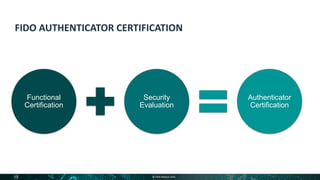
The document outlines the FIDO Alliance's certification programs designed to enhance product quality, security, and market differentiation through standardized evaluations. It details functional certifications, security levels for authenticators, and testing metrics such as false accept/reject rates and presentation attack detection. Ultimately, the goal is to establish a 'FIDO certified' status to build consumer confidence and trust in product offerings.