The document provides descriptions and examples for 15 common Linux networking tools: ip, nc, ssh, scp, arp, rarp, route, netstat, ifup, ifdown, iwconfig, iwspy, iwlist, tracepath, and dhclient. It defines what each tool is used for, provides examples of basic commands, and in some cases describes key options and usage details. The tools can be used to configure and manage network interfaces, view and modify routing tables, connect to remote systems, transfer files securely, and work with wireless networking functionality.
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
1)ip:
Name: show / manipulate routing, devices, policy routing and tunnels .
Synopsis:
ip [ OPTIONS ] OBJECT { COMMAND | help }
OBJECT := { link | addr | addrlabel | route | rule | neigh | tunnel | maddr | mroute | monitor }
OPTIONS := { -V[ersion] | -s[tatistics] | -r[esolve] | -f[amily] { inet | inet6 | ipx | dnet | link } | -o[neline] }
Examples:
ip link show : List network interfaces
ip link set dev eth0 name eth1 : Rename interface eth0 to eth1](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/75/Basic-linux-commands-1-2048.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
ip link set dev eth0 up :Bring interface eth0 up (or down)
ip addr show : List addresses for interfaces
ip route show :List routing table
ip route add default via 10.3.10.1: Set default gateway to 10.3.10.1
2)nc:
NAME: nc — arbitrary TCP and UDP connections and listens.
SYNOPSIS: nc [-46DdhklnrStUuvzC] [-i interval] [-P proxy_username] [-p source_port]
[-s source_ip_address] [-T ToS] [-w timeout] [-X proxy_protocol] [-x
proxy_address[:port]] [hostname] [port[s]]
DESCRIPTION:
The nc (or netcat) utility is used for just about anything under the sun
involving TCP or UDP. It can open TCP connections, send UDP packets,
listen on arbitrary TCP and UDP ports, do port scanning, and deal with
both IPv4 and IPv6. Unlike telnet(1), nc scripts nicely, and separates
error messages onto standard error instead of sending them to standard
output, as telnet(1) does with some.](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-2-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
Examples:
nc host port: where host is the IP address or DNS name of a host to connect to and port is the TCP
port number to connect to. By default, netcat uses TCP. Unlike telnet, netcat doesn't print
anything to the screen when a connection is made unless you use the -v command line option.
To scan ports command used is : nc -z 10.3.10.36 10-100 and to show close ports too include –v:
nc -vz 10.3.10.36 10-100
3)ssh:
NAME: ssh — OpenSSH SSH client (remote login program).
SYNOPSIS:
ssh [-1246AaCfgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec] [-D
[bind_address:]port] [-e escape_char] [-F configfile] [-I pkcs11]
[-i identity_file] [-L [bind_address:]port:host:hostport]
[-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port]
[-R [bind_address:]port:host:hostport] [-S ctl_path] [-W host:port]
[-w local_tun[:remote_tun]] [user@]hostname [command]](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-3-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
DESCRIPTION:
ssh (SSH client) is a program for logging into a remote machine and for
executing commands on a remote machine. It is intended to replace rlogin
and rsh, and provide secure encrypted communications between two
untrusted hosts over an insecure network. X11 connections and arbitrary
TCP ports can also be forwarded over the secure channel.
Examples:
ssh user@hostname
4)scp:
NAME: scp — secure copy (remote file copy program).
SYNOPSIS:
scp [-1246BCpqrv] [-c cipher] [-F ssh_config] [-i identity_file]
[-l limit] [-o ssh_option] [-P port] [-S program]
[[user@]host1:]file1 ... [[user@]host2:]file](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-4-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
5)arp:
NAME: arp - manipulate the system ARP cache.
SYNOPSIS:
arp [-vn] [-H type] [-i if] [-a] [hostname]
arp [-v] [-i if] -d hostname [pub]
arp [-v] [-H type] [-i if] -s hostname hw_addr [temp]
arp [-v] [-H type] [-i if] -s hostname hw_addr [netmask nm] pub
arp [-v] [-H type] [-i if] -Ds hostname ifname [netmask nm] pub
arp [-vnD] [-H type] [-i if] -f [filename]
DESCRIPTION:
Arp manipulates or displays the kernel's IPv4 network neighbour cache.
It can add entries to the table, delete one or display the current con‐
tent.
ARP stands for Address Resolution Protocol, which is used to find the
media access control address of a network neighbour for a given IPv4
Address.
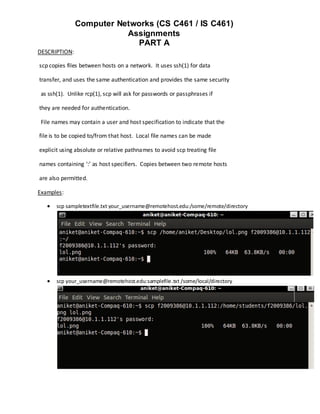
Examples:
arp -a
arp –a ip](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-6-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
Delete an ARP entry: arp -d
6)rarp:
NAME: rarp - manipulate the system RARP table
SYNOPSIS:
rarp [-V] [--version] [-h] [--help]
rarp -a
rarp [-v] -d hostname ...
rarp [-v] [-t type] -s hostname hw_addr
DESCRIPTION:
Arp manipulates or displays the kernel's IPv4 network neighbour cache.
It can add entries to the table, delete one or display the current con‐
tent.
ARP stands for Address Resolution Protocol, which is used to find the
media access control address of a network neighbour for a given IPv4
Address.
Examples:
rarp –a
aniket@ubuntu:~$ rarp -a
This kernel does not support RARP.](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-7-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
7)route:
NAME: route - show / manipulate the IP routing table.
SYNOPSIS:
route [-CFvnee]
route [-v] [-A family] add [-net|-host] target [netmask Nm] [gw Gw]
[metric N] [mss M] [window W] [irtt I] [reject] [mod] [dyn]
[reinstate] [[dev] If]
route [-v] [-A family] del [-net|-host] target [gw Gw] [netmask Nm]
[metric N] [[dev] If]
route [-V] [--version] [-h] [--help]
DESCRIPTION:
Route manipulates the kernel's IP routing tables. Its primary use is
to set up static routes to specific hosts or networks via an interface
after it has been configured with the ifconfig(8) program.
When the add or del options are used, route modifies the routing
tables. Without these options, route displays the current contents of
the routing tables.
Examples:
route](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-8-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
route add default gw 10.3.10.1 eth0
8)netstat:
NAME: netstat - Print network connections, routing tables, interface statistics, masquerade
connections, and multicast memberships.
SYNOPSIS:
netstat [address_family_options] [--tcp|-t] [--udp|-u] [--raw|-w] [--listening|-l] [--all|-a]
[--numeric|-n] [--numeric-hosts] [--numeric-ports]
[--numeric-users] [--symbolic|-N] [--extend|-e[--extend|-e]] [--timers|-o] [--program|-p] [--
verbose|-v] [--continuous|-c]
netstat {--route|-r} [address_family_options] [--extend|-e[--extend|-e]] [--verbose|-v] [--
numeric|-n] [--numeric-hosts] [--numeric-ports] [--numeric-users]
[--continuous|-c]
netstat {--interfaces|-i} [--all|-a] [--extend|-e[--extend|-e]] [--verbose|-v] [--program|-p] [--
numeric|-n] [--numeric-hosts] [--numeric-ports] [--numeric-
users] [--continuous|-c]
netstat {--groups|-g} [--numeric|-n] [--numeric-hosts] [--numeric-ports] [--numeric-users] [--
continuous|-c]
netstat {--masquerade|-M} [--extend|-e] [--numeric|-n] [--numeric-hosts] [--numeric-ports] [--
numeric-users] [--continuous|-c]
netstat {--statistics|-s} [--tcp|-t] [--udp|-u] [--raw|-w]
netstat {--version|-V}
netstat {--help|-h}](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-9-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
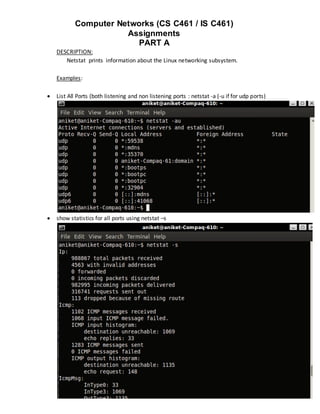
Display the kernel routing information using netstat –r
Show the list of network interfaces: netstat -i
9)ifup:
NAME: ifup - bring a network interface up.
SYNOPSIS:
ifup [-nv] [--no-act] [--verbose] [-i FILE|--interfaces=FILE] [--allow
CLASS] -a|IFACE...
ifup -h|--help
ifup -V|--version
DESCRIPTION:
The ifup and ifdown commands may be used to configure (or, respec‐
tively, deconfigure) network interfaces based on interface definitions
in the file /etc/network/interfaces.](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-11-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
10)ifdown:
NAME: take a network interface down
SYNOPSIS:
ifdown [-nv] [--no-act] [--verbose] [-i FILE|--interfaces=FILE]
[--allow CLASS] -a|IFACE...
DESCRIPTION:
The ifup and ifdown commands may be used to configure (or, respec‐
tively, deconfigure) network interfaces based on interface definitions
in the file /etc/network/interfaces.
Examples(ifup and ifdown examples are provided together):
sudo ifup lo/ sudo ifdown lo
11)iwconfig:
NAME: iwconfig - configure a wireless network
SYNOPSIS:
iwconfig [interface]
iwconfig interface [essid X] [nwid N] [mode M] [freq F]
[channel C][sens S ][ap A ][nick NN ]
[rate R] [rts RT] [frag FT] [txpower T]
[enc E] [key K] [power P] [retry R]
[modu M] [commit]
iwconfig --help
iwconfig –version](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-12-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
12)iwspy:
NAME: iwspy - Get wireless statistics from specific nodes.
SYNOPSIS:
iwspy [interface]
iwspy interface [+] DNSNAME | IPADDR | HWADDR [...]
iwspy interface off
iwspy interface setthr low high
iwspy interface getthr
DESCRIPTION:
Iwspy is used to set a list of addresses to monitor in a wireless net‐
work interface and to read back quality of link information for each of
those. This information is the same as the one available in
/proc/net/wireless : quality of the link, signal strength and noise
level.
This information is updated each time a new packet is received, so each
address of the list adds some overhead in the driver.
Note that this functionality works only for nodes part of the current
wireless cell, you can not monitor Access Points you are not associated
with (you can use Scanning for that) and nodes in other cells. In Man‐
aged mode, in most case packets are relayed by the Access Point, in
this case you will get the signal strength of the Access Point. For
those reasons this functionality is mostly useful in Ad-Hoc and Master
mode.
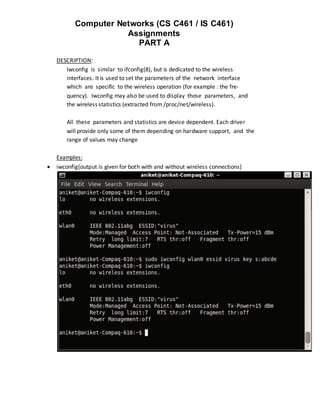
Examples:
sudo iwspy eth0
Output:
aniket@ubuntu:~$ sudo iwspy eth0
eth0 Interface doesn't support wireless statistic collection](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-14-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
13)iwlist:
NAME: iwlist - Get more detailed wireless information from a wireless inter‐
Face.
SYNOPSIS:
iwlist [interface] scanning
iwlist [interface] frequency
iwlist [interface] rate
iwlist [interface] keys
iwlist [interface] power
iwlist [interface] txpower
iwlist [interface] retry
iwlist [interface] event
iwlist [interface] auth
iwlist [interface] wpakeys
iwlist [interface] genie
iwlist [interface] modulation
iwlist --help
iwlist –version
DESCRIPTION:
Iwlist is used to display some additional information from a wireless
network interface that is not displayed by iwconfig(8). The main argu‐
ment is used to select a category of information, iwlist displays in
detailed form all information related to this category, including
information already shown by iwconfig(8).](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-15-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
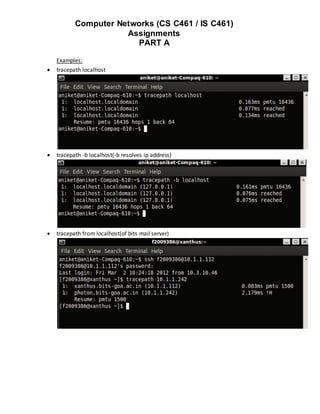
Examples:
iwlist wlan0 scan
14)tracepath:
NAME: tracepath, tracepath6 - traces path to a network host discovering MTU
along this path.
SYNOPSIS:
tracepath [-n] [-b] [-l pktlen] destination [port]
DESCRIPTION:
It traces path to destination discovering MTU along this path. It uses
UDP port port or some random port. It is similar to traceroute, only
does not require superuser privileges and has no fancy options.
tracepath6 is good replacement for traceroute6 and classic example of
application of Linux error queues. The situation with IPv4 is worse,
because commercial IP routers do not return enough information in icmp
error messages. Probably, it will change, when they will be updated.
For now it uses Van Jacobson's trick, sweeping a range of UDP ports to
maintain trace history.](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-16-320.jpg)
![Computer Networks (CS C461 / IS C461)
Assignments
PART A
15)dhclient:
NAME: dhclient - Dynamic Host Configuration Protocol Client.
SYNOPSIS:
dhclient [ -p port ] [ -d ] [ -e VAR=value ] [ -q ] [ -1 ] [ -r ] [ -x
] [ -lf lease-file ] [ -pf pid-file ] [ -cf config-file ] [ -sf
script-file ] [ -s server ] [ -g relay ] [ -n ] [ -nw ] [ -w ] [ if0 [
...ifN ] ]
DESCRIPTION:
The Internet Systems Consortium DHCP Client, dhclient, provides a means
for configuring one or more network interfaces using the Dynamic Host
Configuration Protocol, BOOTP protocol, or if these protocols fail, by
statically assigning an address.
Examples:
sudo dhclient eth0](https://image.slidesharecdn.com/basiclinuxcommands-120424015614-phpapp01/85/Basic-linux-commands-18-320.jpg)