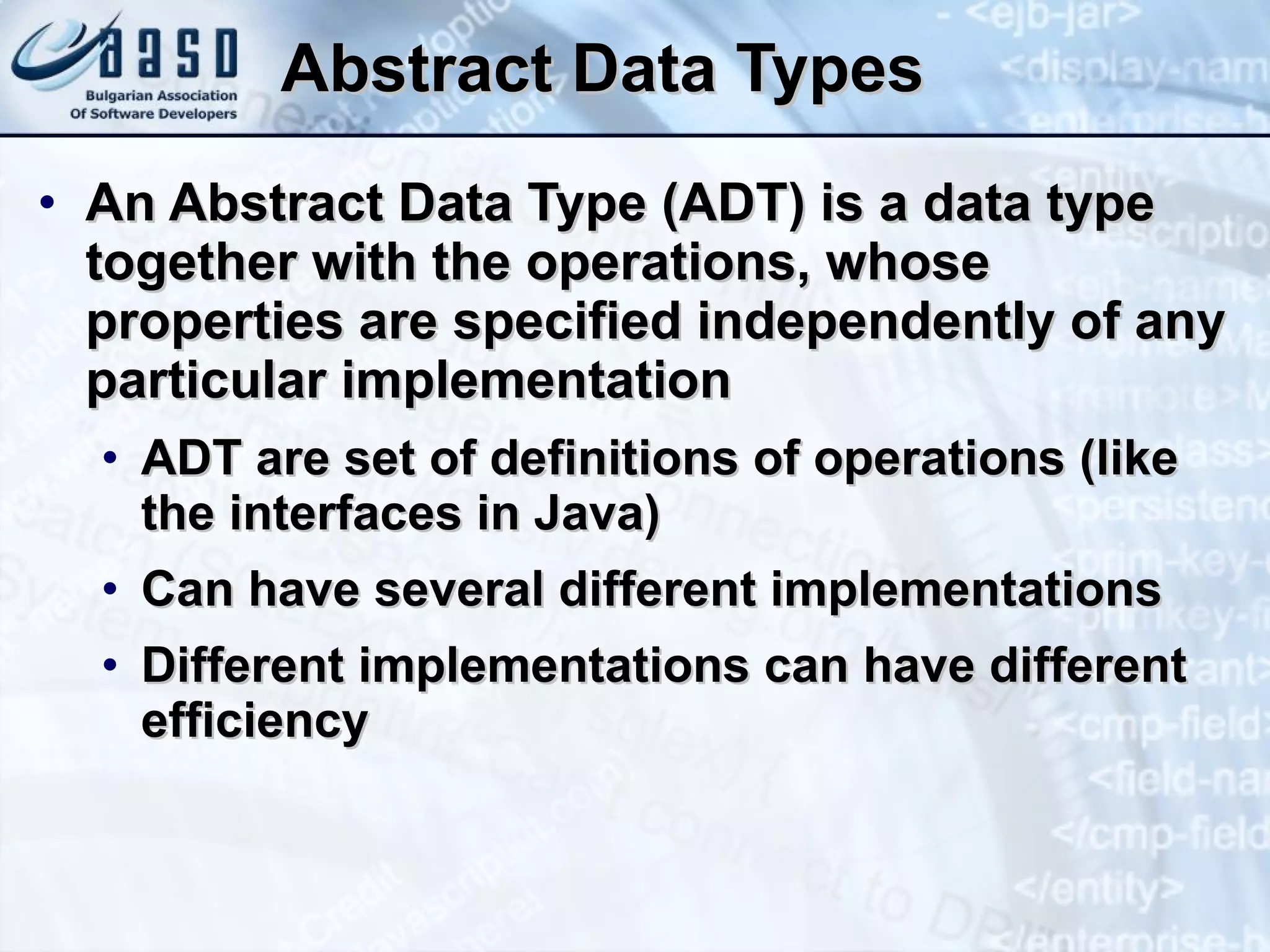
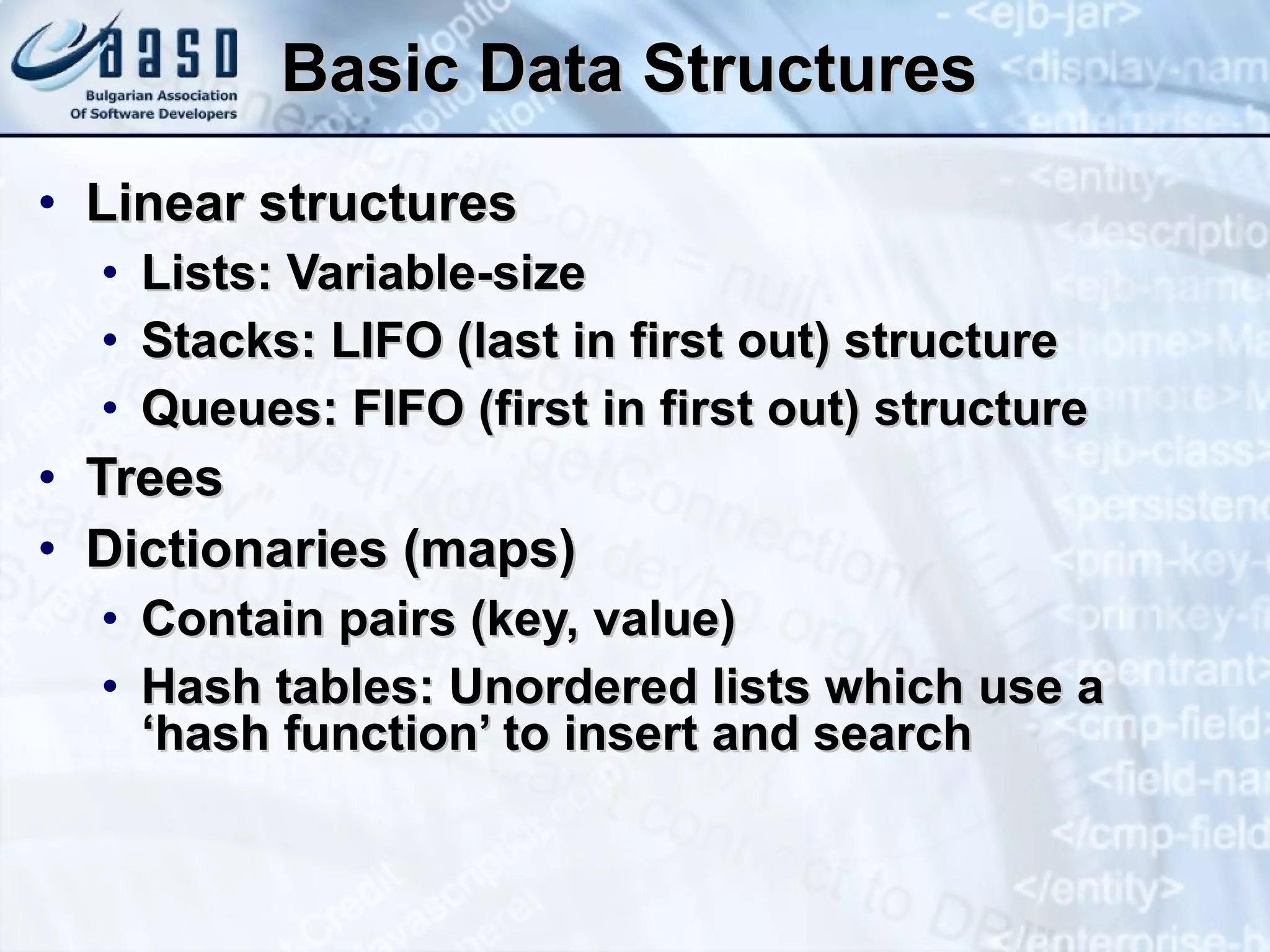
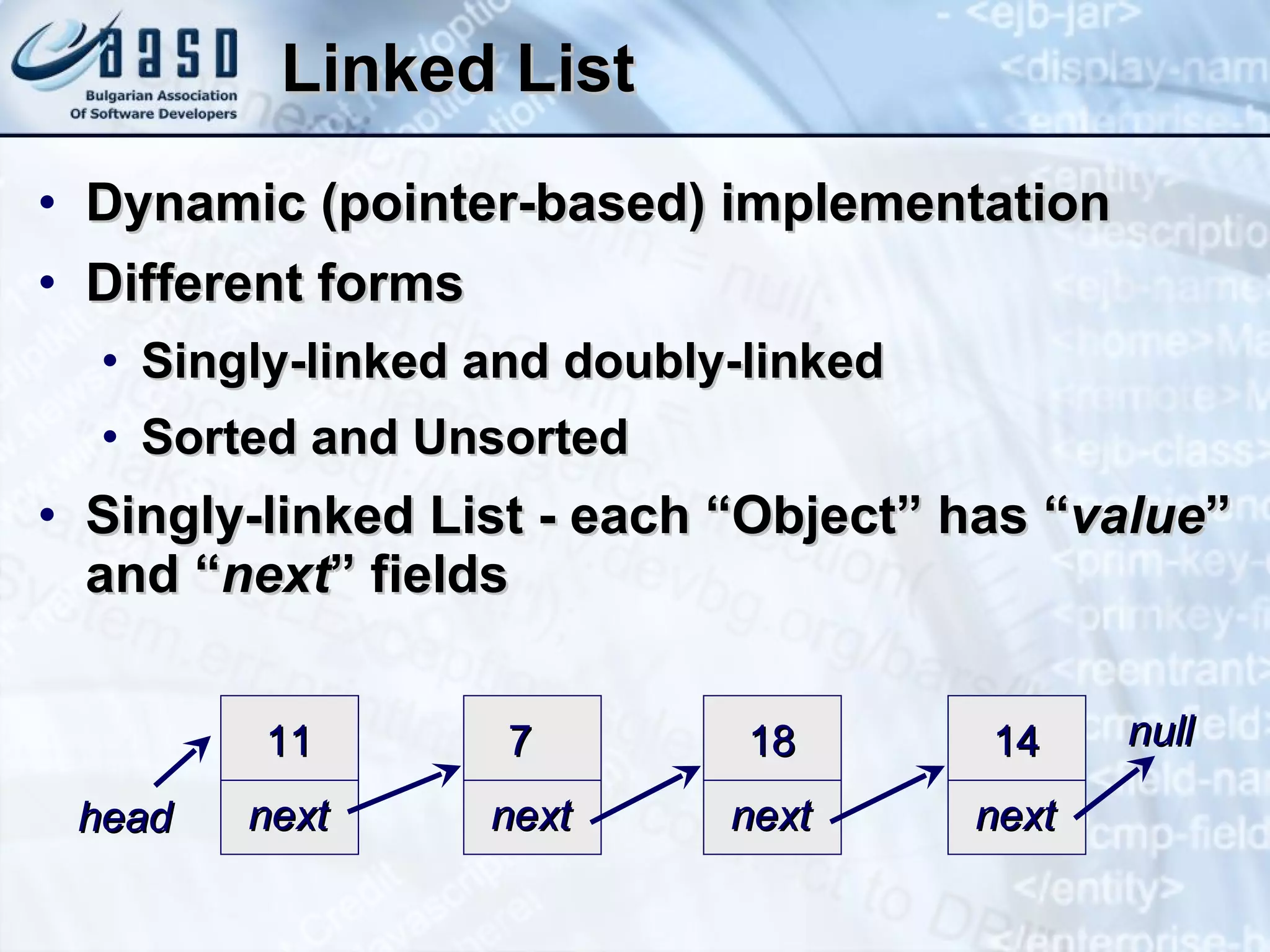
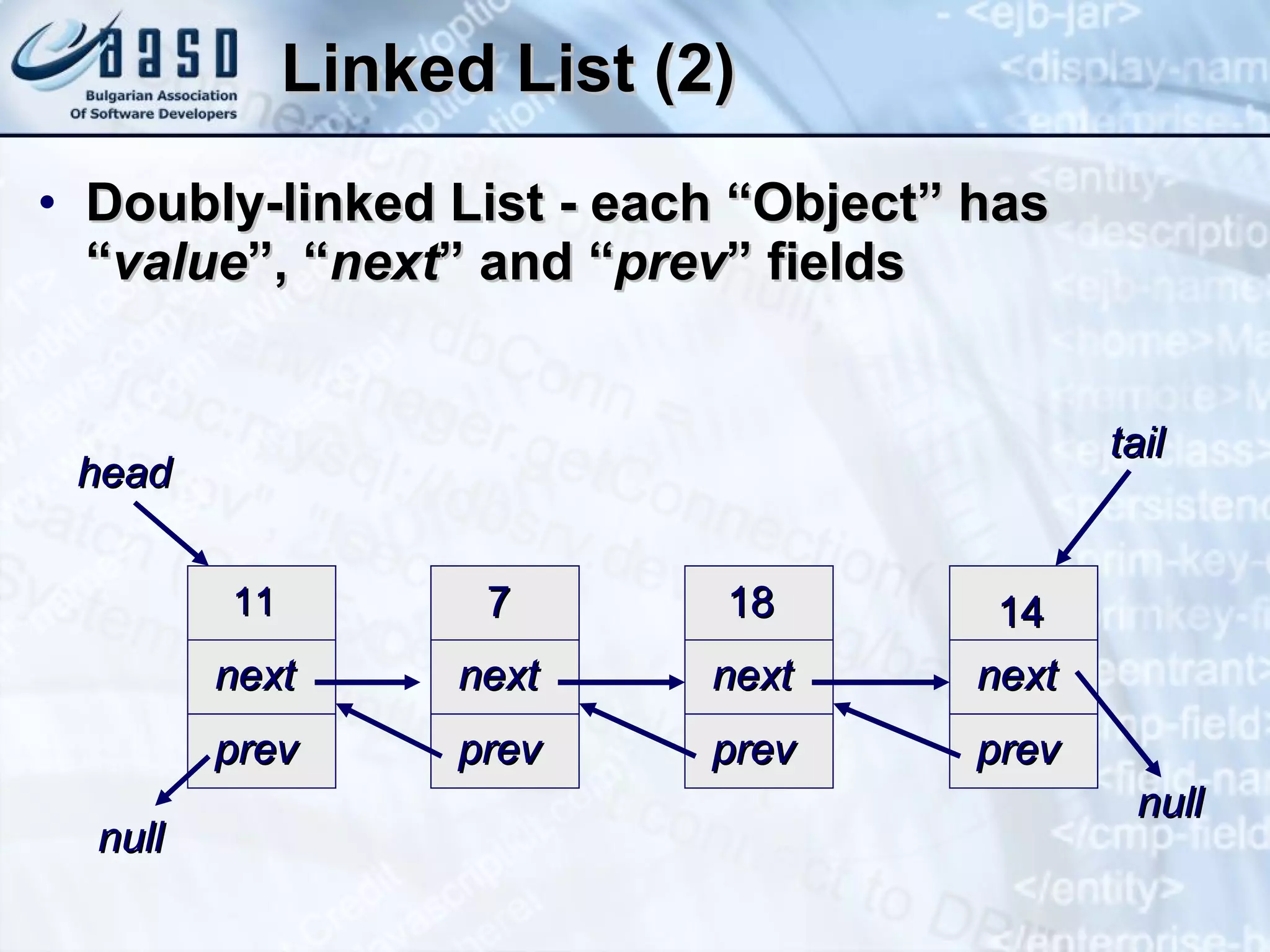
The document provides an overview of common data structures including lists, stacks, queues, trees, and hash tables. It describes each data structure, how it can be implemented both statically and dynamically, and how to use the core Java classes like ArrayList, Stack, LinkedList, and HashMap that implement these structures. Key points covered include common operations for each structure, examples of using the Java classes, and applications like finding prime numbers in a range or matching brackets in an expression.









![The ArrayList Class(2) ArrayList can contain any data type Elements are added directly Typecasting is required when extracting elements unless we use Generics Converting to array List list = new ArrayList(); list. a dd(5); // Add integer value list. a dd("some string"); // Add string value int firstElement = ((Integer)(list.get(0))).intValue(); String secondElement = (String)list.get(1); Integer[] arr = list.toArray(new Integer[list.size()]);](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-14-2048.jpg)
![Primes[n..m] – Example Find all prime numbers in a specified interval public static ArrayList<Integer> getPrimes(int start, int end) { List<Integer> primesList = new ArrayList<Integer>(); for (int num = start; num <= end; num++) { boolean prime = true; for (int div = 2; div <= Math.sqrt(num); div++) { if (num % div == 0) { prime = false; break; } } if (prime) { primesList.add(num); } } return primesList; }](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-16-2048.jpg)
![Primes[n..m] Live Demo](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-17-2048.jpg)
![Union and Intersection of Lists – Example public static Integer[] union(Integer[] firstArr, Integer[] secondArr) { List<Integer> union = new ArrayList<Integer>(); for (Integer item : firstArr) { union.add(item); } for (Integer item : secondArr) { if (!union.contains(item)) { union.add(item); } } return union.toArray(new Integer[union.size()]); } //Example continues...](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-18-2048.jpg)
![Union and Intersection of Lists – Example(2) public static Integer[] intersect(Integer[] firstArr, Integer[] secondArr) { List<Integer> intersect = new ArrayList<Integer>(); for (Integer item : firstArr) { if (Arrays.binarySearch(secondArr, item) >= 0) { intersect.add(item); } } return intersect.toArray( new Integer[intersect.size()]); }](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-19-2048.jpg)





![Stack – Example Using push() , pop() and peek() methods public static void main(String[] args) { Stack<String> stack = new Stack<String>(); stack.push("1. Ivan"); stack.push("2. Nikolay"); stack.push("3. Maria"); stack.push("4. George"); System.out.println("Top = " + stack.peek()); while (stack.size() > 0) { String personName = stack.pop(); System.out.println(personName); } }](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-29-2048.jpg)

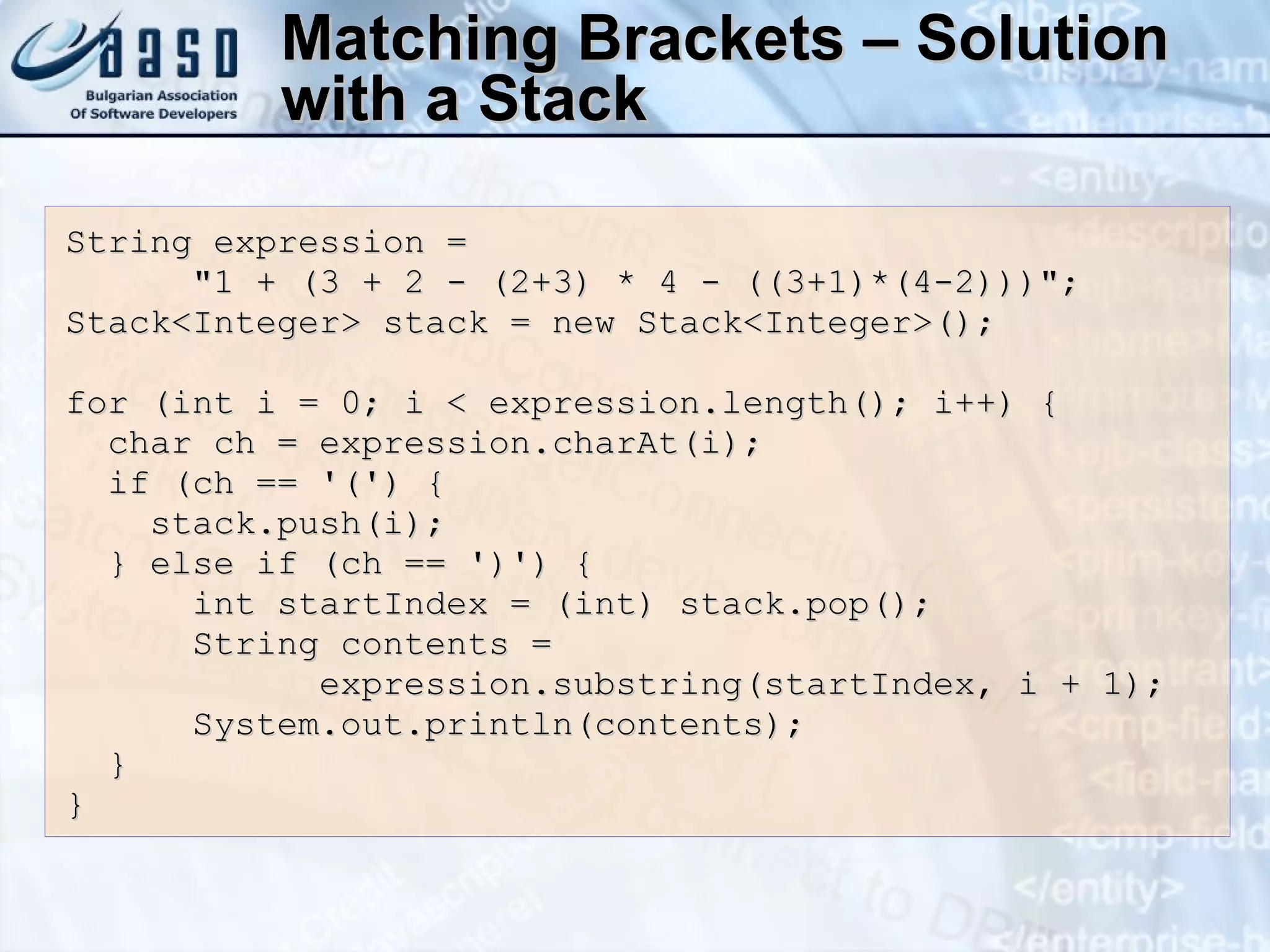



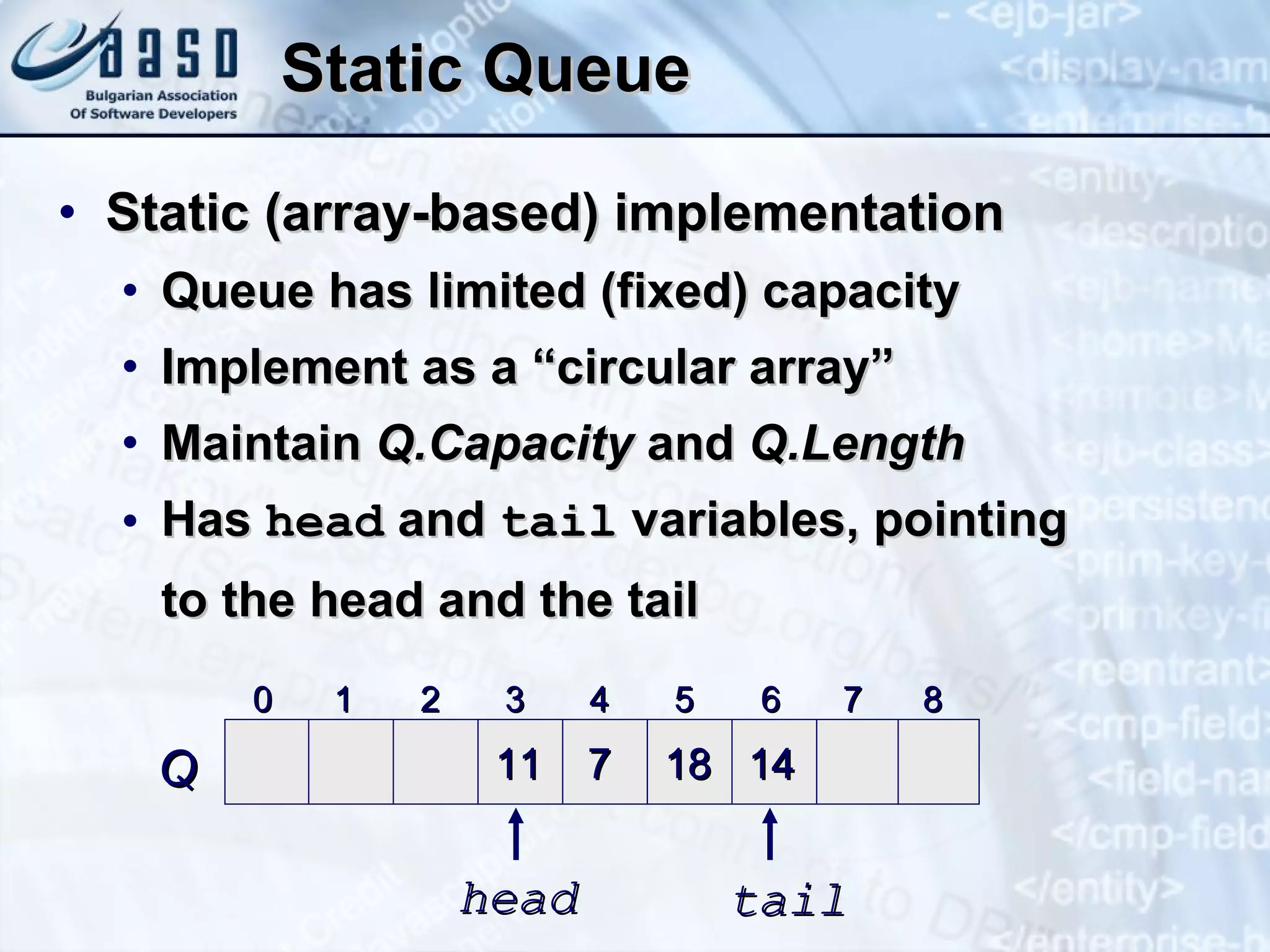
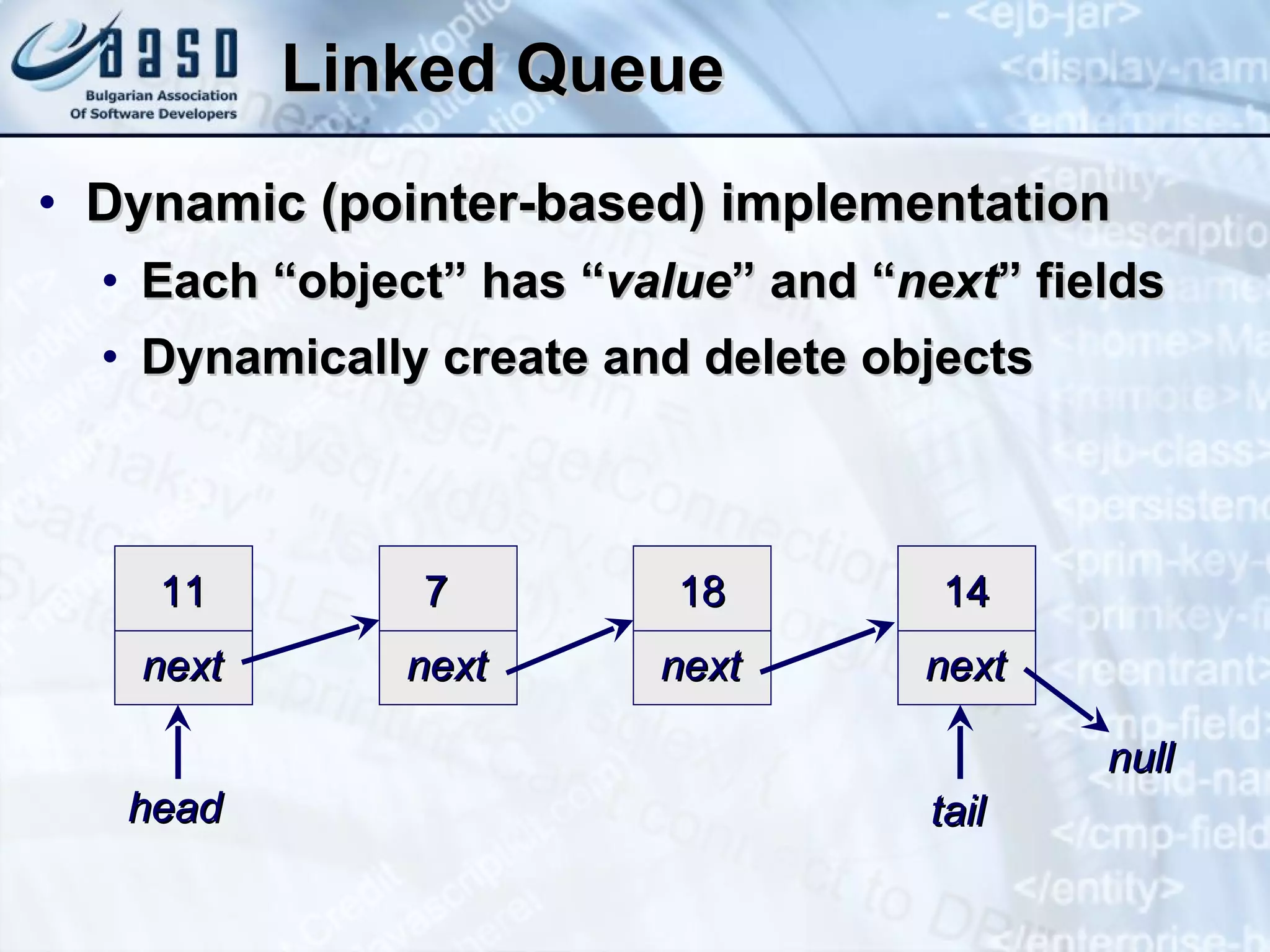




![Queue – Example Using offer () and poll () methods public static void main(String[] args) { Queue<String> queue = new LinkedList<String>(); queue.offer("Message One"); queue.offer("Message Two"); queue.offer("Message Three"); queue.offer("Message Four"); queue.offer("Message Five"); while (queue.size() > 0) { String msg = queue.poll(); System.out.println(msg); } }](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-42-2048.jpg)


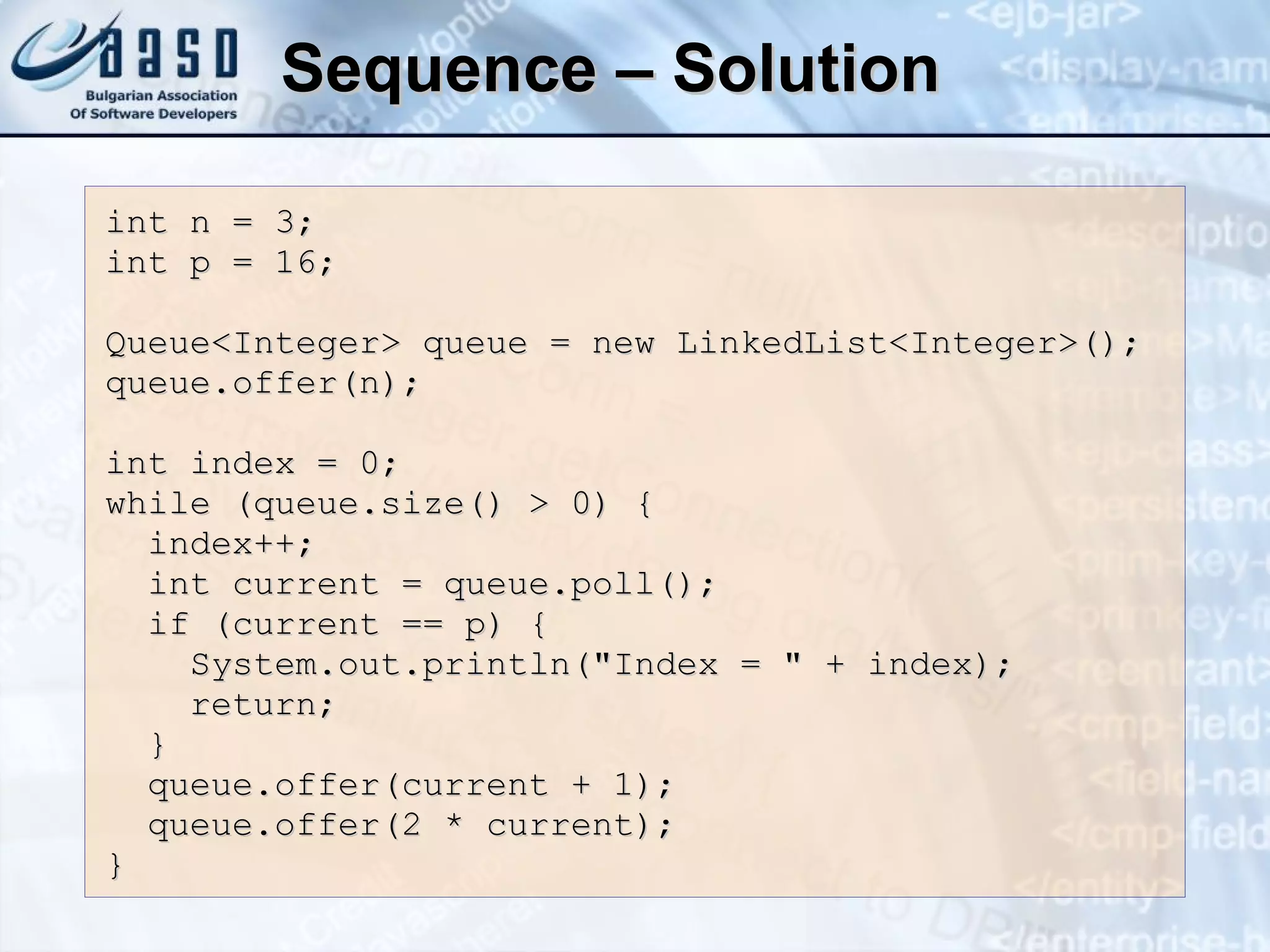







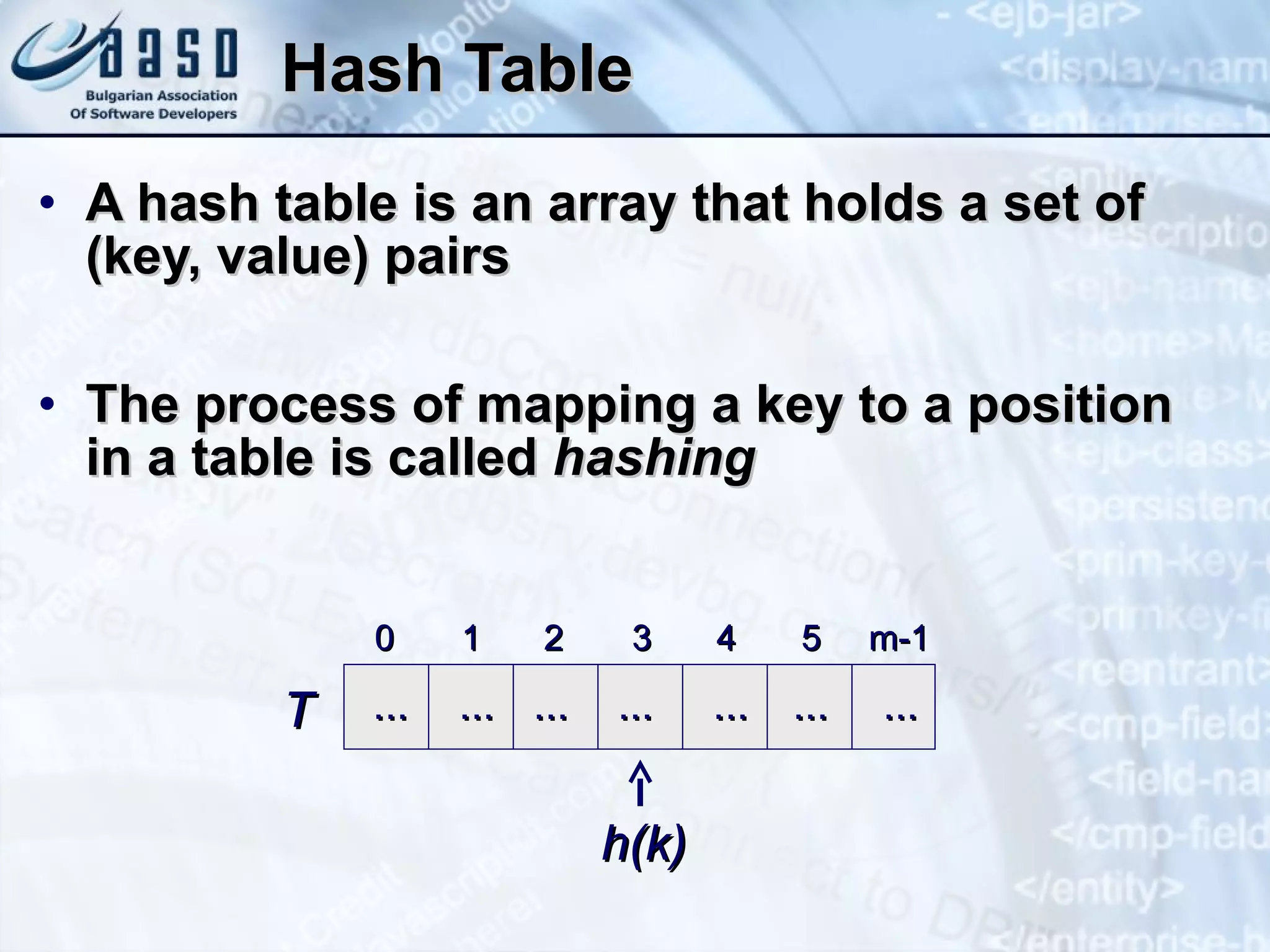
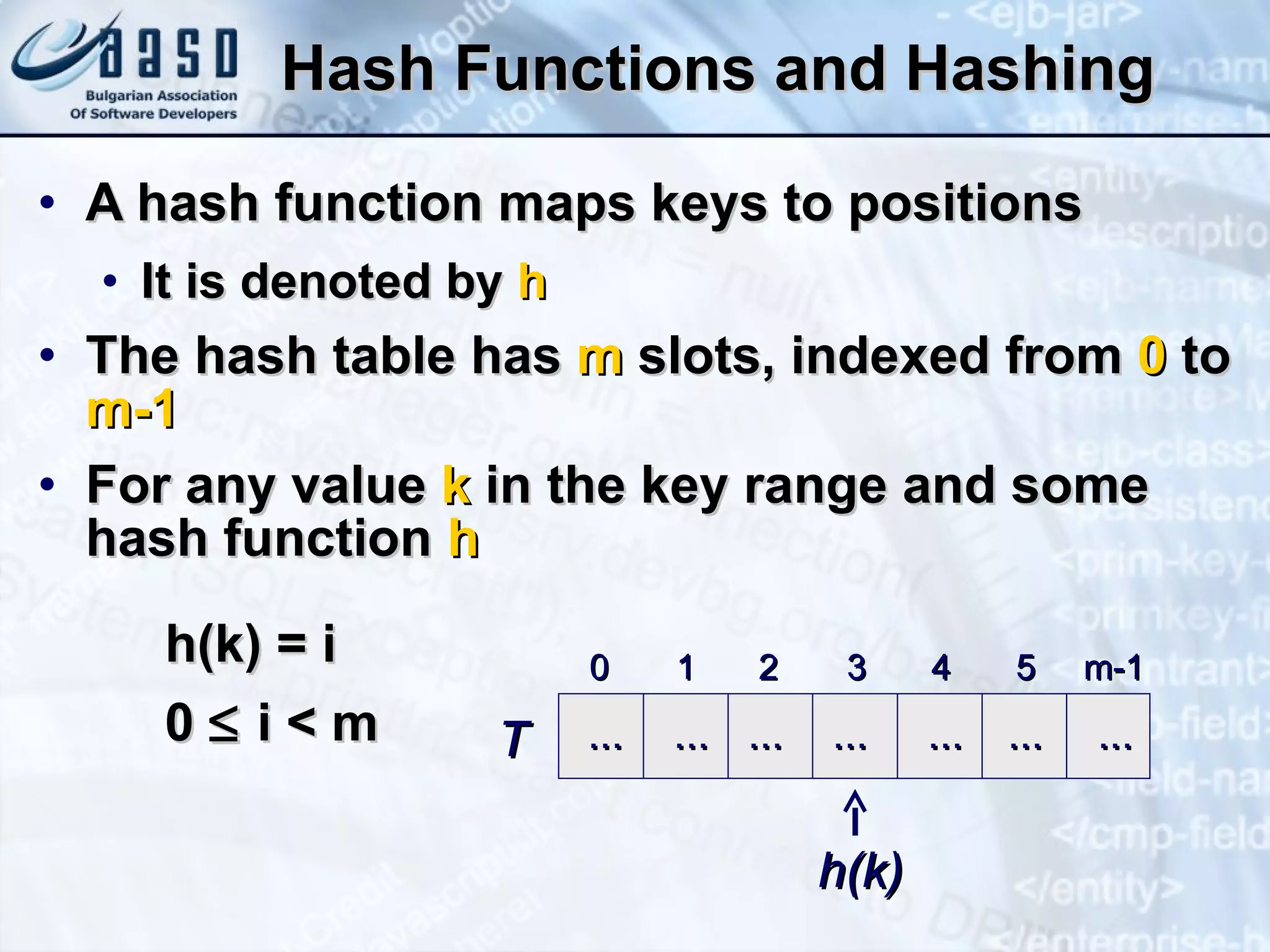
![Mapping Functions Perfect hashing function (PHF) h(k) : one-to-one mapping from each key k to integers in [ 0 , m -1 ] The PHF maps each key to a distinct integer within some manageable range Finding a perfect hashing function is in most cases impossible More realistically Hash functions h(k) map most of the keys onto unique integers, but not all](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-58-2048.jpg)

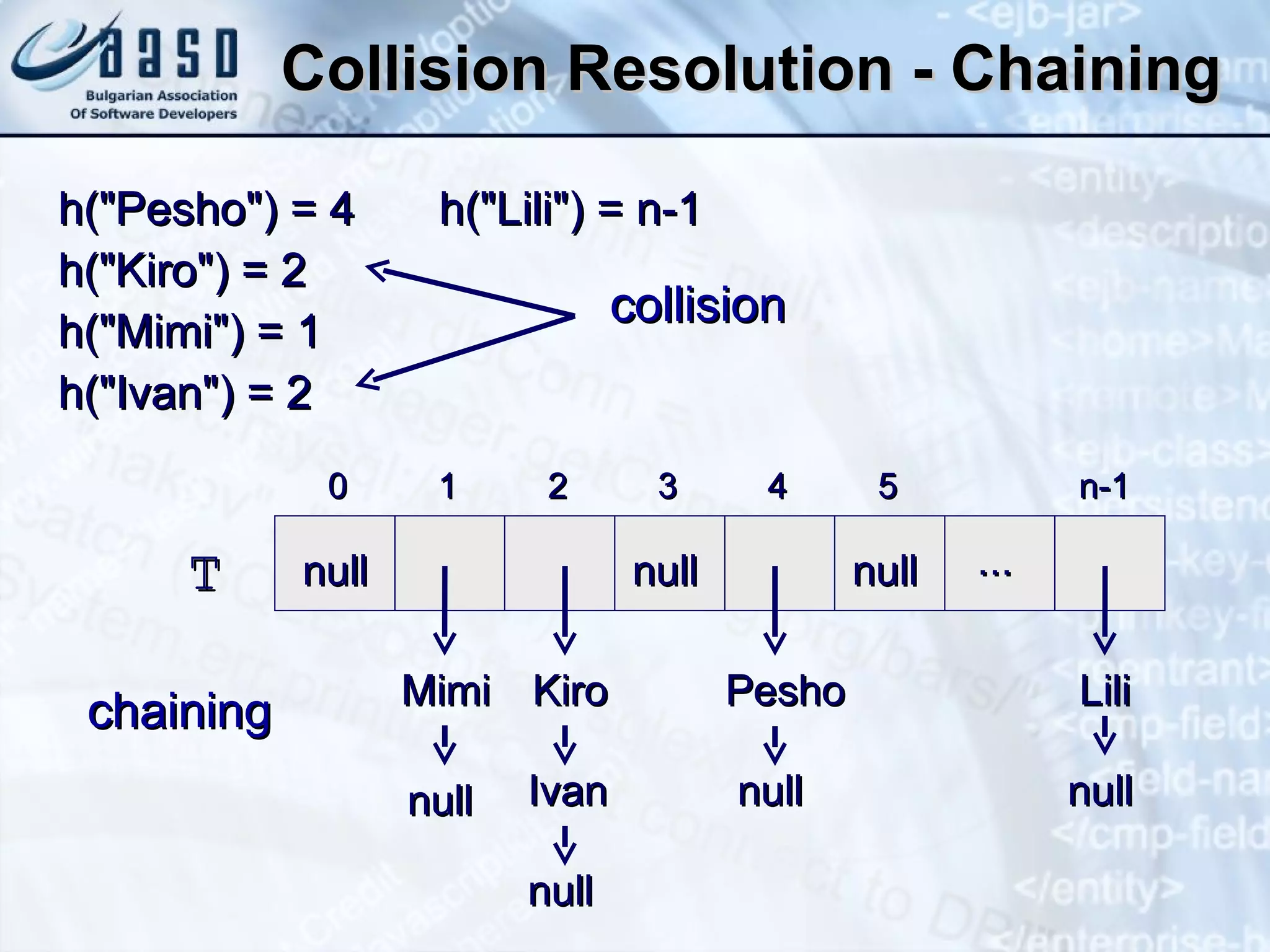





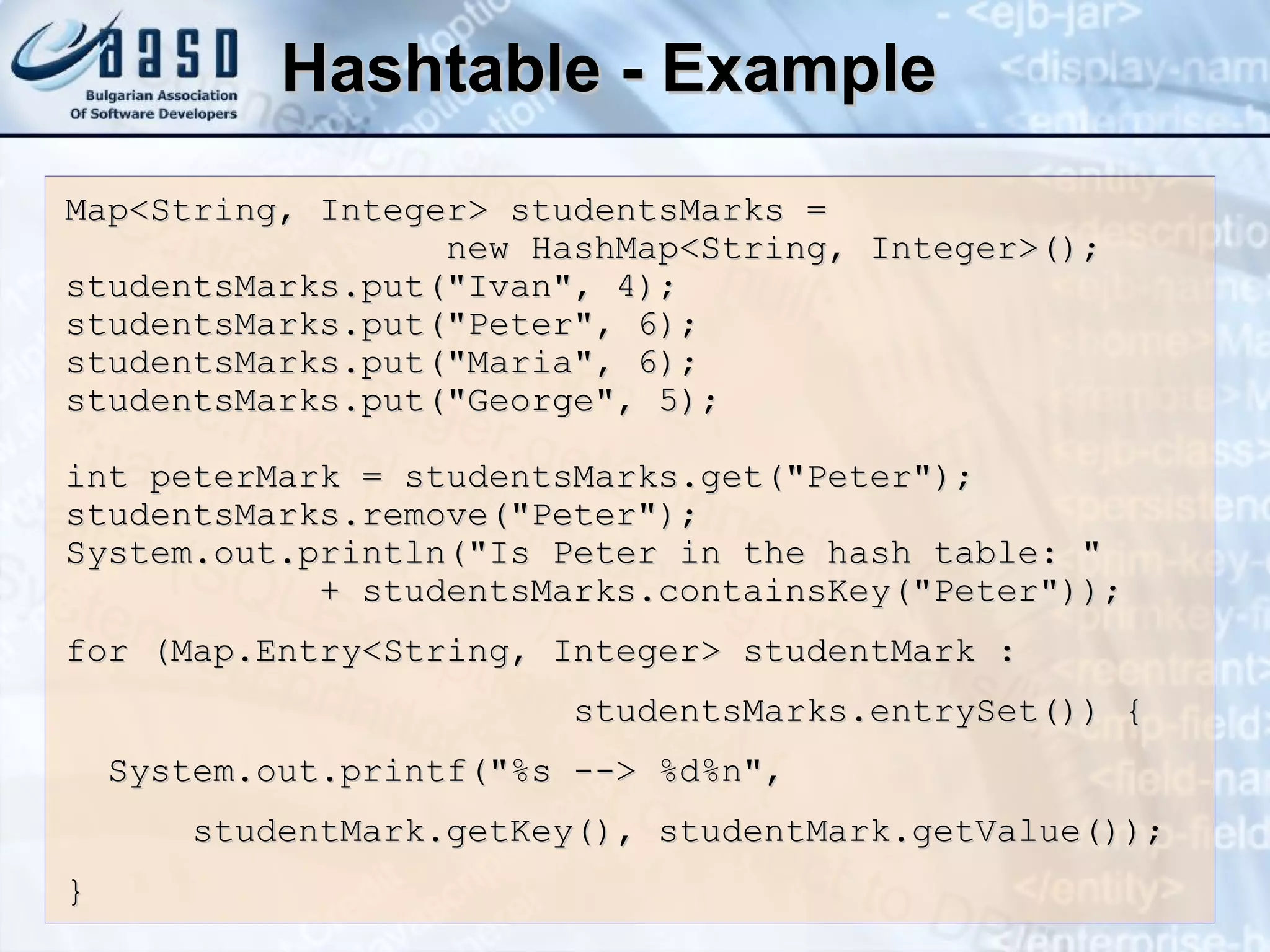

![Counting Words in a Text String s = "Welcome to our Java course. In this " + "course you will learn how to write simple " + "programs in Java"; String[] words = s.split("[ ,.]"); Map<String, Integer> wordsCount = new HashMap<String, Integer>(); for (String word : words) if (!"".equalsIgnoreCase(word)) { int count = 1; if (wordsCount.containsKey(word)) count += wordsCount.get(word); wordsCount.put(word, count); } for (String word : wordsCount.keySet()) System.out.printf("%s --> %d%n", word, wordsCount.get(word));](https://image.slidesharecdn.com/basic-data-structures-v-1-1-101203232258-phpapp02/75/Basic-data-structures-v-1-1-68-2048.jpg)