This document discusses securing the AODV routing protocol against blackhole attacks in mobile ad-hoc networks (MANETs). It first introduces MANETs and the AODV protocol. It then explains the blackhole attack where a malicious node claims to have the shortest path to a destination and drops packets. The proposed solution is an algorithm that stores route replies in a table, calculates the average sequence number, and selects the route with a sequence number lower than the average to mitigate blackhole attacks. Simulation results show the algorithm increases packet delivery ratio with acceptable increases in end-to-end delay and throughput.
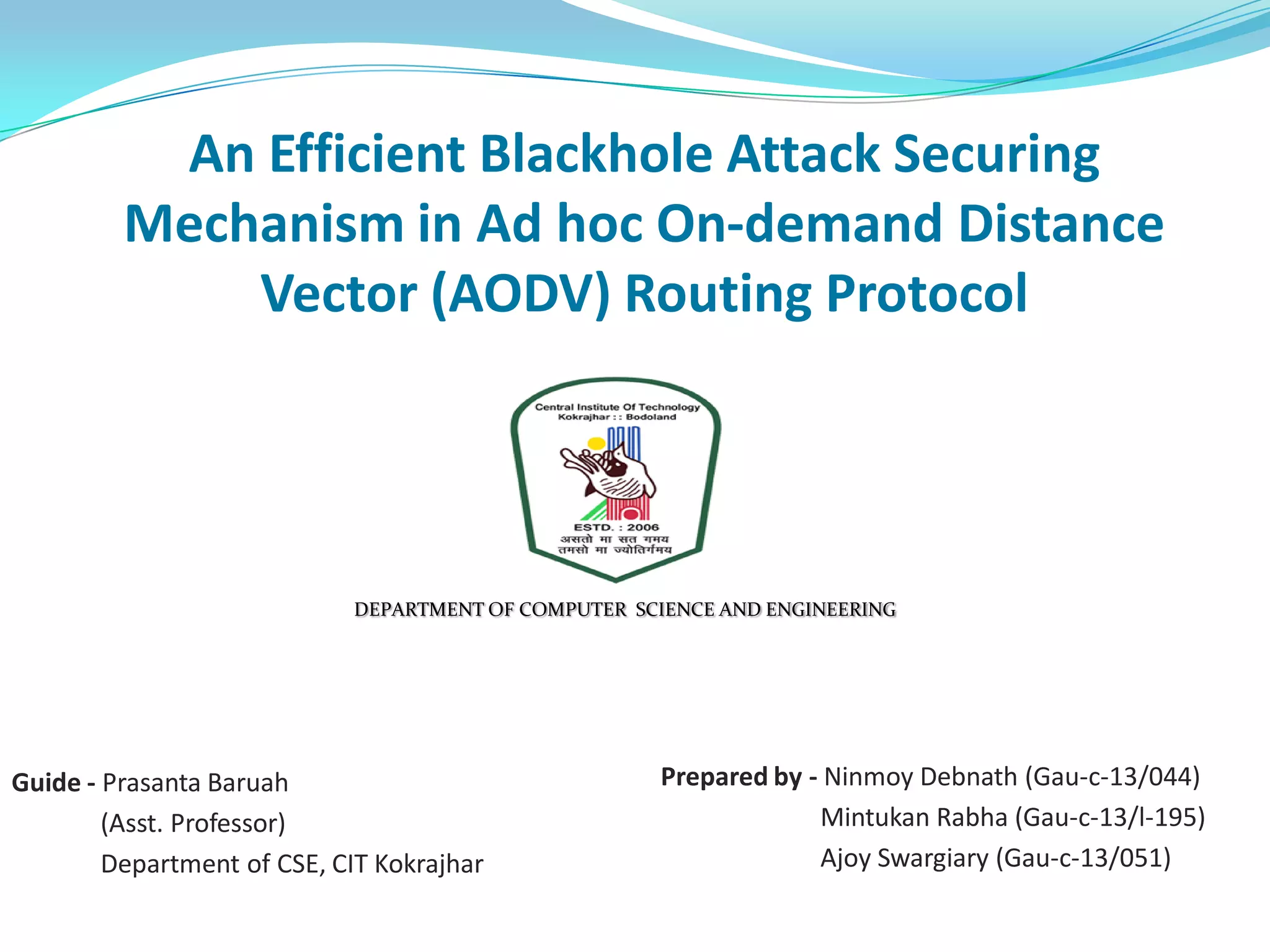







![AODV Routing Protocol
Reactive Routing Protocol.
AODV maintains all the route informations in the form of
tables.
AODV has three control packets
RREQ(Route Request Packet) broadcasting to find a
route.
RREP(Route Reply Packet) is to set up forward path.
RERR(Route Error Packet) to find any broken links.
[5]](https://image.slidesharecdn.com/finalre1-170527201445/75/An-Efficient-Black-Hole-Attack-Securing-Mechanism-in-Ad-Hoc-On-Demand-Distance-Vector-Routing-Protocol-9-2048.jpg)







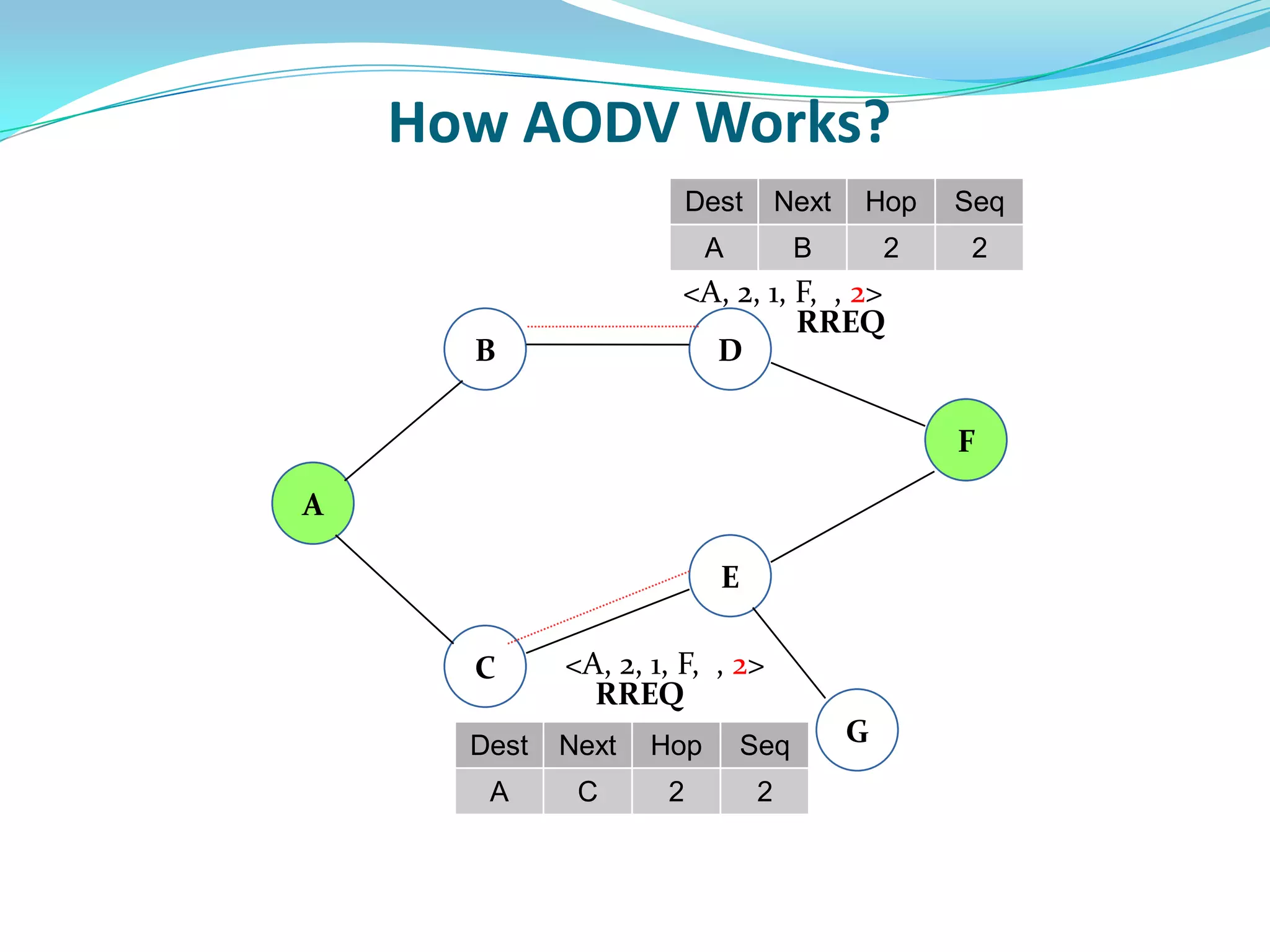

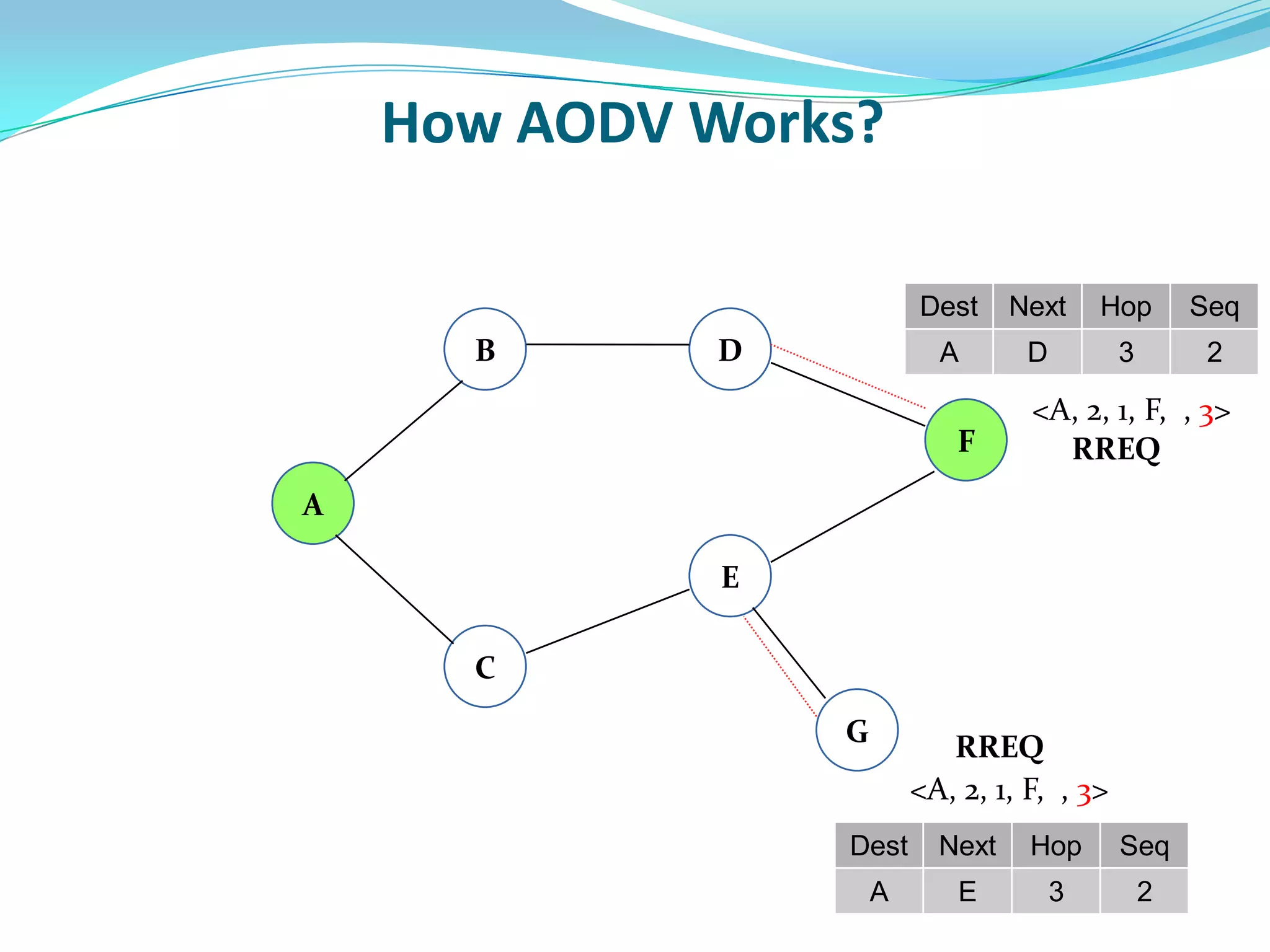
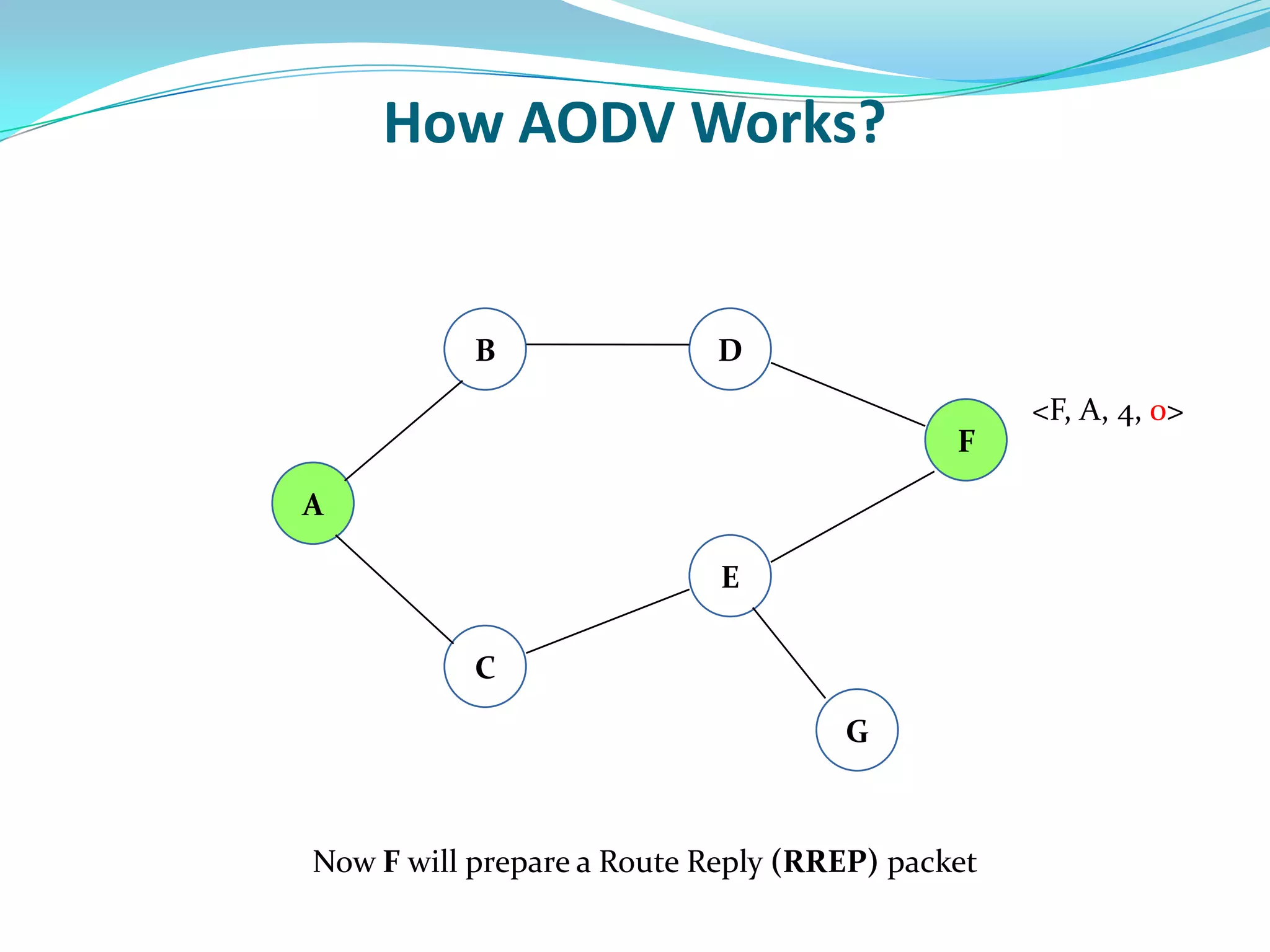





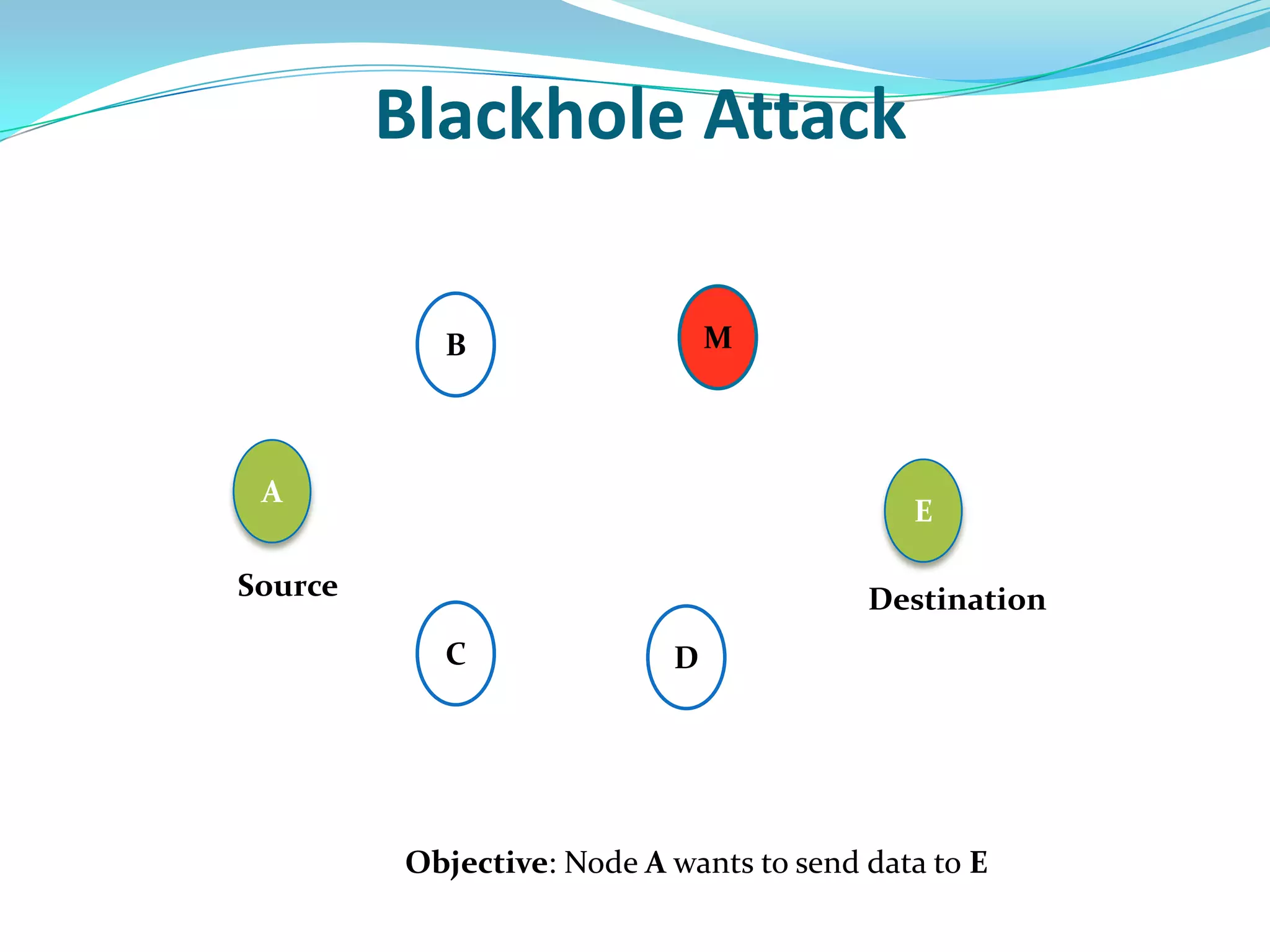
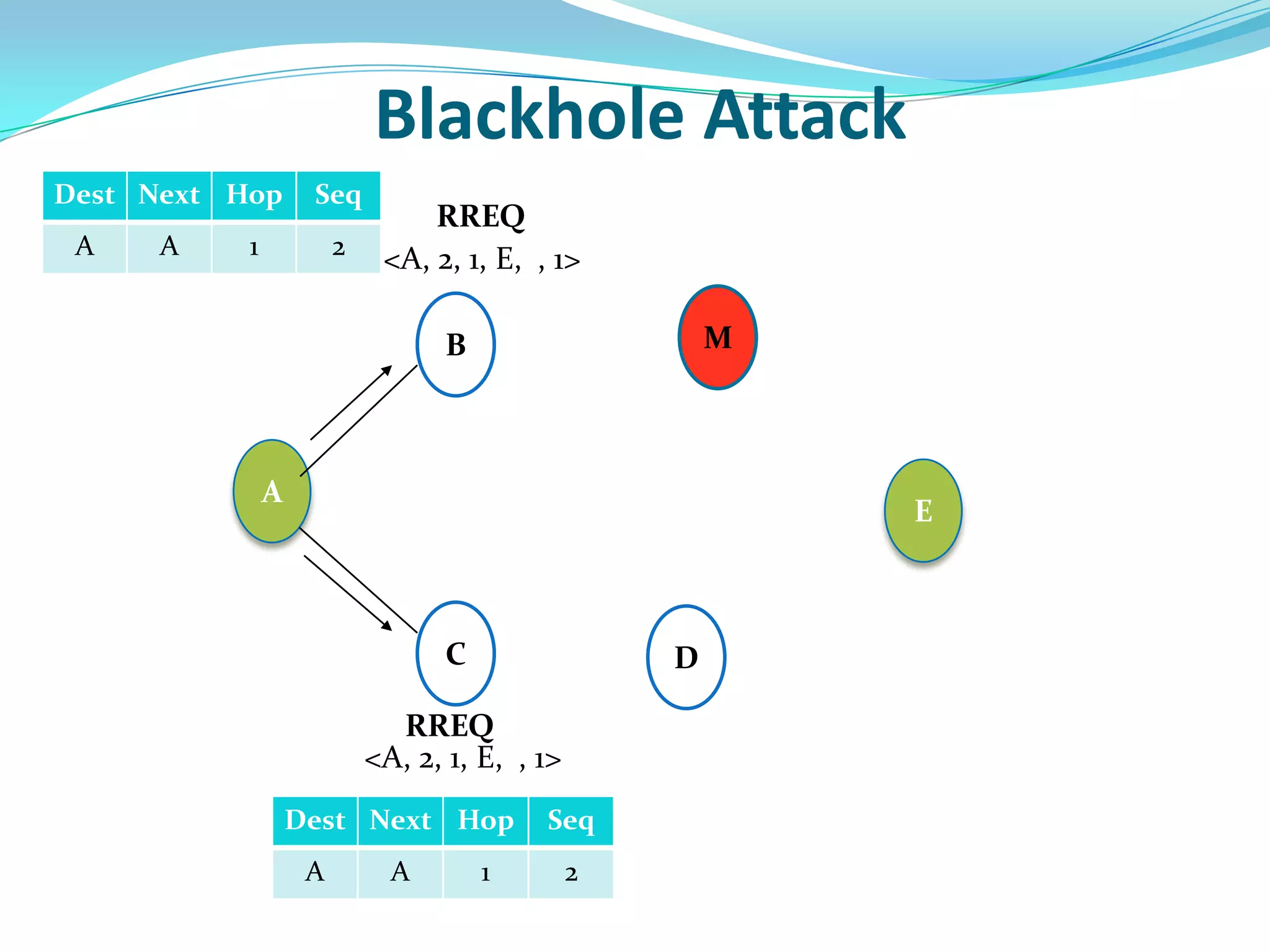
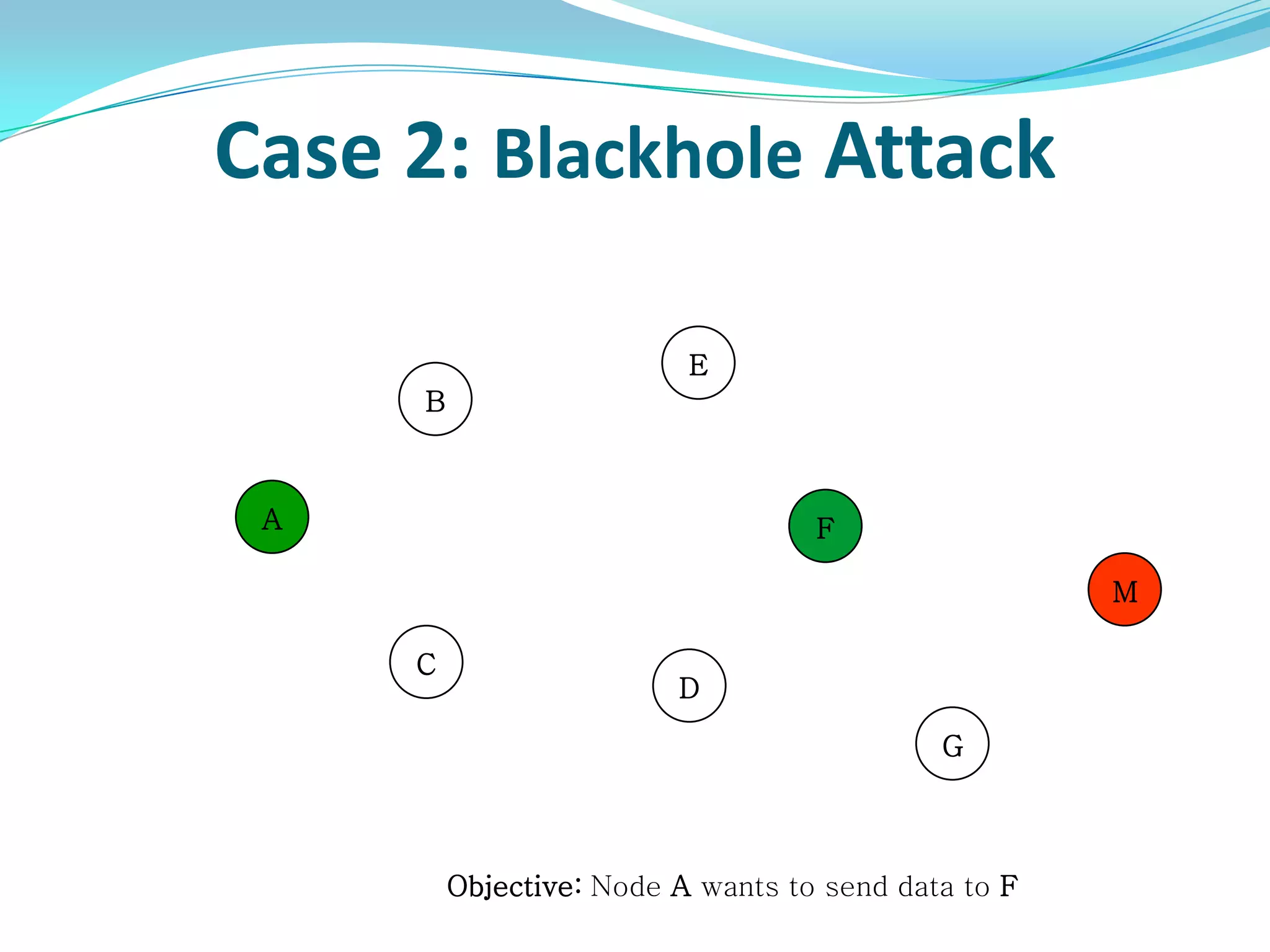
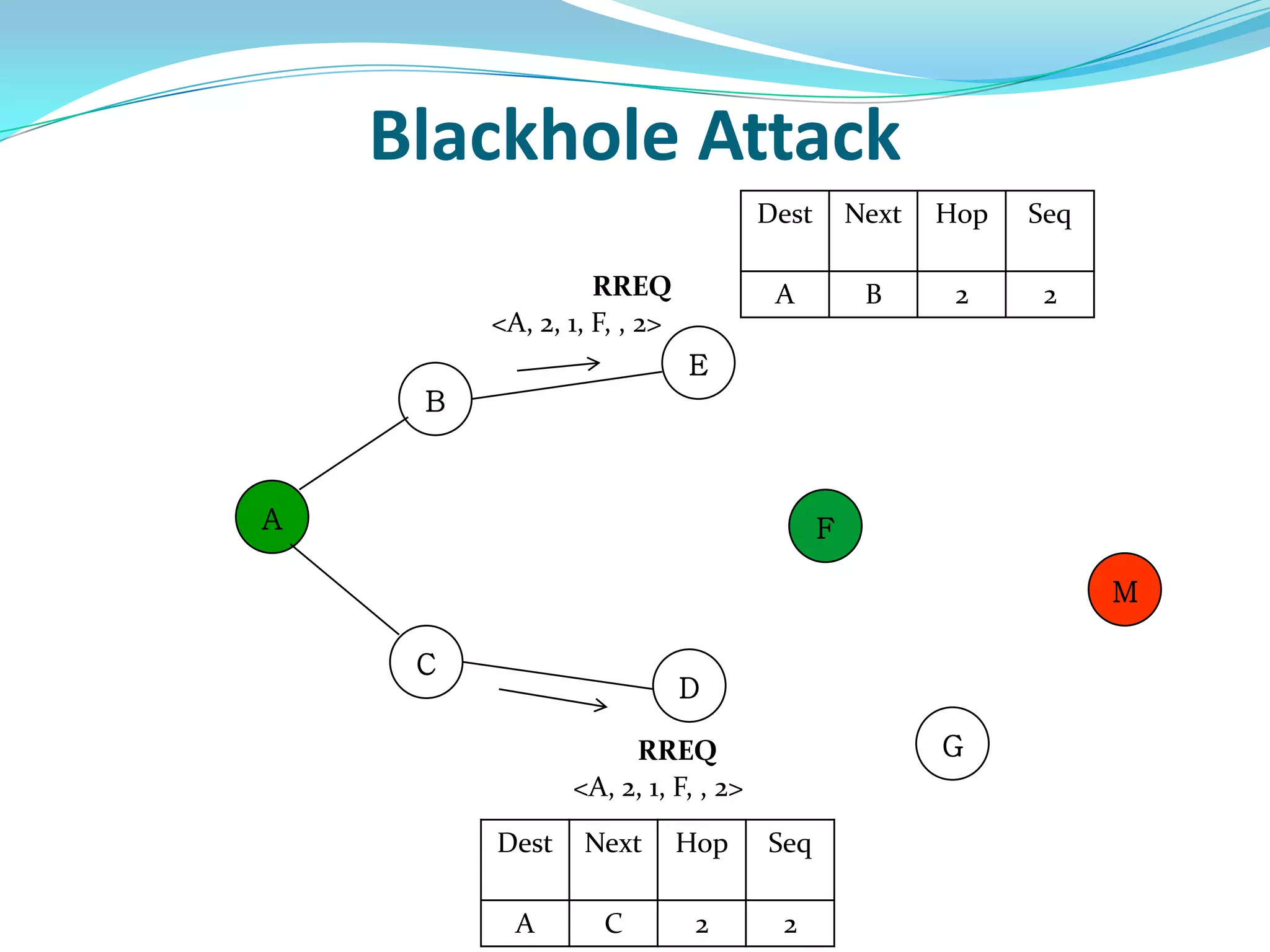
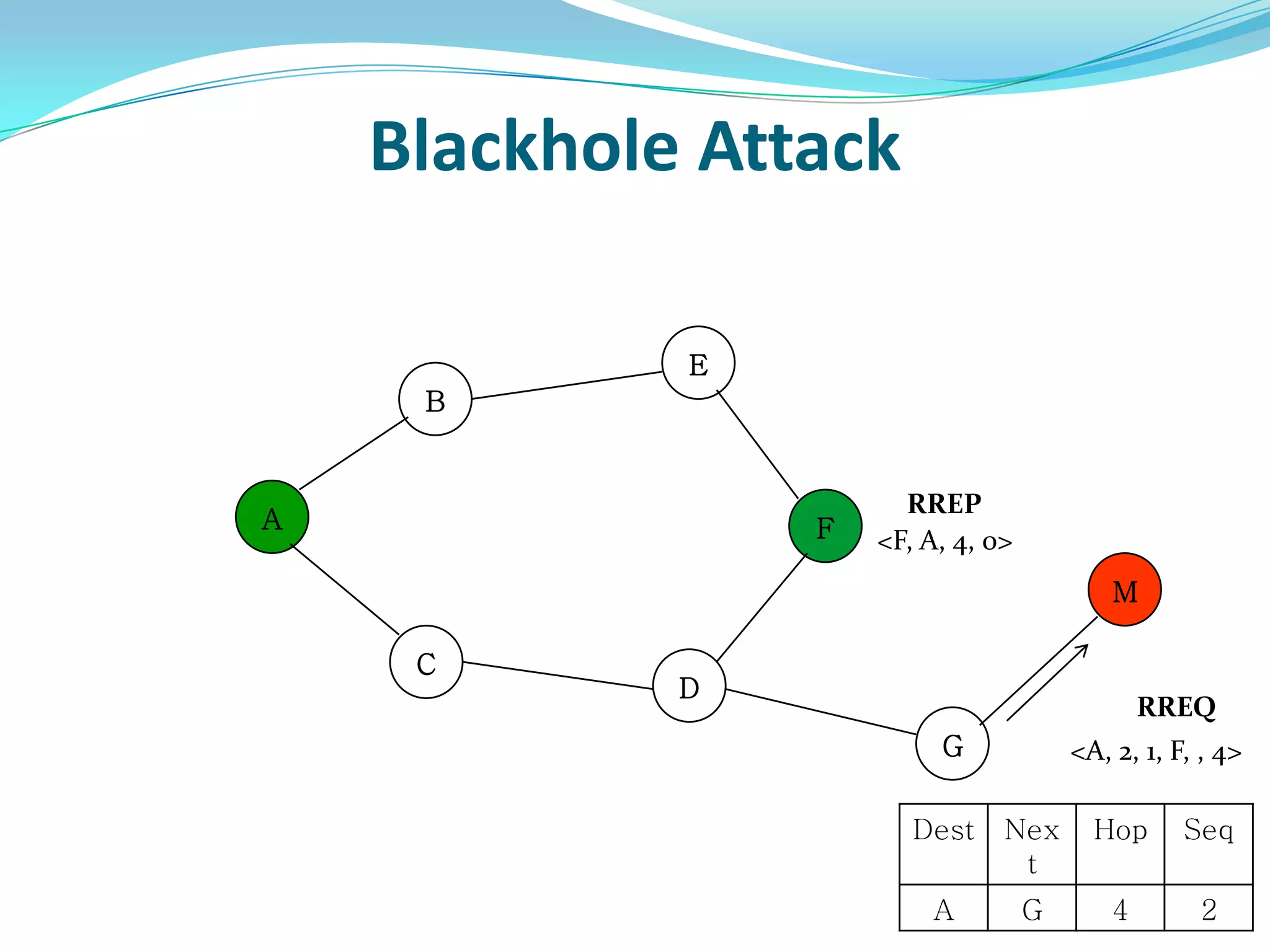
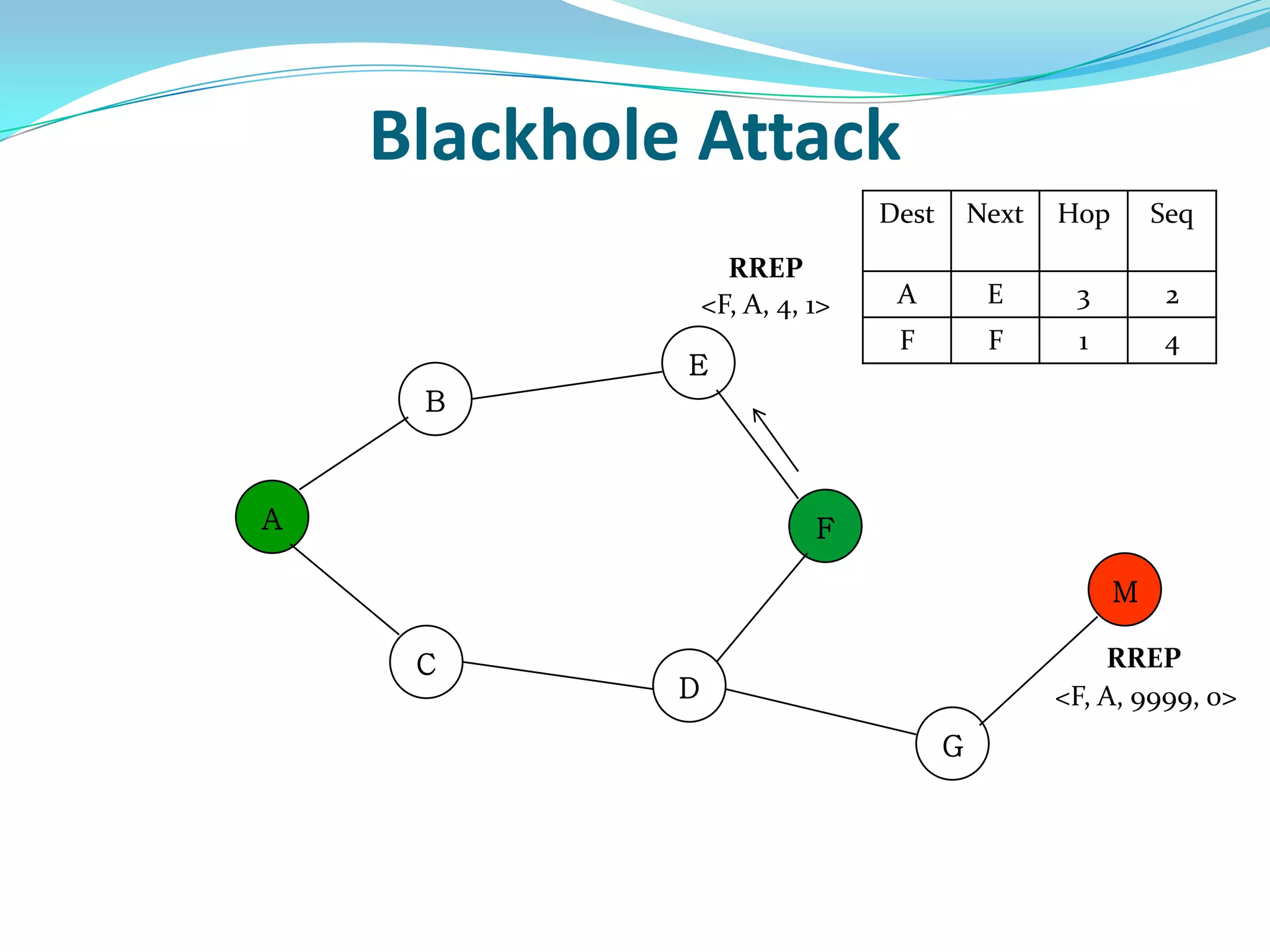
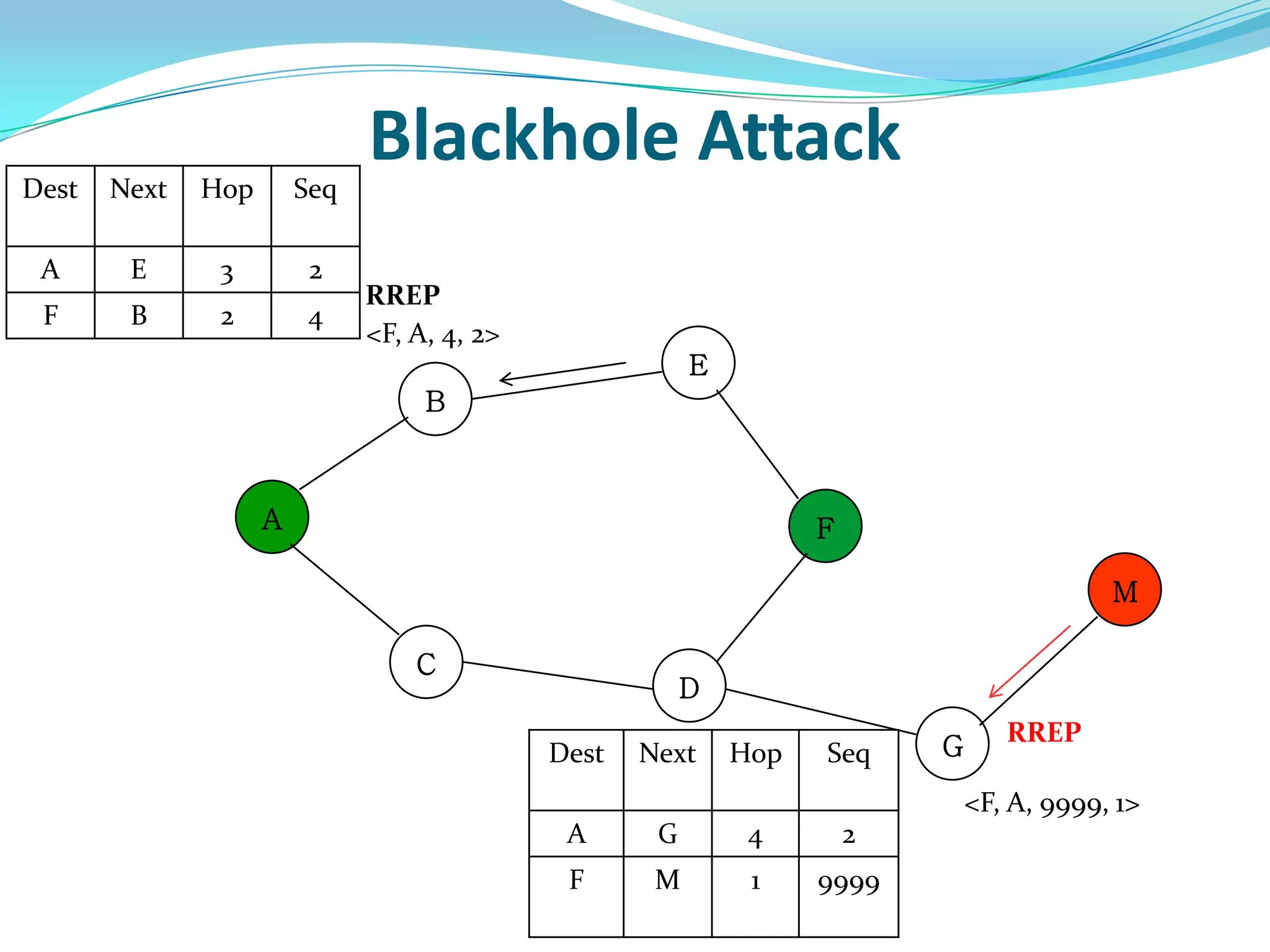
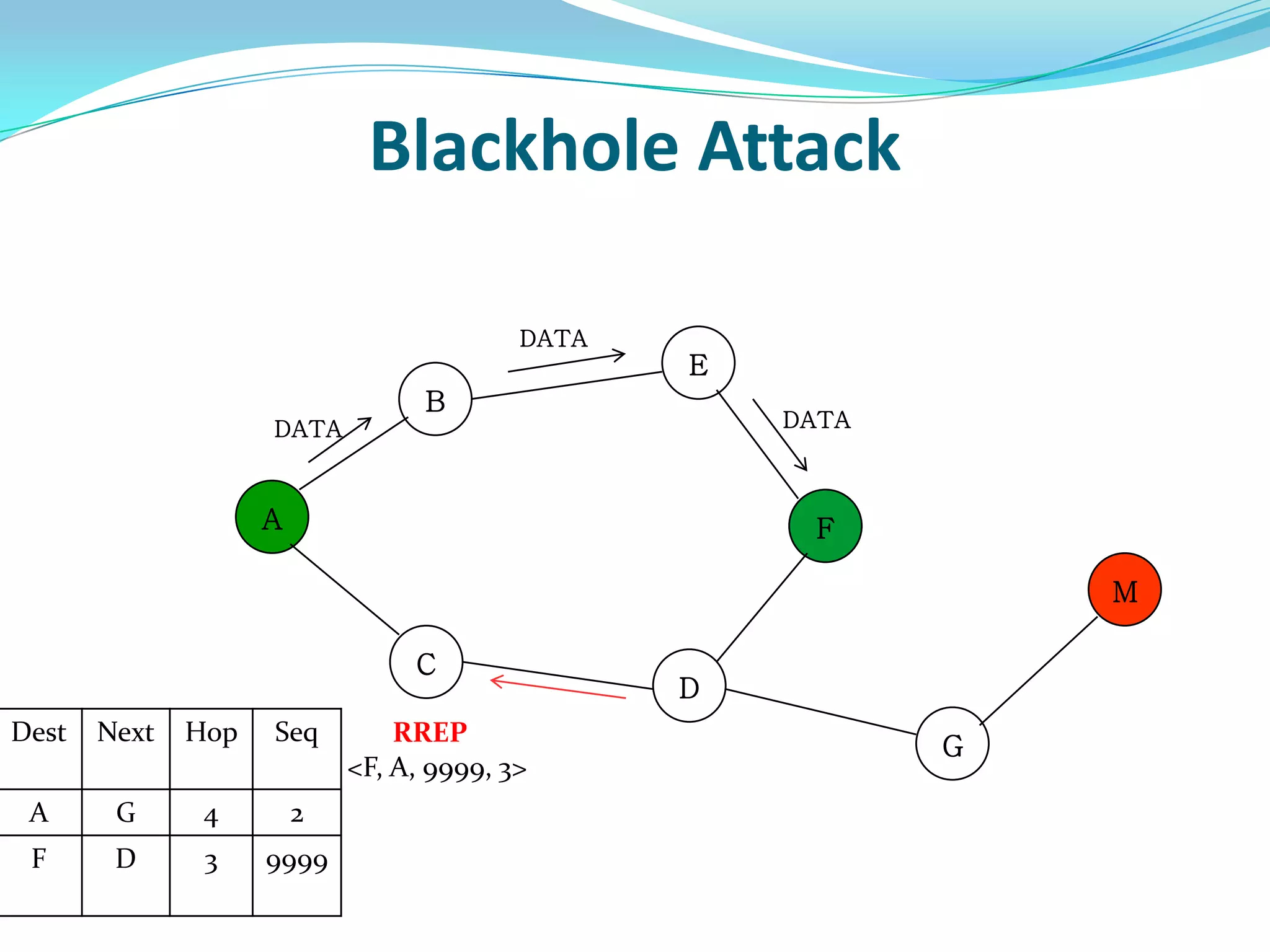
![What is Blackhole Attack?
● Malicious node utilizes the routing protocol to attack.
● Claim itself having shortest path to the destination node.
● Does not forward packets to its neighbors.
[4]](https://image.slidesharecdn.com/finalre1-170527201445/75/An-Efficient-Black-Hole-Attack-Securing-Mechanism-in-Ad-Hoc-On-Demand-Distance-Vector-Routing-Protocol-27-2048.jpg)