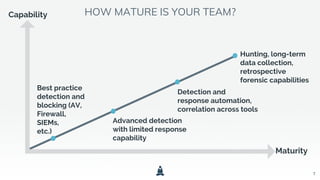
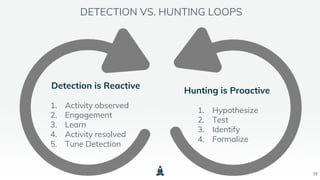
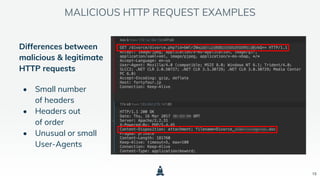
The document discusses building a threat hunting practice in the cloud, emphasizing the importance of being proactive in identifying unknown threats rather than just reacting to known ones. It outlines components necessary for effective threat hunting, including data collection, context, and analytics capabilities offered by cloud technology. Best practices for threat hunting and a call to action for continuous learning and collaboration are highlighted.