Embed presentation
Downloaded 15 times


![API Key
• Like username/password
for user, apikey is
application-id/application-
secret [optional] for the
application](https://image.slidesharecdn.com/apisecurityprotection-210422152322/85/IBM-APIc-API-security-protection-mechanism-3-320.jpg)
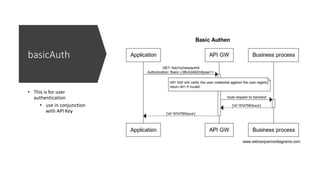
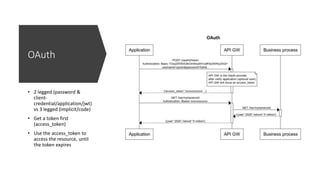


This document discusses different security mechanisms for APIs, including API keys, basic authentication, OAuth 2.0, and mutual TLS (mTLS). API keys function similarly to usernames and passwords for applications to access APIs. Basic authentication is for user authentication to be used with API keys. OAuth 2.0 involves obtaining an access token to access resources, and has two-legged and three-legged flows. It exposes credentials only during the initial handshake, while API keys and basic auth expose them with each request. OAuth 2.0 thus has a lower chance of compromise if a token is stolen, since it is only valid for a limited time.


![API Key
• Like username/password
for user, apikey is
application-id/application-
secret [optional] for the
application](https://image.slidesharecdn.com/apisecurityprotection-210422152322/85/IBM-APIc-API-security-protection-mechanism-3-320.jpg)


