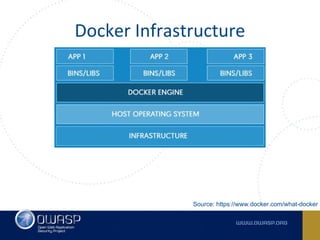
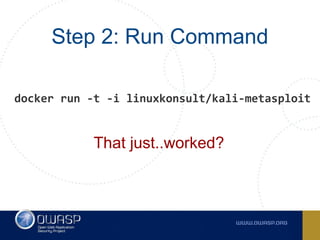
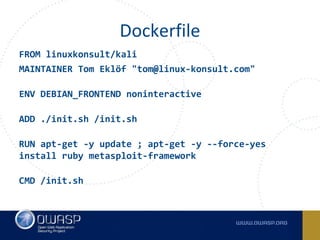
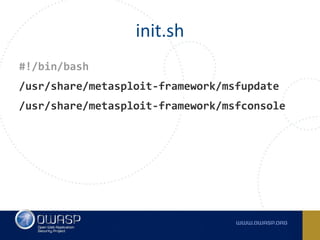
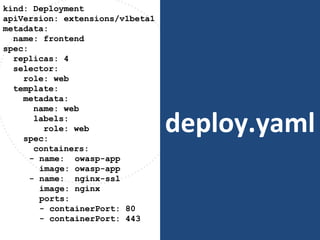
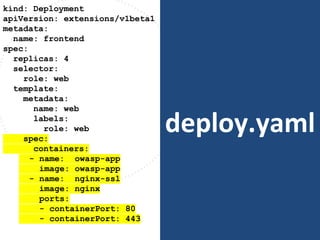
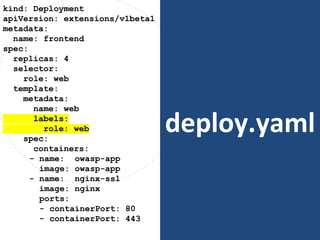
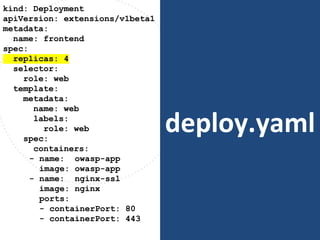
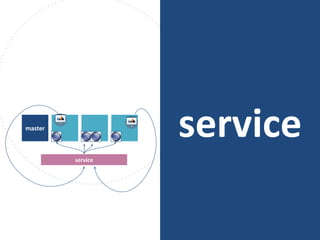
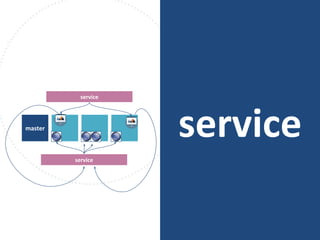
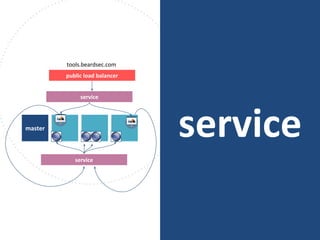
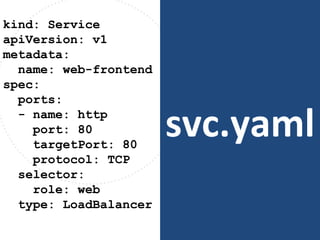
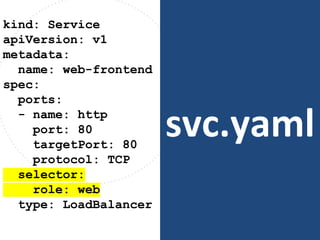
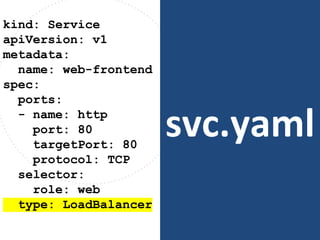
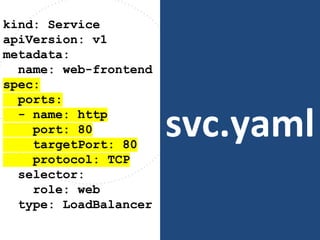
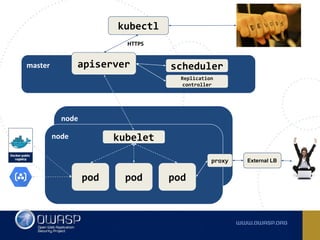
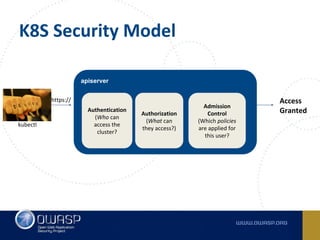
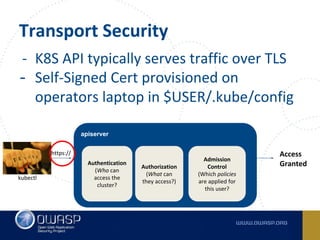
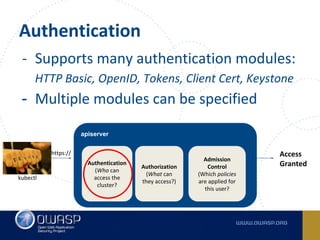
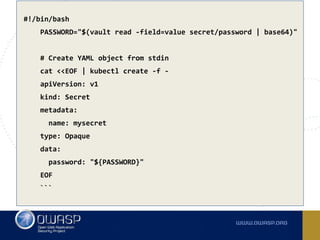
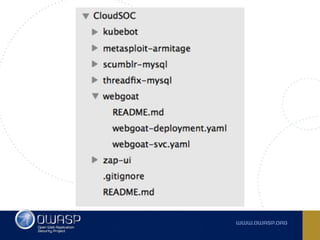
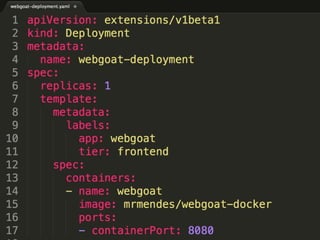
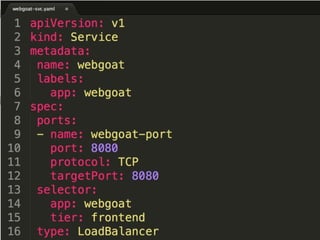
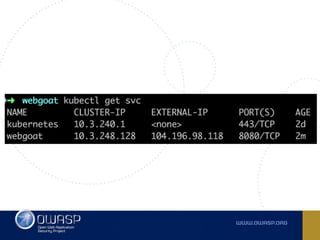
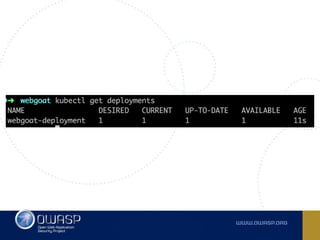
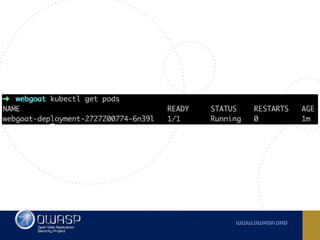
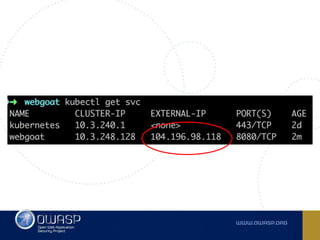
The document discusses best practices for containerizing applications with a focus on security aspects related to Docker and Kubernetes. It covers steps for setting up a secure container environment, including the installation of tools, configuration of databases, and the importance of inspecting Docker images. The document also highlights Kubernetes features such as scaling, orchestration, security models, and the management of secrets within containers.






![Security as a [ ]](https://image.slidesharecdn.com/containerizingyoursoc1-161017203456/85/Containerizing-your-Security-Operations-Center-7-320.jpg)