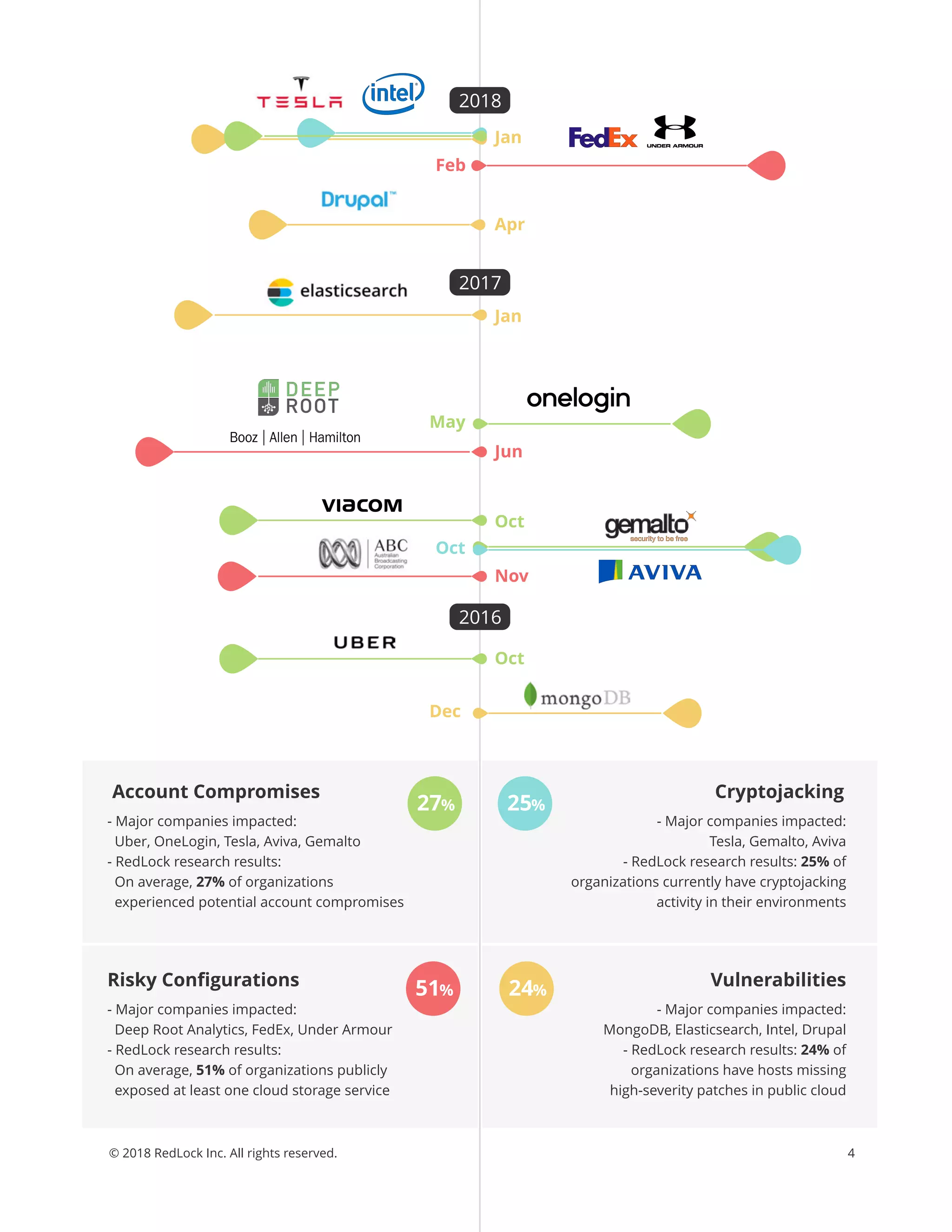
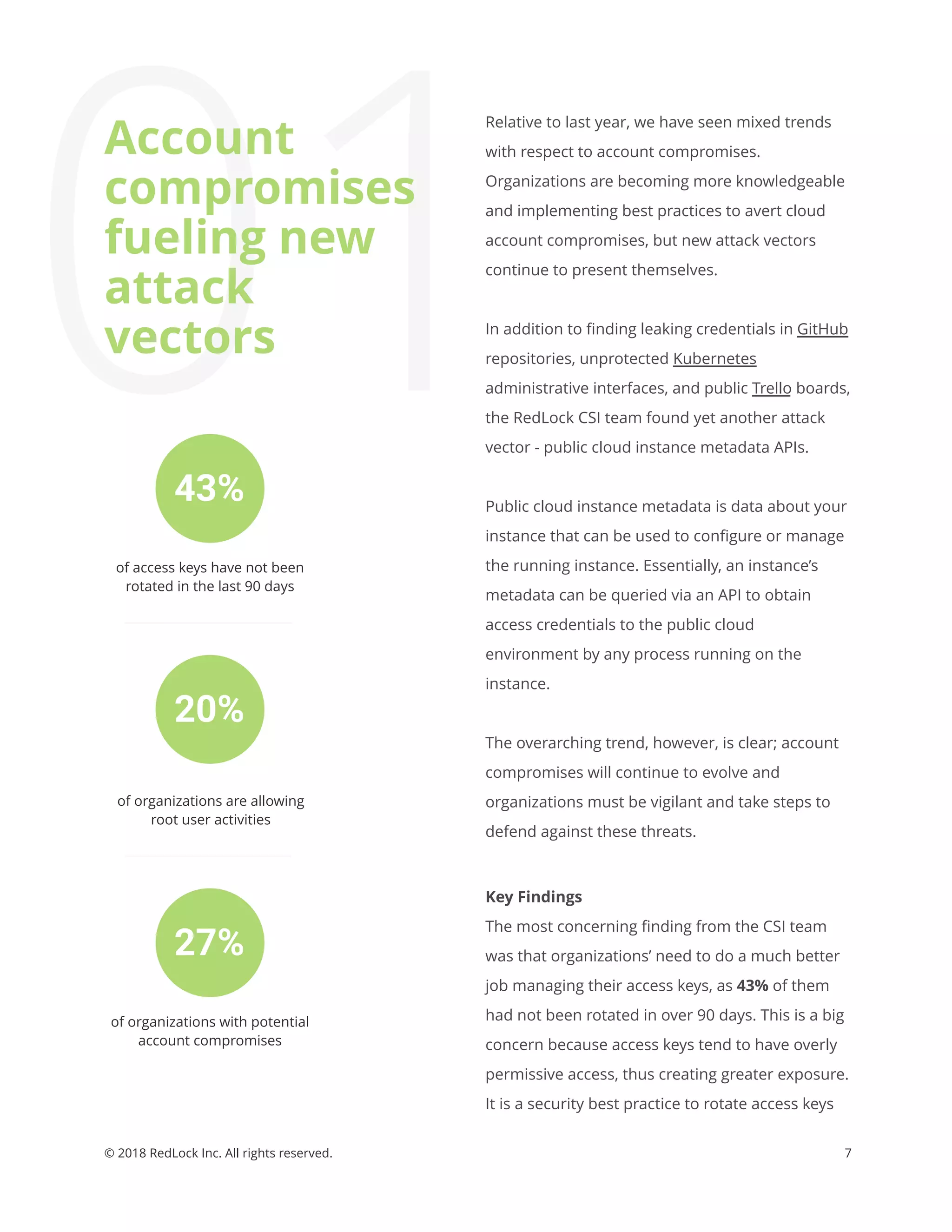
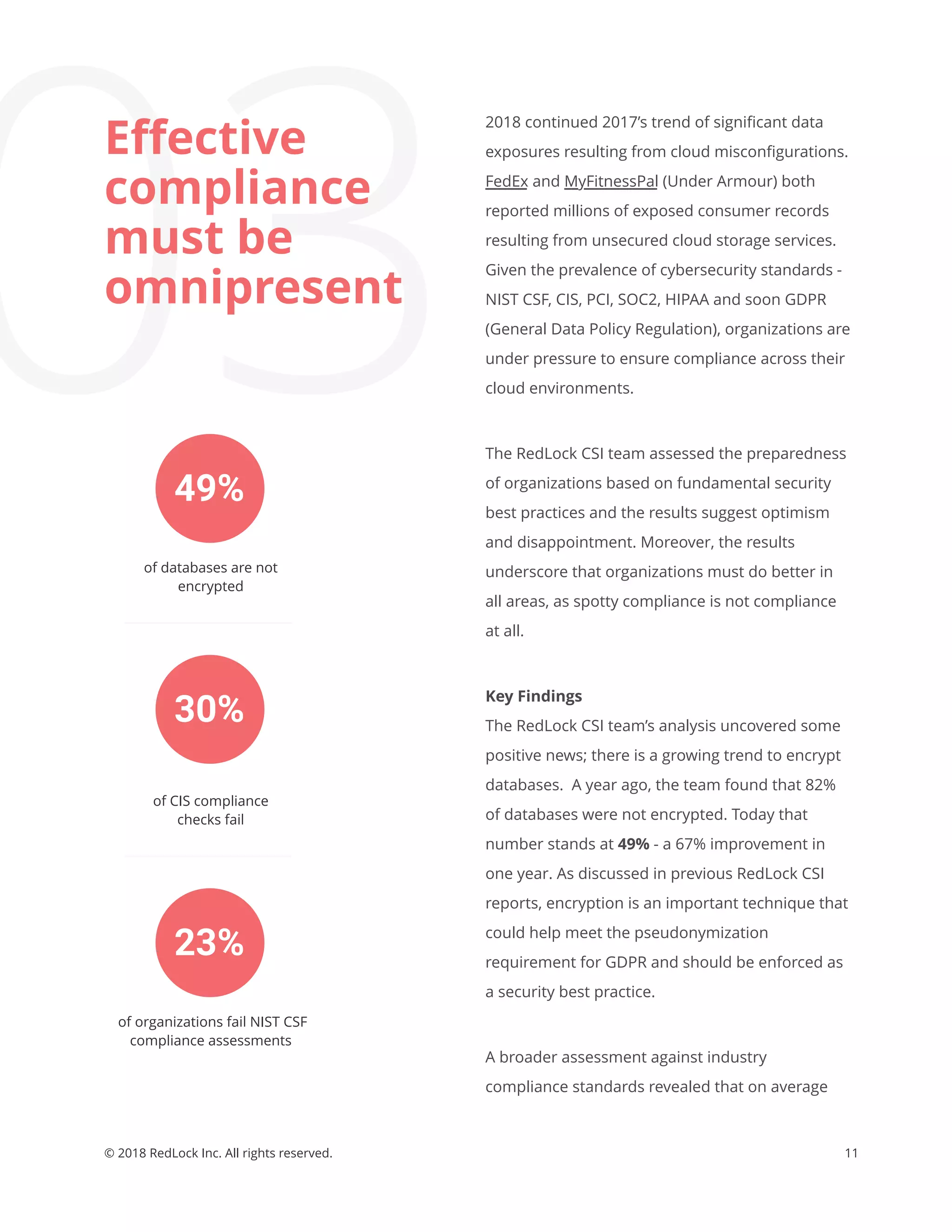
The Redlock CSI team's May 2018 report outlines alarming trends in cloud security, highlighting issues such as account compromises, widespread cryptojacking, and ineffective compliance practices among organizations. Key findings indicate that many organizations are not adequately managing access keys and have significant vulnerabilities in their cloud environments, leading to rising security risks. To combat these challenges, the report provides actionable tips and emphasizes the need for continuous monitoring and enforcement of security best practices.