecidable [FLP 85]
6](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-22-320.jpg)
![F.Kordon-UniversitéP.&M.Curie-CC2016
The verification process
Proof (by any method?)
Proven to be undecidable [FLP 85]
So what?
Being pragmatic
Going for «quasi»
6](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-23-320.jpg)
![F.Kordon-UniversitéP.&M.Curie-CC2016
The verification process
Proof (by any method?)
Proven to be undecidable [FLP 85]
So what?
Being pragmatic
Going for «quasi»
Two steps
1. modeling the protocol in a perfect world (no error)
Use of Petri nets
2. Probabilistic analysis to evaluate the failure rate
Use of a classical fault model,
building a formula + numeric evaluation
6](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-24-320.jpg)








![F.Kordon-UniversitéP.&M.Curie-CC2016
Formulas and experimental values
Protocol failure
More that L/2 nodes are malicious
The formula:
10
PL+1
i=1
L+1
i pi
(1 p)L+1 i
PL
2
i=1
L+1
i pi
(1 p)L+1 i
at most L+1
malicious nodes
at most L/2
malicious nodes
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
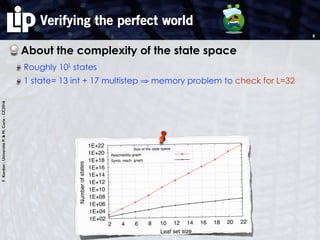
1.16e-43
1 4 8 12 16 20 24 28
Amount of faulty nodes [k]
CORPS 5% of faulty nodes
FIGURE 5.1. Probability to have more than k malicinodes
L DHT - p = 0.3 CORPS - p = 0.05
8 0.188 6.64 ⇥ 10 5
16 0.079 6.57 ⇥ 10 8
32 0.016 8.24 ⇥ 10 14
TABLE 3. Probability of failure of the transaction betweA and S
From equation 5.6 we can deduce the probability thaS won’t respond to the RequestInit or won’t send thfinal ACKs as
PAS = (1 P>L/2)P>|L|/2 + P>|L|/2
PAS = 2P>|L|/2 P 2
>|L|/2
(5.7
Table 3 shows the probability of failure between Aand S, for a trustset size of |L| = {8, 16, 32} nodes, andcompares a quasi CA built directly above the DHT toone built above CORPS. We consider that the worstcase is when the malicious nodes represent 30% of theDHT nodes. In](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-45-320.jpg)
![F.Kordon-UniversitéP.&M.Curie-CC2016
Formulas and experimental values
Protocol failure
More that L/2 nodes are malicious
The formula:
Inappropriate certificate generation
Two parts
‣ Existence of more L/2 malicious nodes
‣ Unable to retrieve at least L/2 + 1 identical answers
The formula (combines problems between S and C)
10
PL+1
i=1
L+1
i pi
(1 p)L+1 i
PL
2
i=1
L+1
i pi
(1 p)L+1 i
at most L+1
malicious nodes
at most L/2
malicious nodes
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
1.16e-43
1 4 8 12 16 20 24 28
Amount of faulty nodes [k]
CORPS 5% of faulty nodes
FIGURE 5.1. Probability to have more than k malicinodes
L DHT - p = 0.3 CORPS - p = 0.05
8 0.188 6.64 ⇥ 10 5
16 0.079 6.57 ⇥ 10 8
32 0.016 8.24 ⇥ 10 14
TABLE 3. Probability of failure of the transaction betweA and S
From equation 5.6 we can deduce the probability thaS won’t respond to the RequestInit or won’t send thfinal ACKs as
PAS = (1 P>L/2)P>|L|/2 + P>|L|/2
PAS = 2P>|L|/2 P 2
>|L|/2
(5.7
Table 3 shows the probability of failure between Aand S, for a trustset size of |L| = {8, 16, 32} nodes, andcompares a quasi CA built directly above the DHT toone built above CORPS. We consider that the worstcase is when the malicious nodes represent 30% of theDHT nodes. In
1 (1 P> L
2
)2](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-46-320.jpg)
![F.Kordon-UniversitéP.&M.Curie-CC2016
Formulas and experimental values
Protocol failure
More that L/2 nodes are malicious
The formula:
Inappropriate certificate generation
Two parts
‣ Existence of more L/2 malicious nodes
‣ Unable to retrieve at least L/2 + 1 identical answers
The formula (combines problems between S and C)
10
PL+1
i=1
L+1
i pi
(1 p)L+1 i
PL
2
i=1
L+1
i pi
(1 p)L+1 i
at most L+1
malicious nodes
at most L/2
malicious nodes
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
1.16e-43
1 4 8 12 16 20 24 28
Amount of faulty nodes [k]
CORPS 5% of faulty nodes
FIGURE 5.1. Probability to have more than k malicinodes
L DHT - p = 0.3 CORPS - p = 0.05
8 0.188 6.64 ⇥ 10 5
16 0.079 6.57 ⇥ 10 8
32 0.016 8.24 ⇥ 10 14
TABLE 3. Probability of failure of the transaction betweA and S
From equation 5.6 we can deduce the probability thaS won’t respond to the RequestInit or won’t send thfinal ACKs as
PAS = (1 P>L/2)P>|L|/2 + P>|L|/2
PAS = 2P>|L|/2 P 2
>|L|/2
(5.7
Table 3 shows the probability of failure between Aand S, for a trustset size of |L| = {8, 16, 32} nodes, andcompares a quasi CA built directly above the DHT toone built above CORPS. We consider that the worstcase is when the malicious nodes represent 30% of theDHT nodes. In
1
⇣
1
PL+1
i=1
L+1
i pi
(1 p)L+1 i
+
PL
2
i=1
L+1
i pi
(1 p)L+1 i
⌘2
1 (1 P> L
2
)2](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-47-320.jpg)
![F.Kordon-UniversitéP.&M.Curie-CC2016
Formulas and experimental values
Protocol failure
More that L/2 nodes are malicious
The formula:
Inappropriate certificate generation
Two parts
‣ Existence of more L/2 malicious nodes
‣ Unable to retrieve at least L/2 + 1 identical answers
The formula (combines problems between S and C)
10
PL+1
i=1
L+1
i pi
(1 p)L+1 i
PL
2
i=1
L+1
i pi
(1 p)L+1 i
at most L+1
malicious nodes
at most L/2
malicious nodes
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
⎞
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎟
⎠
1.16e-43
1 4 8 12 16 20 24 28
Amount of faulty nodes [k]
CORPS 5% of faulty nodes
FIGURE 5.1. Probability to have more than k malicinodes
L DHT - p = 0.3 CORPS - p = 0.05
8 0.188 6.64 ⇥ 10 5
16 0.079 6.57 ⇥ 10 8
32 0.016 8.24 ⇥ 10 14
TABLE 3. Probability of failure of the transaction betweA and S
From equation 5.6 we can deduce the probability thaS won’t respond to the RequestInit or won’t send thfinal ACKs as
PAS = (1 P>L/2)P>|L|/2 + P>|L|/2
PAS = 2P>|L|/2 P 2
>|L|/2
(5.7
Table 3 shows the probability of failure between Aand S, for a trustset size of |L| = {8, 16, 32} nodes, andcompares a quasi CA built directly above the DHT toone built above CORPS. We consider that the worstcase is when the malicious nodes represent 30% of theDHT nodes. In
1
⇣
1
PL+1
i=1
L+1
i pi
(1 p)L+1 i
+
PL
2
i=1
L+1
i pi
(1 p)L+1 i
⌘2
1 (1 P> L
2
)2
L DHT - p = 0.3 CORPS - p = 0.058 0.216 4.97 ⇥ 10 4
16 0.075 3.50 ⇥ 10 8
32 0.014 4.24 ⇥ 10 13](https://image.slidesharecdn.com/osis-2016scuritbuildingandverifyingaquasi-certificationentityoverditributedhashtables-160518161705/85/Building-and-verifying-a-quasi-certification-entity-over-Distributed-Hash-Tables-48-320.jpg)




