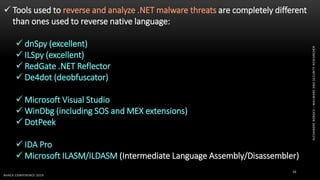
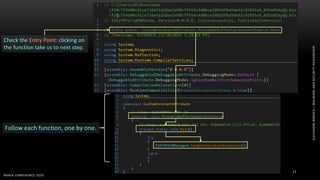
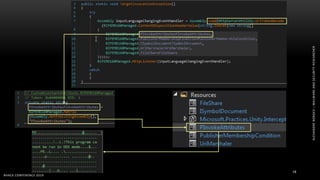
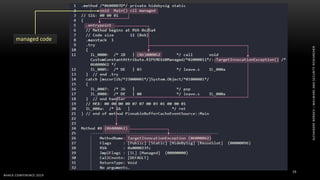
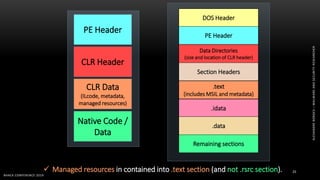
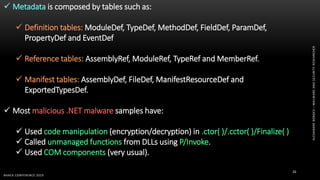
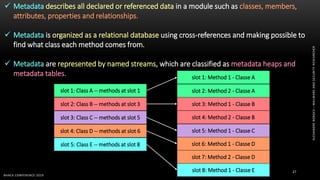
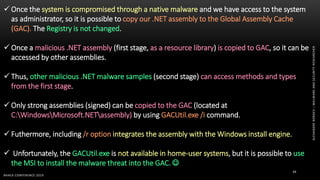
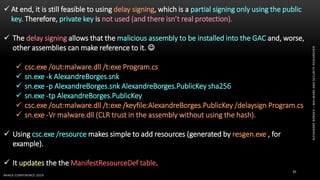
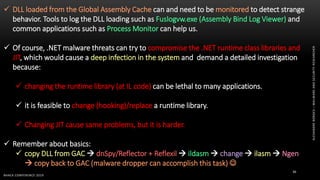
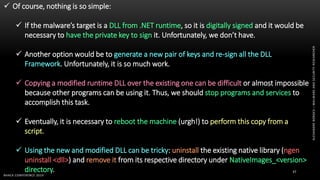
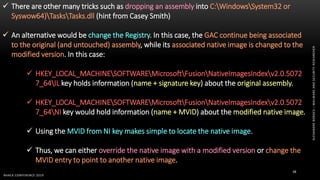
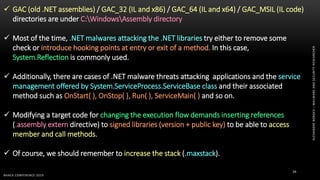
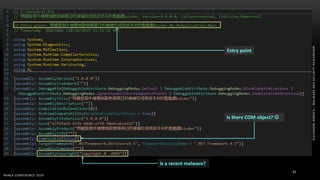
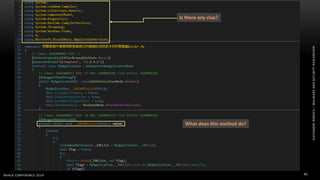
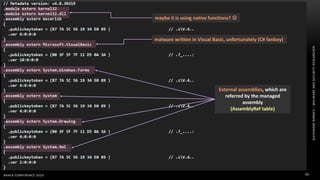
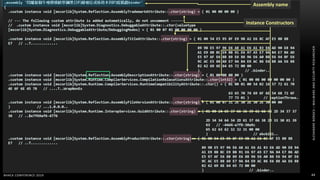
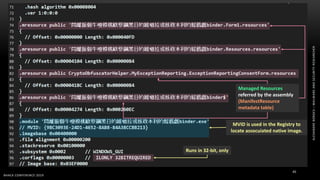
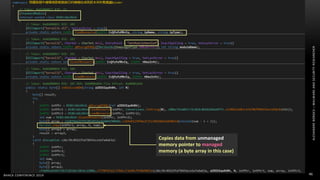
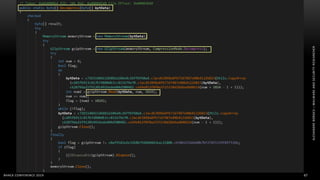
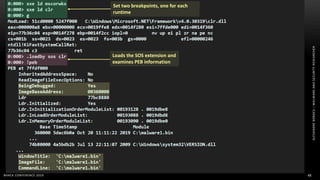
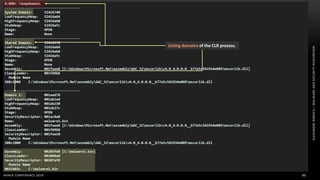
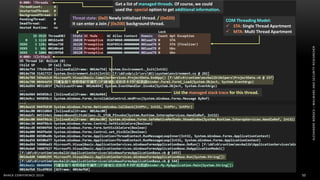
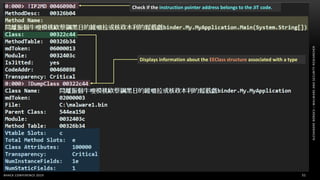
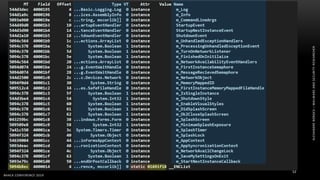
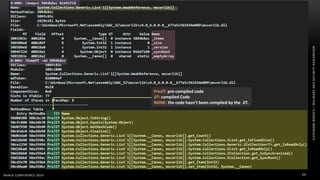
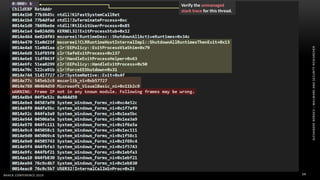
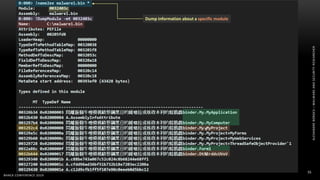
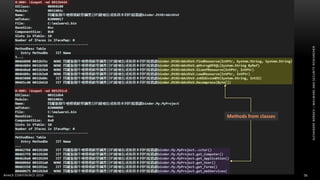
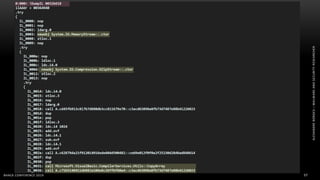
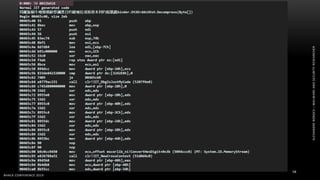
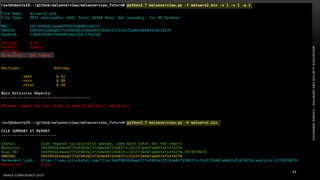
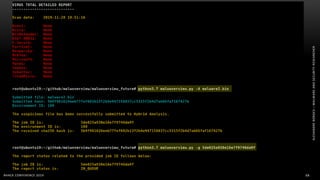
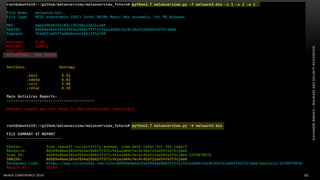
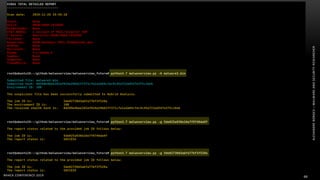
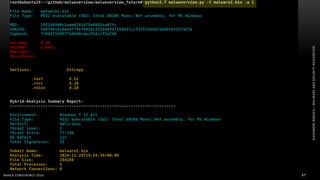
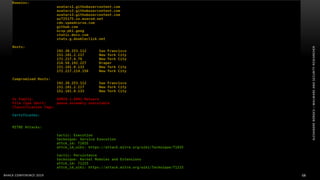
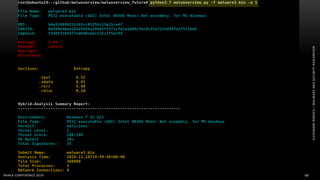
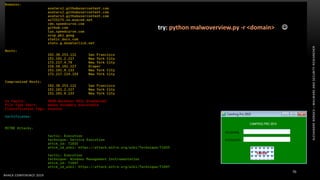
The document discusses .NET malware threats and analysis. It provides an agenda for the talk including an introduction to .NET details and analysis. It discusses common techniques used in .NET malware like decrypting encrypted content and loading external assemblies. The document lists tools that can be used to analyze .NET malware like dnSpy, ILSpy, and WinDbg. It also discusses following the entry point and calling chains in managed code to understand the malware's behavior.