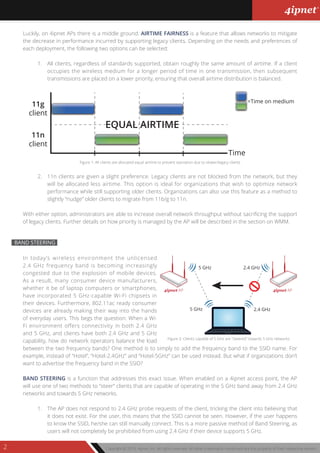
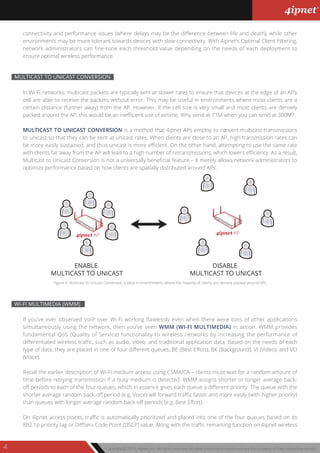
This document serves as a feature guide for 4ipnet access points, detailing various advanced functionalities such as airtime fairness, band steering, and multicast to unicast conversion aimed at optimizing network performance and security. It explains the distinctions between enterprise-grade and consumer access points, addressing common challenges faced in wireless networking, including legacy client support and network congestion. Additionally, it highlights security features like WPA2 and DHCP snooping that enhance network integrity in enterprise environments.