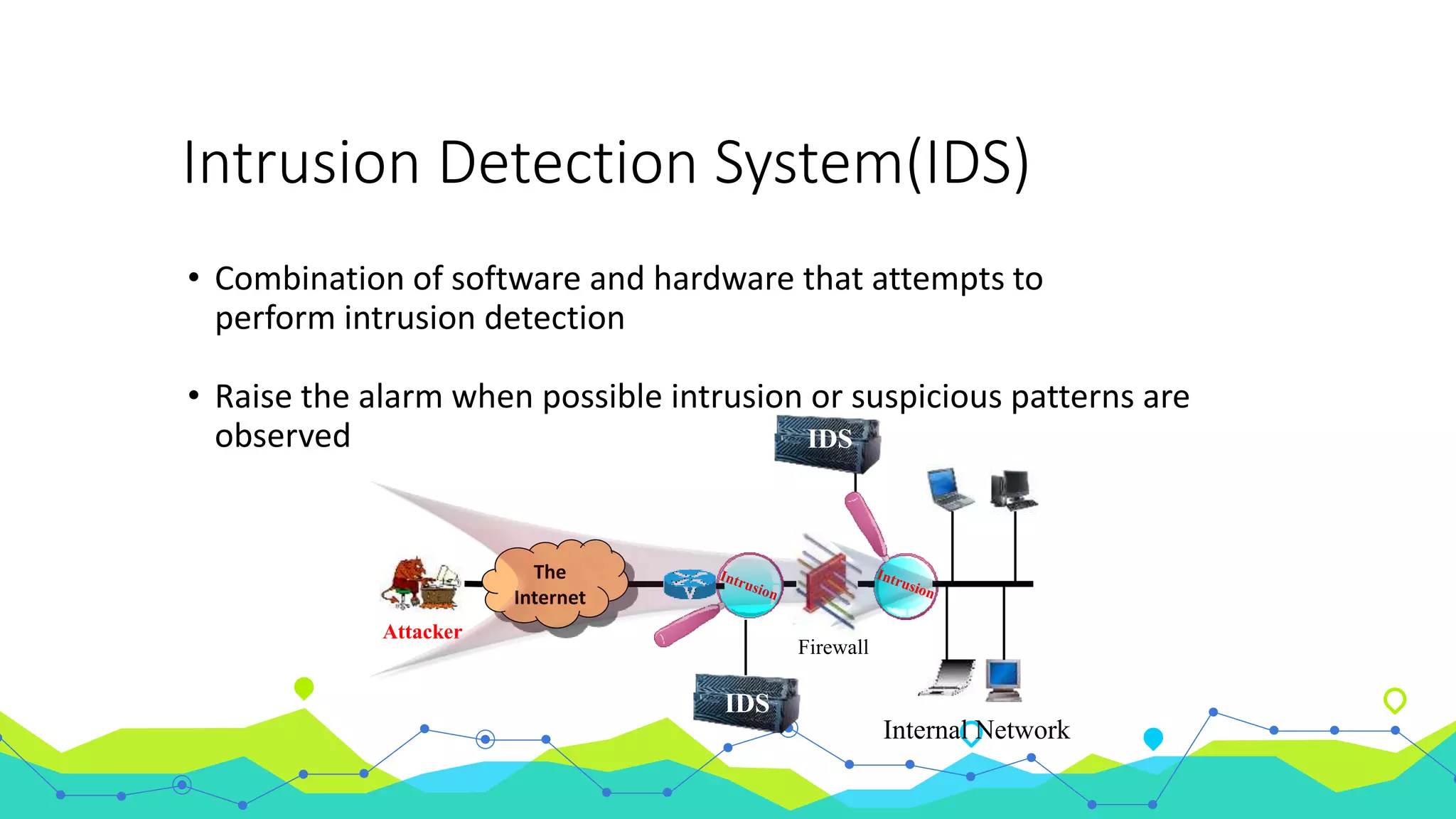
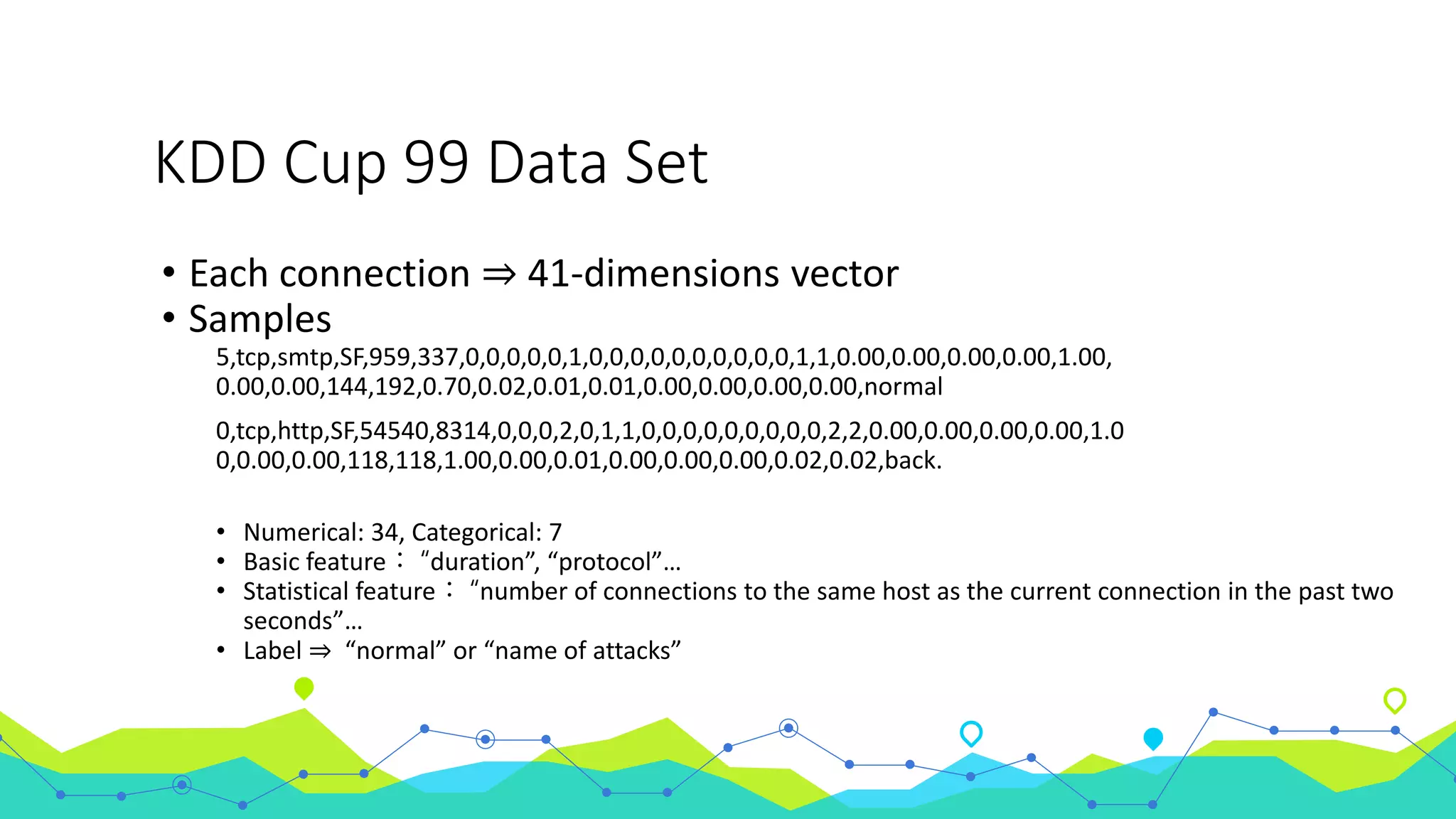
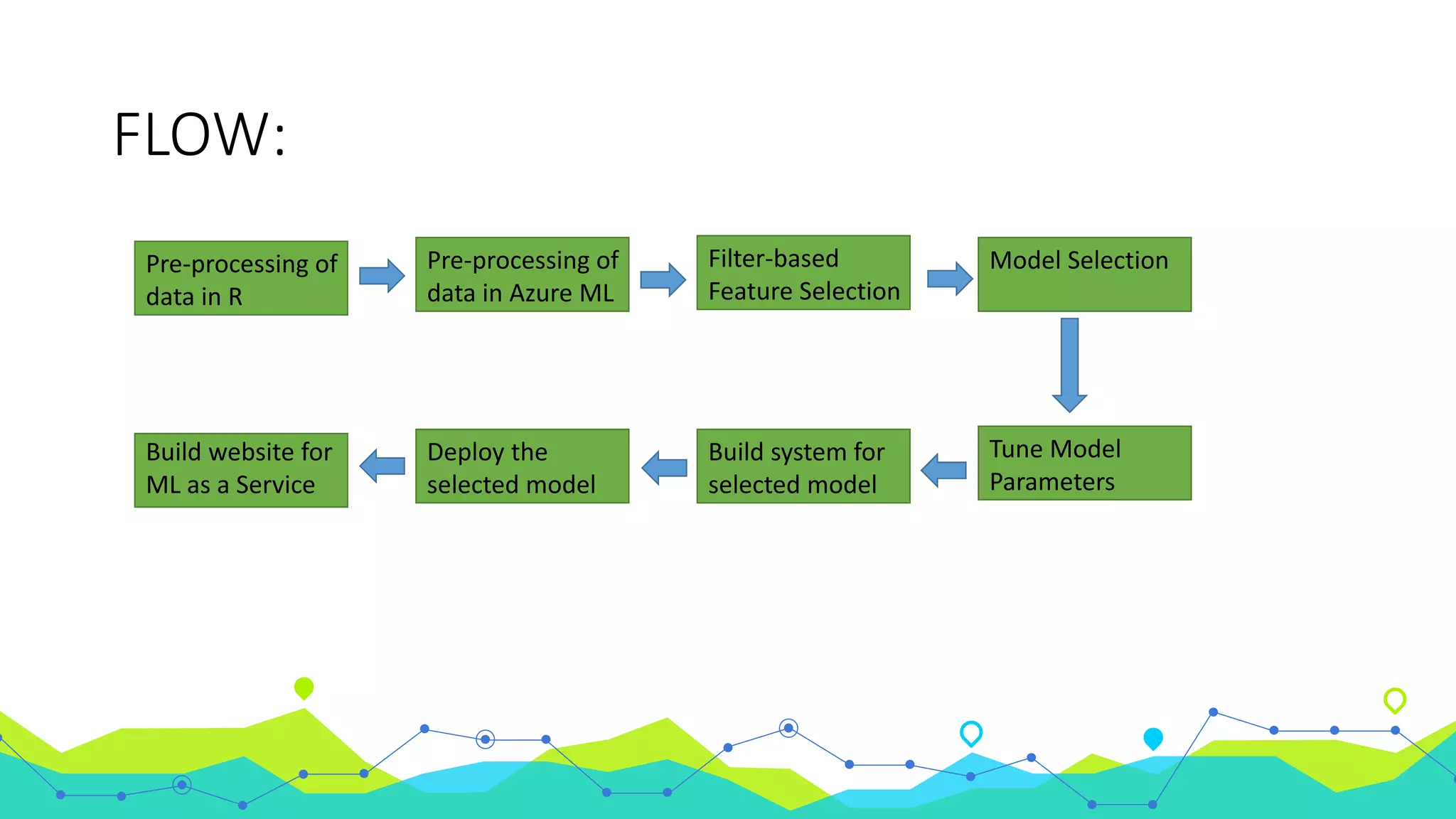
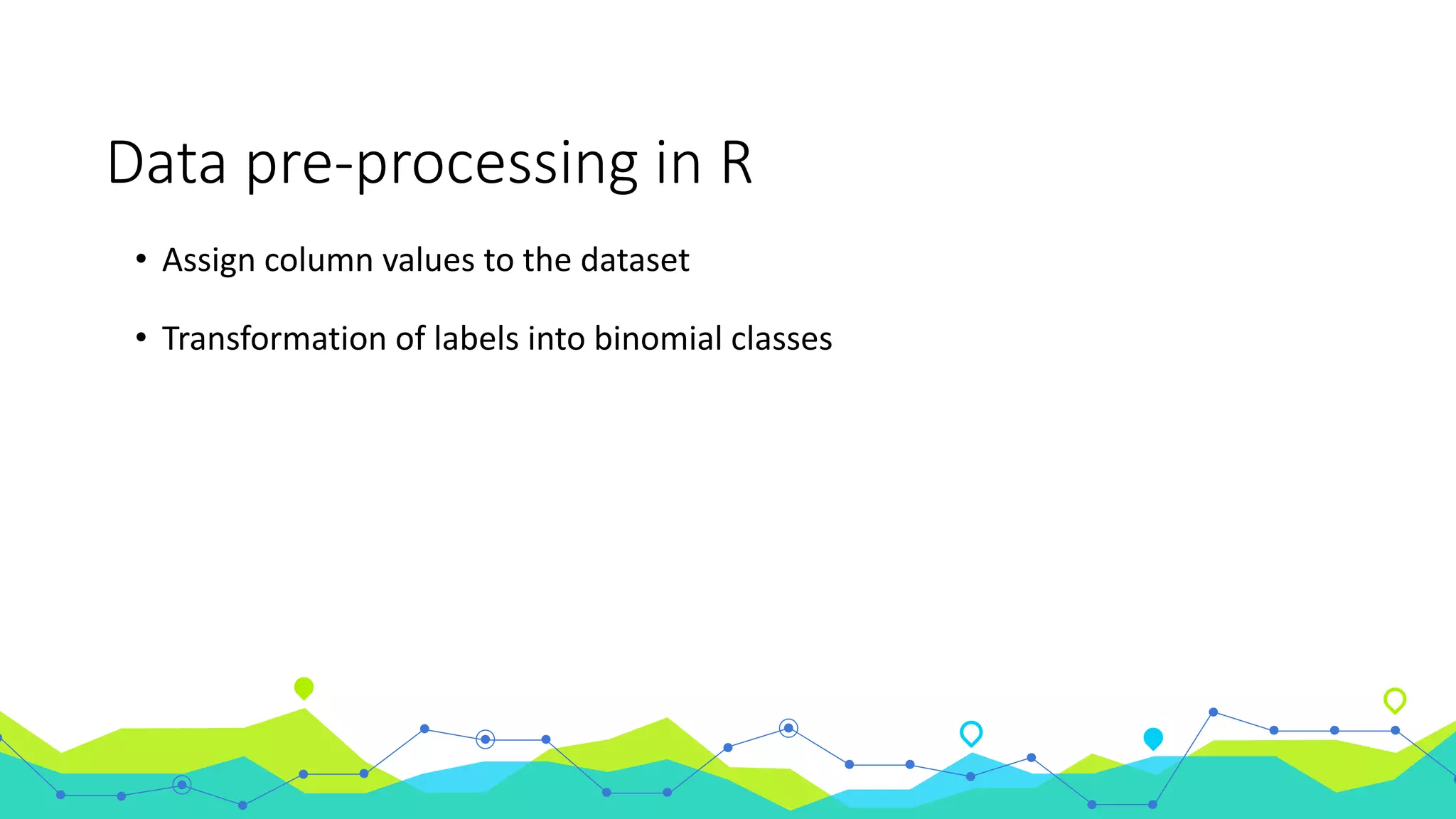
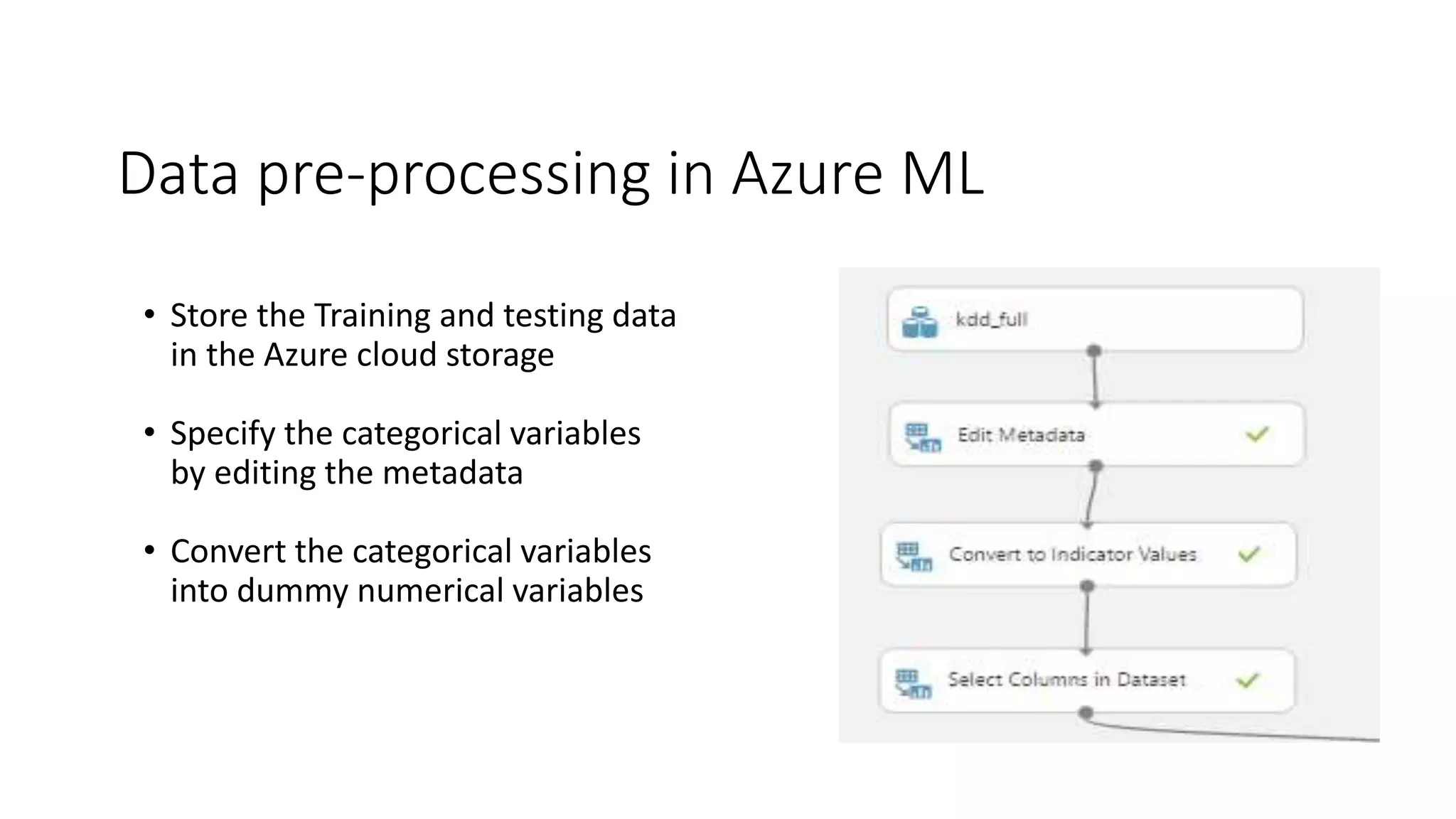
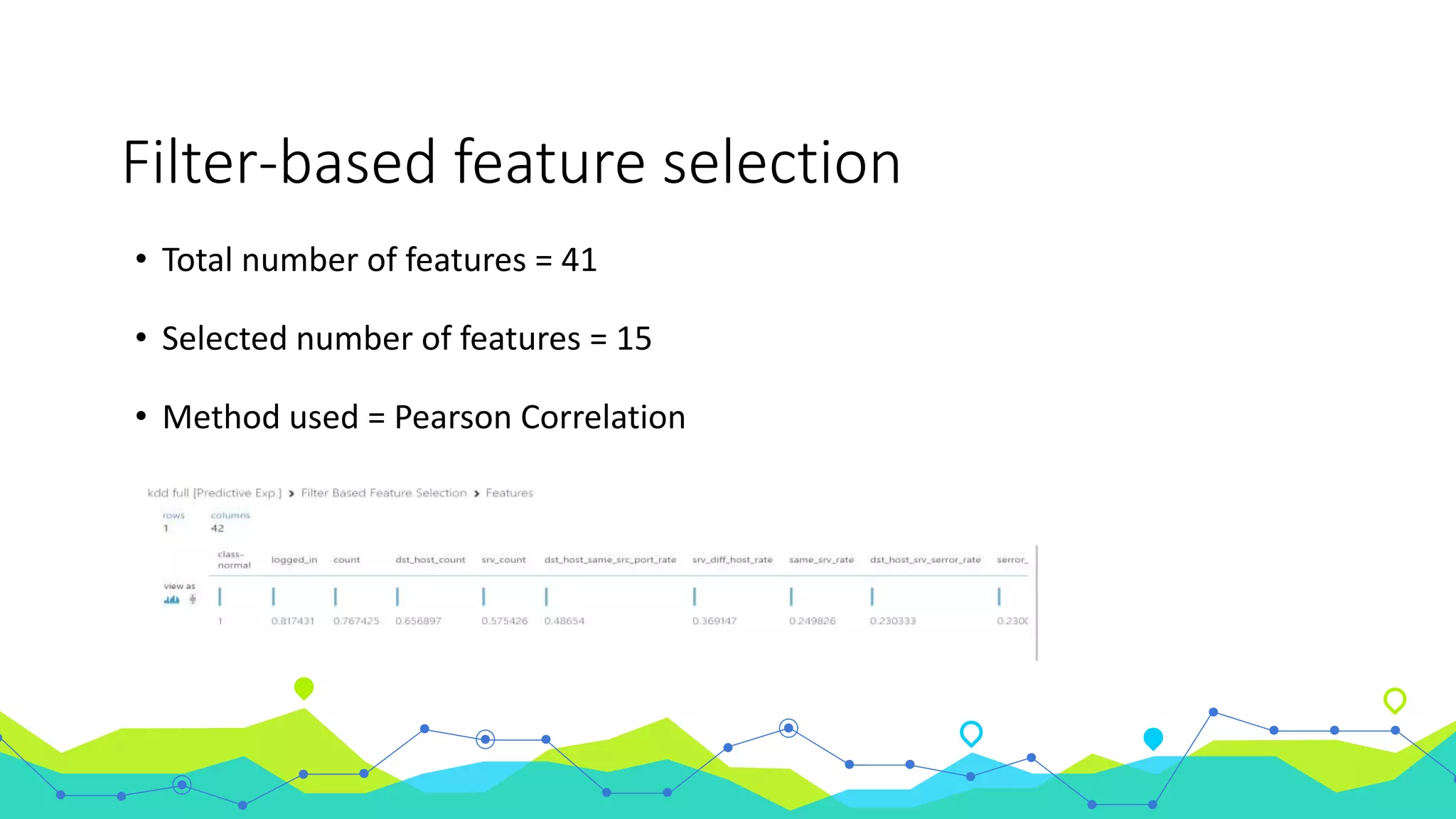
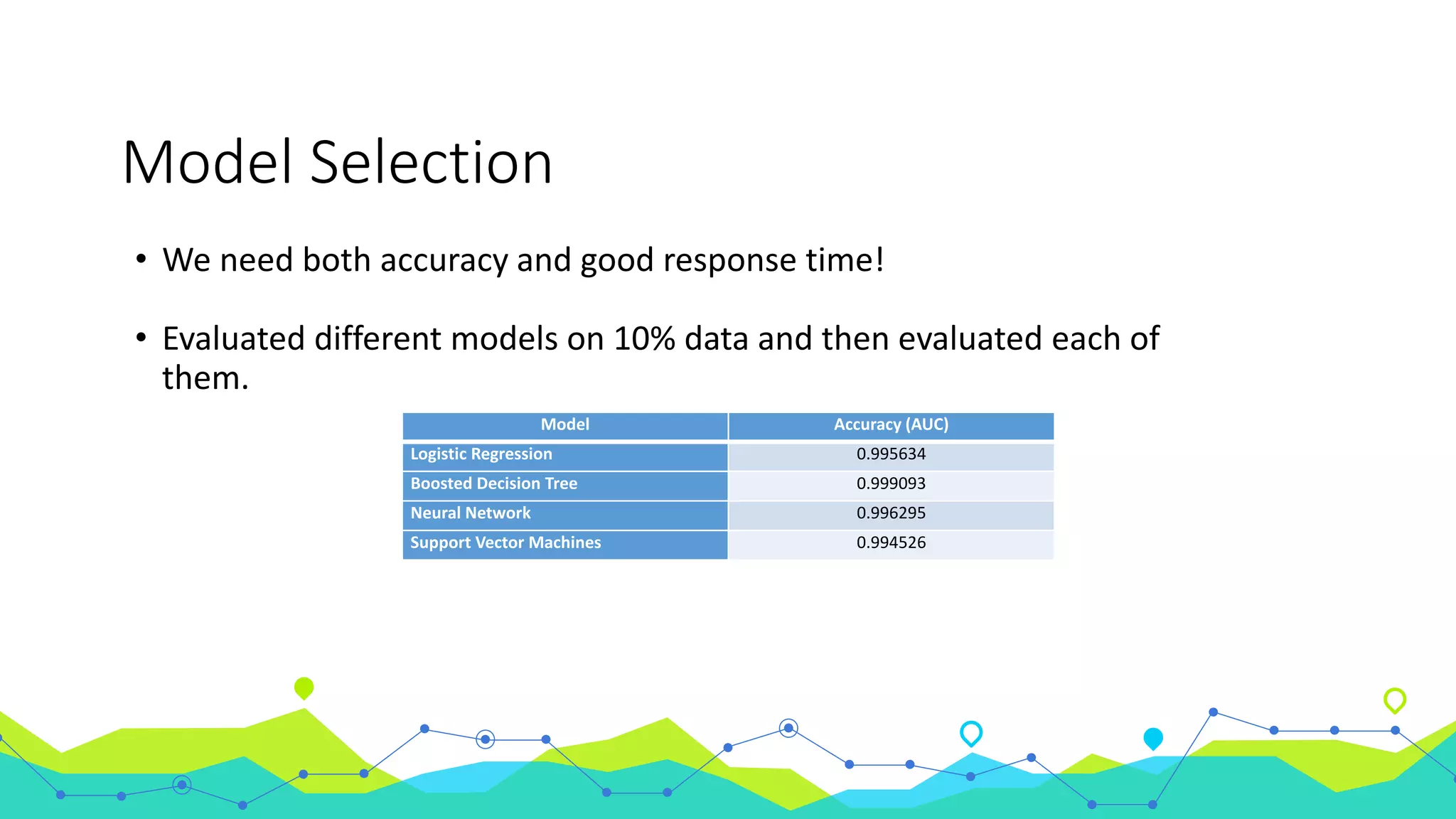
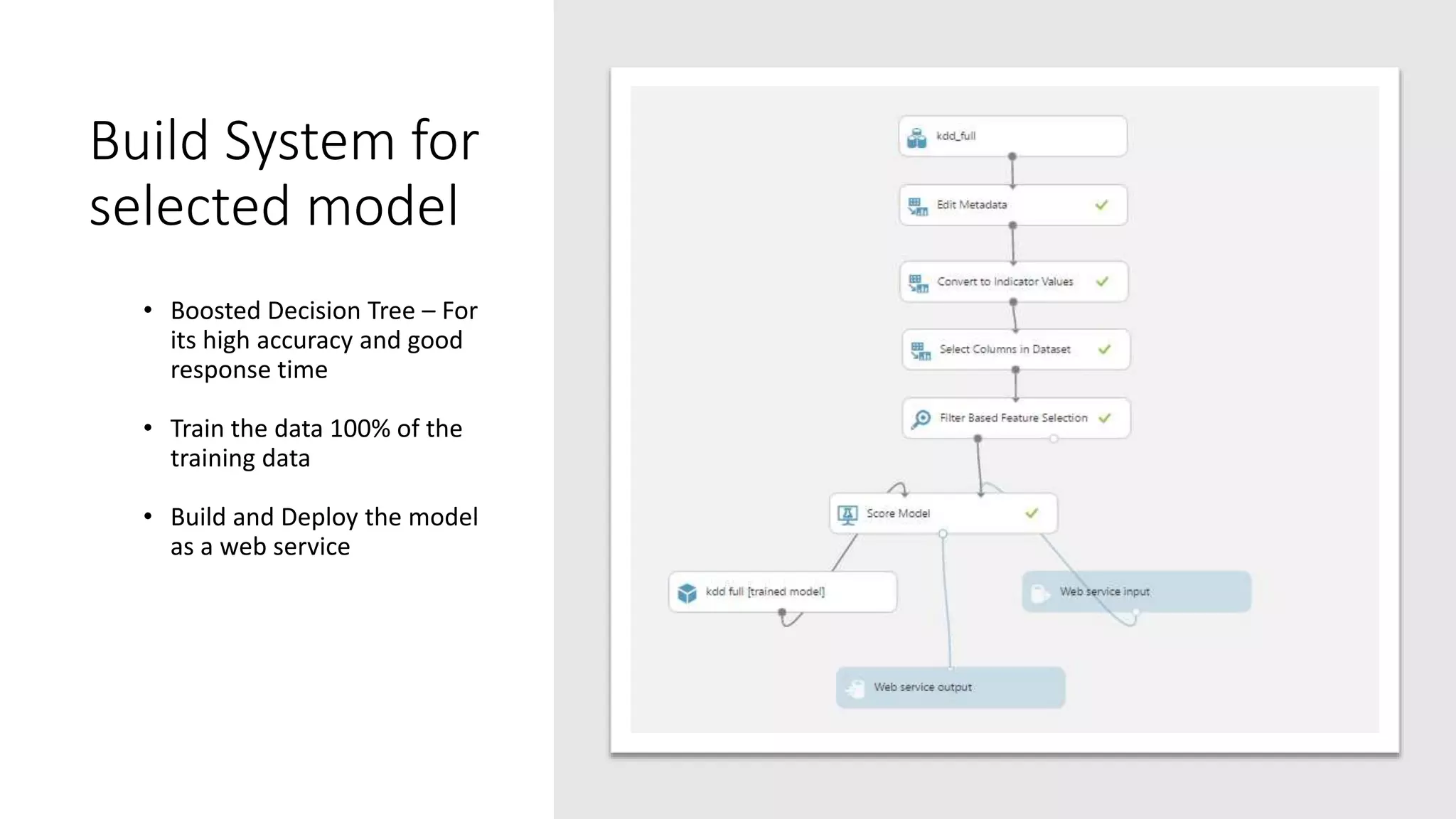
The document discusses the use of machine learning for intrusion detection systems (IDS), highlighting types of IDS, including host-based and anomaly-based systems. It outlines the KDD Cup 99 dataset, which includes various attack simulations and features for model creation and evaluation. The document describes the processes of data preprocessing in R and Azure ML, model selection, tuning, and deploying a boosted decision tree model as a machine learning service.