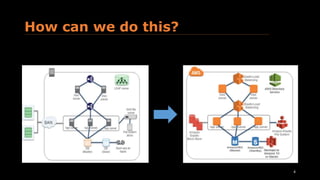
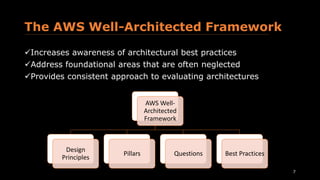
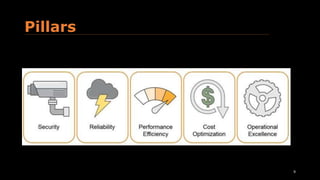
The document provides an overview of the AWS Well-Architected Framework. It discusses the six advantages of moving to the cloud, including trading capital expense for flexible expense. It then outlines the topics that will be covered, including design principles, pillars of security, reliability, performance efficiency, cost optimization, and operational excellence. Finally, it gives examples of questions that can be asked within each pillar to evaluate architectures.