Embed presentation
Download to read offline


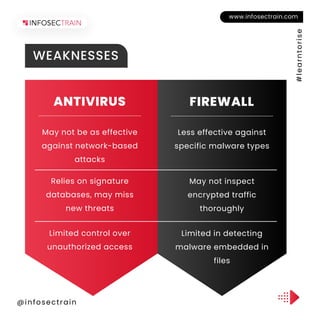

The document compares firewalls and antivirus software in terms of their roles in cybersecurity, highlighting their strengths and weaknesses. Firewalls control network access and employ methods like packet filtering and stateful inspection, while antivirus software focuses on identifying malware through signature-based detection and behavioral analysis. Both have limitations, such as firewalls being less effective against specific malware types and antivirus software struggling with encrypted traffic and new threats.




