Biometric Identification Evolves to Provide Unprecedented Security & Reliability
•
0 likes•26 views
Since it was first introduced in 1858, biometric technology has come a long way. Today, highly advanced, highly accurate biometric technologies can authenticate identity using a person’s fingerprint, iris/eye, facial features, and voice, to name a few. With the rise in identity and data theft, the global financial services industry is ramping up its use of biometrics to provide convenient, reliable, and highly secure protection.
Report
Share
Report
Share
Download to read offline
Recommended
Identive | Press Release | Identive Opens the Door to Physical Access with NF...

Identive Opens the Door to Physical Access with NFC-Enabled Smartphones
http://identive-group.com
http://identivenfc.com
Internet of Things

In this presentation, Sai introduces IoT and associated trends. Sai is interested in Big Data analytics of data generated in the IoT space.
Biometric Trends for 2017 Webinar

The use of biometrics to enable user authentication and identity assurance is an essential improvement over usernames and passwords, and innovations in mobile devices, wearables, and other technologies are helping bring biometrics to mainstream audiences. In this webinar, we'll discuss developments in biometrics and related technologies and how different markets are likely to deploy biometric authentication in 2017.
Pay-Cloak:Biometric

Continuous improvements in technology and quality of life have had a strong impact on the development of payment techniques. With the evolution of near-field communication (NFC) technology, contactless payment has received recent attention because of its short-range, conducive nature. As mobile computing made great leaps due to enormous development in the smart phone platform, companies like Google, Samsung, and Apple embedded NFC in smart phones to provide on-the-go payment capabilities, eliminating the need for payment cards. But due to interoperability and high cost, these technologies are not available to everyone. Dr. B Srinivasa Rao | Ch. Sphoorthi | K. TejaSree | G. Sai Snigdha | V. S R Harika"Pay-Cloak:Biometric" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-2 | Issue-3 , April 2018, URL: http://www.ijtsrd.com/papers/ijtsrd11430.pdf http://www.ijtsrd.com/computer-science/other/11430/pay-cloakbiometric/dr-b-srinivasa-rao
What are Broadband Solutions

This presentation describes the concept of Broadband solutions and its different types
Internet of things (IoT) Patents | Internet of things (IoT) based Systems & M...

Internet of things (IoT) Patents | Internet of things (IoT) based Systems & M...Prity Khastgir IPR Strategic India Patent Attorney Amplify Innovation
Internet of Things (IoT) from a Patent perspective | IPR strategy as a part of your Business Goal: Understanding the patent framework of internet of things (IoT). The following ppt illustrates some of the main technologies filed in the Internet of Things (IoT) sector.
Companies entering into the IoT sector need to have an IPR strategy for a profitable business in the long run.
Linas Eriksonas, Market for mobile biometrics

Presentation given at the lunch-time workshop for IT experts and developers as part of the dissemination activities of the project PIDaaS (Private Identity as a Service)
Near Field Communications Technology Overview

This presentation was created as an overview of Near Field Communications (NFC) Technology prepared for Kennesaw State University's WebMBA program.
Recommended
Identive | Press Release | Identive Opens the Door to Physical Access with NF...

Identive Opens the Door to Physical Access with NFC-Enabled Smartphones
http://identive-group.com
http://identivenfc.com
Internet of Things

In this presentation, Sai introduces IoT and associated trends. Sai is interested in Big Data analytics of data generated in the IoT space.
Biometric Trends for 2017 Webinar

The use of biometrics to enable user authentication and identity assurance is an essential improvement over usernames and passwords, and innovations in mobile devices, wearables, and other technologies are helping bring biometrics to mainstream audiences. In this webinar, we'll discuss developments in biometrics and related technologies and how different markets are likely to deploy biometric authentication in 2017.
Pay-Cloak:Biometric

Continuous improvements in technology and quality of life have had a strong impact on the development of payment techniques. With the evolution of near-field communication (NFC) technology, contactless payment has received recent attention because of its short-range, conducive nature. As mobile computing made great leaps due to enormous development in the smart phone platform, companies like Google, Samsung, and Apple embedded NFC in smart phones to provide on-the-go payment capabilities, eliminating the need for payment cards. But due to interoperability and high cost, these technologies are not available to everyone. Dr. B Srinivasa Rao | Ch. Sphoorthi | K. TejaSree | G. Sai Snigdha | V. S R Harika"Pay-Cloak:Biometric" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-2 | Issue-3 , April 2018, URL: http://www.ijtsrd.com/papers/ijtsrd11430.pdf http://www.ijtsrd.com/computer-science/other/11430/pay-cloakbiometric/dr-b-srinivasa-rao
What are Broadband Solutions

This presentation describes the concept of Broadband solutions and its different types
Internet of things (IoT) Patents | Internet of things (IoT) based Systems & M...

Internet of things (IoT) Patents | Internet of things (IoT) based Systems & M...Prity Khastgir IPR Strategic India Patent Attorney Amplify Innovation
Internet of Things (IoT) from a Patent perspective | IPR strategy as a part of your Business Goal: Understanding the patent framework of internet of things (IoT). The following ppt illustrates some of the main technologies filed in the Internet of Things (IoT) sector.
Companies entering into the IoT sector need to have an IPR strategy for a profitable business in the long run.
Linas Eriksonas, Market for mobile biometrics

Presentation given at the lunch-time workshop for IT experts and developers as part of the dissemination activities of the project PIDaaS (Private Identity as a Service)
Near Field Communications Technology Overview

This presentation was created as an overview of Near Field Communications (NFC) Technology prepared for Kennesaw State University's WebMBA program.
Sbvlc secure barcode based visible light communication for smartphones

Sbvlc secure barcode based visible light communication for smartphones
Do Your Projects With Technology Experts
To Get this projects Call : 9566355386 / 99625 88976
Web : http://www.lemenizinfotech.com
Web : http://www.ieeemaster.com
Mail : projects@lemenizinfotech.com
Blog : http://ieeeprojectspondicherry.weebly.com
Blog : http://www.ieeeprojectsinpondicherry.blogspot.in/
Youtube:https://www.youtube.com/watch?v=eesBNUnKvws
Top 10 trends of internet of things in 2020

The Internet of Things (IoT) is actively shaping both the industrial and consumer worlds. Smart tech finds its way to every business and consumer domain there is-from retail to healthcare, from finances to logistics-and a missed opportunity strategically employed by a competitor can easily qualify as a long-term failure for companies who don't innovate. Check out our latest PPT for more details.
Internet Of Things (IoT) 

Internet of Things (IOT) in simple terms we can describe the iot with a definition it is "A virtual world with a physical touch" it is connected with every thing that are related to the magnetic waves.
It is a new innovation in the era of technology that can change the face of technology and even we can see the change around us.
Please do like and comment
Sbvlc secure barcode based visible light communication for smartphones

SBVLCSecure Barcode based Visible Light Communication for Smartphones
Web : http://www.lemenizinfotech.com
Web : http://ieeemaster.com
Web : http://www.lemenizinfotech.com/android-ieee-projects-2016-2017-2/
Web : http://ieeemaster.com/android-ieee-projects-2016-2017/
Address: 36, 100 Feet Road(Near Indira Gandhi Statue), Natesan Nagar, Pondicherry-605 005
Contact numbers: +91 95663 55386, 99625 88976 (0413) 420 5444
Mail : projects@lemenizinfotech.com
Mobile : 9566355386 / 9962588976
Keynote Speaker Janice Kephart - Founder and CEO of The Secure Identity and B...

Janice recently returned from a Special Counsel position with the Senate Judiciary Committee, where she was asked to testify and then return to staff to support the national, border and identity security aspects of the now Senate-passed immigration reform legislation. Ms. Kephart is an internationally recognized border and ID security expert, who served as counsel to the 9/11 Commission and was a key author of the Staff Monograph, 9/11 and Terrorist Travel as well as the immigration and identity security-related facts and recommendations in the 9/11 Commission Report.
More info: http://www.sibassoc.org/#!aboutsiba/csgz
Janice speaks regularly at conferences, to international media, publishes articles and opeds around the world, and has testified before Congress 16 times on issues of border and ID security.
Internet of Things Challenges and Solutions

The Internet of things IoT is a relatively new concept. It presents numerous benefits to consumers and proves a financial boon for businesses. Pervasive introduction of sensors and devices into currently intimate spaces, such as homes, cars, and wearables, poses some challenges. There are also challenges in deploying IoT by government agencies and private industries. This paper attempts to address these challenges and offers solutions. Matthew N. O. Sadiku | Adedamola Omotoso | Shuza Binzaid | Sarhan M. Musa "Internet of Things: Challenges and Solutions" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-3 | Issue-6 , October 2019, URL: https://www.ijtsrd.com/papers/ijtsrd29302.pdf Paper URL: https://www.ijtsrd.com/engineering/electrical-engineering/29302/internet-of-things-challenges-and-solutions/matthew-n-o-sadiku
IoT Business Reality & Patent Development

The development of patents (drafting for new applications, creating value through prosecution and strategic patent portfolio development) regarding IoT innovation should consider the IoT business reality. Especially, the IoT patent development should support future development of IoT businesses and commercial implementations of IoT innovations. Additionally, the IoT patent development should support for both ecosystem players’ exploitation and customers’ use of the IoT innovation. The disclosures of the IoT patent can be considered as a system that is consist of several subsystems: environmental context, IoT sensor, information, transfer mean and processing tool.
Patenting in Mobile Application (App) & Software Based Technology | How to Pa...

Patenting in Mobile Application (App) & Software Based Technology | How to Pa...Prity Khastgir IPR Strategic India Patent Attorney Amplify Innovation
Yes, You Can Patent Your Mobile App Idea. You need to determine whether Your Mobile App Need A Patent. Important step is to search the existing patent database to determine patentability of the invention. Mobile app developers generally select to file provisional patent application before patent office. Overview of different mobile app patent examples are discussed in this patent presentation. As discussed mobile app patents are patentable. We can assist you to write a mobile application patent & how to patent a mobile app idea.
Mobile app patent searching step is important before filing a patent before the patent office. The mobile app development in India is a booming business. One can copyright various features of the mobile app.
Crossing the Rubicon: Digital Signatures and Digital Transformation

Digital signatures are the perfect tool for digital transformation of your organization. Open, standard digital signatures enable you to easily create truly paperless business processes. With digital signatures, your pdf's and other document types include the digital signature, there is no need to rely on a third signature company for signature verification. Your digitally signed pdf, itself, serves as your original document. Its signatures may be verified by using the free PDF Reader or other applications. Open digital signatures ensure no lock-in and full interoperability between signature applications from multiple vendors.
Security Protocols for Mobile Banking Application 

Mobile banking applications have become a part of
the daily needs of today’s end user. Mobile banking applications
provide multiple features for the end user to perform without the
need to visit the bank branch, ATM machine or calling customer
service, such as opening an account, checking the balance, money
transfer and paying bills. Current banking companies are facing
a problem providing a secure mobile banking application for
customers as there are several threats and challenges appearing
in current mobile banking applications, such as incomplete information,
information leakage loss and distort, virus attacks, denial
of service attack, network challenges and transport challenges.
In this study, we discuss several security protocols solutions to
enhance the security of the current mobile banking applications.
Secure Mobile Banking Approach (SMBA) to enhance the user
financial data transmission in a protected environment, Secure
Short Message Service (SMS) protocol to secure the message
communication system between the end user and the bank
server, Secure General Packet Radio Service (GPRS) protocol to
secure the overall communications between the end user and the
bank server and biometric authentication systems to secure the
authentication of the end users for the bank server such as the
Facial Recognition System. The paper also presents guidelines
for the mobile banking application developers from the Saudi
Arabia Banking Authorities (SABA) to implement and end user
guidelines to follow up while using the mobile device to increase
the security of the secure mobile banking applications.
International Journal of Computer Science and Information Security,IJCSIS ISSN 1947-5500, Pittsburgh, PA, USA
Email: ijcsiseditor@gmail.com
http://sites.google.com/site/ijcsis/
https://google.academia.edu/JournalofComputerScience
https://www.linkedin.com/in/ijcsis-research-publications-8b916516/
http://www.researcherid.com/rid/E-1319-2016
IoT Innovation Fund for Business Growth

Liquidax Capital, LLC is an investment advisory firm sponsoring and managing private equity innovation funds. The Liquidax debut fund; Liquidax Global Exchange Fund I, LP focuses on the acquisition and monetization of Internet of Things (IoT) technologies and intellectual property rights for target injection into numerous public companies operating on global stock exchanges, as well as, venture capital backed private companies boosting business growth and expediting exits.
Liquidax invests its IoT innovation platform to partner companies for providing competitive advantages in the IoT market. Liquidax's strategically packaged technology that is in complete alignment with IPR enables cost effective and faster time to market innovation.
Four ways to secure banking transaction by biometrics

The Biometric Identification Technology surly has the ability to eliminate loopholes of a banking system that criminals can exploit and has the versatility to secure all financial transactions such as Branch Banking, Internet Banking, Mobile Banking and ATM Networks.
Patent Insights: Connected Car Innovations

Liquidax Capital – Summary Innovation Brief #CC-1606 Patent Insights: Toyota, Ford, Hyundai, GM, Allstate Connected Car Innovations / Internet of Things As outlined by PWC; “Worldwide sales of connected car products will increase almost fourfold between 2015 and 2020, adding more than $149 billion in revenues in the passenger car segment alone. Technologies will offer buyers greater flexibility in personalizing the cars they choose, and enable greater contact between manufacturers and customers strengthening the bonds between them and increasing loyalty to the brand. Consumers are already seeing new capabilities and features in the connected auto markets. The below (5) patents & applications highlight the view and vision of some of the largest auto companies in the world and outline products and services planned for the market.
Survey: Identity Authentication For Banks In Malaysia

These infographics are based on independent survey of 5,000 people in 10 countries carried out for FICO in February 2020. This is for Malaysia.
The statistics include:
1.Why Passwords don't work
2.Biometric acceptance
Outsmarting the Smart City: DISCOVERING AND ATTACKING THE TECHNOLOGY THAT RUN...

The super computer gets a panoptic view of the city using data from cameras and sensor networks. The information obtained is used to manage the city’s infrastructure and technology as well as to maintain a database of personal information about citizens and their activities. In this article, we take a look at some of the real dangers facing today’s cities from malicious hackers.
Speakers:
Daniel Crowley , Research Baron at IBM X-Force Red
Jennifer Savage , Security Researcher at Threatcare
Mauro Paredes , Managing Consultant at IBM X-Force Red
Bio metrics in secure e transaction

Information security is concerned with the
assurance of confidentially, integrity and availability of
information in all forms. This is the ancient Greek word:
bios = “life” and metron = “measure.” In the present day
world, online shopping using WAP enabled mobile phone
has widely come into use. Credit cards serve as the currency
during e-business and e-Shopping. As the Hacking or
Spoofing or the Misuse of the credit card is continuously
increasing even you are using a secure network. Also, some
Spam software is sent to your system or device through the
internet that helps spammers to get the
desires relevant information about your credit card and
financial data. To solve these problems or get out of these
insecurities the Bio-metric System that provides the secure
E-transaction by improving the prevention of data spoofing.
So in this paper, we have proposed a multi-biometric model
(integrating voice, fingerprint and facial scanning) that can
be embedded in a mobile phone, this making e-transactions
more secure.
NEC Public Safety | Digital Identity for Banks

The importance of being human-centric instead of techno-centric is now fundamentally assessed in the context of secure digital identity for the financial services landscape.
Forward-looking banks and financial institutions are increasingly responding with resources and investments that deliver NEC’s state-of-the-art authentication methods
to meet consumer expectations. As a result, NEC’s vantage point goes far beyond cutting-edge technologies and solutions, such as integration of multimodal biometrics. Brought to you by NEC. To find out more, do visit http://www.nec.com/safety
More Related Content
What's hot
Sbvlc secure barcode based visible light communication for smartphones

Sbvlc secure barcode based visible light communication for smartphones
Do Your Projects With Technology Experts
To Get this projects Call : 9566355386 / 99625 88976
Web : http://www.lemenizinfotech.com
Web : http://www.ieeemaster.com
Mail : projects@lemenizinfotech.com
Blog : http://ieeeprojectspondicherry.weebly.com
Blog : http://www.ieeeprojectsinpondicherry.blogspot.in/
Youtube:https://www.youtube.com/watch?v=eesBNUnKvws
Top 10 trends of internet of things in 2020

The Internet of Things (IoT) is actively shaping both the industrial and consumer worlds. Smart tech finds its way to every business and consumer domain there is-from retail to healthcare, from finances to logistics-and a missed opportunity strategically employed by a competitor can easily qualify as a long-term failure for companies who don't innovate. Check out our latest PPT for more details.
Internet Of Things (IoT) 

Internet of Things (IOT) in simple terms we can describe the iot with a definition it is "A virtual world with a physical touch" it is connected with every thing that are related to the magnetic waves.
It is a new innovation in the era of technology that can change the face of technology and even we can see the change around us.
Please do like and comment
Sbvlc secure barcode based visible light communication for smartphones

SBVLCSecure Barcode based Visible Light Communication for Smartphones
Web : http://www.lemenizinfotech.com
Web : http://ieeemaster.com
Web : http://www.lemenizinfotech.com/android-ieee-projects-2016-2017-2/
Web : http://ieeemaster.com/android-ieee-projects-2016-2017/
Address: 36, 100 Feet Road(Near Indira Gandhi Statue), Natesan Nagar, Pondicherry-605 005
Contact numbers: +91 95663 55386, 99625 88976 (0413) 420 5444
Mail : projects@lemenizinfotech.com
Mobile : 9566355386 / 9962588976
Keynote Speaker Janice Kephart - Founder and CEO of The Secure Identity and B...

Janice recently returned from a Special Counsel position with the Senate Judiciary Committee, where she was asked to testify and then return to staff to support the national, border and identity security aspects of the now Senate-passed immigration reform legislation. Ms. Kephart is an internationally recognized border and ID security expert, who served as counsel to the 9/11 Commission and was a key author of the Staff Monograph, 9/11 and Terrorist Travel as well as the immigration and identity security-related facts and recommendations in the 9/11 Commission Report.
More info: http://www.sibassoc.org/#!aboutsiba/csgz
Janice speaks regularly at conferences, to international media, publishes articles and opeds around the world, and has testified before Congress 16 times on issues of border and ID security.
Internet of Things Challenges and Solutions

The Internet of things IoT is a relatively new concept. It presents numerous benefits to consumers and proves a financial boon for businesses. Pervasive introduction of sensors and devices into currently intimate spaces, such as homes, cars, and wearables, poses some challenges. There are also challenges in deploying IoT by government agencies and private industries. This paper attempts to address these challenges and offers solutions. Matthew N. O. Sadiku | Adedamola Omotoso | Shuza Binzaid | Sarhan M. Musa "Internet of Things: Challenges and Solutions" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-3 | Issue-6 , October 2019, URL: https://www.ijtsrd.com/papers/ijtsrd29302.pdf Paper URL: https://www.ijtsrd.com/engineering/electrical-engineering/29302/internet-of-things-challenges-and-solutions/matthew-n-o-sadiku
IoT Business Reality & Patent Development

The development of patents (drafting for new applications, creating value through prosecution and strategic patent portfolio development) regarding IoT innovation should consider the IoT business reality. Especially, the IoT patent development should support future development of IoT businesses and commercial implementations of IoT innovations. Additionally, the IoT patent development should support for both ecosystem players’ exploitation and customers’ use of the IoT innovation. The disclosures of the IoT patent can be considered as a system that is consist of several subsystems: environmental context, IoT sensor, information, transfer mean and processing tool.
Patenting in Mobile Application (App) & Software Based Technology | How to Pa...

Patenting in Mobile Application (App) & Software Based Technology | How to Pa...Prity Khastgir IPR Strategic India Patent Attorney Amplify Innovation
Yes, You Can Patent Your Mobile App Idea. You need to determine whether Your Mobile App Need A Patent. Important step is to search the existing patent database to determine patentability of the invention. Mobile app developers generally select to file provisional patent application before patent office. Overview of different mobile app patent examples are discussed in this patent presentation. As discussed mobile app patents are patentable. We can assist you to write a mobile application patent & how to patent a mobile app idea.
Mobile app patent searching step is important before filing a patent before the patent office. The mobile app development in India is a booming business. One can copyright various features of the mobile app.
Crossing the Rubicon: Digital Signatures and Digital Transformation

Digital signatures are the perfect tool for digital transformation of your organization. Open, standard digital signatures enable you to easily create truly paperless business processes. With digital signatures, your pdf's and other document types include the digital signature, there is no need to rely on a third signature company for signature verification. Your digitally signed pdf, itself, serves as your original document. Its signatures may be verified by using the free PDF Reader or other applications. Open digital signatures ensure no lock-in and full interoperability between signature applications from multiple vendors.
Security Protocols for Mobile Banking Application 

Mobile banking applications have become a part of
the daily needs of today’s end user. Mobile banking applications
provide multiple features for the end user to perform without the
need to visit the bank branch, ATM machine or calling customer
service, such as opening an account, checking the balance, money
transfer and paying bills. Current banking companies are facing
a problem providing a secure mobile banking application for
customers as there are several threats and challenges appearing
in current mobile banking applications, such as incomplete information,
information leakage loss and distort, virus attacks, denial
of service attack, network challenges and transport challenges.
In this study, we discuss several security protocols solutions to
enhance the security of the current mobile banking applications.
Secure Mobile Banking Approach (SMBA) to enhance the user
financial data transmission in a protected environment, Secure
Short Message Service (SMS) protocol to secure the message
communication system between the end user and the bank
server, Secure General Packet Radio Service (GPRS) protocol to
secure the overall communications between the end user and the
bank server and biometric authentication systems to secure the
authentication of the end users for the bank server such as the
Facial Recognition System. The paper also presents guidelines
for the mobile banking application developers from the Saudi
Arabia Banking Authorities (SABA) to implement and end user
guidelines to follow up while using the mobile device to increase
the security of the secure mobile banking applications.
International Journal of Computer Science and Information Security,IJCSIS ISSN 1947-5500, Pittsburgh, PA, USA
Email: ijcsiseditor@gmail.com
http://sites.google.com/site/ijcsis/
https://google.academia.edu/JournalofComputerScience
https://www.linkedin.com/in/ijcsis-research-publications-8b916516/
http://www.researcherid.com/rid/E-1319-2016
IoT Innovation Fund for Business Growth

Liquidax Capital, LLC is an investment advisory firm sponsoring and managing private equity innovation funds. The Liquidax debut fund; Liquidax Global Exchange Fund I, LP focuses on the acquisition and monetization of Internet of Things (IoT) technologies and intellectual property rights for target injection into numerous public companies operating on global stock exchanges, as well as, venture capital backed private companies boosting business growth and expediting exits.
Liquidax invests its IoT innovation platform to partner companies for providing competitive advantages in the IoT market. Liquidax's strategically packaged technology that is in complete alignment with IPR enables cost effective and faster time to market innovation.
Four ways to secure banking transaction by biometrics

The Biometric Identification Technology surly has the ability to eliminate loopholes of a banking system that criminals can exploit and has the versatility to secure all financial transactions such as Branch Banking, Internet Banking, Mobile Banking and ATM Networks.
Patent Insights: Connected Car Innovations

Liquidax Capital – Summary Innovation Brief #CC-1606 Patent Insights: Toyota, Ford, Hyundai, GM, Allstate Connected Car Innovations / Internet of Things As outlined by PWC; “Worldwide sales of connected car products will increase almost fourfold between 2015 and 2020, adding more than $149 billion in revenues in the passenger car segment alone. Technologies will offer buyers greater flexibility in personalizing the cars they choose, and enable greater contact between manufacturers and customers strengthening the bonds between them and increasing loyalty to the brand. Consumers are already seeing new capabilities and features in the connected auto markets. The below (5) patents & applications highlight the view and vision of some of the largest auto companies in the world and outline products and services planned for the market.
Survey: Identity Authentication For Banks In Malaysia

These infographics are based on independent survey of 5,000 people in 10 countries carried out for FICO in February 2020. This is for Malaysia.
The statistics include:
1.Why Passwords don't work
2.Biometric acceptance
Outsmarting the Smart City: DISCOVERING AND ATTACKING THE TECHNOLOGY THAT RUN...

The super computer gets a panoptic view of the city using data from cameras and sensor networks. The information obtained is used to manage the city’s infrastructure and technology as well as to maintain a database of personal information about citizens and their activities. In this article, we take a look at some of the real dangers facing today’s cities from malicious hackers.
Speakers:
Daniel Crowley , Research Baron at IBM X-Force Red
Jennifer Savage , Security Researcher at Threatcare
Mauro Paredes , Managing Consultant at IBM X-Force Red
What's hot (20)
Sbvlc secure barcode based visible light communication for smartphones

Sbvlc secure barcode based visible light communication for smartphones
Sbvlc secure barcode based visible light communication for smartphones

Sbvlc secure barcode based visible light communication for smartphones
WhitePaper-BioConnect-The-Future-of-Bring-Your-Own-Identity-in-Identity-Relat...

WhitePaper-BioConnect-The-Future-of-Bring-Your-Own-Identity-in-Identity-Relat...
Keynote Speaker Janice Kephart - Founder and CEO of The Secure Identity and B...

Keynote Speaker Janice Kephart - Founder and CEO of The Secure Identity and B...
Patenting in Mobile Application (App) & Software Based Technology | How to Pa...

Patenting in Mobile Application (App) & Software Based Technology | How to Pa...
Crossing the Rubicon: Digital Signatures and Digital Transformation

Crossing the Rubicon: Digital Signatures and Digital Transformation
Acacia’s patent monetization operating subsidiaries

Acacia’s patent monetization operating subsidiaries
Four ways to secure banking transaction by biometrics

Four ways to secure banking transaction by biometrics
Survey: Identity Authentication For Banks In Malaysia

Survey: Identity Authentication For Banks In Malaysia
Outsmarting the Smart City: DISCOVERING AND ATTACKING THE TECHNOLOGY THAT RUN...

Outsmarting the Smart City: DISCOVERING AND ATTACKING THE TECHNOLOGY THAT RUN...
Similar to Biometric Identification Evolves to Provide Unprecedented Security & Reliability
Bio metrics in secure e transaction

Information security is concerned with the
assurance of confidentially, integrity and availability of
information in all forms. This is the ancient Greek word:
bios = “life” and metron = “measure.” In the present day
world, online shopping using WAP enabled mobile phone
has widely come into use. Credit cards serve as the currency
during e-business and e-Shopping. As the Hacking or
Spoofing or the Misuse of the credit card is continuously
increasing even you are using a secure network. Also, some
Spam software is sent to your system or device through the
internet that helps spammers to get the
desires relevant information about your credit card and
financial data. To solve these problems or get out of these
insecurities the Bio-metric System that provides the secure
E-transaction by improving the prevention of data spoofing.
So in this paper, we have proposed a multi-biometric model
(integrating voice, fingerprint and facial scanning) that can
be embedded in a mobile phone, this making e-transactions
more secure.
NEC Public Safety | Digital Identity for Banks

The importance of being human-centric instead of techno-centric is now fundamentally assessed in the context of secure digital identity for the financial services landscape.
Forward-looking banks and financial institutions are increasingly responding with resources and investments that deliver NEC’s state-of-the-art authentication methods
to meet consumer expectations. As a result, NEC’s vantage point goes far beyond cutting-edge technologies and solutions, such as integration of multimodal biometrics. Brought to you by NEC. To find out more, do visit http://www.nec.com/safety
Biometrics: The Key to Securing Smart Cities

Enhancing Smart Cities' Security with Biometrics! Explore how #Biometrics fortify access control in #SmartCities, paving the way for a secure and efficient future.
https://bahaaabdulhadi.com/biometrics-securing-smart-cities/
#TechSecurity #IoT #DataProtection
Biometrics: A New Wrinkle Changes the Authentication Landscape 

Criminal theft of passwords has made passwords obsolete, and so a new factor is required for authentication. Biometrics will be that new factor. It increases security and will prove more convenient for the consumer than passwords as it transitions into a persistent identity over the next 5 to 8 years. Increasingly smartphones are shipping with trusted execution environments that can displace traditional hardware security fobs. These new smartphones are critical to this fundamental shift in biometrics.
A new research report from Mercator Advisory Group titled Biometrics: A New Wrinkle Changes the Authentication Landscape explains the need for multimodal biometric authentication and describes many types of biometrics available from various technology providers. The report shows how biometrics technology has shifted from a primarily hardware-based solution to a software-and cloud-based solution enabled by smartphones that have become much more secure. With voice and face recognition, and now the addition of behavioral biometrics, this shift will drive rapid new innovation and will tip the market in favor of the mobile architecture.
Ins & Outs of Biometric Authentication

A brief overview of biometric authentication and the benefits it can have on your business and its overall security. Is biometric authentication something you should be looking into? Find out now...
Multimodal Biometric endorsement for secure Internet banking using Skin Spect...

https://irjet.net/archives/V3/i2/IRJET-V3I2190.pdf
The Future of Biometrics, Transforming Age and Identity Verification

Explore the future of biometric technology and its transformative impact across diverse industries. Learn how biometrics can enhance security, efficiency, and user experience. Discover critical factors when selecting the right biometric solutions for specific industry needs.
How AI is impacting digital identity security.pdf

AI is revolutionizing digital identity security by enhancing authentication methods, detecting anomalies, and preventing fraud with its ability to analyze vast data sets and recognize patterns accurately.
Website : https://vlinkinc-my.sharepoint.com/:w:/g/personal/vipul_bhardwaj_vlinkinfo_com/EaQPA2UFPuxKomhOXisVC40Bmj4Jvbu6Zx5XRvmCfNJMSQ?e=cjJXCt
NEC Public Safety | Biometric for Safer Cities

Biometric technologies use biological features such as fingerprints, veins, faces and irises to identify individuals. They greatly improve the accuracy and reliability of identification and verification systems by taking out the element of human error. In the area of public safety, biometric technologies in the form of fingerprinting, iris and facial recognition have made a significant contribution to border control and law enforcement. Brought to you by NEC. To find out more, do visit http://www.nec.com/safety
Iris Recognition Market PDF.pdf

As iris recognition systems continue to evolve and improve, their adoption across diverse industries is set to rise. By enhancing security measures, streamlining authentication processes, and safeguarding sensitive information, iris recognition technology promises a safer and more efficient future.
Multi-factor Implicit Biometric Authentication: Analysis and Approach

Research Paper Outline - Cyber Security Management ITMS 578, IIT, Chicago - Fall 2016 ITM, Department of Applied Technology.
The How of Biometrics

Biometrics have found use in various fields including, consumer electronics, corporate and public security systems, and point of sale.
Other than access control and identification, security forces and research teams use biometrics to denote individuals who are under their surveillance.
Other than their oblivious merit in application to security, they also carry the advantage of being convenient. Unlike passwords they do not have to be remembered.
NEC Public Safety | Govware 2018 AI for Next Gen Cyber Defence by Walter Lee

Powering the Internet of Identities with integrated cyber-physical security.
The Internet of Things is driving the integration of the cyber and physical state today. in order to ensure that commercial transactions and government services can be further enhanced, digital identity is critical, and will be the cornerstone that defines the very fabric of public safety in future societies.
NEC is unique in providing multi-layered security solutions, allowing us to assemble different solutions in response to the complexity of the different layers and provide a turn-key solution to our clients.
Walter Lee, Evangelist & Government Relations leader of NEC Global Safety Division shares about AI for Next Generation Cyber Defense.
Brought to you by NEC. To find out more, do visit http://www.nec.com/safety
NXT-ID, Inc.'s (OTCQB:NXTD) Presentation

About NXT- ID Inc. - Mobile Security for a Mobile World
NXT-ID, Inc.'s (OTCQB:NXTD) innovative MobileBio™ solution mitigates consumer risks associated with mobile computing, m-commerce and smart OS-enabled devices. The company is focused on the growing m-commerce market, launching its innovative MobileBio™ suite of biometric solutions that secure consumers' mobile platforms led by the Wocket™; a next generation smart wallet designed to replace all the cards in your wallet, no smart phone required. The Wocket works anywhere credit cards are accepted and only works with your biometric stamp of approval. http://www.thewocket.com/, http://www.wocketwallet.com/
NXT-ID's wholly owned subsidiary, 3D-ID LLC, is engaged in biometric identification has 22 licensed patents in the field of 3D facial recognition http://www.nxt-id.com/, http://3d-id.net/
Similar to Biometric Identification Evolves to Provide Unprecedented Security & Reliability (20)
Biometrics: A New Wrinkle Changes the Authentication Landscape 

Biometrics: A New Wrinkle Changes the Authentication Landscape
Multimodal Biometric endorsement for secure Internet banking using Skin Spect...

Multimodal Biometric endorsement for secure Internet banking using Skin Spect...
The Future of Biometrics, Transforming Age and Identity Verification

The Future of Biometrics, Transforming Age and Identity Verification
Multi-factor Implicit Biometric Authentication: Analysis and Approach

Multi-factor Implicit Biometric Authentication: Analysis and Approach
NEC Public Safety | Govware 2018 AI for Next Gen Cyber Defence by Walter Lee

NEC Public Safety | Govware 2018 AI for Next Gen Cyber Defence by Walter Lee
Recently uploaded
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP of Product, Amplitude
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

In this insightful webinar, Inflectra explores how artificial intelligence (AI) is transforming software development and testing. Discover how AI-powered tools are revolutionizing every stage of the software development lifecycle (SDLC), from design and prototyping to testing, deployment, and monitoring.
Learn about:
• The Future of Testing: How AI is shifting testing towards verification, analysis, and higher-level skills, while reducing repetitive tasks.
• Test Automation: How AI-powered test case generation, optimization, and self-healing tests are making testing more efficient and effective.
• Visual Testing: Explore the emerging capabilities of AI in visual testing and how it's set to revolutionize UI verification.
• Inflectra's AI Solutions: See demonstrations of Inflectra's cutting-edge AI tools like the ChatGPT plugin and Azure Open AI platform, designed to streamline your testing process.
Whether you're a developer, tester, or QA professional, this webinar will give you valuable insights into how AI is shaping the future of software delivery.
Mission to Decommission: Importance of Decommissioning Products to Increase E...

Mission to Decommission: Importance of Decommissioning Products to Increase Enterprise-Wide Efficiency by VP Data Platform, American Express
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
Recently uploaded (20)
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality
Mission to Decommission: Importance of Decommissioning Products to Increase E...

Mission to Decommission: Importance of Decommissioning Products to Increase E...
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
Biometric Identification Evolves to Provide Unprecedented Security & Reliability
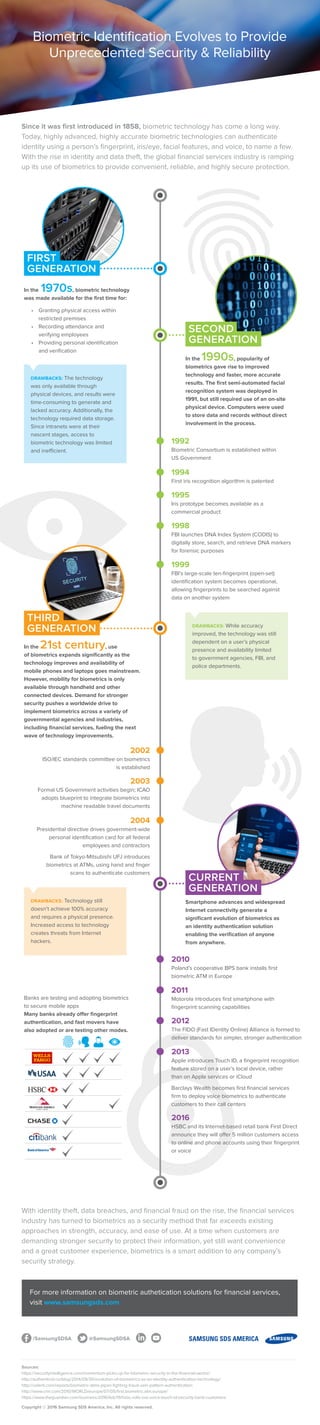
- 1. In the 1970s, biometric technology was made available for the first time for: • Granting physical access within restricted premises • Recording attendance and verifying employees • Providing personal identification and verification Since it was first introduced in 1858, biometric technology has come a long way. Today, highly advanced, highly accurate biometric technologies can authenticate identity using a person’s fingerprint, iris/eye, facial features, and voice, to name a few. With the rise in identity and data theft, the global financial services industry is ramping up its use of biometrics to provide convenient, reliable, and highly secure protection. With identity theft, data breaches, and financial fraud on the rise, the financial services industry has turned to biometrics as a security method that far exceeds existing approaches in strength, accuracy, and ease of use. At a time when customers are demanding stronger security to protect their information, yet still want convenience and a great customer experience, biometrics is a smart addition to any company’s security strategy. For more information on biometric authetication solutions for financial services, visit www.samsungsds.com @SamsungSDSA/SamsungSDSA Sources: https://securityintelligence.com/momentum-picks-up-for-biometric-security-in-the-financial-sector/ http://authenticid.co/blog/2014/09/30/evolution-of-biometrics-as-an-identity-authentication-technology/ http://celent.com/reports/biometric-atms-japan-fighting-fraud-vein-pattern-authentication http://www.cnn.com/2010/WORLD/europe/07/05/first.biometric.atm.europe/ https://www.theguardian.com/business/2016/feb/19/hsbc-rolls-out-voice-touch-id-security-bank-customers Copyright © 2016 Samsung SDS America, Inc. All rights reserved. Biometric Identification Evolves to Provide Unprecedented Security & Reliability FIRST GENERATION DRAWBACKS: The technology was only available through physical devices, and results were time-consuming to generate and lacked accuracy. Additionally, the technology required data storage. Since intranets were at their nascent stages, access to biometric technology was limited and inefficient. In the 1990s, popularity of biometrics gave rise to improved technology and faster, more accurate results. The first semi-automated facial recognition system was deployed in 1991, but still required use of an on-site physical device. Computers were used to store data and records without direct involvement in the process. SECOND GENERATION DRAWBACKS: While accuracy improved, the technology was still dependent on a user’s physical presence and availability limited to government agencies, FBI, and police departments. 1992 Biometric Consortium is established within US Government 1994 First iris recognition algorithm is patented 2002 ISO/IEC standards committee on biometrics is established 2003 Formal US Government activities begin; ICAO adopts blueprint to integrate biometrics into machine readable travel documents 2004 Presidential directive drives government-wide personal identification card for all federal employees and contractors Bank of Tokyo-Mitsubishi UFJ introduces biometrics at ATMs, using hand and finger scans to authenticate customers 1995 Iris prototype becomes available as a commercial product 1998 FBI launches DNA Index System (CODIS) to digitally store, search, and retrieve DNA markers for forensic purposes 1999 FBI’s large-scale ten-fingerprint (open-set) identification system becomes operational, allowing fingerprints to be searched against data on another system In the 21st century, use of biometrics expands significantly as the technology improves and availability of mobile phones and laptops goes mainstream. However, mobility for biometrics is only available through handheld and other connected devices. Demand for stronger security pushes a worldwide drive to implement biometrics across a variety of governmental agencies and industries, including financial services, fueling the next wave of technology improvements. THIRD GENERATION DRAWBACKS: Technology still doesn’t achieve 100% accuracy and requires a physical presence. Increased access to technology creates threats from Internet hackers. Smartphone advances and widespread Internet connectivity generate a significant evolution of biometrics as an identity authentication solution enabling the verification of anyone from anywhere. CURRENT GENERATION 2010 Poland’s cooperative BPS bank installs first biometric ATM in Europe 2011 Motorola introduces first smartphone with fingerprint scanning capabilities 2012 The FIDO (Fast IDentity Online) Alliance is formed to deliver standards for simpler, stronger authentication 2013 Apple introduces Touch ID, a fingerprint recognition feature stored on a user’s local device, rather than on Apple services or iCloud Barclays Wealth becomes first financial services firm to deploy voice biometrics to authenticate customers to their call centers 2016 HSBC and its Internet-based retail bank First Direct announce they will offer 5 million customers access to online and phone accounts using their fingerprint or voice Banks are testing and adopting biometrics to secure mobile apps Many banks already offer fingerprint authentication, and fast movers have also adopted or are testing other modes.
