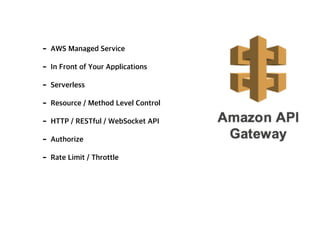
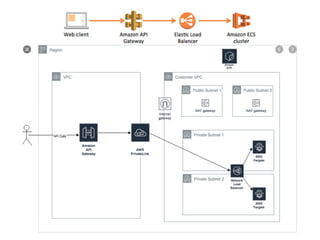
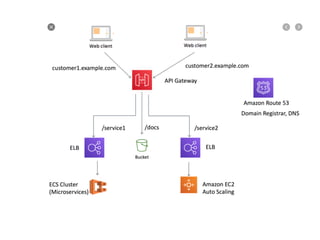
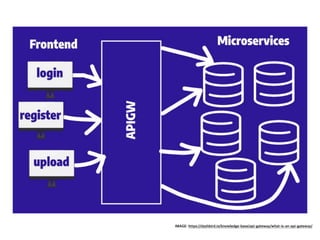
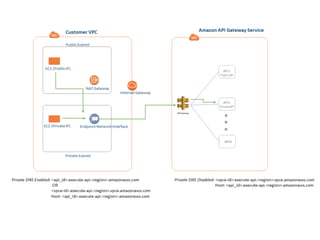
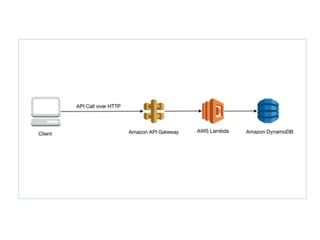
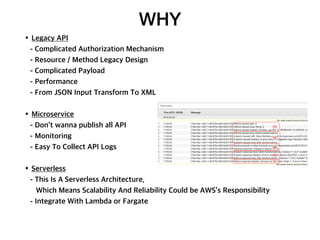
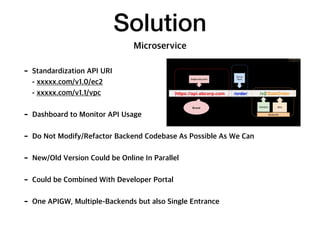
API Gateway is a managed service by AWS that sits in front of applications and provides resource and method level control over HTTP and RESTful APIs. It can authorize access, rate limit requests, and integrate with services like Lambda and Cognito. API Gateway helps standardize API URIs, monitor usage with dashboards, and provide a single entrance point to multiple backends for microservices. However, managing API Gateway requires considerations around infrastructure as code, debugging, and continuous delivery challenges. Key requirements of an API gateway include single entry point, authentication, traffic control, formatting transformations, security, networking, developer portals, and operational aspects like deployments, logging, and monitoring.