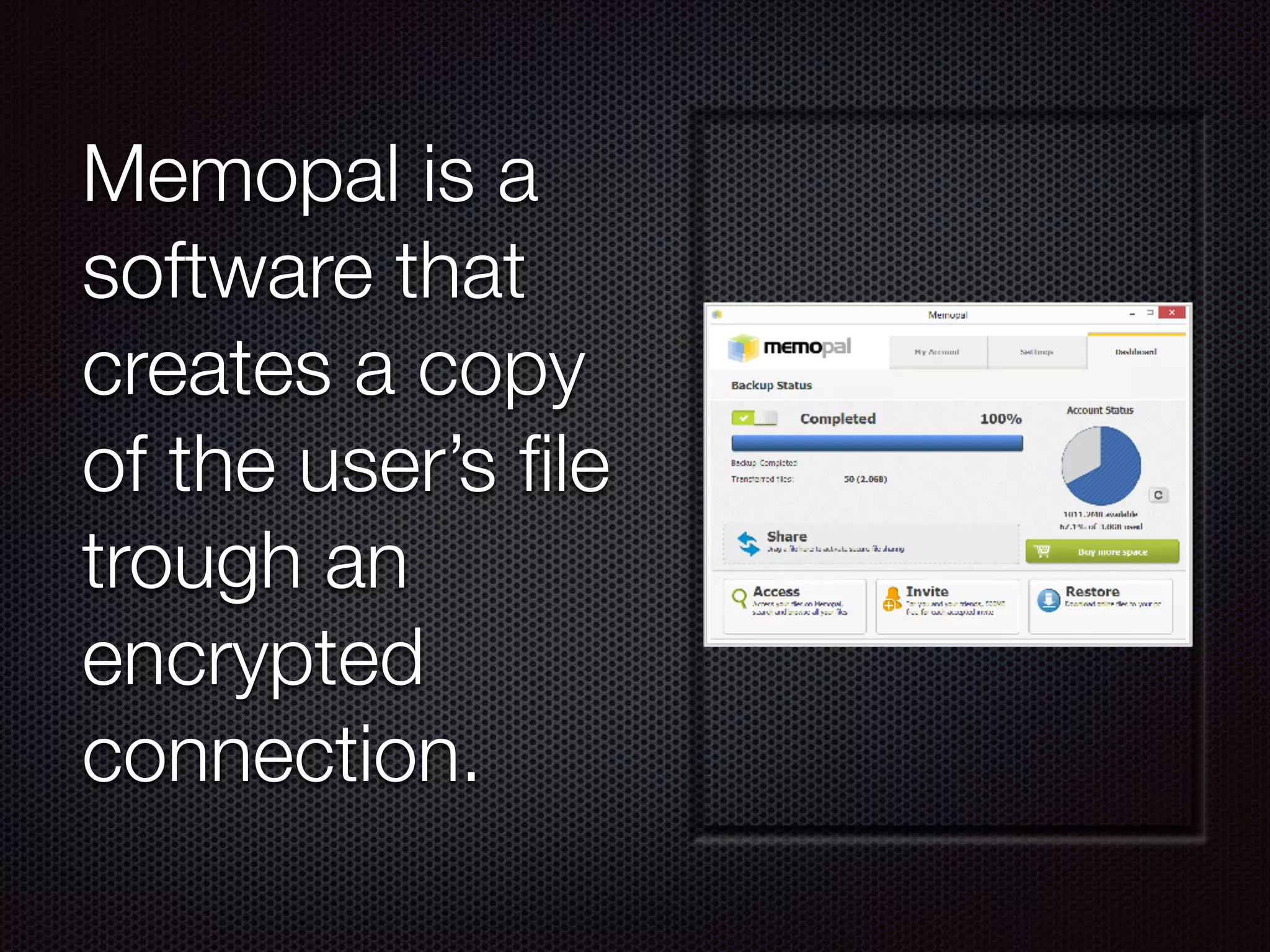
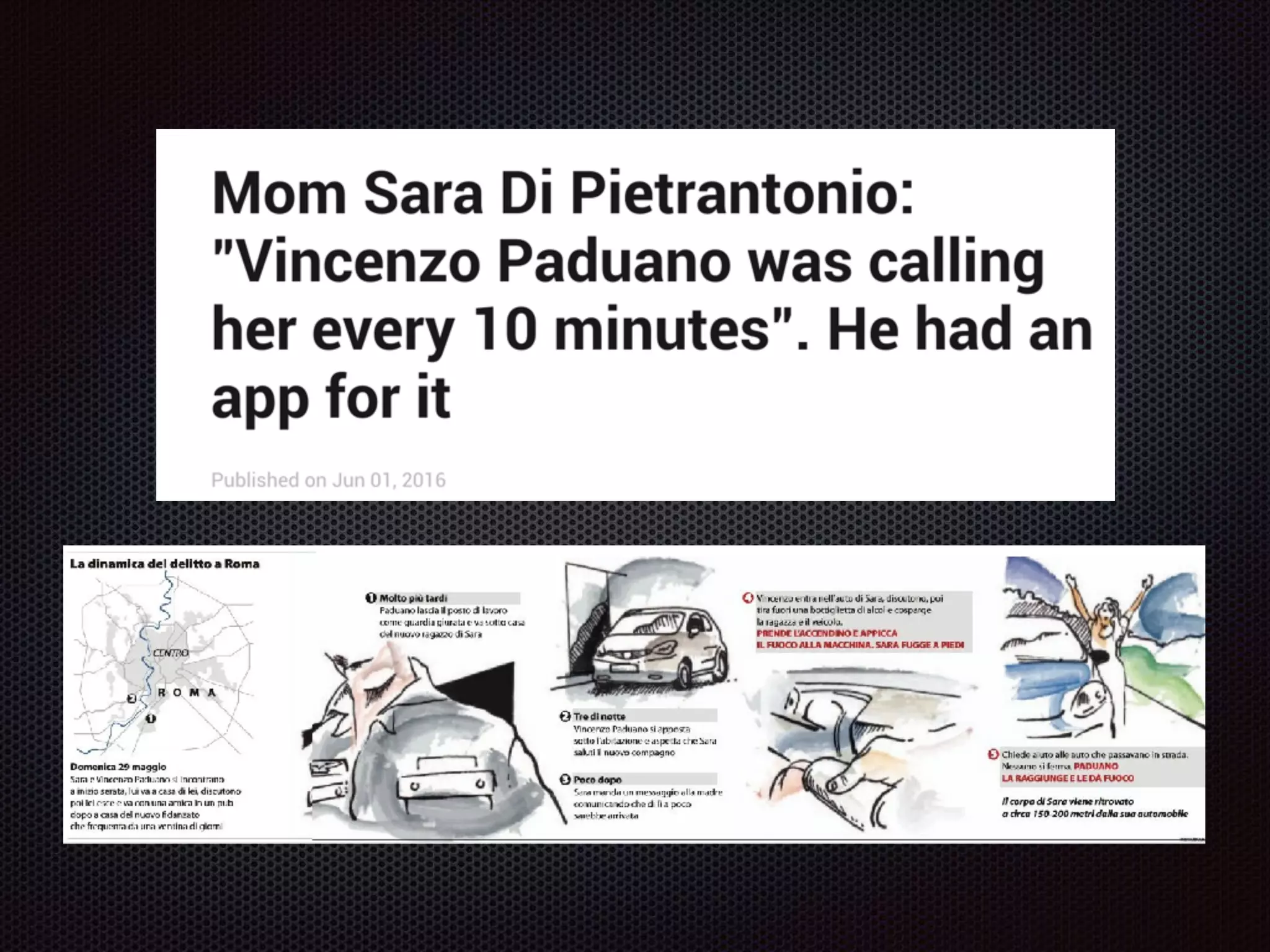
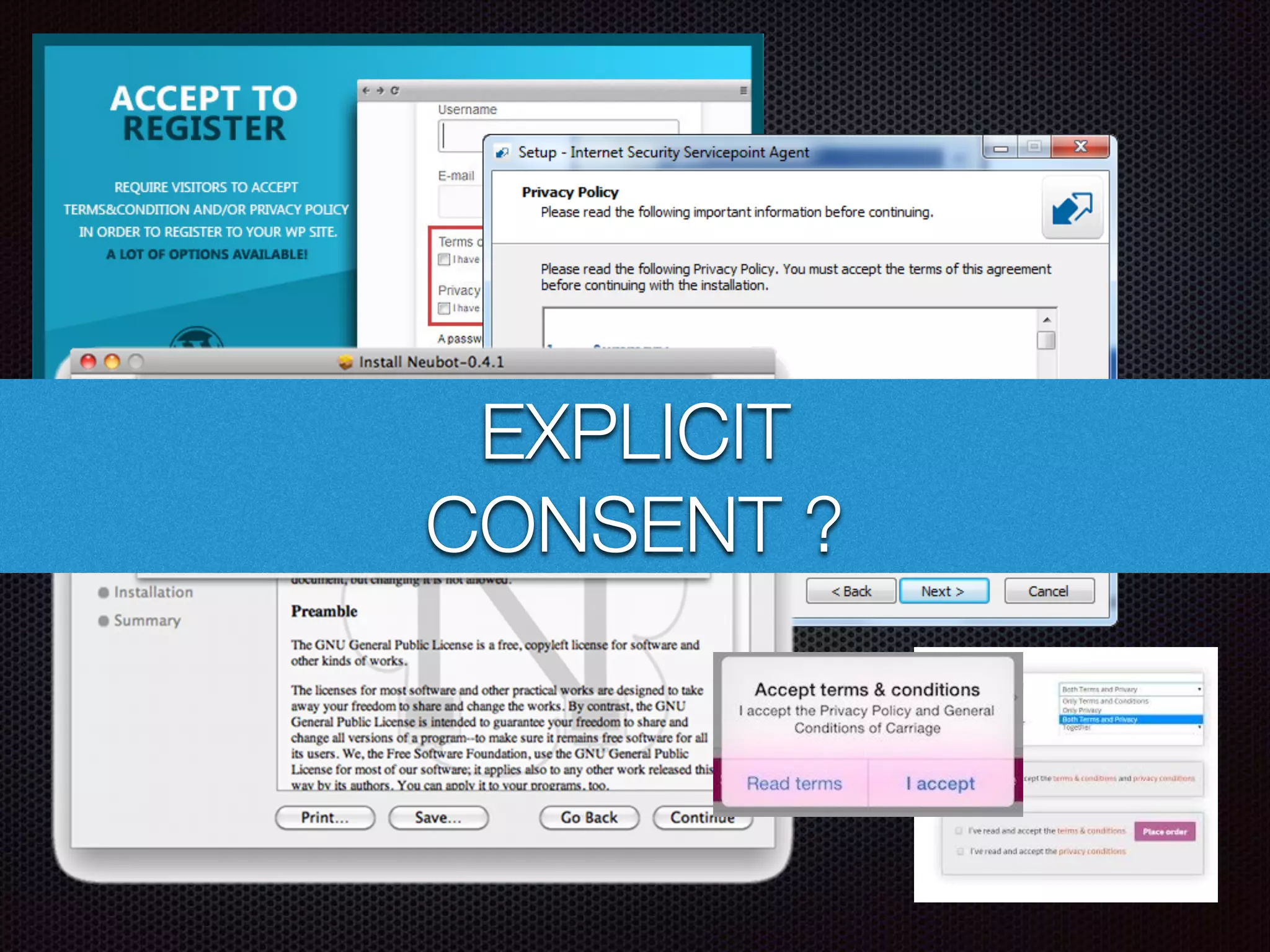
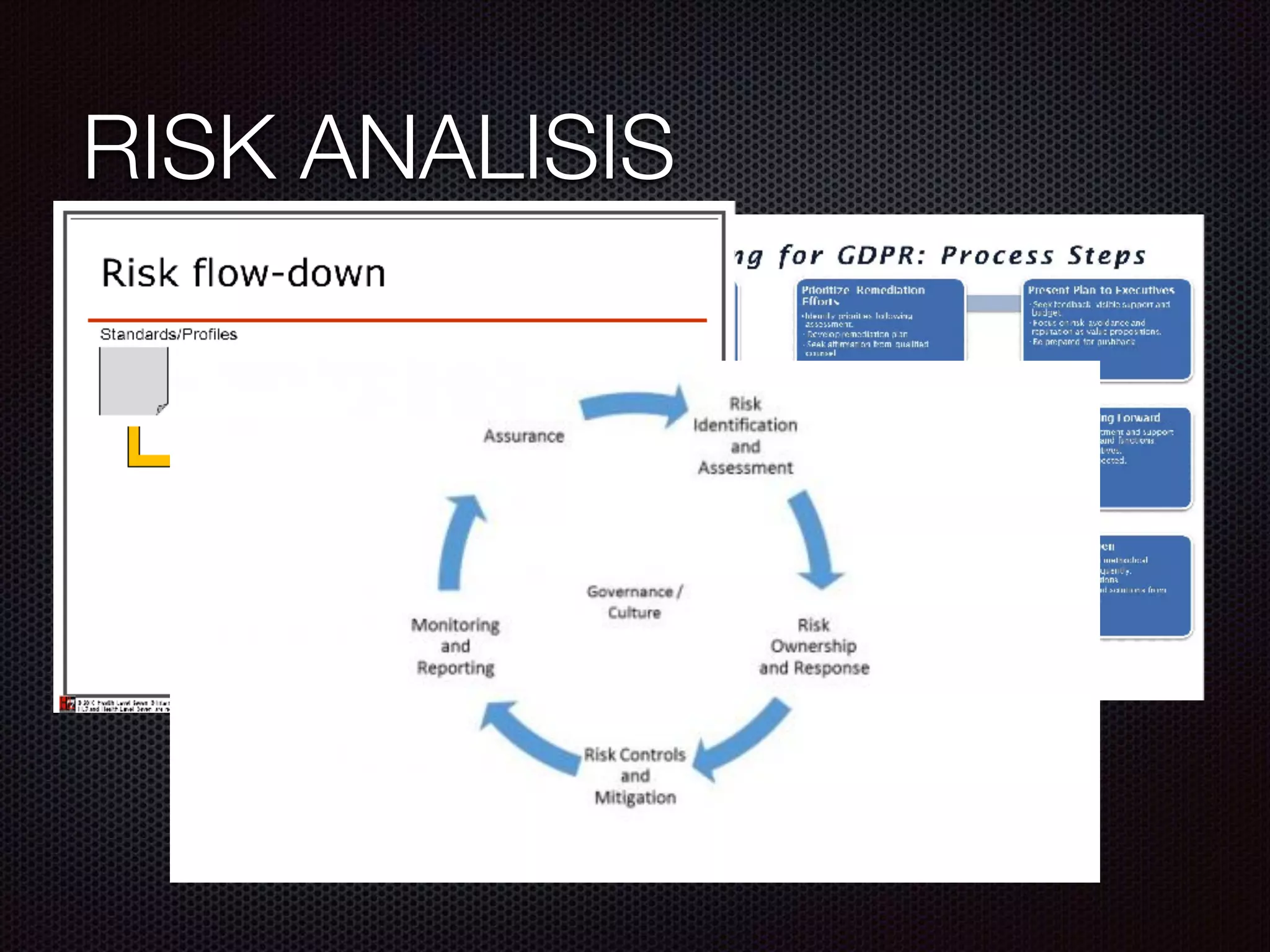
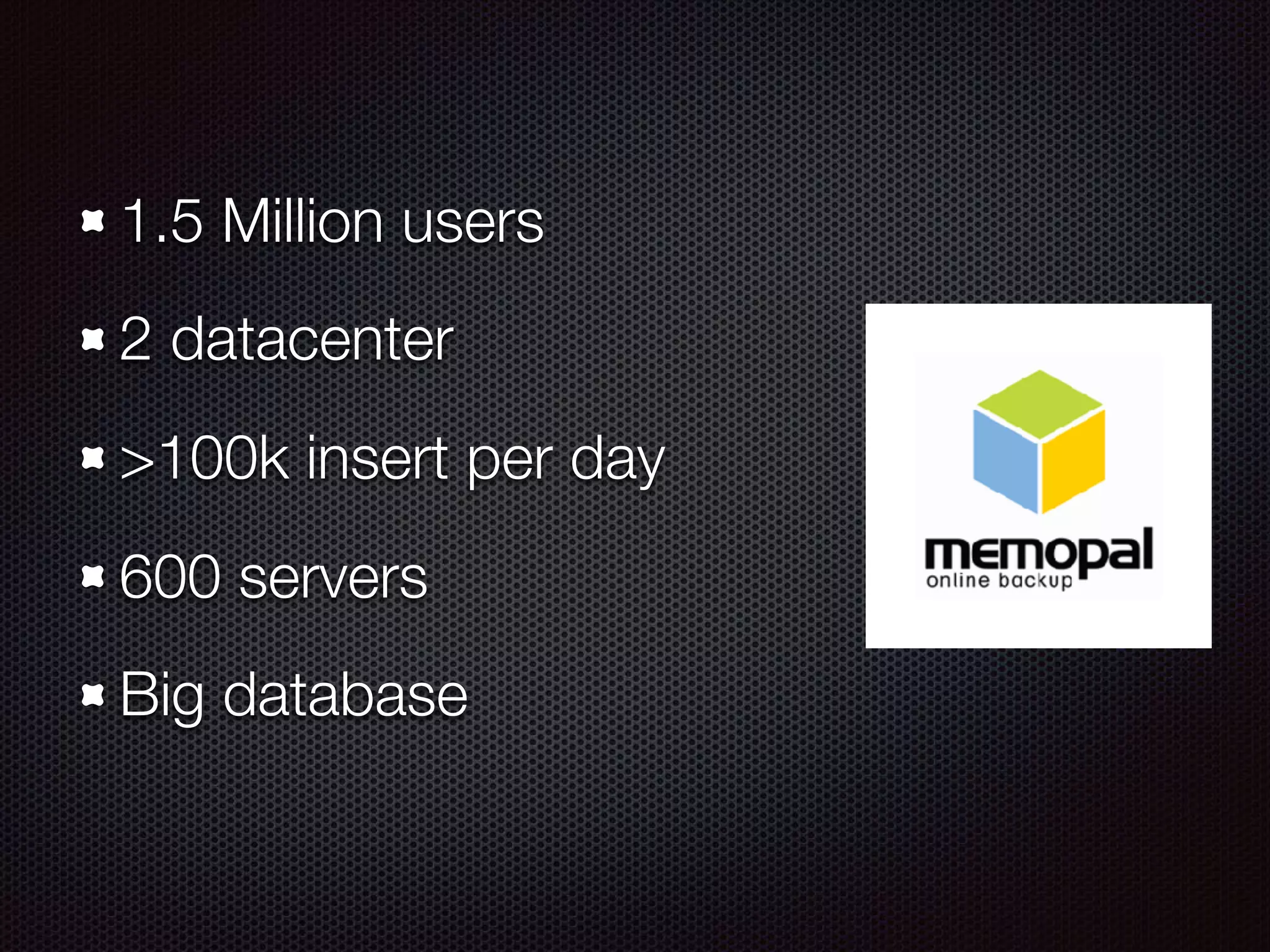
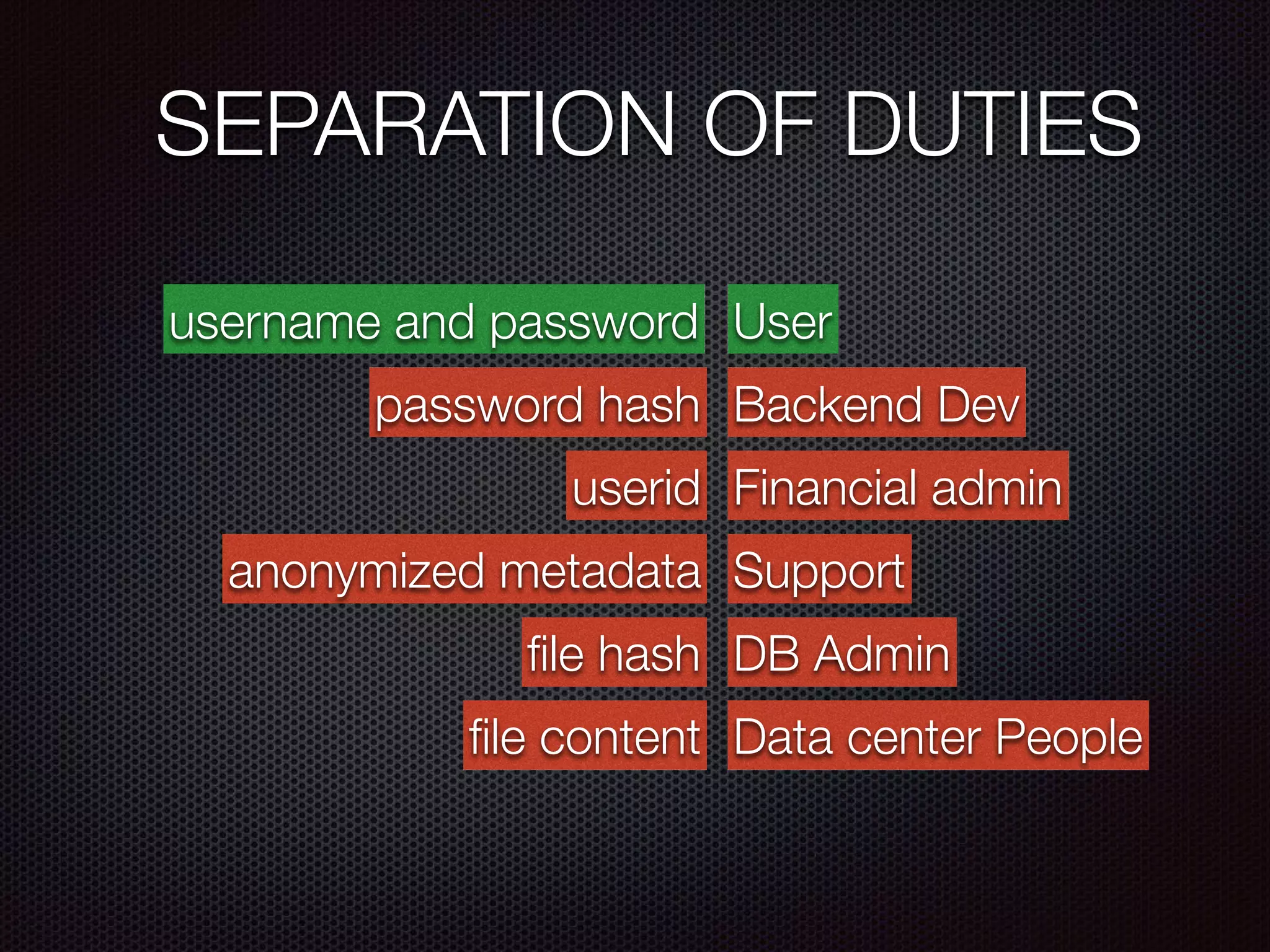
This document summarizes a presentation given by Evan Tedeschi on GDPR and data privacy. It provides an overview of Evan's background in physics, computing linguistics, and as the founder of Memopal, a cloud storage software company. The presentation discusses Memopal's operations and data centers, highlights of GDPR regulations around personal data protection, Memopal's architecture ensuring privacy and security of user data, and strategies for responding to data breaches. Key aspects of GDPR covered include explicit consent, right to be forgotten, pseudonymization vs encryption, and separation of duties.