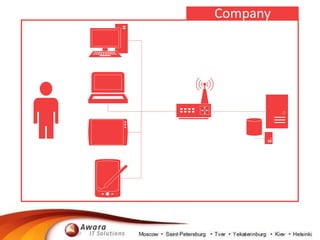
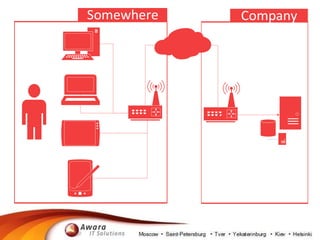
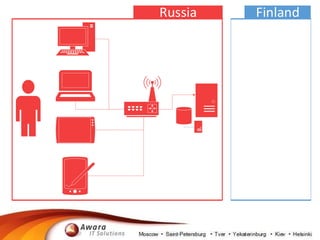
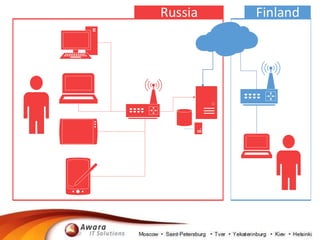
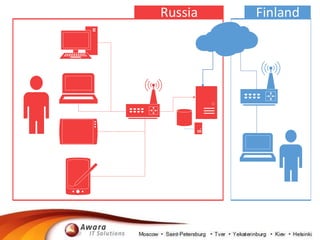
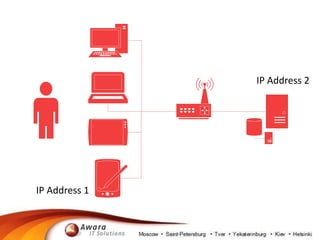
The document details the processing of personal data in Russia, highlighting the importance of identifying data types at risk due to recent legislation. It outlines necessary actions for companies, including analyzing IT infrastructure and ensuring compliance with data localization requirements. It also suggests practical steps for managing personal data, such as deleting or substituting data and understanding backup policies.