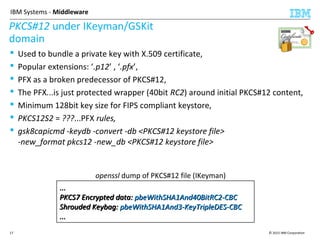
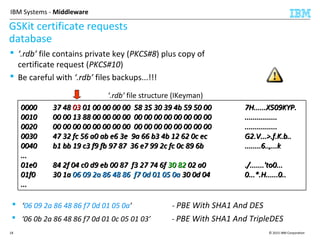
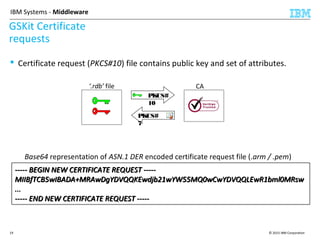
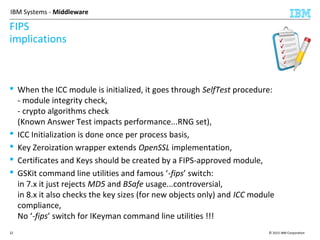
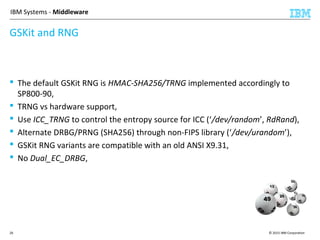
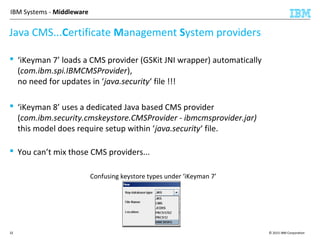
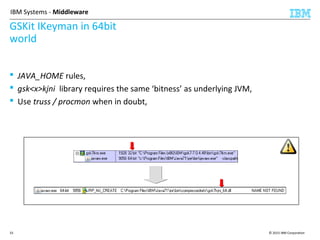
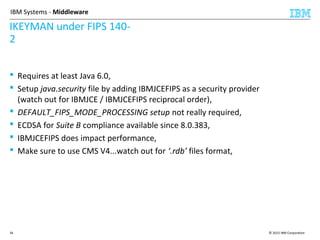
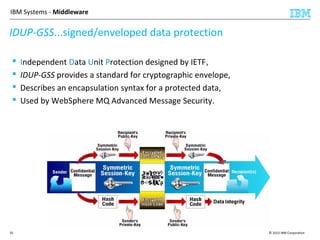
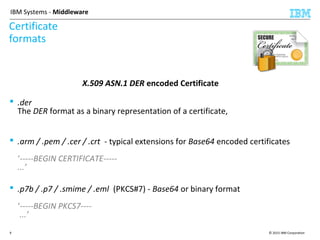
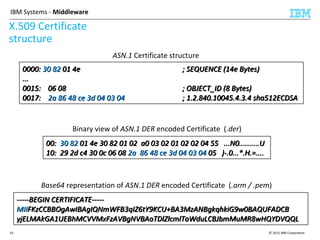
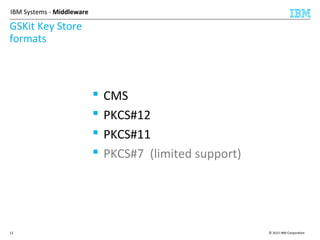
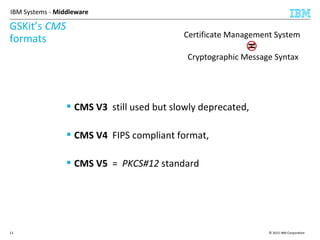
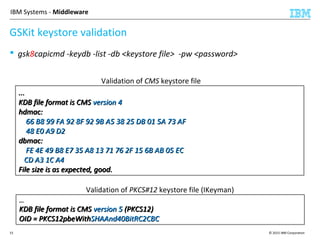
This document discusses IBM's Global Security Kit (GSKit), which provides cryptographic functionality for IBM middleware applications. GSKit implements SSL/TLS for secure communication and uses standardized algorithms and key formats that are FIPS certified. It supports a variety of IBM products running on different platforms and operating systems. The document describes GSKit components, commands, application programming interfaces, certificate formats, and key store formats like CMS, PKCS#12, and PKCS#11.







![© 2015 IBM Corporation16
IBM Systems - Middleware
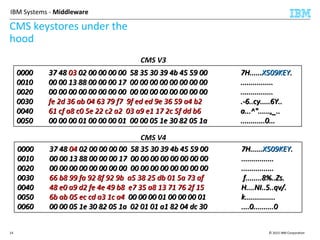
CMS Keystore password
tale
0000 85 94 86 86 82 9a 87 91 c7 f5 4e 25 8b aa 05 9c ..........N%....
0010 d0 b4 fd 59 91 95 a4 0a d9 85 98 7d ba 59 e7 10 ...Y.......}.Y..
0020 3f 05 ce cb 96 e1 4e 11 4b 89 71 ae 25 d8 82 29 ?.....N.K.q.%..)
0030 ca bf f9 4f 02 47 1a 57 18 2b f4 14 68 fa f2 50 ...O.G.W.+..h..P
0040 d8 cd 04 3b 21 4e fe 2a f7 4b 71 ba a2 3c 5f 63 ...;!N.*.Kq..<_c
0050 b1 76 69 df fe f4 86 0f 4e 43 9e 7d db 5a 57 66 .vi.....NC.}.ZWf
0060 16 99 79 87 fa a3 2e ec 6f fc 5d 1c 3a ed b7 dc ..y.....o.].:...
0070 54 9d 4f c2 4a 75 7c 7a ef f1 43 c8 ab ff bd c2 T.O.Ju|z..C.....
0000 85 94 86 86 82 9a 87 91 c7 f5 4e 25 8b aa 05 9c ..........N%....
0010 d0 b4 fd 59 91 95 a4 0a d9 85 98 7d ba 59 e7 10 ...Y.......}.Y..
0020 3f 05 ce cb 96 e1 4e 11 4b 89 71 ae 25 d8 82 29 ?.....N.K.q.%..)
0030 ca bf f9 4f 02 47 1a 57 18 2b f4 14 68 fa f2 50 ...O.G.W.+..h..P
0040 d8 cd 04 3b 21 4e fe 2a f7 4b 71 ba a2 3c 5f 63 ...;!N.*.Kq..<_c
0050 b1 76 69 df fe f4 86 0f 4e 43 9e 7d db 5a 57 66 .vi.....NC.}.ZWf
0060 16 99 79 87 fa a3 2e ec 6f fc 5d 1c 3a ed b7 dc ..y.....o.].:...
0070 54 9d 4f c2 4a 75 7c 7a ef f1 43 c8 ab ff bd c2 T.O.Ju|z..C.....
‘password2’
0000 85 94 86 86 82 9a 87 91 c4 f5 af 58 00 2d d8 f3 ...........X.-..
0010 63 a1 81 1a ea 4e 83 22 a7 8f b5 4d 85 da 88 49 c....N."...M...I
0020 82 42 ce 45 a5 8d d6 9f 59 ed 10 ea 06 72 46 f3 .B.E....Y....rF.
0030 0a 9d be 2b c5 bf 0c 88 ed 65 b4 6a 6b 2d 0a 4e ...+.....e.jk-.N
0040 c2 f3 b2 ac 01 be e2 ff 55 3f cf 50 72 47 31 33 ........U?.PrG13
0050 24 8c c3 17 27 12 84 f4 e2 ce 57 6c 18 96 47 be $...'.....Wl..G.
0060 f8 ad 19 f6 d6 64 df b8 e4 22 3c 32 73 8a dc ca .....d..."<2s...
0070 be 94 bf 51 f7 07 6e d6 14 ec 5e 33 c3 c0 71 d2 ...Q..n...^3..q.
0000 85 94 86 86 82 9a 87 91 c4 f5 af 58 00 2d d8 f3 ...........X.-..
0010 63 a1 81 1a ea 4e 83 22 a7 8f b5 4d 85 da 88 49 c....N."...M...I
0020 82 42 ce 45 a5 8d d6 9f 59 ed 10 ea 06 72 46 f3 .B.E....Y....rF.
0030 0a 9d be 2b c5 bf 0c 88 ed 65 b4 6a 6b 2d 0a 4e ...+.....e.jk-.N
0040 c2 f3 b2 ac 01 be e2 ff 55 3f cf 50 72 47 31 33 ........U?.PrG13
0050 24 8c c3 17 27 12 84 f4 e2 ce 57 6c 18 96 47 be $...'.....Wl..G.
0060 f8 ad 19 f6 d6 64 df b8 e4 22 3c 32 73 8a dc ca .....d..."<2s...
0070 be 94 bf 51 f7 07 6e d6 14 ec 5e 33 c3 c0 71 d2 ...Q..n...^3..q.
‘password1’](https://image.slidesharecdn.com/gskit-2015techacademy-160117100047/85/IBM-Global-Security-Kit-as-a-Cryptographic-layer-for-IBM-middleware-16-320.jpg)