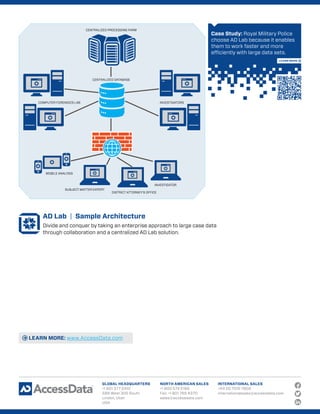
This document summarizes an AD Lab software platform that allows forensic analysts and investigators to collaborate on cases. Key features include:
- Examiners can work individually on cases while sharing a centralized database and storage.
- Role-based access controls allow administrators to assign users to specific cases or data.
- A web interface enables secure remote review without file conversions.
- Distributed processing allows large datasets to be analyzed across multiple machines.