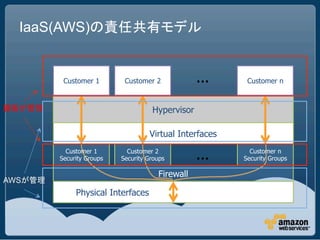
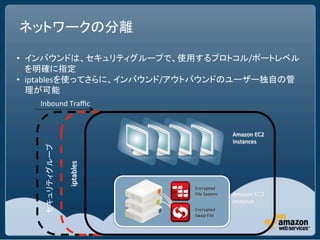
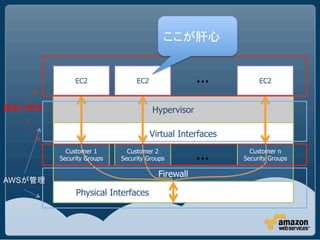
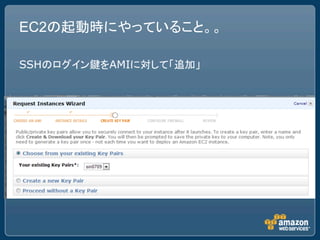
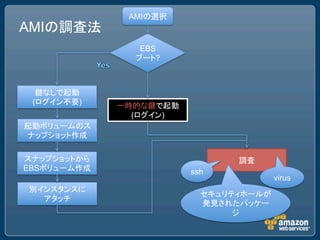
This document discusses security best practices for Amazon Web Services (AWS). It recommends removing SSH host key pairs from public Amazon Machine Images (AMIs) to prevent security risks. It also suggests configuring virtual private clouds (VPCs) to restrict outbound traffic, using smaller instance types like t1.micro that offer less resources to attackers, mounting filesystems as noexec to prevent execution of unauthorized code, and using chroot jails.