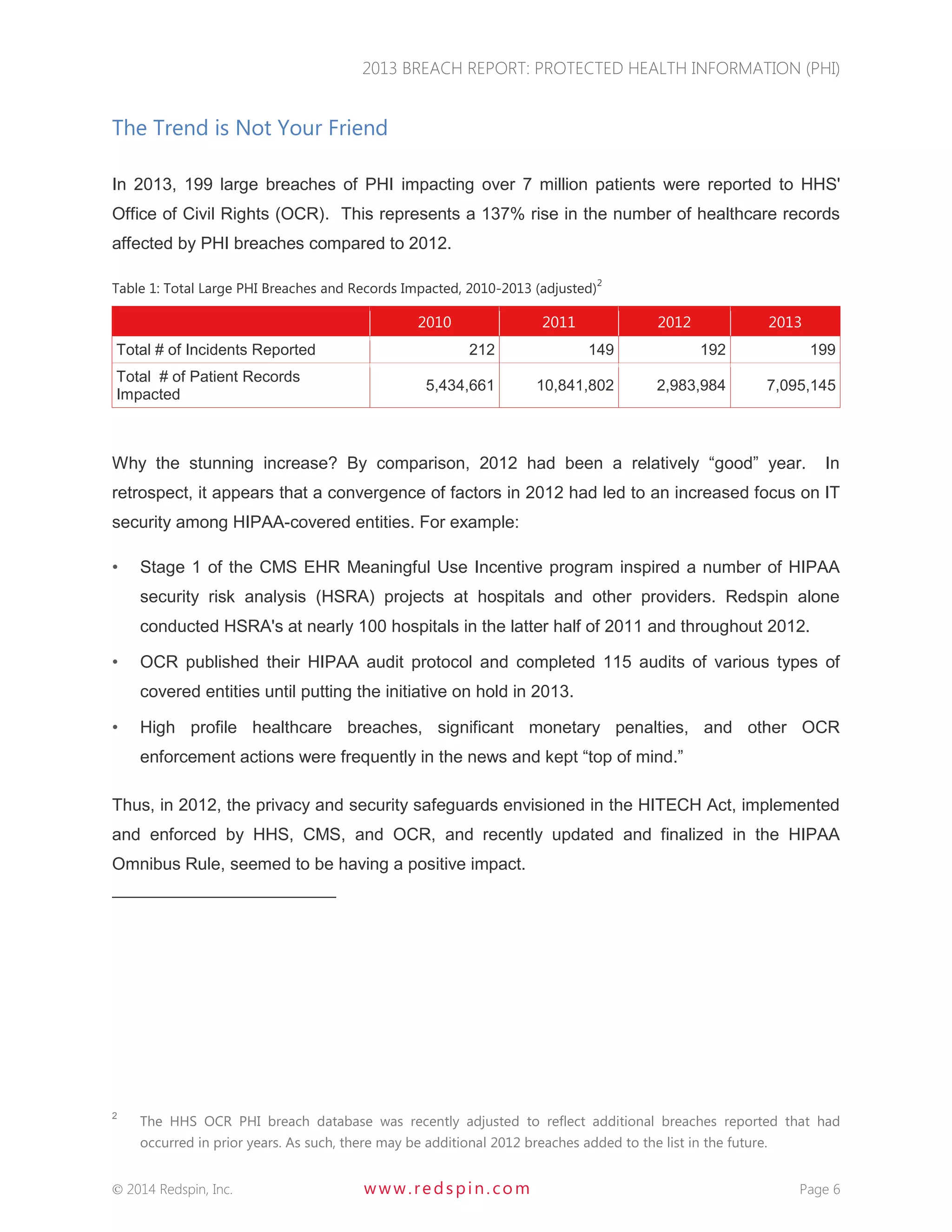
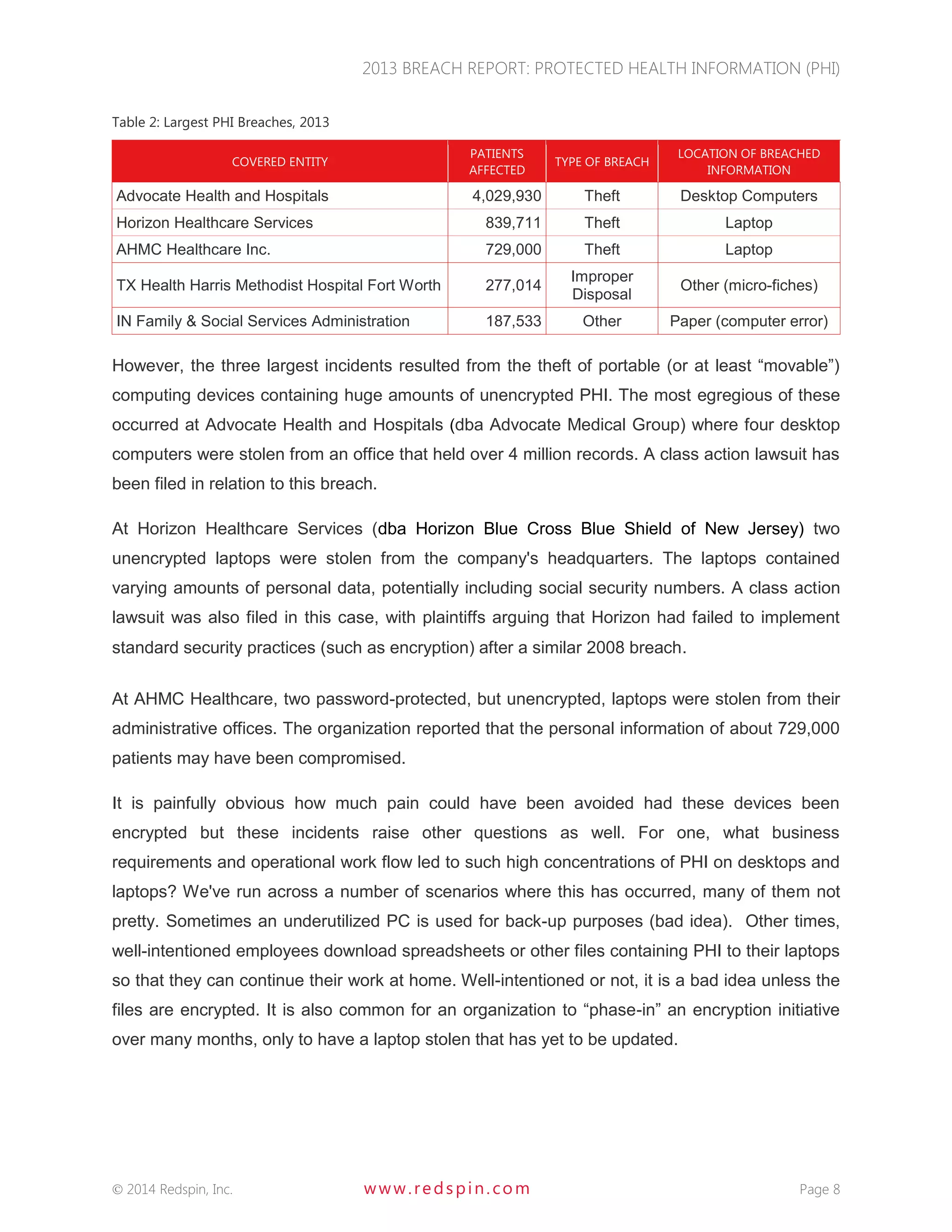
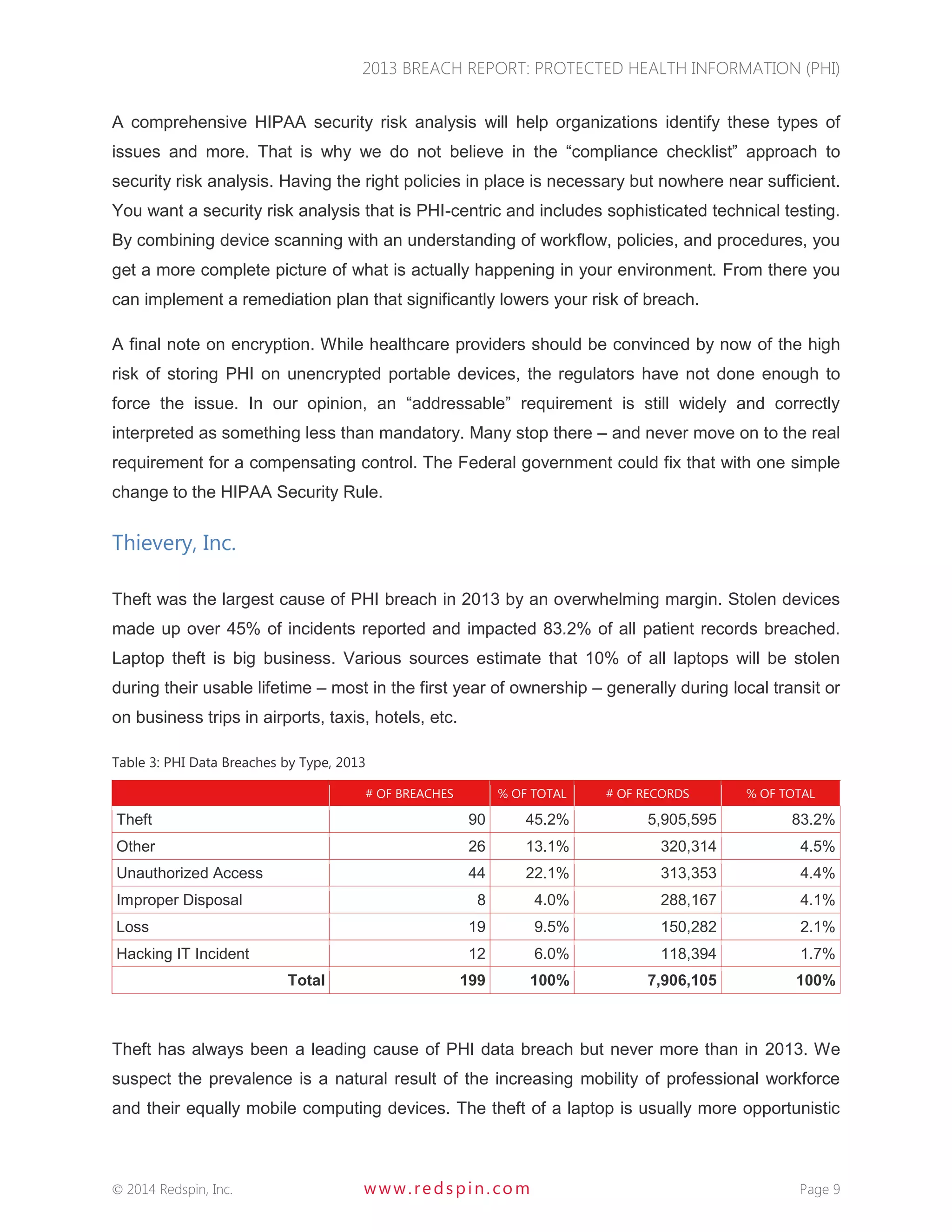
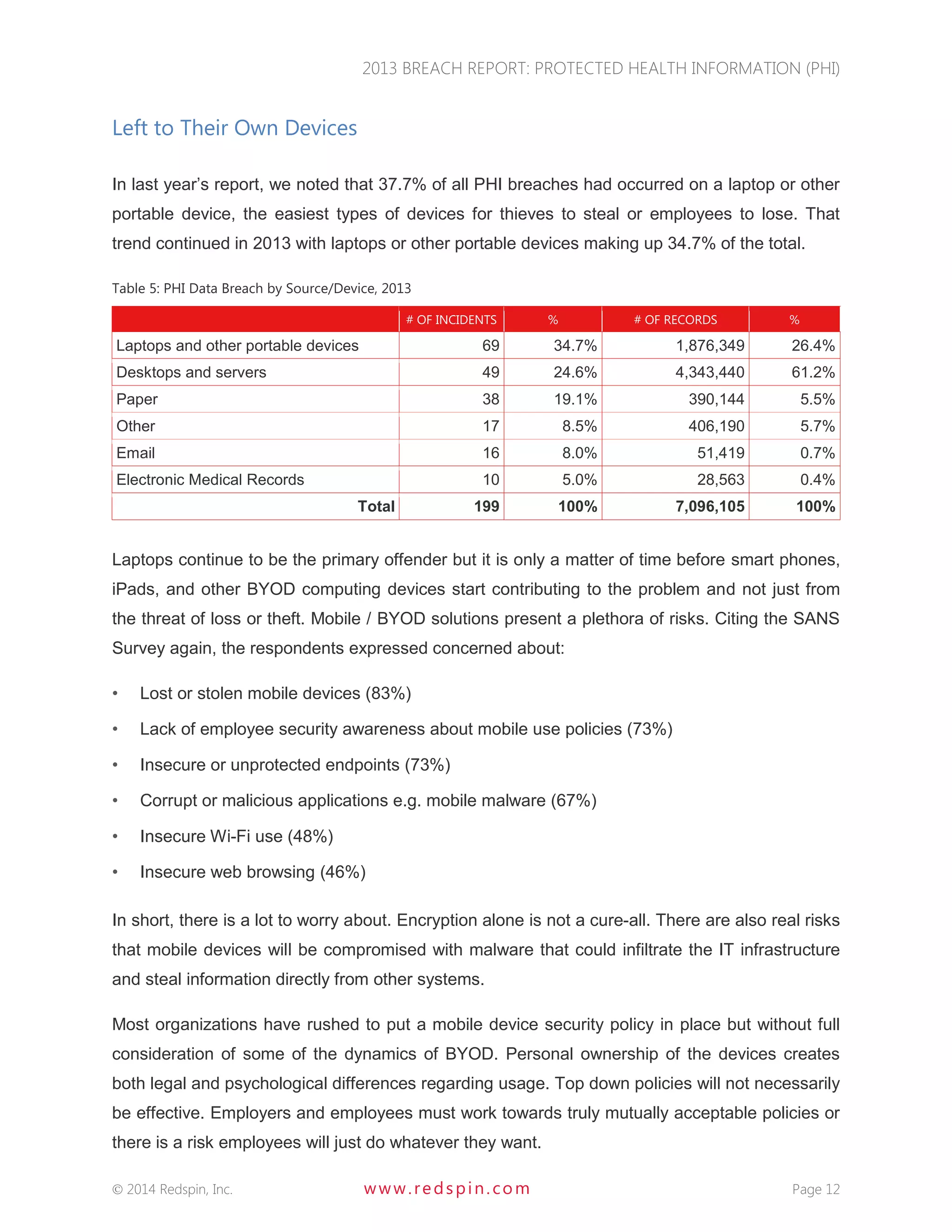
The 2013 Breach Report from Redspin reveals that there were a total of 804 large breaches of protected health information (PHI) since 2009, affecting over 29 million patient records, with 199 breaches reported in 2013 alone. The report highlights a 137% increase in patient records breached compared to 2012, primarily due to theft of unencrypted portable devices, which constituted 83.2% of breaches in 2013. Redspin emphasizes the need for improved security measures, including encryption, to prevent further incidents and protect patient information.