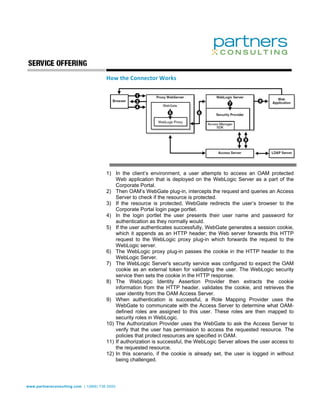
American Bureau of Shipping engaged Partners Consulting to deploy a single sign-on solution for its customer-facing applications. Partners implemented Oracle Access Manager for centralized authentication, authorizing users through WebLogic Security Provider Interface. They migrated user data to Oracle Internet Directory and configured Oracle Access Manager policies and WebGates to provide single sign-on for over 20 portal applications while integrating with the existing WebLogic security framework.