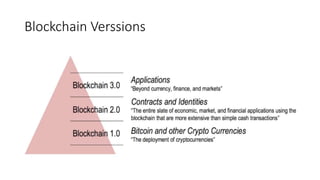
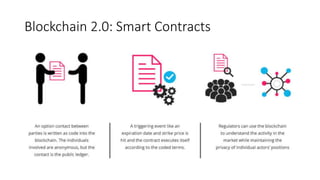
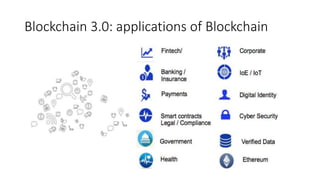
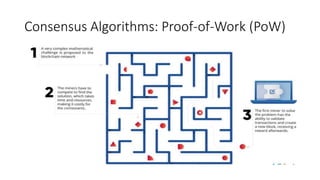
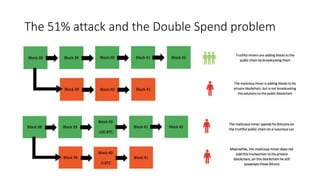
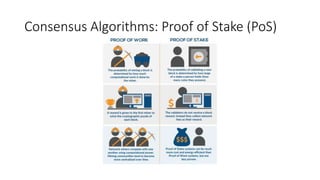
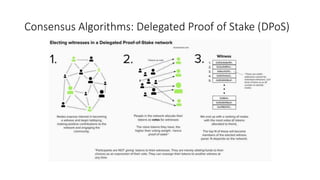
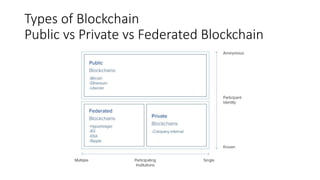
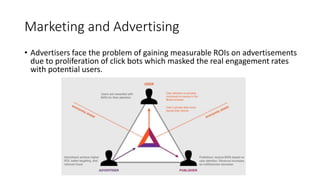
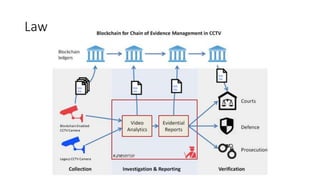
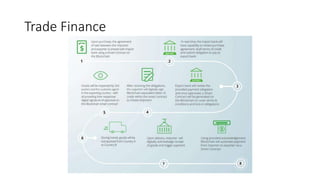
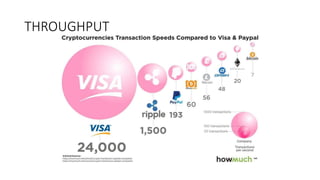
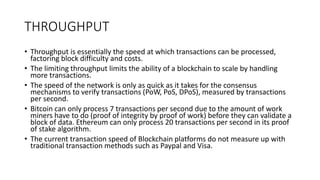
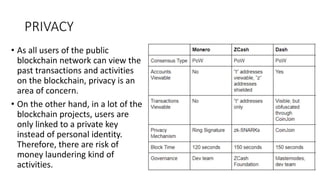
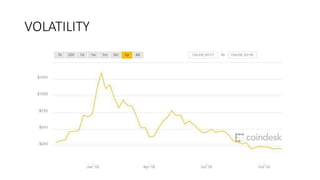
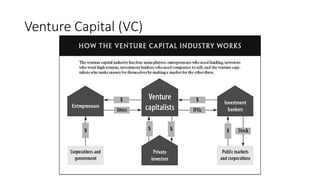
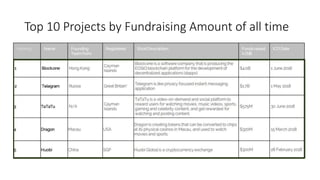
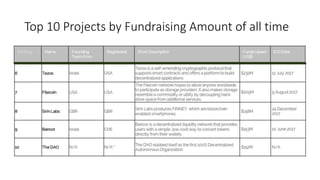
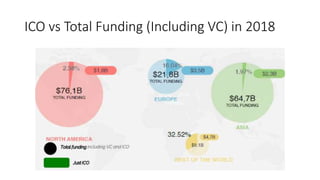
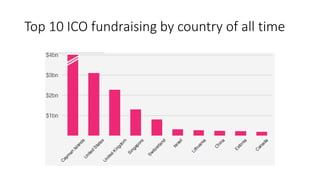
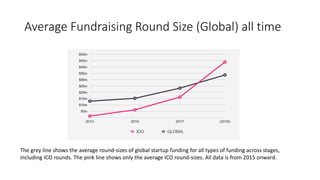
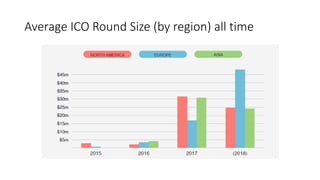
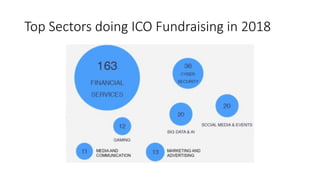
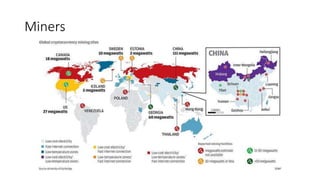
The document provides an extensive overview of the blockchain ecosystem, covering its evolution from cryptocurrency (Blockchain 1.0) to smart contracts (Blockchain 2.0) and various applications across sectors (Blockchain 3.0). It details consensus algorithms like proof-of-work and proof-of-stake, explaining their roles in transaction validation and network security. Additionally, the document outlines practical use cases in fields such as real estate, gaming, marketing, e-commerce, law, healthcare, and trade finance.