Embed presentation
Download to read offline
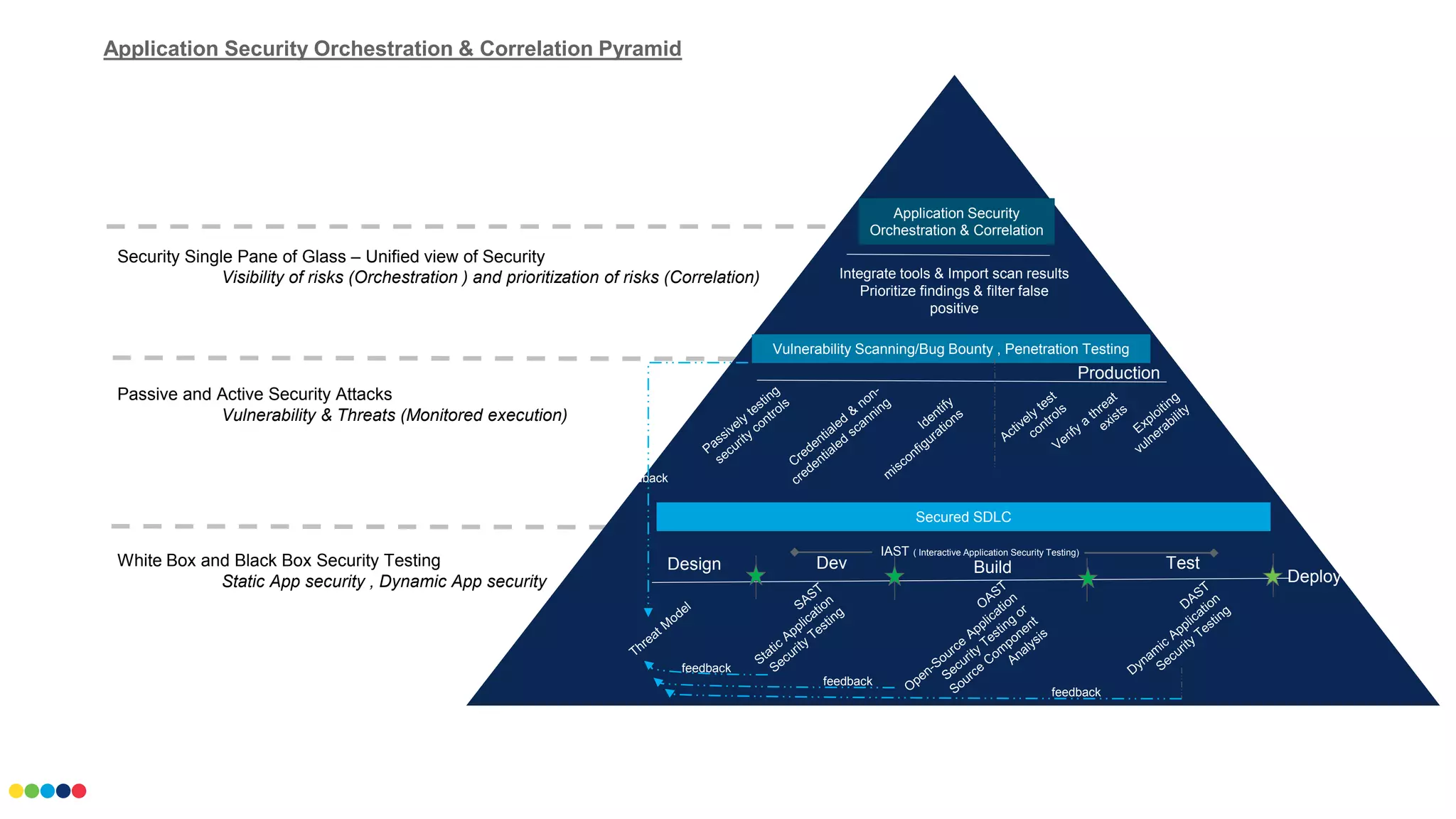

This document outlines the key steps in application security from design through deployment. It discusses integrating tools for vulnerability scanning, prioritizing findings while filtering false positives. It also covers various security testing techniques like static, dynamic, white box, and black box testing as well as passive and active security attacks. The goal is unified visibility and prioritization of risks through application security orchestration and correlation.
