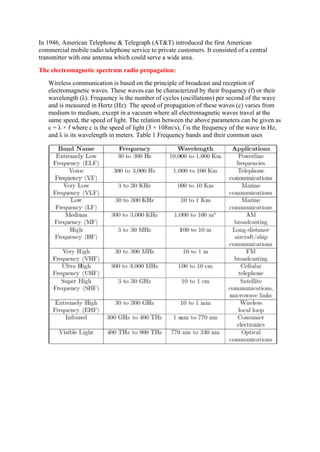
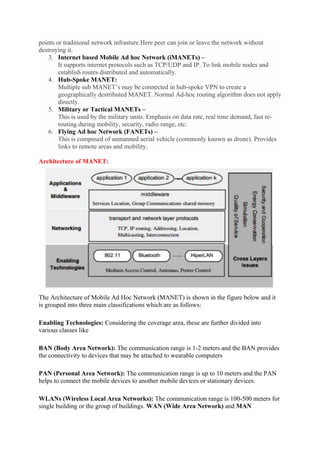
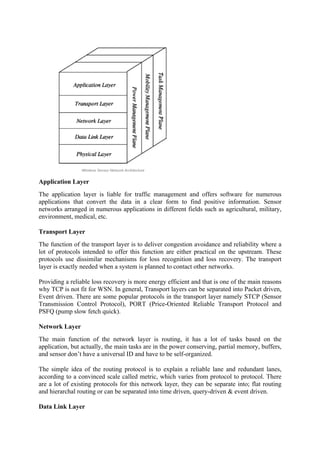
The document provides a comprehensive overview of wireless communication technology, including its fundamental principles, the electromagnetic spectrum, and various historical advancements such as radio and radar communications. It discusses mobile ad hoc networks (MANETs) and wireless sensor networks (WSNs), highlighting their architectures, applications, and the challenges they face. The text also explains key concepts related to wireless communication, such as radio propagation mechanisms, path loss, fading, and interference.