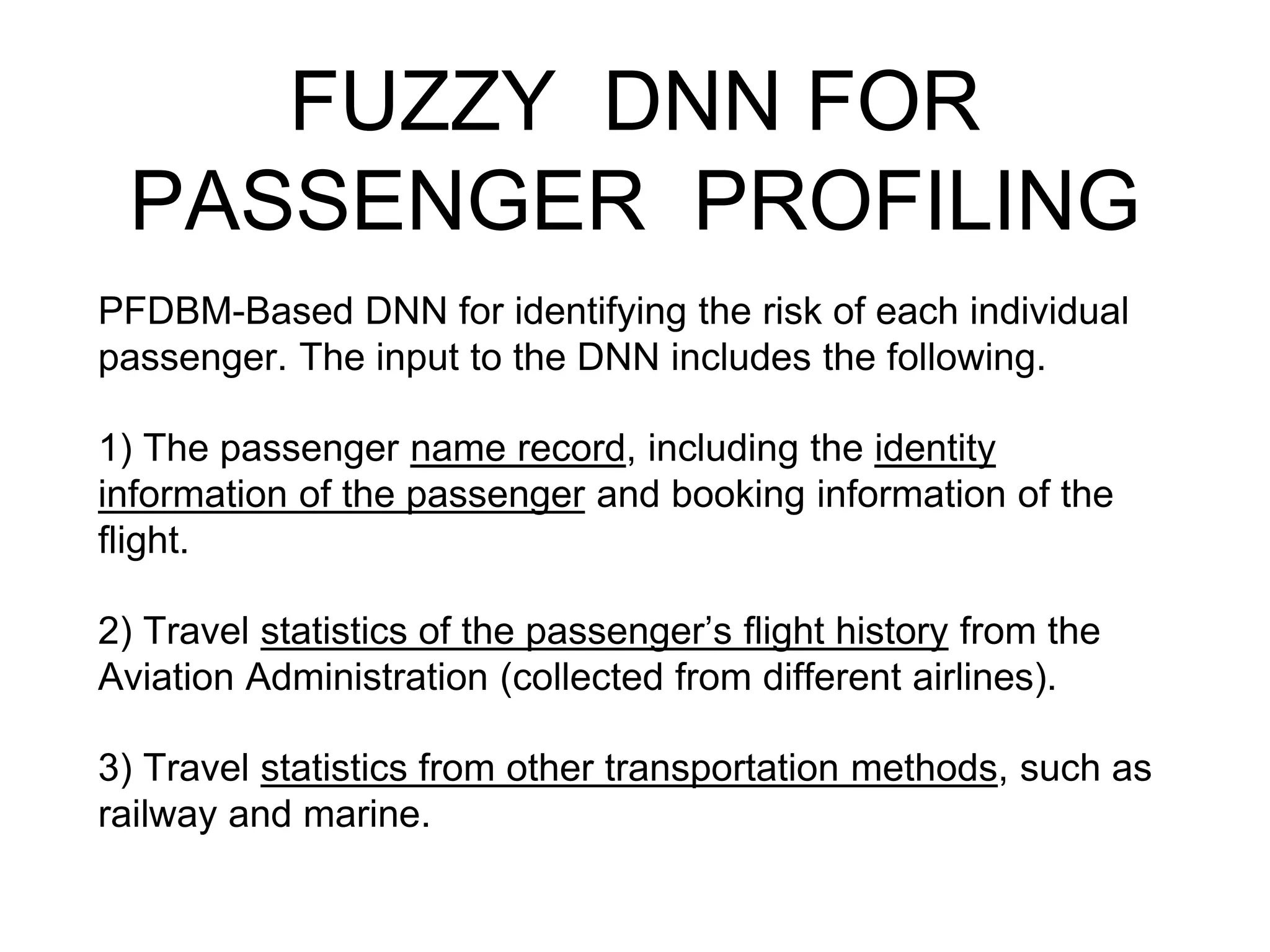
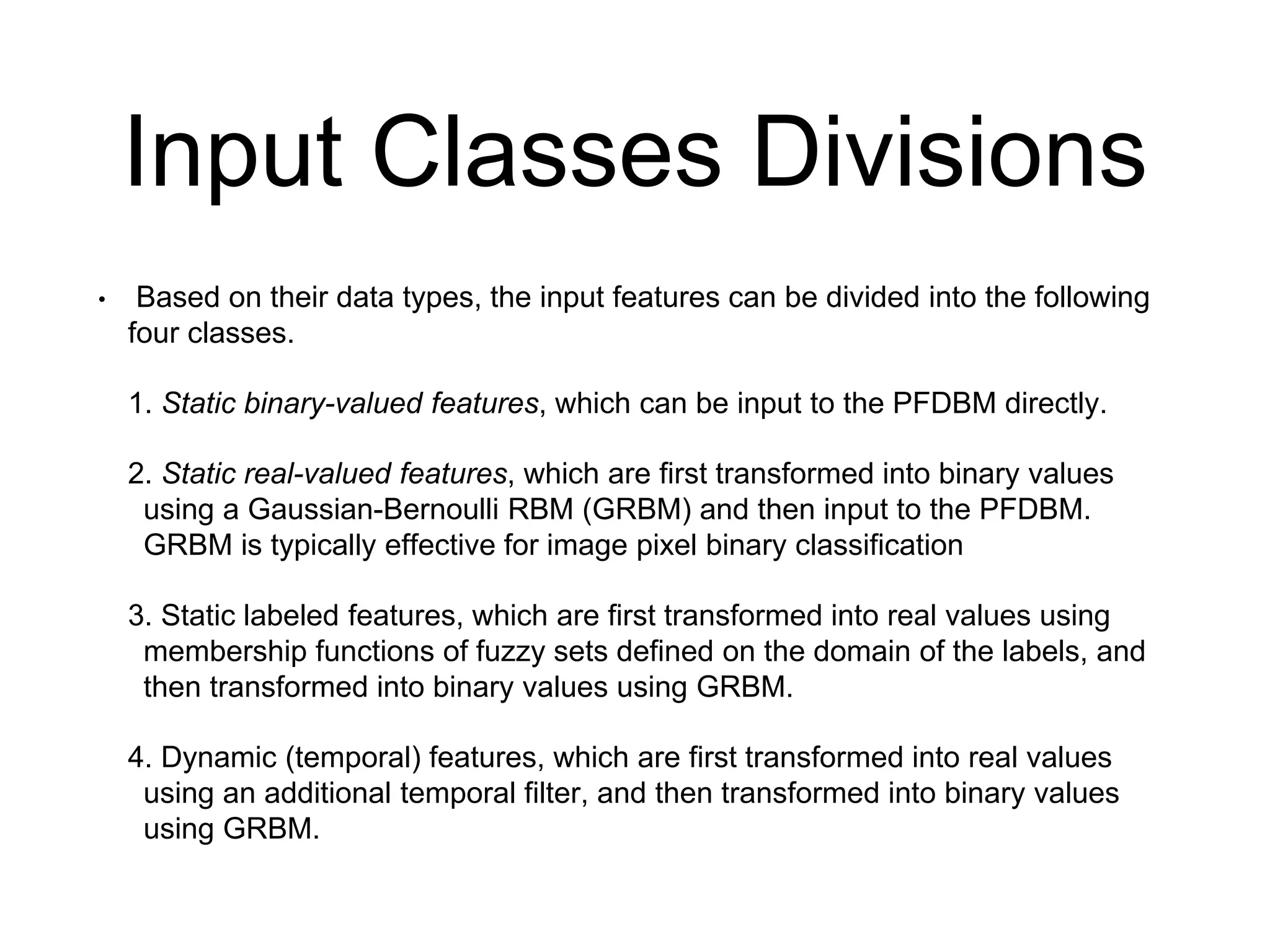
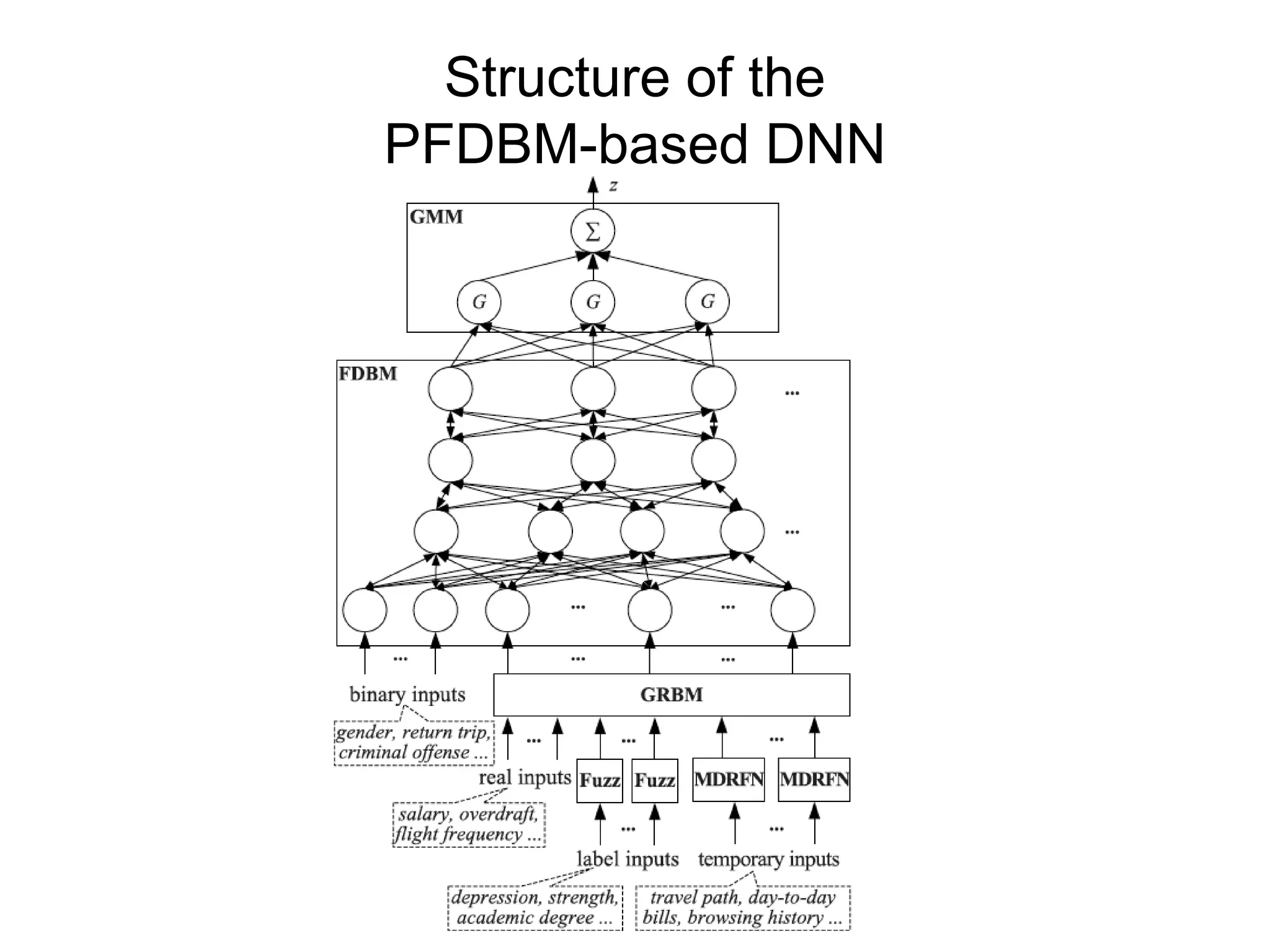
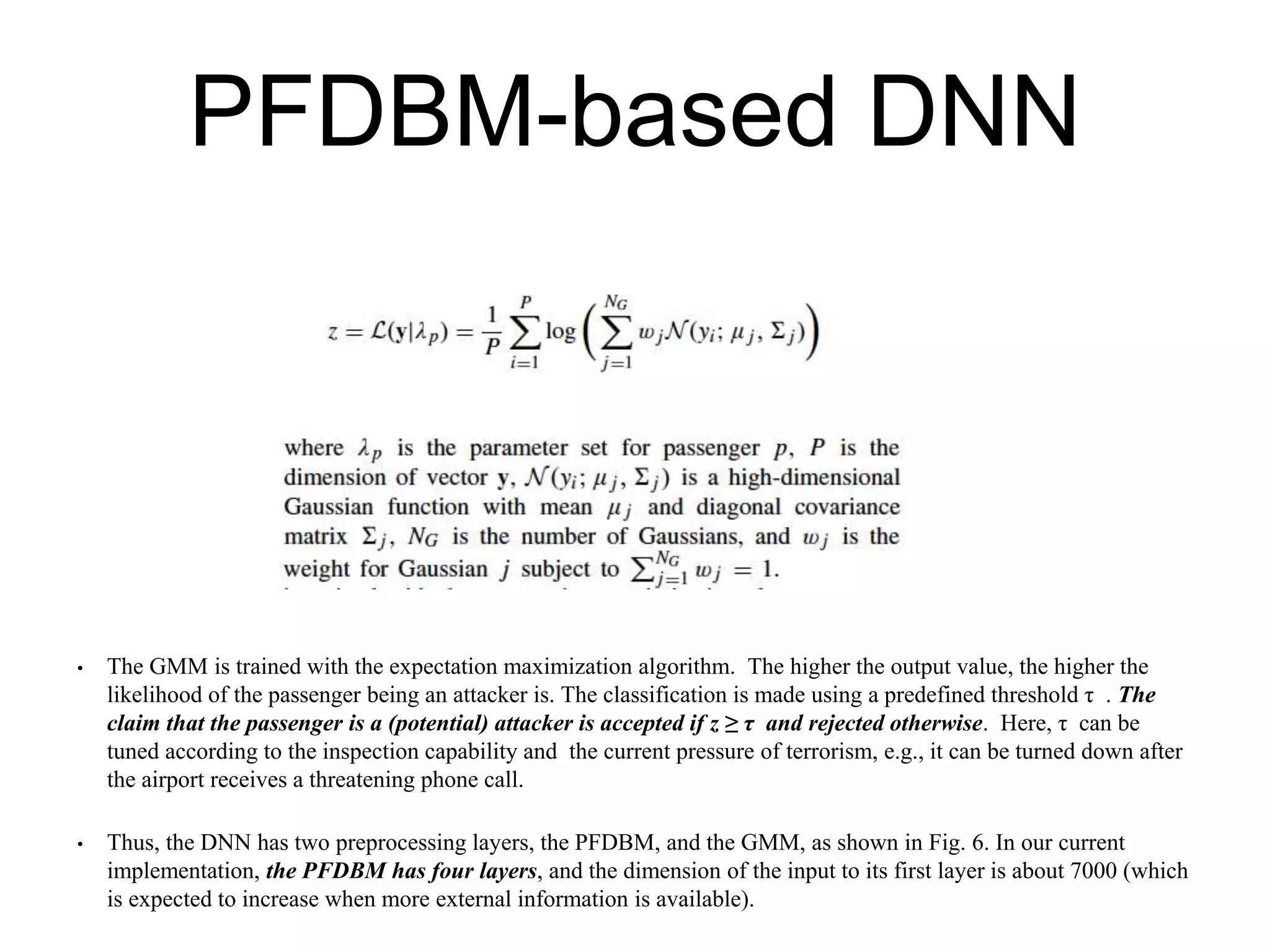
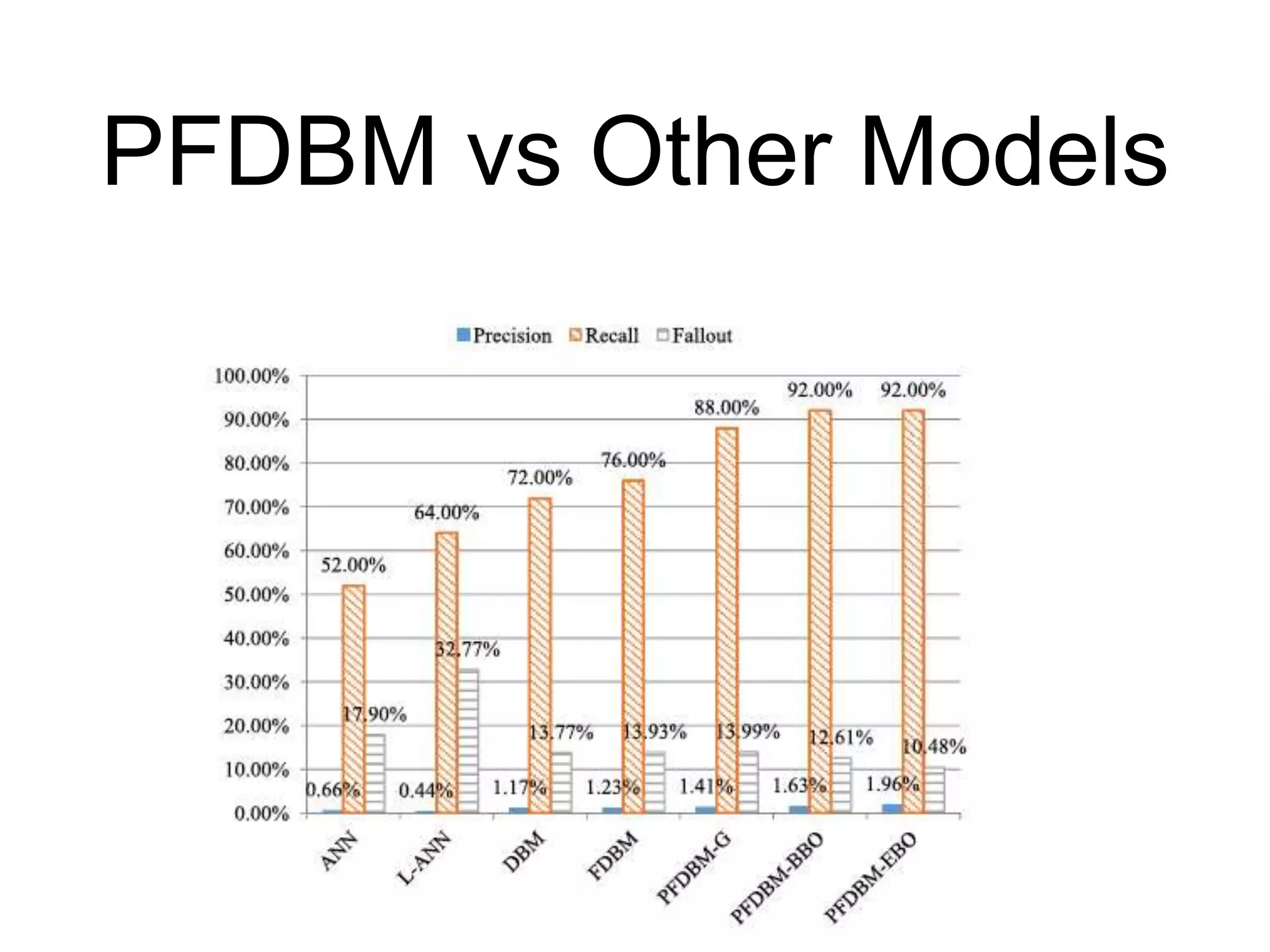
The document discusses airline passenger profiling using fuzzy deep machine learning, emphasizing its importance for aviation security, particularly after 9/11. It highlights the evolution of profiling systems from initial rule-based methods to advanced systems like CAPPS II and Secure Flight, while addressing the inefficiencies and challenges of current methods. The proposed solution involves a Pythagorean fuzzy deep Boltzmann machine (PFDBM) for improved classification accuracy of normal passengers versus potential attackers, integrating various data sources for training.






![Pythagorean fuzzy set
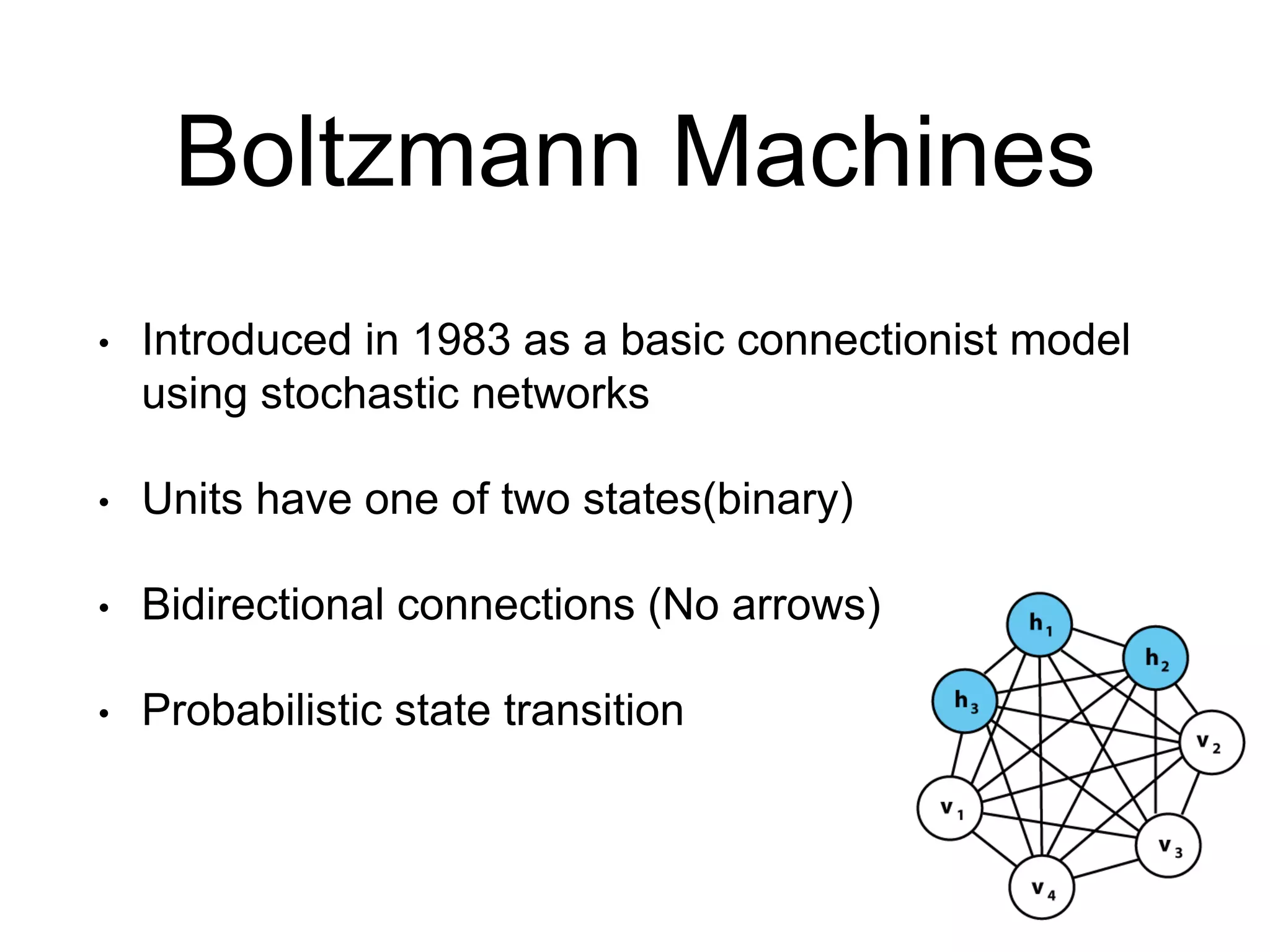
• Any two items are usually compared by a user as either a ‘match’ or a
‘mismatch’
• In fuzzy logic, the range between a perfect match & a perfect mismatch is
extended. For instance, [0,1] set can be subdivided into [0,0.25,0.5,0.75,1]
• Membership into an extended subset can be expressed in terms of a r(x),
strength of membership and d(x), direction of commitment. (Intuitionistic
Fuzzy Set)
• PFS which is more general than IFS in that the sum of squares of the
membership degree and the nonmembership degree is less than or equal to
1.
• Fuzzified neural networks can handle inputs with fuzzy (labeled) and/or
incomplete features, which are inevitable in passenger profilers](https://image.slidesharecdn.com/airlinepassengerprofilingbasedonfuzzydeepmachinelearning-170309200408/75/Airline-passenger-profiling-based-on-fuzzy-deep-machine-learning-9-2048.jpg)