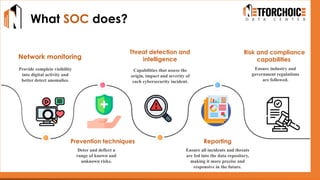
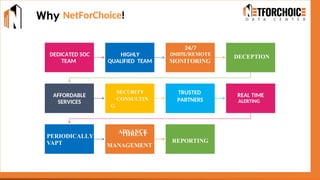
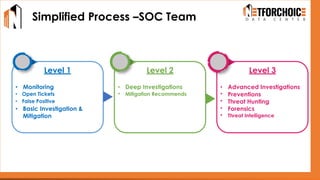
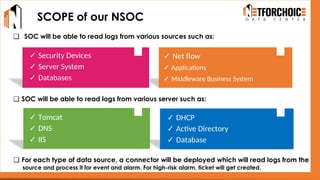
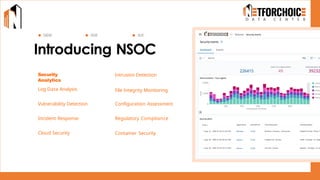
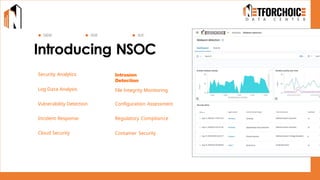
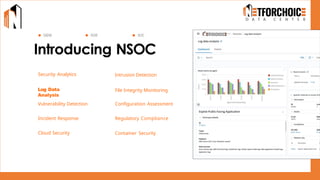
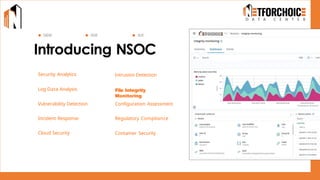
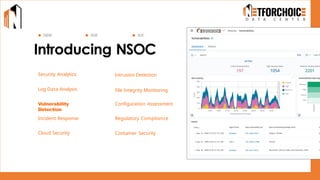
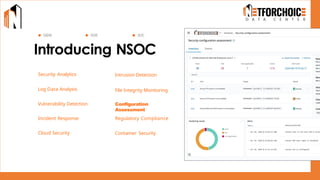
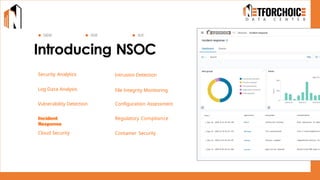
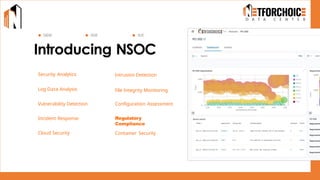
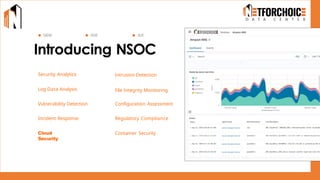
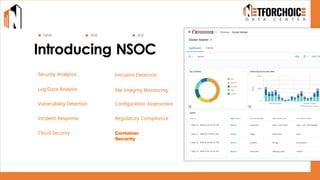
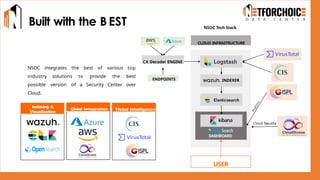
NetForChoice’s NSOC offers 24/7 advanced threat monitoring, real-time incident response, and complete log analytics. Integrated with SIEM, XDR, and cloud-native tools, it ensures regulatory compliance, minimizes risks, and enhances IT security for enterprises with precision, efficiency, and affordability. Trusted by 50k+ clients across industries.