A priest’s phone location data outed his private life. It could happen to anyone.
•
0 likes•85 views
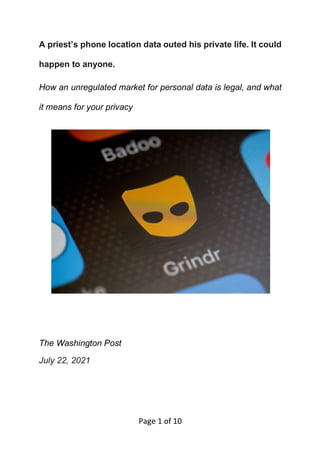
A Catholic priest's private location data from his smartphone was obtained by a Catholic newsletter and used to out aspects of his private life. This occurred because personal data, including from apps like Grindr, is collected by apps and data brokers and sold with little regulation of how it is used. Experts have long warned that insufficient protections allow supposedly anonymous personal data to be de-anonymized and used against individuals. There are some steps people can take to protect their data privacy, but it requires vigilance that most people cannot reasonably maintain. Stronger regulation may be needed to better safeguard individual privacy as personal data is increasingly commodified.
Report
Share
Report
Share
Download to read offline
Recommended
Big Data, Transparency & Social Media Networks

This document examines transparency issues in the data usage policies of large social media networks like Facebook, Twitter, and LinkedIn. It finds that while the policies appear clear, most users do not actually read or understand them. The networks also frequently change how they use and share data without updating policies. This became a major issue after Facebook conducted an emotion manipulation experiment on users without their consent. The document argues that social networks need to improve transparency by making policies more visible, explaining how data is used simply, and giving users more control over their personal information.
Facebook data breach

Facebook has been blamed for data breech of India users before presidential in 2016 in US. Cambridge Analytica had harvested on the stolen data to analyze the election based on user messages. Here solution on how Facebook can avoid such situations in future has been stated.
Smartphones are smarter than you thought geo bellas

Smartphones contain lots of data that can make or break a lawsuit. How do you recover the info from a Smartphone?
Who Has Your Back 2014: Protecting Your Data From Government Requests

• Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
The Impacts of PopVote in Hong Kong - Virgile Deville (Democracy Earth) 

This was presented by Virgile Deville from Democracy Earth at the Impacts of Civic Technology Conference (TICTeC@Taipei) in Taipei on 12th September 2017. You can find out more information about the conference here: http://civictechfest.org/agenda
Abstract:
Hong Kong’s 'small circle' election system means that only 1,200 people had a vote for the Chief Executive of the city, from a population of 3.77 million.
Prof. Benny Tai, leader of the Umbrella Movement, working with more than 20 civic communities in Hong Kong, led a campaign against this lack of inclusion, and commissioned the building of the PopVote application.
Seeing that the referendum provided an extraordinary opportunity for a large scale experiment, Democracy Earth were happy to collaborate to see how blockchain technologies such as Bitcoin or the IPFS network could best be leveraged to make the election process secure from cyber attacks.
Popvote aimed to collect a million citizens’ votes for the Chief Executive election, but it looked to future reuse, too. On a low budget, it was built as Open Source software that could also cater for future referendums. Crucially, based on previous experiences, it also had to be able to withstand cyber attacks.
Virgile shares the project’s outcomes, some encouraging; others disappointing. He also spells out how such collaborations are becoming more and more relevant to civil society, especially in a world of cyber attacks, data leaks and electoral fraud.
Considerations for the future of Online Dispute Resolution

The document discusses emerging technologies and their impact including:
- Growth of smartphones like the iPhone and increased mobile internet usage
- Facebook facing a privacy complaint in Canada over how it discloses personal information to third parties
- Changing definitions of privacy, disclosure and trust models in light of new technologies and services
Your privacy online: Health information at serious risk of abuse, researchers...

Libert points out that the Federal Health Insurance Portability and Accountability Act (HIPPA) is no...
Project_Paper_ISSC455_Intindolo

The document discusses computer forensics and its importance in criminal investigations. Computer forensics plays a vital role due to the prevalence of digital evidence even in typical criminal cases. The summary provides an overview of computer forensics, including its definition, benefits, the role of computer forensic investigators, common cybercrimes, and the forensic investigation process.
Recommended
Big Data, Transparency & Social Media Networks

This document examines transparency issues in the data usage policies of large social media networks like Facebook, Twitter, and LinkedIn. It finds that while the policies appear clear, most users do not actually read or understand them. The networks also frequently change how they use and share data without updating policies. This became a major issue after Facebook conducted an emotion manipulation experiment on users without their consent. The document argues that social networks need to improve transparency by making policies more visible, explaining how data is used simply, and giving users more control over their personal information.
Facebook data breach

Facebook has been blamed for data breech of India users before presidential in 2016 in US. Cambridge Analytica had harvested on the stolen data to analyze the election based on user messages. Here solution on how Facebook can avoid such situations in future has been stated.
Smartphones are smarter than you thought geo bellas

Smartphones contain lots of data that can make or break a lawsuit. How do you recover the info from a Smartphone?
Who Has Your Back 2014: Protecting Your Data From Government Requests

• Company names mentioned herein are the property of, and may be trademarks of, their respective owners and are for educational purposes only.
The Impacts of PopVote in Hong Kong - Virgile Deville (Democracy Earth) 

This was presented by Virgile Deville from Democracy Earth at the Impacts of Civic Technology Conference (TICTeC@Taipei) in Taipei on 12th September 2017. You can find out more information about the conference here: http://civictechfest.org/agenda
Abstract:
Hong Kong’s 'small circle' election system means that only 1,200 people had a vote for the Chief Executive of the city, from a population of 3.77 million.
Prof. Benny Tai, leader of the Umbrella Movement, working with more than 20 civic communities in Hong Kong, led a campaign against this lack of inclusion, and commissioned the building of the PopVote application.
Seeing that the referendum provided an extraordinary opportunity for a large scale experiment, Democracy Earth were happy to collaborate to see how blockchain technologies such as Bitcoin or the IPFS network could best be leveraged to make the election process secure from cyber attacks.
Popvote aimed to collect a million citizens’ votes for the Chief Executive election, but it looked to future reuse, too. On a low budget, it was built as Open Source software that could also cater for future referendums. Crucially, based on previous experiences, it also had to be able to withstand cyber attacks.
Virgile shares the project’s outcomes, some encouraging; others disappointing. He also spells out how such collaborations are becoming more and more relevant to civil society, especially in a world of cyber attacks, data leaks and electoral fraud.
Considerations for the future of Online Dispute Resolution

The document discusses emerging technologies and their impact including:
- Growth of smartphones like the iPhone and increased mobile internet usage
- Facebook facing a privacy complaint in Canada over how it discloses personal information to third parties
- Changing definitions of privacy, disclosure and trust models in light of new technologies and services
Your privacy online: Health information at serious risk of abuse, researchers...

Libert points out that the Federal Health Insurance Portability and Accountability Act (HIPPA) is no...
Project_Paper_ISSC455_Intindolo

The document discusses computer forensics and its importance in criminal investigations. Computer forensics plays a vital role due to the prevalence of digital evidence even in typical criminal cases. The summary provides an overview of computer forensics, including its definition, benefits, the role of computer forensic investigators, common cybercrimes, and the forensic investigation process.
GRBN Trust and Personal Data Survey - Market Research Industry Special Report

A special report focusing on how trusted the market research industry is across the globe to protect and appropriately use personal data
US mining data from 9 leading internet firms and companies deny knowledge

The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track one target or trace a whole network of associates, according to a top-secret document obtained by The Washington Post.
The program, code-named PRISM, has not been made public until now. It may be the first of its kind. The NSA prides itself on stealing secrets and breaking codes, and it is accustomed to corporate partnerships that help it divert data traffic or sidestep barriers. But there has never been a Google or Facebook before, and it is unlikely that there are richer troves of valuable intelligence than the ones in Silicon Valley.
Obama administration reverses on HealthCare.gov privacy policy after concerns

Bowing to an outcry over online privacy, the Obama administration reversed itself Friday, scaling ba...
Obama administration reverses on HealthCare.gov privacy policy after concerns

The Obama administration reversed its HealthCare.gov privacy policy after concerns were raised that the website was sending consumers' personal information like age, income, and health conditions to third-party advertising and analytics companies without consent. The administration made changes to reduce this sharing of data, though privacy advocates said more should be done since these third parties can still track users' behavior across websites and build profiles about their health interests. Officials had initially defended the practices but made the changes after lawmakers demanded an explanation.
CCPA: What You Need to Know

The document summarizes key aspects of California's new data privacy law, the California Consumer Privacy Act (CCPA). It outlines consumer rights like the right to access, delete, and opt-out of the sale of their data. It also discusses which businesses are impacted, obligations of covered businesses, potential penalties for noncompliance up to $7,500 per violation, and exemptions. There is uncertainty around how the law may be amended or preempted by future federal privacy legislation sought by big tech companies seeking to weaken its protections and reduce penalties.
Sbs facebook data privacy dilemma case study

Dear students get fully solved assignments
Send your semester & Specialization name to our mail id :
help.mbaassignments@gmail.com
or
call us at : 08263069601
Pli government investigations 2020

This document announces a government investigations program that will explore data breach investigations from the perspective of investigating agencies and corporations responding to such investigations. It will consider the scope of investigations arising from data breaches and privacy concerns, how corporations should respond by locating and producing electronic information. It will also discuss potential parallel civil proceedings and how information shared with investigating agencies may be used in litigation. The program aims to help corporations understand investigation obligations and protect privileged information.
Open Source Insight: Drupageddon, Heartbleed Problems & Open Source 360 Surve...

Open Source Insight: Drupageddon, Heartbleed Problems & Open Source 360 Surve...Black Duck by Synopsys
Open source insight this week on CVE-2014-3704, aka “Drupageddon” and CVE-2014-0160, the everlasting Heartbleed, plus results of our Open Source 360 Survey.Bericht icomp vol4

This document summarizes the results of an eye tracking study commissioned by ICOMP to analyze attention and selection behavior on Google search result pages. The study found that:
1) Google's own product search results and map/image panes received the majority of visual attention from users and were clicked on most frequently.
2) Alternative search sites logos received little visual attention and few clicks.
3) Organic links received less visual attention than Google elements above them and were often not noticed due to their positioning lower on the page.
4) Google ads received very little visual attention or clicks across all search result pages tested.
Exposing the Hidden Web

The purpose of this article is to provide a quantitative analysis of privacy-compromising mechanisms on the top 1 million websites as determined by Alexa. It is demonstrated that nearly 9 in 10 websites leak user data to parties of which the user is likely unaware; more than 6 in 10 websites spawn third-party cookies; and more than 8 in 10 websites load Javascript code. Sites that leak user data contact an average of nine external domains. Most importantly, by tracing the flows of personal browsing histories on the Web, it is possible to discover the corporations that profit from tracking users. Although many companies track users online, the overall landscape is highly consolidated, with the top corporation, Google, tracking users on nearly 8 of 10 sites in the Alexa top 1 million. Finally, by consulting internal NSA documents leaked by Edward Snowden, it has been determined that roughly one in five websites are potentially vulnerable to known NSA spying techniques at the time of analysis.
Using Social Media Ethically

An overview of the way the law profession's rules of professional responsibility/conduct apply to the use of social media platforms and tools, including advertising, searching, and use of social media information in investigation, discovery, and at trial.
Privacy & Transparency in Digital Life

Is it safe to share your location on Foursquare, Gowalla, Facebook, Twitter? Shouldn't we all share more, since only wrongdoers have something to hide? Is it even possible to opt out of sharing in a connected society?
The Firecat Studio First Friday Coworking and Brownbag lunch topic of May, 2011 covered these examples and currently proposed legislation.
Fearsquare (1)

This document discusses FearSquare, an application that combines public crime data with social media check-in services. It allows users to visualize and interact with official UK crime statistics based on places they frequently visit. The application retrieves crime data through APIs from Police.uk and locational check-in data from Foursquare. However, it is currently limited to UK data. The document calls for other governments to release crime statistics in standardized, machine-readable formats to allow the concept to expand internationally. It also discusses the need to ensure data is presented accurately to avoid misrepresenting locations.
Fraudsters Hackers & Thieves!

How can we better protect our customers?
It’s official: consumers do not feel their private data is being kept private. Looking around at the headlines, where high profile breach after high-profile breach is documented, the lack of trust in data security is no surprise.
In this graphical report, we delve into the fears surrounding online security and the economic impact of losing your customers’ trust.
Report on data breach and privacy in nepal during covid19 by shreedeep rayamajhi

This report analyzes data breaches and privacy issues in Nepal during the COVID-19 pandemic. It discusses several high-profile cases where hackers accessed and leaked personal information from major organizations, including food delivery service Foodmandu, internet provider Vianet, money transfer service Prabhu Money Transfer, and government websites. The report argues there is a lack of awareness and proper implementation of privacy laws in Nepal, as well as insufficient cybersecurity practices among many organizations. Improving cybersecurity culture and legal protections for personal data is needed to address the ongoing risks of data breaches during the pandemic.
Critical Update Needed: Cybersecurity Expertise in the Boardroom

Critical Update Needed: Cybersecurity Expertise in the BoardroomStanford GSB Corporate Governance Research Initiative
By David F. Larcker, Peter C. Reiss, and Brian Tayan
Stanford Closer Look Series, November 16, 2017
The board of directors is expected to ensure that management has identified and developed processes to mitigate risks facing the organization, including risks arising from data theft and the loss of information. Unfortunately, recent experience suggests that companies are not doing a sufficient job of securing this data. In this Closer Look, we examine they types of cyberattacks that occur and how companies respond to them.
We ask:
• What steps can the board take to prevent, monitor, and mitigate data theft?
• What data, metrics, and information should board members review to satisfy themselves that management has taken proper steps to minimize cyber risks?
• What qualifications should a board member have in order to constructively contribute to boardroom discussions on cybersecurity?
• How difficult is it to find board candidates with these skills?
Weekly eDiscovery Top Story Digest - March 5, 2014

Compiled by @ComplexD from online public domain resources, provided for your review/use is this week’s update of key industry news, views, and events highlighting key electronic discovery related stories, developments, and announcements.
Available as an information source for eDiscovery and information management professionals since 2010, the Top Story Digest is published weekly on the ComplexDiscovery (.com) blog.
Follow ComplexDiscovery.com via social media on Twitter (@ComplexD), LinkedIn, Google+ and RSS.
To receive the Weekly eDiscovery News Update by email for eDiscovery news, corporate risk information and vendor clips, visit http://www.ComplexDiscovery.com.
Toolkit on factchecking by shreedeep rayamajhi

This Toolkit on fact checking is developed for awareness and capacity building by shreedeep rayamajhi
Right Forgotten_v

1. Young people are increasingly conscious of curating their online image and digital footprint due to concerns about how future employers and others may judge them based on old social media posts and photos.
2. A recent European court ruling established a "right to be forgotten", allowing EU citizens to request certain personal information be deleted from search results, but the information can only be removed from specific Google domains and not entirely.
3. While some U.S. states have passed laws regarding privacy of social media accounts and data destruction, establishing a similar "right to be forgotten" in the U.S. is unlikely due to strong legal protections of free expression.
Privacy: Protecting Personal Information

This TechTalk session was presented by John Nicholson for the Johnson County Community College (JCCC) Retirees Association on August 31, 2017. The session covered information about personal data that is being sold about you, with no way for you to check its accuracy. This information includes health, financial, personal preferences, and search history. The session also briefly covered the Net Neutrality Act, recently vetoed by President Trump, and its effect on you. Finally, Suggestions were offered on how to protect yourself and your information in the future by making a few small, free or low cost changes to how you are currently using the Web. These changes can be made to your PC, tablet, and smart phones.
Data Mining: Privacy and Concerns

Data mining involves extracting and analyzing large amounts of data to find patterns. While it provides benefits to companies, some view it as an invasion of privacy. There is little regulation in the US on data mining. The government has broad powers to collect data under laws like the Patriot Act. Data breaches have compromised over 800 million records, revealing sensitive personal information. Retailers use data mining to target customers, while gamers mine data to learn about new game content. More regulation may be needed to protect personal privacy as data mining becomes more widespread.
Consumers' and Citizens' Privacy 

This document summarizes issues related to privacy and emerging technologies. It discusses how technologies like body cameras, big data, and the internet of things impact privacy based on international human rights standards. Specific concerns addressed include behavioral marketing, data aggregation, metadata collection, and government surveillance partnerships with private companies. The document advocates that any reforms around these issues must consider the close relationship between companies and governments when it comes to accessing people's personal information.
More Related Content
What's hot
GRBN Trust and Personal Data Survey - Market Research Industry Special Report

A special report focusing on how trusted the market research industry is across the globe to protect and appropriately use personal data
US mining data from 9 leading internet firms and companies deny knowledge

The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track one target or trace a whole network of associates, according to a top-secret document obtained by The Washington Post.
The program, code-named PRISM, has not been made public until now. It may be the first of its kind. The NSA prides itself on stealing secrets and breaking codes, and it is accustomed to corporate partnerships that help it divert data traffic or sidestep barriers. But there has never been a Google or Facebook before, and it is unlikely that there are richer troves of valuable intelligence than the ones in Silicon Valley.
Obama administration reverses on HealthCare.gov privacy policy after concerns

Bowing to an outcry over online privacy, the Obama administration reversed itself Friday, scaling ba...
Obama administration reverses on HealthCare.gov privacy policy after concerns

The Obama administration reversed its HealthCare.gov privacy policy after concerns were raised that the website was sending consumers' personal information like age, income, and health conditions to third-party advertising and analytics companies without consent. The administration made changes to reduce this sharing of data, though privacy advocates said more should be done since these third parties can still track users' behavior across websites and build profiles about their health interests. Officials had initially defended the practices but made the changes after lawmakers demanded an explanation.
CCPA: What You Need to Know

The document summarizes key aspects of California's new data privacy law, the California Consumer Privacy Act (CCPA). It outlines consumer rights like the right to access, delete, and opt-out of the sale of their data. It also discusses which businesses are impacted, obligations of covered businesses, potential penalties for noncompliance up to $7,500 per violation, and exemptions. There is uncertainty around how the law may be amended or preempted by future federal privacy legislation sought by big tech companies seeking to weaken its protections and reduce penalties.
Sbs facebook data privacy dilemma case study

Dear students get fully solved assignments
Send your semester & Specialization name to our mail id :
help.mbaassignments@gmail.com
or
call us at : 08263069601
Pli government investigations 2020

This document announces a government investigations program that will explore data breach investigations from the perspective of investigating agencies and corporations responding to such investigations. It will consider the scope of investigations arising from data breaches and privacy concerns, how corporations should respond by locating and producing electronic information. It will also discuss potential parallel civil proceedings and how information shared with investigating agencies may be used in litigation. The program aims to help corporations understand investigation obligations and protect privileged information.
Open Source Insight: Drupageddon, Heartbleed Problems & Open Source 360 Surve...

Open Source Insight: Drupageddon, Heartbleed Problems & Open Source 360 Surve...Black Duck by Synopsys
Open source insight this week on CVE-2014-3704, aka “Drupageddon” and CVE-2014-0160, the everlasting Heartbleed, plus results of our Open Source 360 Survey.Bericht icomp vol4

This document summarizes the results of an eye tracking study commissioned by ICOMP to analyze attention and selection behavior on Google search result pages. The study found that:
1) Google's own product search results and map/image panes received the majority of visual attention from users and were clicked on most frequently.
2) Alternative search sites logos received little visual attention and few clicks.
3) Organic links received less visual attention than Google elements above them and were often not noticed due to their positioning lower on the page.
4) Google ads received very little visual attention or clicks across all search result pages tested.
Exposing the Hidden Web

The purpose of this article is to provide a quantitative analysis of privacy-compromising mechanisms on the top 1 million websites as determined by Alexa. It is demonstrated that nearly 9 in 10 websites leak user data to parties of which the user is likely unaware; more than 6 in 10 websites spawn third-party cookies; and more than 8 in 10 websites load Javascript code. Sites that leak user data contact an average of nine external domains. Most importantly, by tracing the flows of personal browsing histories on the Web, it is possible to discover the corporations that profit from tracking users. Although many companies track users online, the overall landscape is highly consolidated, with the top corporation, Google, tracking users on nearly 8 of 10 sites in the Alexa top 1 million. Finally, by consulting internal NSA documents leaked by Edward Snowden, it has been determined that roughly one in five websites are potentially vulnerable to known NSA spying techniques at the time of analysis.
Using Social Media Ethically

An overview of the way the law profession's rules of professional responsibility/conduct apply to the use of social media platforms and tools, including advertising, searching, and use of social media information in investigation, discovery, and at trial.
Privacy & Transparency in Digital Life

Is it safe to share your location on Foursquare, Gowalla, Facebook, Twitter? Shouldn't we all share more, since only wrongdoers have something to hide? Is it even possible to opt out of sharing in a connected society?
The Firecat Studio First Friday Coworking and Brownbag lunch topic of May, 2011 covered these examples and currently proposed legislation.
Fearsquare (1)

This document discusses FearSquare, an application that combines public crime data with social media check-in services. It allows users to visualize and interact with official UK crime statistics based on places they frequently visit. The application retrieves crime data through APIs from Police.uk and locational check-in data from Foursquare. However, it is currently limited to UK data. The document calls for other governments to release crime statistics in standardized, machine-readable formats to allow the concept to expand internationally. It also discusses the need to ensure data is presented accurately to avoid misrepresenting locations.
Fraudsters Hackers & Thieves!

How can we better protect our customers?
It’s official: consumers do not feel their private data is being kept private. Looking around at the headlines, where high profile breach after high-profile breach is documented, the lack of trust in data security is no surprise.
In this graphical report, we delve into the fears surrounding online security and the economic impact of losing your customers’ trust.
Report on data breach and privacy in nepal during covid19 by shreedeep rayamajhi

This report analyzes data breaches and privacy issues in Nepal during the COVID-19 pandemic. It discusses several high-profile cases where hackers accessed and leaked personal information from major organizations, including food delivery service Foodmandu, internet provider Vianet, money transfer service Prabhu Money Transfer, and government websites. The report argues there is a lack of awareness and proper implementation of privacy laws in Nepal, as well as insufficient cybersecurity practices among many organizations. Improving cybersecurity culture and legal protections for personal data is needed to address the ongoing risks of data breaches during the pandemic.
Critical Update Needed: Cybersecurity Expertise in the Boardroom

Critical Update Needed: Cybersecurity Expertise in the BoardroomStanford GSB Corporate Governance Research Initiative
By David F. Larcker, Peter C. Reiss, and Brian Tayan
Stanford Closer Look Series, November 16, 2017
The board of directors is expected to ensure that management has identified and developed processes to mitigate risks facing the organization, including risks arising from data theft and the loss of information. Unfortunately, recent experience suggests that companies are not doing a sufficient job of securing this data. In this Closer Look, we examine they types of cyberattacks that occur and how companies respond to them.
We ask:
• What steps can the board take to prevent, monitor, and mitigate data theft?
• What data, metrics, and information should board members review to satisfy themselves that management has taken proper steps to minimize cyber risks?
• What qualifications should a board member have in order to constructively contribute to boardroom discussions on cybersecurity?
• How difficult is it to find board candidates with these skills?
Weekly eDiscovery Top Story Digest - March 5, 2014

Compiled by @ComplexD from online public domain resources, provided for your review/use is this week’s update of key industry news, views, and events highlighting key electronic discovery related stories, developments, and announcements.
Available as an information source for eDiscovery and information management professionals since 2010, the Top Story Digest is published weekly on the ComplexDiscovery (.com) blog.
Follow ComplexDiscovery.com via social media on Twitter (@ComplexD), LinkedIn, Google+ and RSS.
To receive the Weekly eDiscovery News Update by email for eDiscovery news, corporate risk information and vendor clips, visit http://www.ComplexDiscovery.com.
Toolkit on factchecking by shreedeep rayamajhi

This Toolkit on fact checking is developed for awareness and capacity building by shreedeep rayamajhi
Right Forgotten_v

1. Young people are increasingly conscious of curating their online image and digital footprint due to concerns about how future employers and others may judge them based on old social media posts and photos.
2. A recent European court ruling established a "right to be forgotten", allowing EU citizens to request certain personal information be deleted from search results, but the information can only be removed from specific Google domains and not entirely.
3. While some U.S. states have passed laws regarding privacy of social media accounts and data destruction, establishing a similar "right to be forgotten" in the U.S. is unlikely due to strong legal protections of free expression.
Privacy: Protecting Personal Information

This TechTalk session was presented by John Nicholson for the Johnson County Community College (JCCC) Retirees Association on August 31, 2017. The session covered information about personal data that is being sold about you, with no way for you to check its accuracy. This information includes health, financial, personal preferences, and search history. The session also briefly covered the Net Neutrality Act, recently vetoed by President Trump, and its effect on you. Finally, Suggestions were offered on how to protect yourself and your information in the future by making a few small, free or low cost changes to how you are currently using the Web. These changes can be made to your PC, tablet, and smart phones.
What's hot (20)
GRBN Trust and Personal Data Survey - Market Research Industry Special Report

GRBN Trust and Personal Data Survey - Market Research Industry Special Report
US mining data from 9 leading internet firms and companies deny knowledge

US mining data from 9 leading internet firms and companies deny knowledge
Obama administration reverses on HealthCare.gov privacy policy after concerns

Obama administration reverses on HealthCare.gov privacy policy after concerns
Obama administration reverses on HealthCare.gov privacy policy after concerns

Obama administration reverses on HealthCare.gov privacy policy after concerns
Open Source Insight: Drupageddon, Heartbleed Problems & Open Source 360 Surve...

Open Source Insight: Drupageddon, Heartbleed Problems & Open Source 360 Surve...
Report on data breach and privacy in nepal during covid19 by shreedeep rayamajhi

Report on data breach and privacy in nepal during covid19 by shreedeep rayamajhi
Critical Update Needed: Cybersecurity Expertise in the Boardroom

Critical Update Needed: Cybersecurity Expertise in the Boardroom
Weekly eDiscovery Top Story Digest - March 5, 2014

Weekly eDiscovery Top Story Digest - March 5, 2014
Similar to A priest’s phone location data outed his private life. It could happen to anyone.
Data Mining: Privacy and Concerns

Data mining involves extracting and analyzing large amounts of data to find patterns. While it provides benefits to companies, some view it as an invasion of privacy. There is little regulation in the US on data mining. The government has broad powers to collect data under laws like the Patriot Act. Data breaches have compromised over 800 million records, revealing sensitive personal information. Retailers use data mining to target customers, while gamers mine data to learn about new game content. More regulation may be needed to protect personal privacy as data mining becomes more widespread.
Consumers' and Citizens' Privacy 

This document summarizes issues related to privacy and emerging technologies. It discusses how technologies like body cameras, big data, and the internet of things impact privacy based on international human rights standards. Specific concerns addressed include behavioral marketing, data aggregation, metadata collection, and government surveillance partnerships with private companies. The document advocates that any reforms around these issues must consider the close relationship between companies and governments when it comes to accessing people's personal information.
How to protect privacy sensitive data that is collected to control the corona...

In Singapore, the Government launched an app using short-distance Bluetooth signals to connect one phone using the app with another user who is close by. It stores detailed records on a user's phone for 21 days decrypt the data if there is a public health risk related to an individual's movements.
China used a similar method to track a person's health status and to control movement in cities with high numbers of coronavirus cases. Individuals had to use the app and share their status to be able to access public transportation.
The keys to addressing privacy concerns about high-tech surveillance by the state is de-identifying the data and giving individuals control over their own data. Personal details that may reveal your identity such as a user's name should not be collected or should be protected with access to be granted for only specific health purposes, and data should be deleted after its specific use is no longer needed.
We will discuss how to protect privacy sensitive data that is collected to control the coronavirus outbreak.
Accessing Password Protected andor Encrypted Mobile DataAbstrac.docx

Accessing Password Protected and/or Encrypted Mobile Data
Abstract- This research paper examines the potential solution to a problem faced by law enforcement; wherein the inability to decrypt a number of encrypted communications that they have been given appropriate legal permission to intercept or examine, loom large. This research paper utilizes a theoretical approach to explore the ‘going dark’ concern. This paper will also provide an overview of an encryption workaround, which will address the widely used “Signal Messaging Protocol” which is used to encrypt messages transmitted via applications such as Whatsapp, Telegram, Facebook, among others.
Keywords—Signal Messaging Protocol, Encrypted Messaging, Privacy, Law Enforcement, Mobile Phones, WhatsAppI. Introduction
As the use of digital mobile devices continues to become more ubiquitous, so too does the use of strong encryption protocols, which are being made available to users by communication application providers. In an effort to provide even more security to users, those same application providers are developing the encryption protocols in such a way that the providers themselves are not even able to decrypt the private messages. These trends are posing an ever-increasing challenge to law enforcement agencies who are often able to obtain the legal authority necessary to intercept or retrieve certain communication dataonly to find that they are unable to decrypt and view that same data. The FBI has labeled this issue as the “Going Dark” problem.
The “Going Dark” problem often has adverse effects on law enforcement’s ability to investigate all kinds of crimes; such as kidnappings, child pornography, violent gang activity, etc. However, the gravest consequential examples of this problem have arisen through terrorist investigations, wherein the stakes are extremely high.
Agencies charged with combating terrorism, such as the FBI, quietly face this obstacle every day. In December 2015, the public was given an inside view of this dilemma, during the aftermath of the San Bernardino, California, terrorist attack. Following the attack, the FBI recovered a passcode locked iPhone 5, which had belonged to one of the shooters. The passcode function keeps the encased data encrypted until the correct passcode is entered. If the wrong passcode is entered more than ten times, the data is automatically permanently wiped from the device. In response, the FBI obtained a court order directing Apple to assist them in developing software to unlock the phone. Apple refused, which set off a fierce public outcry, and a subsequent legal battle. The standoff was ultimately diffused when the FBI was able to find a third party to crack the four-digit passcode.
As a result of that legal dispute between the Department of Justice and Apple not having being resolved in court, the debate continued over the question: should the government be able to legally force private vendors to create decryption keys for law .
iStart feature: Protect and serve how safe is your personal data?

The revelations of the Heartbleed vulnerability in April and the recent implementation of Australia’s new privacy regime in March have put data breaches firmly back in the limelight. Clare Coulson finds out more...
Where In The World Is Your Sensitive Data?

Consumers rely on businesses to keep their personal information safe. Too few of those businesses are actively protecting that data. Here’s what’s gone wrong, and how businesses should be responding. Full blog here: http://bit.ly/1Jtzym5
Emerging Applications on Smart Phones: The Role of Privacy Concerns and its A...

Emerging Applications on Smart Phones: The Role of Privacy Concerns and its A...AIRCC Publishing Corporation
Many applications on smart Phones can use various sensors embedded in the mobiles to provide users’ private information. This can result in a variety of privacy issues that may lessening level of mobile apps usage. To understand this issue better the researcher identified the root causes of privacy concerns. The study proposed a model identifies the root causes of privacy concerns and perceived benefits based on our interpretation for information boundary theory. The proposed model also addresses the usage behavior and behavioral intention toward using mobile apps by using the Theory of Planned Behavior. The result shows that “Cultural values” alone explains 70% of “Perceived privacy concerns” followed by “Self-defense” which explains around 23% of “Perceived privacy concerns”, and then “Context of the situation” with 5%. Whereas, the findings show that “Perceived effectiveness of privacy policy” and “Perceived effectiveness of industry self-regulation” both are factors which have the ability to reduce individuals “Perceived privacy concerns” by 9% and 8% respectively.
Privacy study Mobile and online Dating

This paper is intended to educate mobile and internet users on the daily threats they face while using their cell phone, emails to communicate and browsing the web.
It contains current statistics on cybercrimes, online dating, web browsing privacy issues and so forth. Analyses case studies and offers solutions to protect your privacy.
Mobile Privacy and Security - Study by Mobidigger

In a world where Google, Facebook, Twitter and other top web sites share and save user
information, it is increasingly hard to protect individual privacy in new media—on the Internet and
mobile phones. At the same time, information about privacy protection is very hard to find.
Further, the majority of people who use the Internet are generally not properly informed about
new media privacy issues. To help users protect themselves, this presentation explores Internet
and mobile privacy problems and solutions through reviews of case studies. It is designed to
educate users of new media in both key issues and solutions.
AI for humans - the future of your digital self

ABSTRACT: In this talk, George will demonstrate the extent and power of personal data collected by technology companies. He will explore the potential of personal data to do both good and bad, the dangers of giving up your "digital DNA", and the value these companies extract from this data.
Data rights are finally legally recognised. With the combination of GDPR & rising awareness of personal data abuse, we might eventually be able to control our data, or at least understand as much about our digital footprint as profit-driven companies do.
AI is only possible because it has data. Imagine your data being used to benefit you, instead of targeting you with gambling adverts. Imagine the potential for next-generation research to understand our society, which can only happen if we break data out from being locked in corporate databases. Data rights are just the start, now we need to use them.
BIO: George Punter holds a first class Masters degree from Imperial College London in Electronics & Information Engineering. He co-founded Ethi (ethi.me), a startup that aims to make controlling your personal data easier, and allow users to use their personal data for their own benefit, or for social good. Ethi is currently partnering with a cyber security firm, TurgenSec, to help create next-generation, user-centred security.
Designing for Privacy in an Increasingly Public World

Designing for Privacy in an Increasingly Public World as presented by Robert Stribley at the Brooklyn Product Design Meetup, Wednesday, July 21, 2021
httpsdigitalguardian.comblogsocial-engineering-attacks-common.docx

https://digitalguardian.com/blog/social-engineering-attacks-common-techniques-how-prevent-attack
Statement of Michelle Richardson, Director, Privacy & Data
Center for Democracy & Technology
before the
United States Senate Committee on the Judiciary
GDPR & CCPA: Opt-ins, Consumer Control, and the Impact on Competition and Innovation
March 12, 2019
On behalf of the Center for Democracy & Technology (CDT), thank you for the
opportunity to testify about the importance of crafting a federal consumer privacy law that
provides meaningful protections for Americans and clarity for entities of all sizes and sectors.
CDT is a nonpartisan, nonprofit 501(c)(3) charitable organization dedicated to advancing the
rights of the individual in the digital world. CDT is committed to protecting privacy as a
fundamental human and civil right and as a necessity for securing other rights such as access to
justice, equal protection, and freedom of expression. CDT has offices in Washington, D.C., and
Brussels, and has a diverse funding portfolio from foundation grants, corporate donations, and
individual donations.1
The United States should be leading the way in protecting digital civil rights. This hearing
is an opportunity to learn how Congress can improve upon the privacy frameworks offered in
the European Union via the General Data Protection Regulation (GDPR) and the California
Consumer Privacy Act (CCPA) to craft a comprehensive privacy law that works for the U.S. Our
digital future should be one in which technology supports human rights and human dignity. This
future cannot be realized if people are forced to choose between protecting their personal
information and using the technologies and services that enhance our lives. This future depends
on clear and meaningful rules governing data processing; rules that do not simply provide
1 All donations over $1,000 are disclosed in our annual report and are available online at:
https://cdt.org/financials/.
2
people with notices and check boxes but actually protect them from privacy and security
abuses and data-driven discrimination; protections that cannot be signed away.
Congress should resist the narratives that innovative technologies and strong privacy
protections are fundamentally at odds, and that a privacy law would necessarily cement the
market dominance of a few large companies. Clear and focused privacy rules can help
companies of all sizes gain certainty with respect to appropriate and inappropriate uses of data.
Clear rules will also empower engineers and product managers to design for privacy on the
front end, rather than having to wait for a public privacy scandal to force the rollback of a
product or data practice.
We understand that drafting comprehensive privacy legislation is a complex endeavor.
Over the past year we have worked with partners in civil societ.
9 Trends in Identity Verification (2023) by Regula

Regula held an internal panel discussion and compiled nine expert opinion-based identity verification trends to watch and leverage in 2023. You can find the full text in our blog: https://regulaforensics.com/blog/identity-verification-trends-2023/
10 Criminology in the FutureCriminology in the FutureKristop.docx

10 Criminology in the Future
Criminology in the Future
Kristopher Freitag, Javielle Watson, Michael Westphal, Starcia Zeigler
CJA/314
April 7, 2014
Judy Mazzucca
Technology is advancing in every aspect of the criminal justice system, from the investigation to the prosecution of the crimes. Crime fighting methodologies have the potential to greatly assist law enforcement in the war on crime. Some experts even think that some software and tools will be able to help prevent crime. (Yeung, n.d.). Methodologies, such as mandating DNA collection programs, biometrics, and implementing cybercrime spyware programs are on the list of the next big things of the future, when it comes to fighting crime. DNA testing helps law enforcement investigate and prosecute crimes, as well as clear the names of those who have been wrongfully convicted. There are currently about twenty states with laws requiring DNA collection at the time of the person’s arrest. The federal government also has this requirement. As, with any controversial subject, DNA testing has its critics. Some are saying that DNA testing is in violation of the Fourth Amendment, especially for those who have not been convicted of a crime. Others are concerned that DNA testing may open the doors for abuse of the genetic information being stored in the databases. (Berson, n.d.). Biometrics are automated methods of recognizing a person based on physiological or behavioral characteristics. Some of the features measured using biometrics are handwriting, voice, iris, hand geometry, vein, retinal, and fingerprints. Biometric based solutions provide personal data privacy, and confidential financial transactions, and are starting to become the foundation of an extensive array of highly secure identification and personal verification solutions. The need for highly secure identification and personal verification technologies is great, due to the increased number of transaction fraud and security breaches. This need is especially great in the areas of local, state, and federal governments. Infrastructures such as electronic banking, health and social services, law enforcement, and retail sales are already taking advantage of, and seeing the benefits of biometric technology. ("The Biometrics Consortium", n.d.).
As we become more and more dependent on technology, the increase of cybercrimes are skyrocketing, which has forced law enforcement to figure out ways of combatting cybercrimes. We have become extremely vulnerable to many cybercrimes, including social media fraud, which consists of cyber criminals using social media to steal the identities of unsuspecting people; and luring people to download malicious materials, or reveal their passwords; corporate security breaches, which consists of cyber criminals exploiting company employees via scams; and phishing, which involves cyber criminals targeting company employees by sending emails that appear to be from someone within the company. ("Homeland .
Carpe Datum! Who knows who you are?

This article written Diarmaid Byrne, Editor, STQ, was published in issue 08 of the Social Technology Quarterly.
Summary: In the face of rising demand for data, privacy and ownership become a critical concern as vast amounts of data are accessed and bartered without the knowledge of people. In such scenarios, it is crucial to determine practices towards maintaining privacy.
Noggin - World's first marketplace for Personal Data

Direct marketing is expensive; and customer details are usually unknown. Customer on other hand is worried about personal data. Noggin is a marketplace to connect these two. Discover us at www.nogginasia.com. Consumers can earn by sharing personal data
Social Network Crime on Rise

Social networking sites have become major targets for cybercrime due to the large amounts of personal user information they collect. Criminals are able to use details from profiles to craft convincing phishing emails and social engineer victims. While anonymity online enables some criminal behavior, removing anonymity also poses risks to privacy and freedom of expression. As more data is aggregated about individuals, it will become easier over time to identify users and develop detailed profiles about their lives, habits, and relationships, even if they try to remain anonymous. This aggregated data could then potentially be used for surveillance and other strategic purposes beyond just marketing. Strong privacy laws and regulations are needed to curb these emerging threats to privacy.
Getting the social side of pervasive computing right

The document discusses privacy issues that may arise with the rise of pervasive computing technologies. It outlines four "dark scenarios" showing potential social problems, including inaccurate personal profiling, location tracking without consent, and health monitoring system failures. The document calls for privacy to be designed into new technologies from the start through principles like data minimization, in order to build public trust and avoid privacy disasters.
privtechsomeassemb

Privacy is being threatened by new technologies that collect and track personal data. Companies are developing facial recognition in phones and cameras, location tracking in vehicles, and smart home meters. The NSA also engages in mass surveillance programs like collecting cell phone metadata and infecting millions of devices with malware. While governments and businesses claim this data is used for security and research, it often leads to abuses of power over individuals. Strong privacy laws and oversight of data collection are needed to curb these threats and restore trust between technology and users.
Privacy

Americans are highly concerned about the privacy and security of their personal data, with 58% reporting they are very concerned. This level of concern is greater than for issues like gun violence and climate change. The rollout of 5G is expected to increase privacy and security concerns further. People feel stuck and overwhelmed trying to manage their data privacy, and they are conflicted - expressing concern but not taking many proactive steps. Existing regulations to protect privacy are not reassuring to most people, as the majority are unaware of laws like GDPR and CCPA. Customers continue doing business with companies after data breaches, despite feeling resigned that further breaches will occur.
Similar to A priest’s phone location data outed his private life. It could happen to anyone. (20)
How to protect privacy sensitive data that is collected to control the corona...

How to protect privacy sensitive data that is collected to control the corona...
Accessing Password Protected andor Encrypted Mobile DataAbstrac.docx

Accessing Password Protected andor Encrypted Mobile DataAbstrac.docx
iStart feature: Protect and serve how safe is your personal data?

iStart feature: Protect and serve how safe is your personal data?
Emerging Applications on Smart Phones: The Role of Privacy Concerns and its A...

Emerging Applications on Smart Phones: The Role of Privacy Concerns and its A...
Designing for Privacy in an Increasingly Public World

Designing for Privacy in an Increasingly Public World
httpsdigitalguardian.comblogsocial-engineering-attacks-common.docx

httpsdigitalguardian.comblogsocial-engineering-attacks-common.docx
9 Trends in Identity Verification (2023) by Regula

9 Trends in Identity Verification (2023) by Regula
10 Criminology in the FutureCriminology in the FutureKristop.docx

10 Criminology in the FutureCriminology in the FutureKristop.docx
Noggin - World's first marketplace for Personal Data

Noggin - World's first marketplace for Personal Data
Getting the social side of pervasive computing right

Getting the social side of pervasive computing right
More from LUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
Howard Fineman, Veteran Political Journalist and TV Pundit, Dies at 75

Howard Fineman, Veteran Political Journalist and TV Pundit, Dies at 75LUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
From his beginnings with a daily newspaper, he moved easily through Newsweek magazine to cable news and, later, to the frontiers of online journalism.What Ukraine Has Lost During Russia’s Invasion

An astonishing, first-of-its-kind, report by the NYT assessing damage in Ukraine. Even if the war ends tomorrow, in many places there will be nothing to go back to.
A.I. Has a Measurement Problem: Can It Be Solved?

Which A.I. system writes the best computer code or generates the most realistic image? Right now, there’s no easy way to answer those questions.
Let’s Say Someone Did Drop the Bomb. Then What?

In “Nuclear War” and “Countdown,” Annie Jacobsen and Sarah Scoles talk to the people whose job it is to prepare for atomic conflict.
How Tech Giants Cut Corners to Harvest Data for A.I.

OpenAI, Google and Meta ignored corporate policies, altered their own rules and discussed skirting copyright law as they sought online information to train their newest artificial intelligence systems.
Why democracy dies in Trumpian boredom (by Edward Luce)

The candidate’s unchecked flow of untruths and bizarre outbursts spell danger but no longer cause sufficient shock
An interview with the director of "Zone of Interest"

I have never seen any movie like it, ever. There are no words. Simply, “The Zone of Interest” is the greatest meditation ever made on film about the banality of evil and the capacity of human beings to be indifferent towards cruelty that beggars imagination.
"Schindler’s List" : an oral history with the actors

30 years after Spielberg won best picture and best director for his movie about Oskar Schindler, an oral history with the original actors
Chinese Startup 01.AI Is Winning the Open Source AI Race

Chinese Startup 01.AI Is Winning the Open Source AI RaceLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
Kai-Fu Lee, an AI expert and prominent investor who helped Google and Microsoft get established in China, says his new startup 01.AI will create the first “killer apps” of generative AI.The mismeasuring of AI: How it all began

This document is the first part of a three-part series exploring issues with measuring and evaluating AI systems. It discusses how AI was traditionally evaluated by benchmarks like chess games, but that benchmarks are limited for large language models like GPT-3. Old tests like the Turing Test are no longer relevant as newer models can mimic humans. The document examines the history of focusing on data-driven approaches to progress AI and how that led to more complex models that are difficult to properly evaluate. It introduces the need to address challenges in evaluating large language models to help guide their development and impact.
Google’s Gemini Marketing Trick: what a trickster!

Google introduced its new AI model Gemini this week, which showed impressive capabilities. However, Google exaggerated in its promotional video for Gemini by speeding up responses, shortening outputs, and using still images rather than video. While hype videos often take artistic license, people in the AI community felt Google's exaggerations went too far. The misleading marketing tactics damaged Google's credibility with developers and onlookers, though its parent company Alphabet's stock still rose following the announcement.
Inside the Magical World of AI Prompters on Reddit

The story of AI images isn’t just about robots, but also about the people behind these strange, futuristic visuals.
Regulators blame Bezos for making Amazon worse in new lawsuit details

Regulators blame Bezos for making Amazon worse in new lawsuit detailsLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
Previously redacted portions of the Federal Trade Commission’s lawsuit against Amazon allege Bezos gave the go-ahead to make search results worse in favor of increasing advertising revenue
Bariatric Surgery at 16

This article discusses 16-year-old Alexandra Duarte's decision to undergo bariatric surgery to address her severe obesity. It describes her struggles over many years trying different diets and programs, as well as bullying due to her weight. The article provides context on the rise of childhood obesity in the US and debates around new guidelines recommending more aggressive treatment, including drugs and surgery. It also explores the biological factors that influence appetite and weight regulation in the brain and genes.
Palestinians Claim Social Media 'Censorship' Is Endangering Lives

Palestinians Claim Social Media 'Censorship' Is Endangering LivesLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
Alleged censorship of social media and disruptions to electricity and internet access have meant people under fire in Gaza can’t get the information they need to survive.Who’s Responsible for the Gaza Hospital Explosion? Here’s Why It’s Hard to Know

Who’s Responsible for the Gaza Hospital Explosion? Here’s Why It’s Hard to KnowLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
A flood of false information, partisan narratives, and weaponized “fact-checking" has obscured efforts to find out who’s responsible for an explosion at a hospital in Gaza.Why ChatGPT Is Getting Dumber at Basic Math

AI chatbots have stoked fears that they could spin out of control, but they also suffer from a type of deterioration called ‘drift’
U.S. and E.U. Finalize Long-Awaited Deal on Sharing Data

U.S. and E.U. Finalize Long-Awaited Deal on Sharing DataLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
The US and EU finalized a long-awaited data-sharing agreement that will allow personal data to continue flowing freely between the two regions. The deal establishes an independent review body for Europeans to appeal potential improper data collection by US intelligence agencies. It also outlines more clearly when intelligence agencies can access personal data of EU residents and how Europeans can appeal such collection. Some privacy advocates and EU lawmakers remain skeptical that it does enough to curb US mass surveillance.Will A.I. Become the New McKinsey?

As it’s currently imagined, the technology promises to concentrate wealth and disempower workers. Is an alternative possible?
AI is already writing books, websites and online recipes

AI is already writing books, websites and online recipesLUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP
He wrote a book on a rare subject. Then a ChatGPT replica appeared on Amazon.
From recipes to product reviews to how-to books, artificial intelligence text generators are quietly authoring more and more of the internet.More from LUMINATIVE MEDIA/PROJECT COUNSEL MEDIA GROUP (20)
Howard Fineman, Veteran Political Journalist and TV Pundit, Dies at 75

Howard Fineman, Veteran Political Journalist and TV Pundit, Dies at 75
How Tech Giants Cut Corners to Harvest Data for A.I.

How Tech Giants Cut Corners to Harvest Data for A.I.
Why democracy dies in Trumpian boredom (by Edward Luce)

Why democracy dies in Trumpian boredom (by Edward Luce)
An interview with the director of "Zone of Interest"

An interview with the director of "Zone of Interest"
"Schindler’s List" : an oral history with the actors

"Schindler’s List" : an oral history with the actors
Chinese Startup 01.AI Is Winning the Open Source AI Race

Chinese Startup 01.AI Is Winning the Open Source AI Race
Google’s Gemini Marketing Trick: what a trickster!

Google’s Gemini Marketing Trick: what a trickster!
Inside the Magical World of AI Prompters on Reddit

Inside the Magical World of AI Prompters on Reddit
Regulators blame Bezos for making Amazon worse in new lawsuit details

Regulators blame Bezos for making Amazon worse in new lawsuit details
Palestinians Claim Social Media 'Censorship' Is Endangering Lives

Palestinians Claim Social Media 'Censorship' Is Endangering Lives
Who’s Responsible for the Gaza Hospital Explosion? Here’s Why It’s Hard to Know

Who’s Responsible for the Gaza Hospital Explosion? Here’s Why It’s Hard to Know
U.S. and E.U. Finalize Long-Awaited Deal on Sharing Data

U.S. and E.U. Finalize Long-Awaited Deal on Sharing Data
AI is already writing books, websites and online recipes

AI is already writing books, websites and online recipes
Recently uploaded
A tale of scale & speed: How the US Navy is enabling software delivery from l...

Rapid and secure feature delivery is a goal across every application team and every branch of the DoD. The Navy’s DevSecOps platform, Party Barge, has achieved:
- Reduction in onboarding time from 5 weeks to 1 day
- Improved developer experience and productivity through actionable findings and reduction of false positives
- Maintenance of superior security standards and inherent policy enforcement with Authorization to Operate (ATO)
Development teams can ship efficiently and ensure applications are cyber ready for Navy Authorizing Officials (AOs). In this webinar, Sigma Defense and Anchore will give attendees a look behind the scenes and demo secure pipeline automation and security artifacts that speed up application ATO and time to production.
We will cover:
- How to remove silos in DevSecOps
- How to build efficient development pipeline roles and component templates
- How to deliver security artifacts that matter for ATO’s (SBOMs, vulnerability reports, and policy evidence)
- How to streamline operations with automated policy checks on container images
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI

Enchancing adoption of Open Source Libraries. A case study on Albumentations.AIVladimir Iglovikov, Ph.D.
Presented by Vladimir Iglovikov:
- https://www.linkedin.com/in/iglovikov/
- https://x.com/viglovikov
- https://www.instagram.com/ternaus/
This presentation delves into the journey of Albumentations.ai, a highly successful open-source library for data augmentation.
Created out of a necessity for superior performance in Kaggle competitions, Albumentations has grown to become a widely used tool among data scientists and machine learning practitioners.
This case study covers various aspects, including:
People: The contributors and community that have supported Albumentations.
Metrics: The success indicators such as downloads, daily active users, GitHub stars, and financial contributions.
Challenges: The hurdles in monetizing open-source projects and measuring user engagement.
Development Practices: Best practices for creating, maintaining, and scaling open-source libraries, including code hygiene, CI/CD, and fast iteration.
Community Building: Strategies for making adoption easy, iterating quickly, and fostering a vibrant, engaged community.
Marketing: Both online and offline marketing tactics, focusing on real, impactful interactions and collaborations.
Mental Health: Maintaining balance and not feeling pressured by user demands.
Key insights include the importance of automation, making the adoption process seamless, and leveraging offline interactions for marketing. The presentation also emphasizes the need for continuous small improvements and building a friendly, inclusive community that contributes to the project's growth.
Vladimir Iglovikov brings his extensive experience as a Kaggle Grandmaster, ex-Staff ML Engineer at Lyft, sharing valuable lessons and practical advice for anyone looking to enhance the adoption of their open-source projects.
Explore more about Albumentations and join the community at:
GitHub: https://github.com/albumentations-team/albumentations
Website: https://albumentations.ai/
LinkedIn: https://www.linkedin.com/company/100504475
Twitter: https://x.com/albumentationsFull-RAG: A modern architecture for hyper-personalization

Mike Del Balso, CEO & Co-Founder at Tecton, presents "Full RAG," a novel approach to AI recommendation systems, aiming to push beyond the limitations of traditional models through a deep integration of contextual insights and real-time data, leveraging the Retrieval-Augmented Generation architecture. This talk will outline Full RAG's potential to significantly enhance personalization, address engineering challenges such as data management and model training, and introduce data enrichment with reranking as a key solution. Attendees will gain crucial insights into the importance of hyperpersonalization in AI, the capabilities of Full RAG for advanced personalization, and strategies for managing complex data integrations for deploying cutting-edge AI solutions.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
20 Comprehensive Checklist of Designing and Developing a Website

Dive into the world of Website Designing and Developing with Pixlogix! Looking to create a stunning online presence? Look no further! Our comprehensive checklist covers everything you need to know to craft a website that stands out. From user-friendly design to seamless functionality, we've got you covered. Don't miss out on this invaluable resource! Check out our checklist now at Pixlogix and start your journey towards a captivating online presence today.
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

ここ3000字までしか入らないけどタイトルの方がたくさん文字入ると思います。
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
Recently uploaded (20)
A tale of scale & speed: How the US Navy is enabling software delivery from l...

A tale of scale & speed: How the US Navy is enabling software delivery from l...
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI

Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
Full-RAG: A modern architecture for hyper-personalization

Full-RAG: A modern architecture for hyper-personalization
20 Comprehensive Checklist of Designing and Developing a Website

20 Comprehensive Checklist of Designing and Developing a Website
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...

Alt. GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using ...
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
A priest’s phone location data outed his private life. It could happen to anyone.
- 1. Page 1 of 10 A priest’s phone location data outed his private life. It could happen to anyone. How an unregulated market for personal data is legal, and what it means for your privacy The Washington Post July 22, 2021
- 2. Page 2 of 10 What stands out about this particular incident isn’t that it’s improbable but that it’s the exact worst-case scenario privacy experts have been warning about for a long time. Personal data is collected, sold and bought by a tangle of app developers, data brokers and advertising companies with little oversight. The biggest shock may be that it didn’t happen sooner. “This is the first instance that I know of, of this data being used by a journalistic entity to track a specific person and weaponize their private, secretly collected information against them,” said Bennett Cyphers, a staff technologist at the Electronic Frontier Foundation, a digital rights organization. “This is exactly the kind of privacy threat advocates have been describing for years.” There is still much to be learned about how the priest’s private data could have made the journey from his smartphone into the hands of a Catholic newsletter’s writer. The newsletter, the Pillar, didn’t name the source of the data or clarify how it obtained the revealing location information, which it says spanned three years. But the story implies it started with data that Grindr
- 3. Page 3 of 10 allegedly shared with advertising partners and data brokers in the past that was then legally sold by a data broker. In a statement posted to Twitter defending the article and the anonymity it granted the data provider, method and funder, the Pillar’s editor in chief, JD Flynn, said it weighed the balance between an individual’s privacy and public interest, and was “confident in our deliberation.” He added that “technology accountability has been an issue of importance among church leaders for quite some time.” How anyone’s information could end up for sale Right now, your smartphone is likely filled with apps that are collecting details about you, including your age, gender, political leanings, GPS data or browsing habits. Grindr and other apps have long shared this kind of information with third-party data brokers, which exist in a largely unregulated sweet spot between websites, apps and advertisers. The brokers gather the data from apps, then sell it on the open market to
- 4. Page 4 of 10 parties that use it for ad targeting, political profiling or even research. It’s a well-established industry but one that doesn’t typically draw this level of attention. “Often the location data is used to determine what stores people visit. Things like sexual orientation are used to determine what demographics to target,” said Ashkan Soltani, an independent researcher and a former chief technologist at the Federal Trade Commission. “People don’t actually know or care that much that they’re being targeted. Or it’s used by nation state actors to surveil people, but that’s not publicly talked about.” It’s all above board, app companies have claimed, because the arrangement is spelled out in their privacy policies and there are precautions built in. Experts say those precautions aren’t enough. The data is typically stripped of the most obvious identifying information like a name, email or cell number. However, it still contains information that could reveal the person behind it, such as a device ID, an IP address or an advertising identifier. With the
- 5. Page 5 of 10 right outside information or a third-party service, so-called anonymous data can be de-anonymized, as the Pillar claims it did in the case of Burrill. In this case, the Pillar says it “correlated a unique mobile device to Burrill” using his presence at his family lake house, meetings he attended and the USCCB staff residence and headquarters. It did not say how it collected that information.The Pillar says the data set it used was “commercially available app signal data” from a data vendor that included Grindr information, but it did not name the vendor or clarify if it bought the data directly from a broker or received it from another party. In a 2013 paper, researchers found that as little as four pieces of data on average were enough to re-identify someone 95 percent of the time. Latanya Sweeney, a data privacy expert and professor at Harvard Kennedy School, showed how just a Zip code, age and gender could be used to identify patients in anonymous hospital data sets. Even something as simple as a
- 6. Page 6 of 10 person’s work and home address could be enough to find a pattern strong enough to identify anonymous location data. A 2020 study by the Norwegian Consumer Council found that Grindr and other apps were sharing personal data about their users with outside companies, including numerous data brokers. In Grindr’s case, it also shared detailed location data, according to the Norwegian researchers. In January this year, the Norwegian Data Protection Authority said it would fine Grindr $11.7 million for sharing data without users’ consent. In its response, Grindr confirmed that it shared data, including a hashed device ID, age, gender and location information with advertisers, but claimed that it was done with consent from users and that the app had since updated its sharing policies. “Historical data collection remains a problem,” said Tor Erling Bjorstad, a security researcher at Mnemonic who was in charge of the Norwegian Consumer Council research report. “GPS
- 7. Page 7 of 10 position data collected in 2019 and earlier is still out there, and can still have explosive power.” Grindr said in a statement in response to the Pillar newsletter post on Tuesday that the alleged activities are “incredibly unlikely to occur.” However, on Wednesday, it shared an updated statement saying that “we do not believe Grindr is the source of the data” and that the company had policies and systems in place to protect personal data. It did not specify what they were. How you can protect yourself What is stopping similar instances from happening to other people? Very little, according to privacy experts. “Consumers don’t really have the tools to be able to protect themselves,” said Serge Egelman, research director of the Usable Security and Privacy Group at the International Computer Science Institute. “Once the data leaves the device, there’s no way of knowing what’s actually going to happen to it,
- 8. Page 8 of 10 what other third parties will receive it. … There’s no knowledge of how the data will be used by anyone.” Trying to fully protect your data would be a full-time job, and not something most smartphone owners could easily manage. To start, you’d need to comb through every privacy policy, manually opt out of any relevant sharing options for each app you download, use a virtual private network, or VPN, and maybe move somewhere with stronger consumer privacy protections like the European Union or even California. In California, individuals have the right to ask companies not to sell their personal information, including anything under a pseudonymous identification like their device ID, if they know it. They can opt out of letting data brokers sell their information, one by one — an arduous task. In other locations, that process isn’t available or is impossible. There are some steps you can take to try to reduce your exposure, says EFF’s Cyphers.
- 9. Page 9 of 10 Download fewer smartphone apps in general and delete anything you don’t use. Lock down the kinds of data the remaining apps are able to access, especially your location. Go into your phone’s privacy settings and look up location sharing, where you should find a list of apps with access to your location. Both Android and iOS devices let you limit when an app can access your location. Always limit location access to while you’re using the app or make the app ask each time, and never let an app continuously track your location in the background without an exceptionally good reason. Reset your advertising ID in your smartphone’s settings. If you’re worried about someone knowing your browsing history, use a VPN, but be careful about which ones. (Cyphers says a VPN won’t protect your location information as well.) Ultimately, it’s an overwhelming amount of work to ask of regular people. It’s a problem that may require more serious intervention, such as privacy regulation or even stricter rules for apps from the smartphone makers themselves.
- 10. Page 10 of 10 “Time and time again, whenever the burden is on users to opt out of something, the vast amount of users are not going to opt out of that thing,” said Cyphers.
