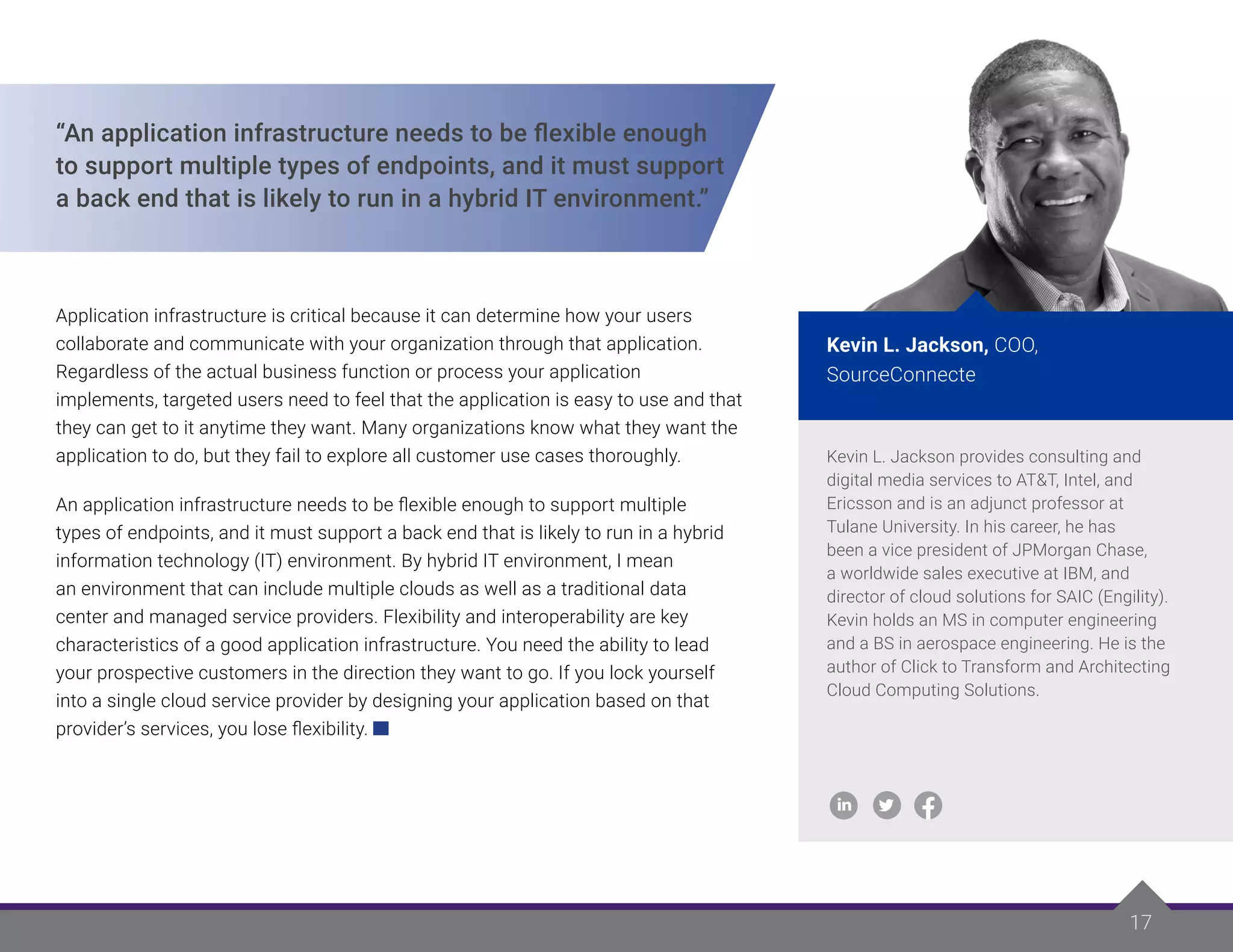
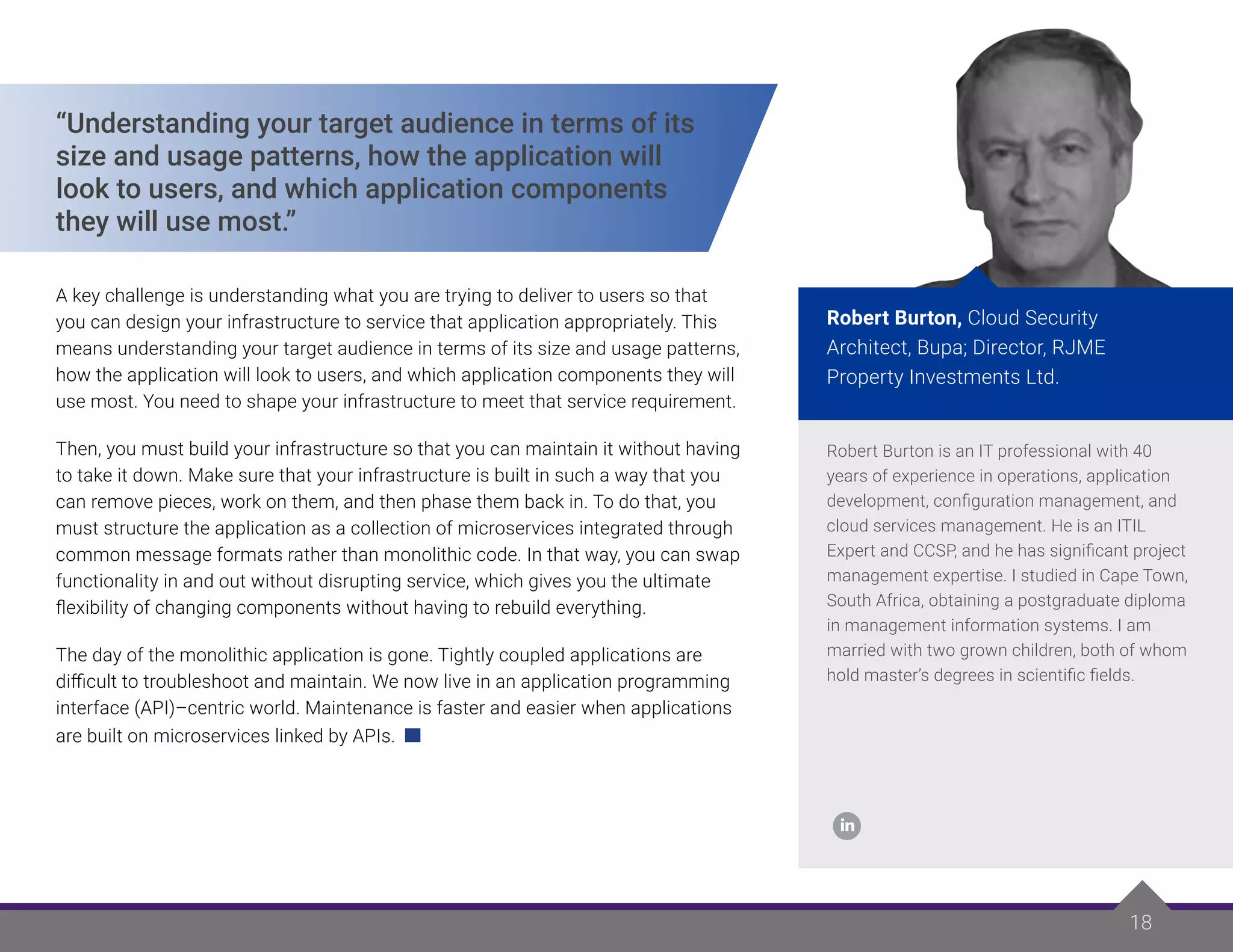
The experts discuss several major considerations when selecting an application infrastructure:
- Access controls, authentication management, common data stores, and messaging infrastructure are essential platform capabilities.
- Balance costs, performance needs, data usage, and scalability requirements based on the application's users and purpose.
- Thoroughly review the application's requirements, use cases, data needs, security risks, and integration requirements before choosing.
- Focus first on the business problems and outcomes needed, then determine the necessary delivery and support mechanisms.































![37
“[An] invaluable tool for a complex application
environment is an artificial intelligence/machine
learning tool that monitors all traffic and activity
in the environment and alerts you to anything
suspicious.”
The biggest challenge with security is trying to manage the unknown. It
keeps you awake at night.
In a hybrid environment, you need a hardened perimeter on fixed assets,
such as a corporate data center; with load-balancing and network policy
controllers, you need plenty of firewall protection, as well. Encrypting data
at rest and in flight is important. Another invaluable tool for a complex
application environment is an artificial intelligence/machine learning tools
that monitors all traffic and activity in the environment and alerts you to
anything suspicious.
Application programming interface (API) authentication is also important.
I have found it valuable to ensure that every API has secure keys and
performs a handshake for authentication. It is also critical to implement
tools that enable the verification that an API call has been authorized.
Another best practice, outside your internal domain, is to ensure that all
access of this type require multifactor authentication.
When workloads are moved to a major cloud provider environment, I
have seen that the level of security goes up dramatically, assuming that
Adan K. Pope is a leading authority
on digital transformation, strategic
technology leadership and disruption
with over thirty years of career
experience. He has held almost every
role in software technology innovation
and development from developer
to chief technology and innovation
officer for some of the most innovative
technology companies including
Ericcson, ShopperTrak, Ciena, and
InnerWorkings.
Adan Pope, Serial Chief Technology
Officer and Innovator](https://image.slidesharecdn.com/citrix-210204123408/75/8-Experts-on-Flawless-App-Delivery-37-2048.jpg)
















![57
“[Machine learning] adds value in environments where
there are many data points and it’s not clear which data
points influence which other data points.”
There are four layers to effective troubleshooting:
• Information that you receive. Build a layer of communication that helps you
receive essential diagnostic information, not just someone creating a ticket. You
need the ability to pull a status record or a mechanism for telling the app to send a
compilation of all known information relevant to an incident.
• Understanding what happened. The information you receive is useless if you do
not understand it. You need data in a digestible form, and the team must have the
skills to understand what it means.
• Operational circumstances. This layer can pose a significant challenge for
developers because they will never have the exact set of data points or the exact
number of transactions that take place in a live environment going on in their testing
environment.
• Access to code. Sometimes, particularly in larger companies, developers or
support teams do not always have technical access at the level they need to be
able to feed the diagnostic and test data into the system to see what is actually
happening.
Early in his career, Johannes Drooghaag
realized that the development of
technology outpaces the development of
our understanding of technology. Working
based on the principal that we don’t have
to understand the bits and bytes to use
technology, but we must understand how
to use it optimal and secure, Johannes
developed consulting services, training
programs, keynotes and workshops to
allow people and organizations to do just
that: embrace technology in the optimal
and secure way.
Dr. Ir Johannes Drooghaag, CEO,
Spearhead Management](https://image.slidesharecdn.com/citrix-210204123408/75/8-Experts-on-Flawless-App-Delivery-57-2048.jpg)