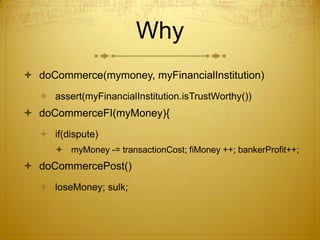
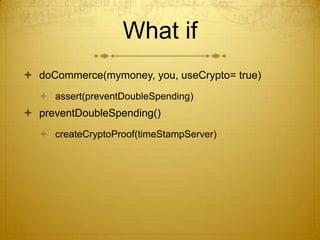
This document discusses Bitcoin, a peer-to-peer electronic cash system. It outlines problems with traditional financial institutions, such as the risk of disputes and transaction fees. It then introduces Bitcoin as an alternative that allows for direct peer-to-peer transactions using cryptography to prevent double spending, through techniques like digital signatures, timestamping, proof of work, and an incentive-driven network. The document provides high-level explanations of these core Bitcoin concepts and technologies.