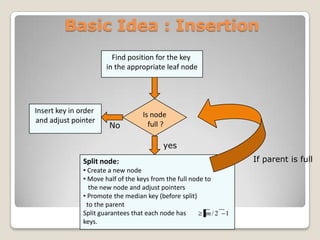
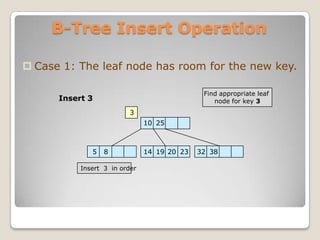
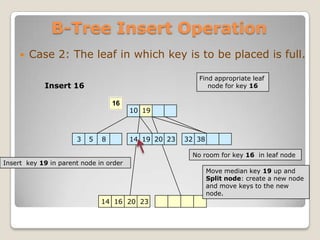
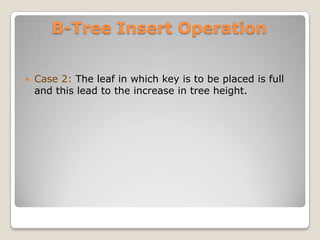
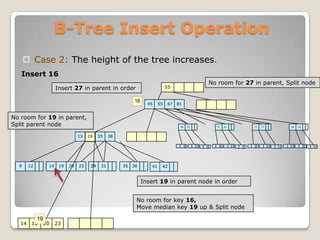
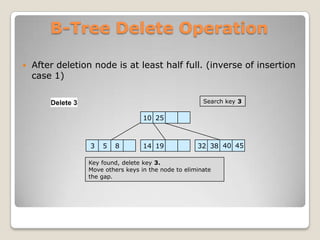
The document discusses B-trees, which are self-balancing tree data structures that allow efficient insertion and deletion of data while keeping the tree height shallow. B-trees allow for efficient searching, insertion, and deletion of data in logarithmic time by allowing nodes to have more than two child nodes, and by splitting and merging nodes as needed to balance the tree during operations. The document covers the basic structure and properties of B-trees and explains the algorithms for insertion and deletion of keys through cases involving splitting, merging, redistribution and underflow of nodes.

![Definition
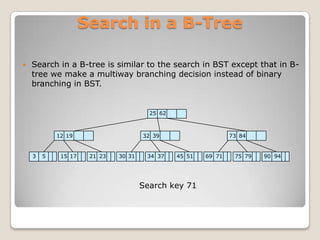
A B-tree is a tree data structure that keeps data sorted and allows
searches, sequential access, insertions, and deletions in
logarithmic amortized time. The B-tree is a generalization of
a binary search tree in which more than two paths diverge from a
single node.
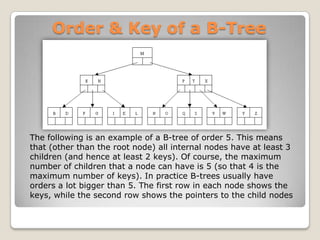
A B-tree of order m (the maximum number of children for each
node) is a tree which satisfies the following properties:
Every node has at most m children.
Every node (except root and leaves) has at least m⁄2 children.
The root has at least two children if it is not a leaf node.
All leaves appear in the same level, and carry information.
A non-leaf node with k children contains k−1 keys.
Declaration in C:
typedef struct { int Count; // number of keys stored in the current node
ItemType Key[3]; // array to hold the 3 keys [4];
long Branch[4]; // array of fake pointers (record numbers)
} NodeType;](https://image.slidesharecdn.com/b-treelong-111102094257-phpapp01/85/B-tree-long-2-320.jpg)