The document outlines the AES (Advanced Encryption Standard) encryption and decryption process, detailing parameters such as the number of columns, 32-bit words in the key, and rounds. It describes the sequence of transformations (addroundkey, subbytes, shiftrows, mixcolumns) used in AES, including key expansion for unique round keys. The process is illustrated through both encryption and decryption operations, emphasizing the importance of the key in both processes.









![Encryption
byte state[4,Nb]
state = in
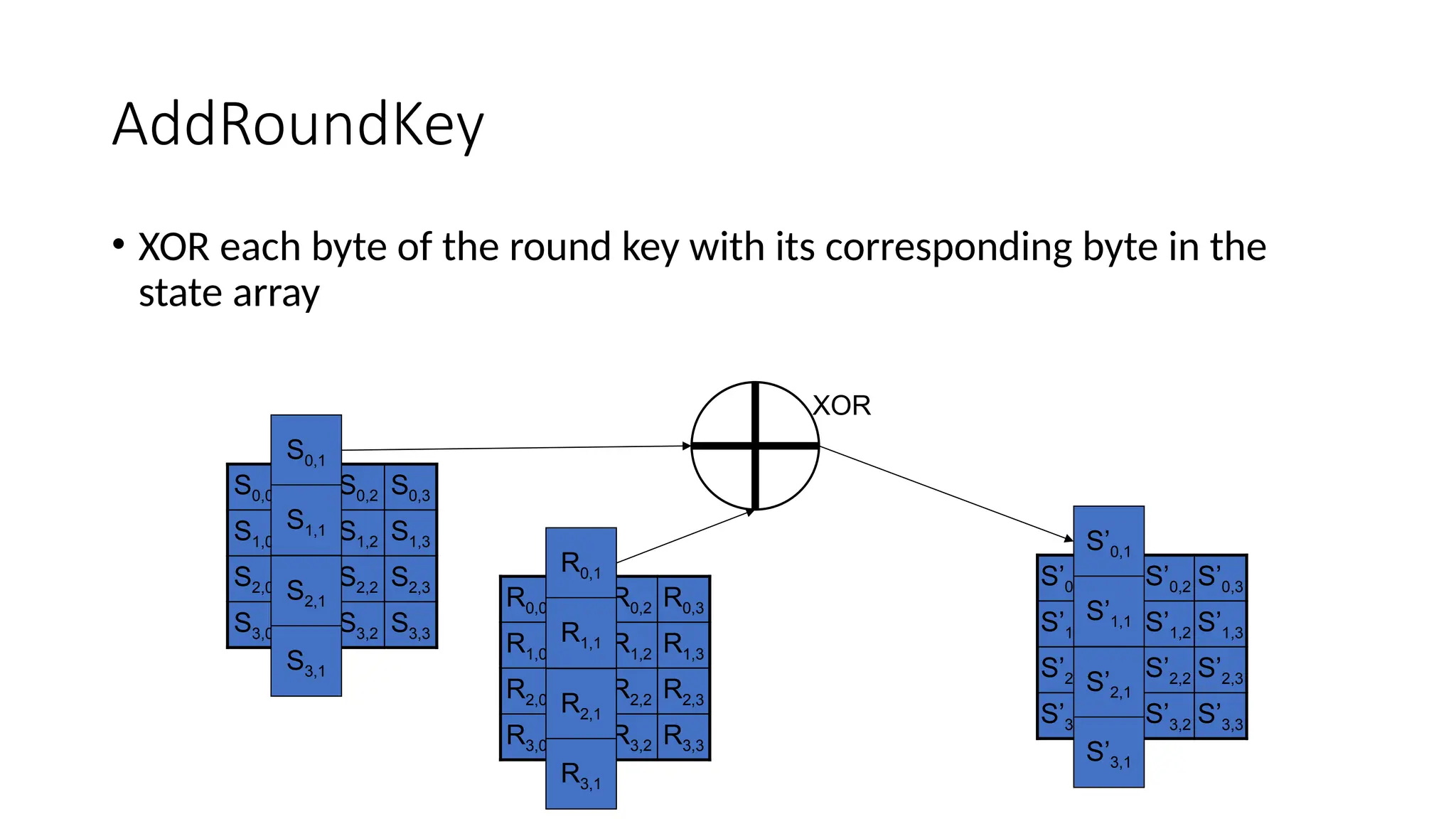
AddRoundKey(state, keySchedule[0, Nb-1])
for round = 1 step 1 to Nr–1 {
SubBytes(state)
ShiftRows(state)
MixColumns(state)
AddRoundKey(state, keySchedule[round*Nb, (round+1)*Nb-1])
}
SubBytes(state)
ShiftRows(state)
AddRoundKey(state, keySchedule[Nr*Nb, (Nr+1)*Nb-1])
out = state
First and last operations
involve the key
Prevents an attacker from
even beginning to encrypt or
decrypt without the key](https://image.slidesharecdn.com/aesencryptiondecryption-241212040500-e5c8efd6/75/AES-Encryption-Decryption-in-Crptography-pptx-11-2048.jpg)
![Decryption
byte state[4,Nb]
state = in
AddRoundKey(state, keySchedule[Nr*Nb, (Nr+1)*Nb-1])
for round = Nr-1 step -1 downto 1 {
InvShiftRows(state)
InvSubBytes(state)
AddRoundKey(state, keySchedule[round*Nb, (round+1)*Nb-1])
InvMixColumns(state)
}
InvShiftRows(state)
InvSubBytes(state)
AddRoundKey(state, keySchedule[0, Nb-1])
out = state](https://image.slidesharecdn.com/aesencryptiondecryption-241212040500-e5c8efd6/75/AES-Encryption-Decryption-in-Crptography-pptx-12-2048.jpg)
