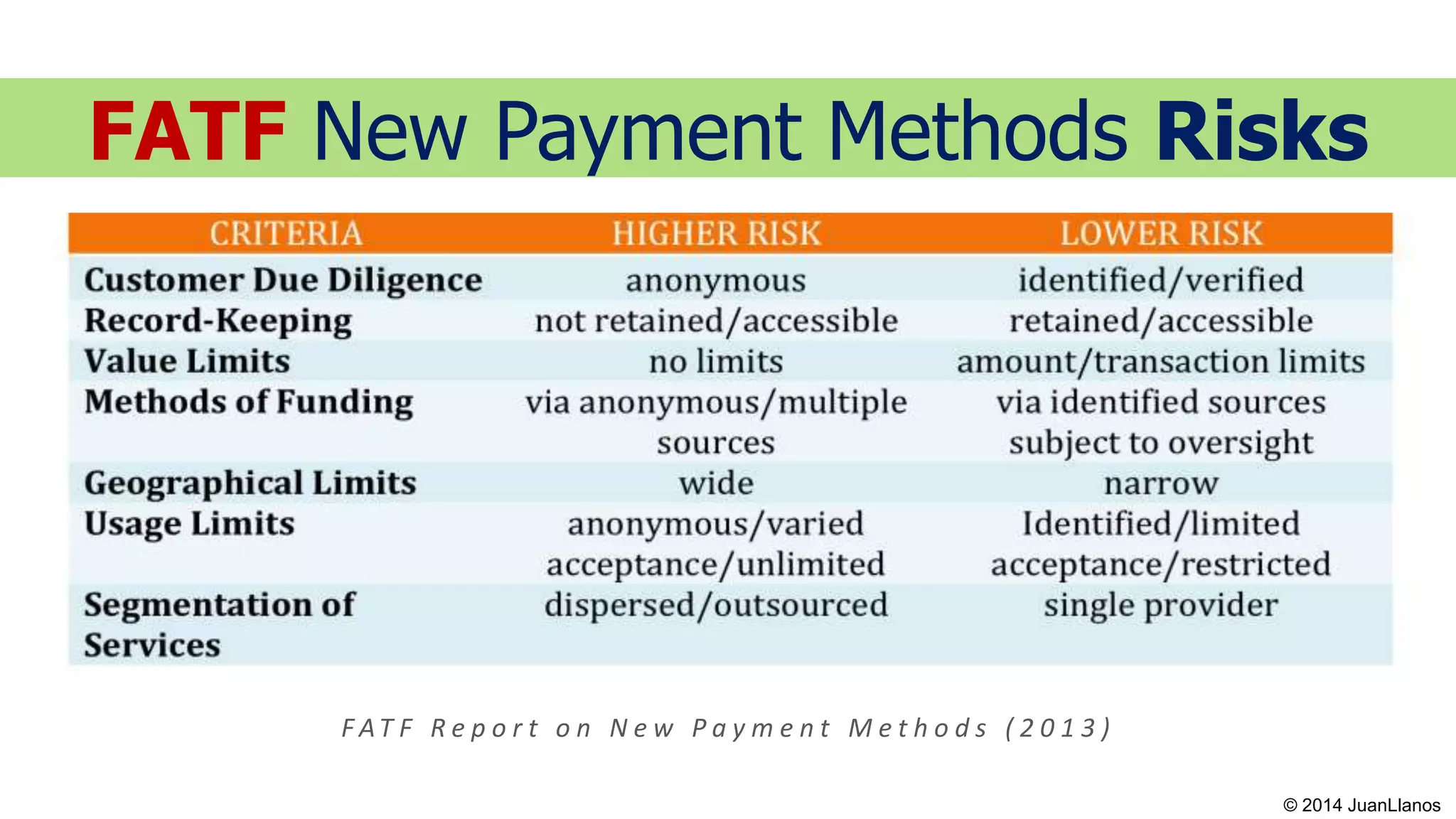
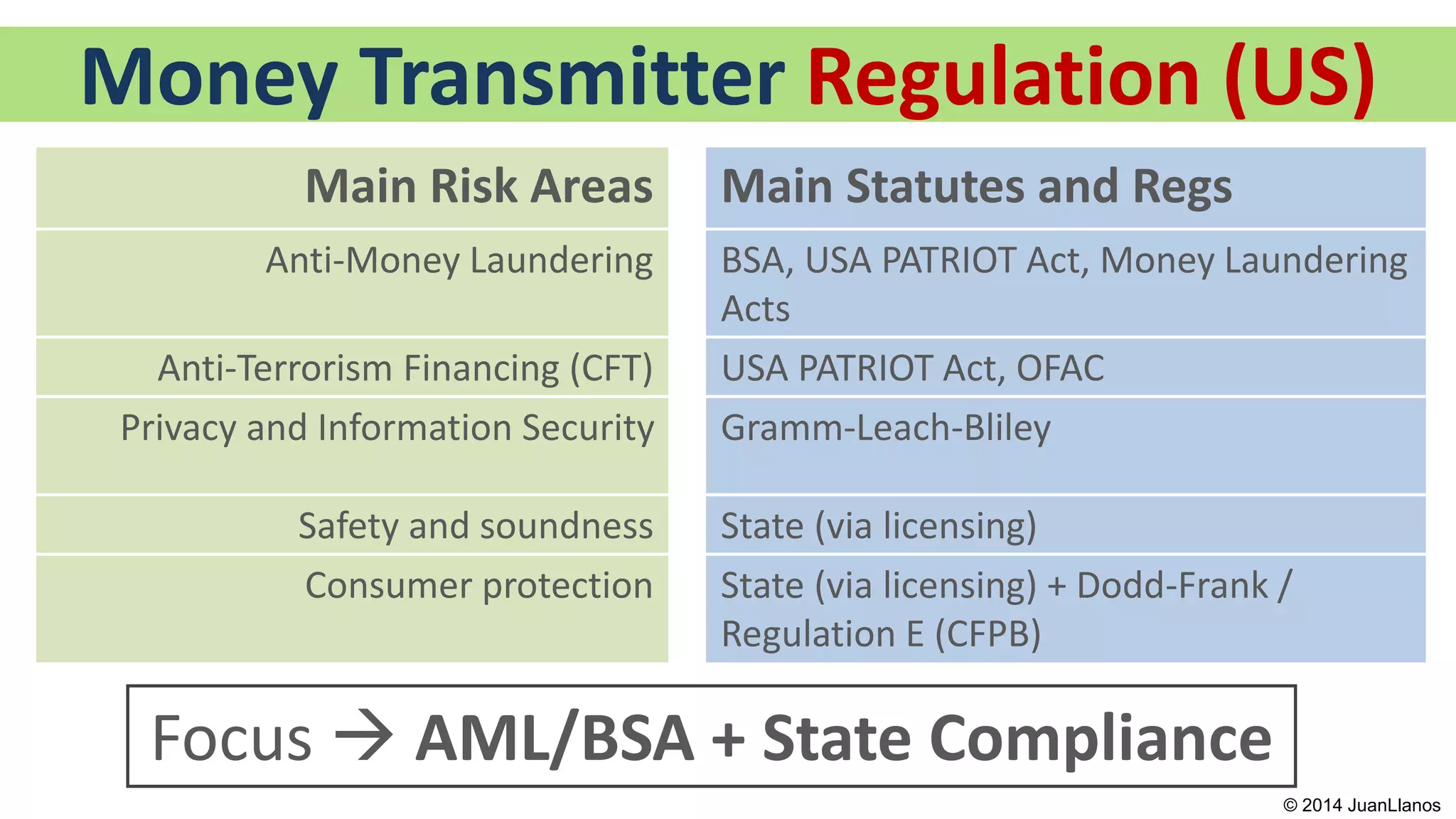
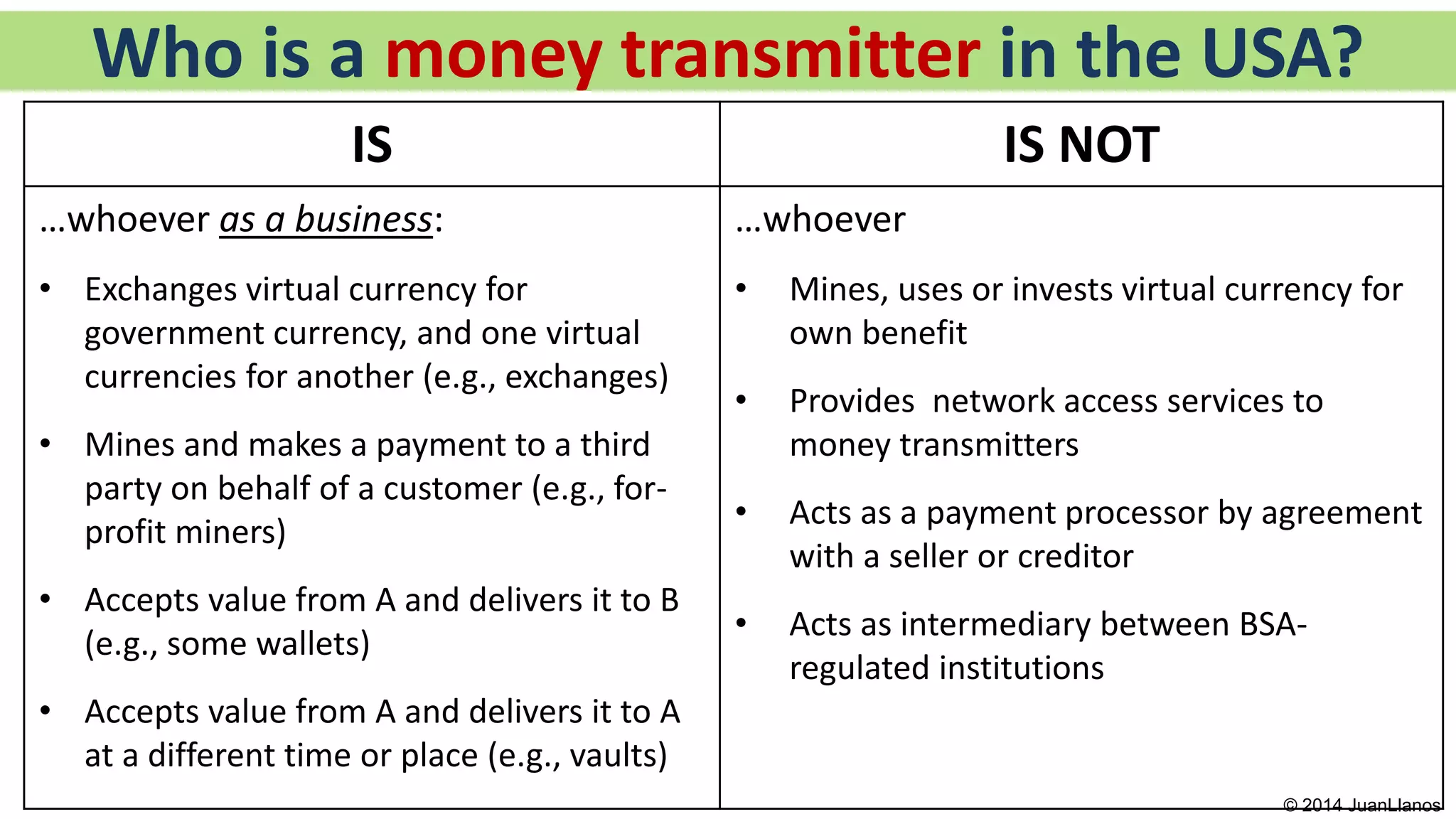
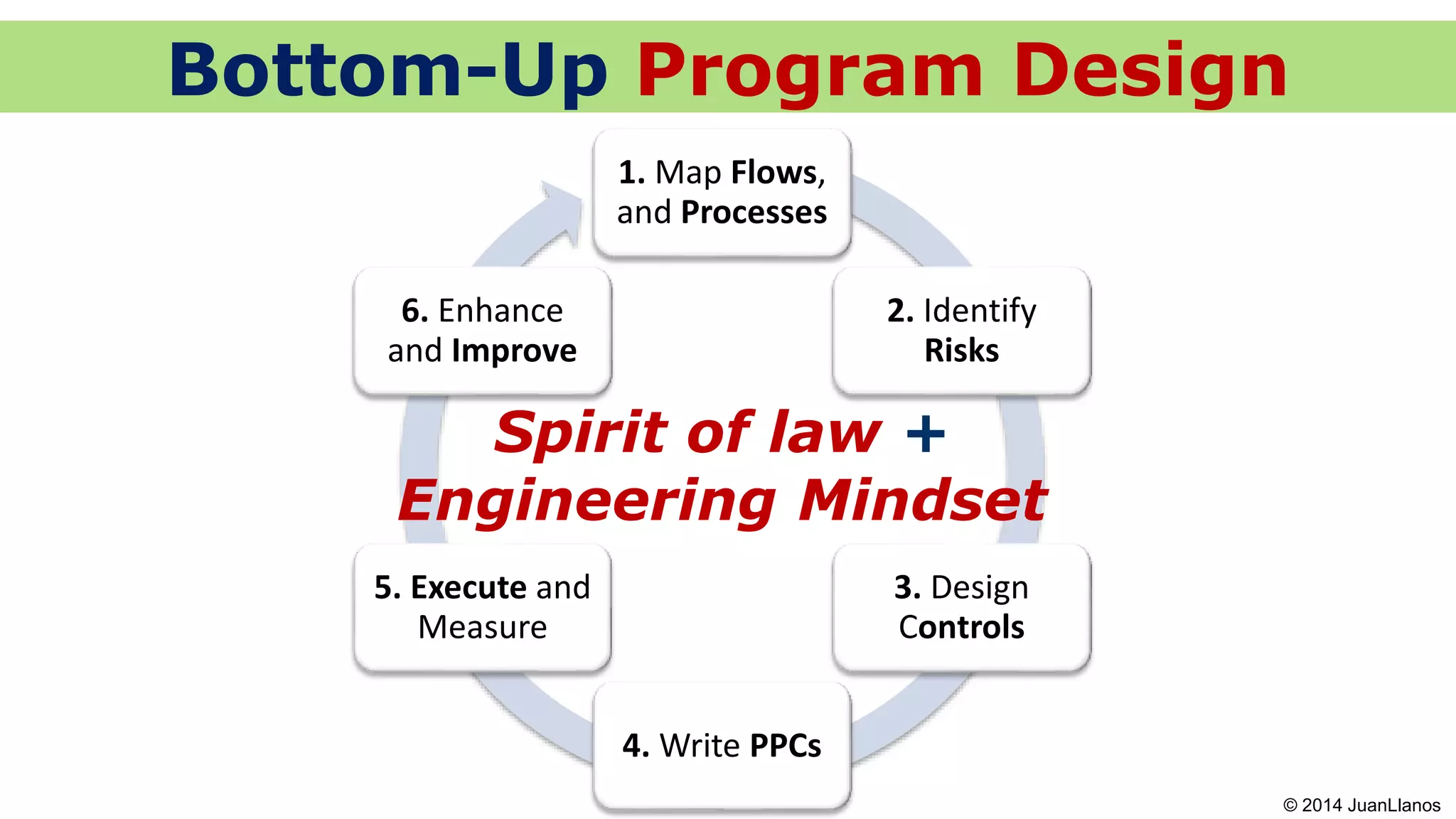
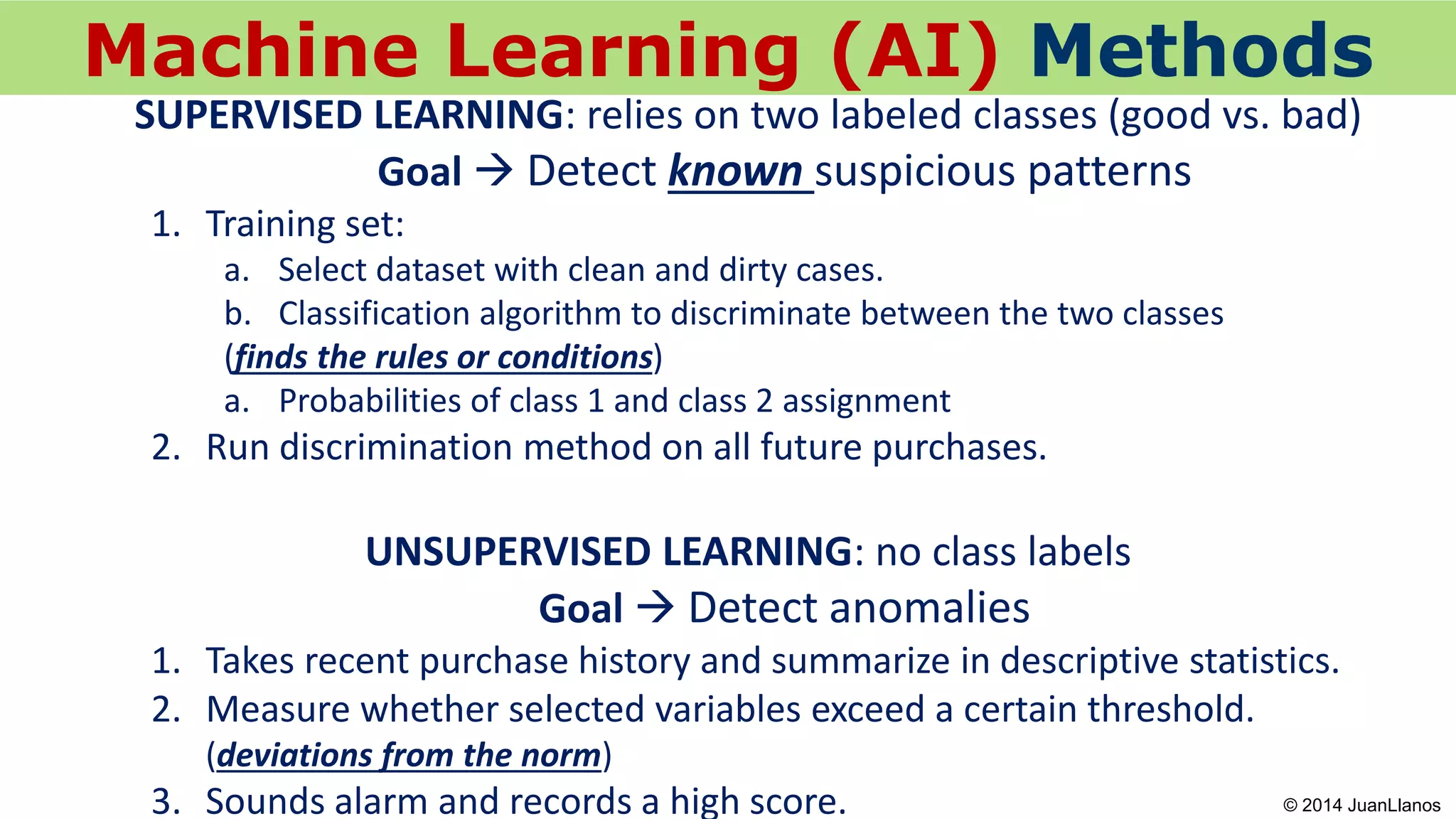
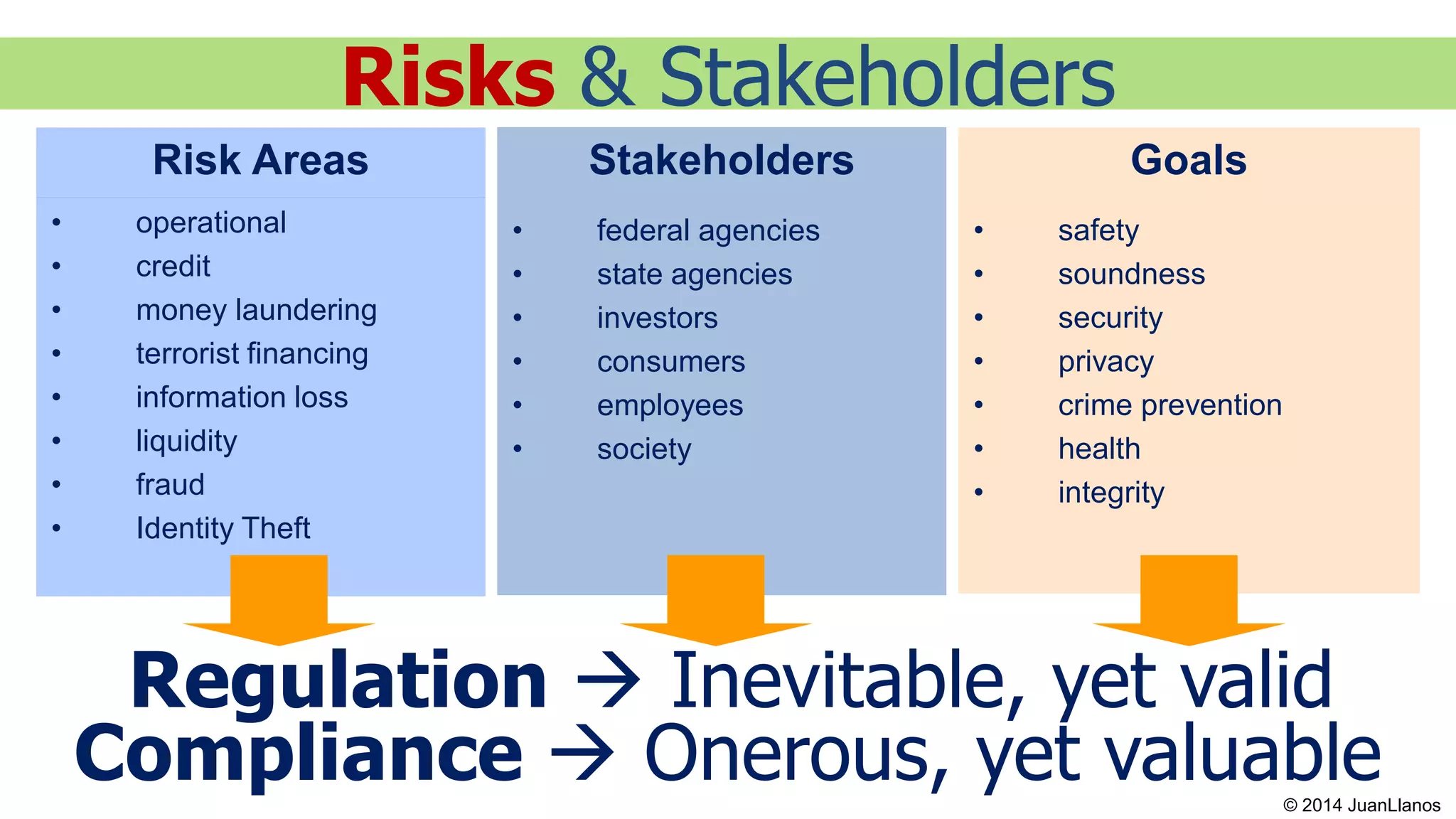
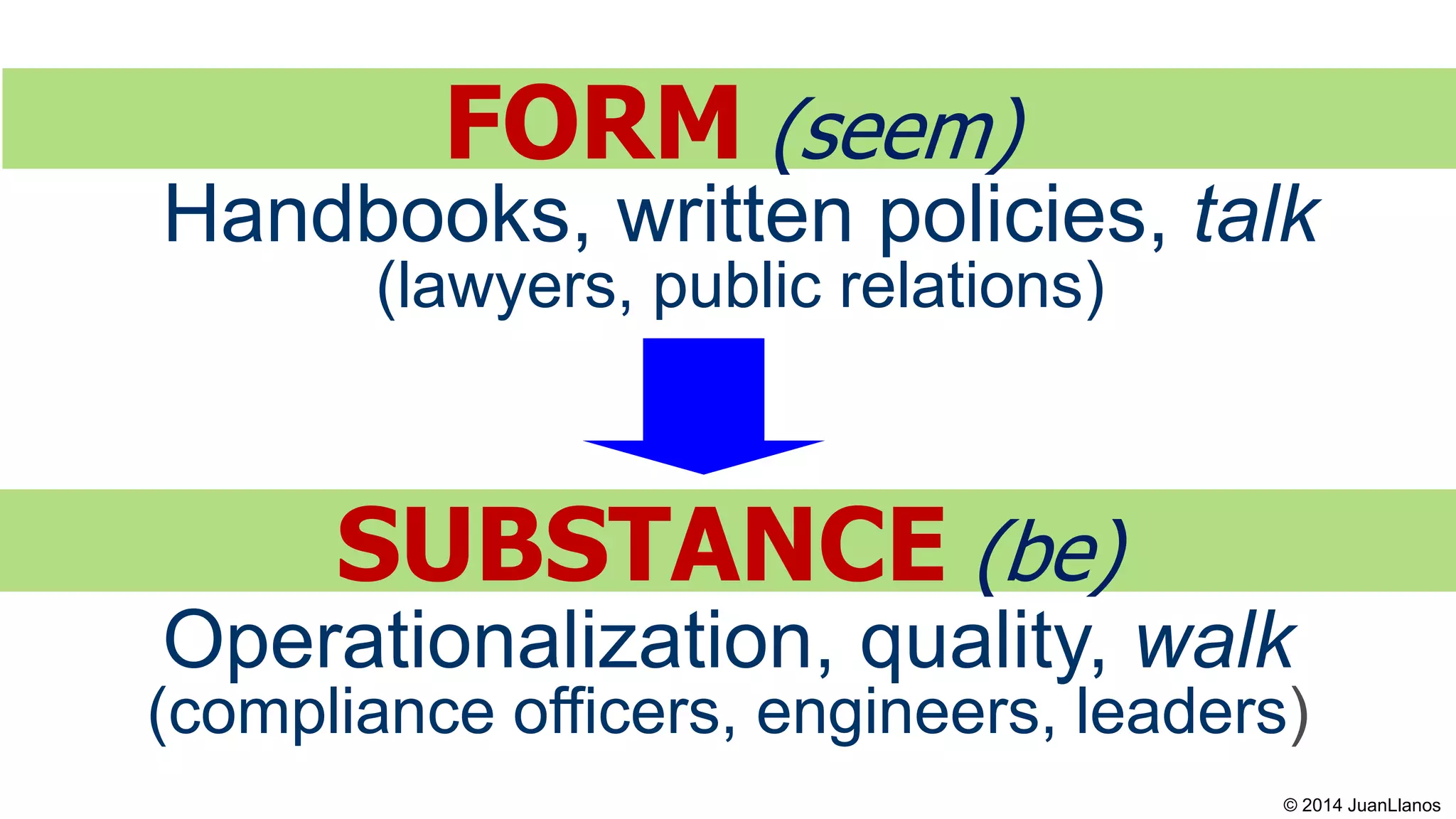
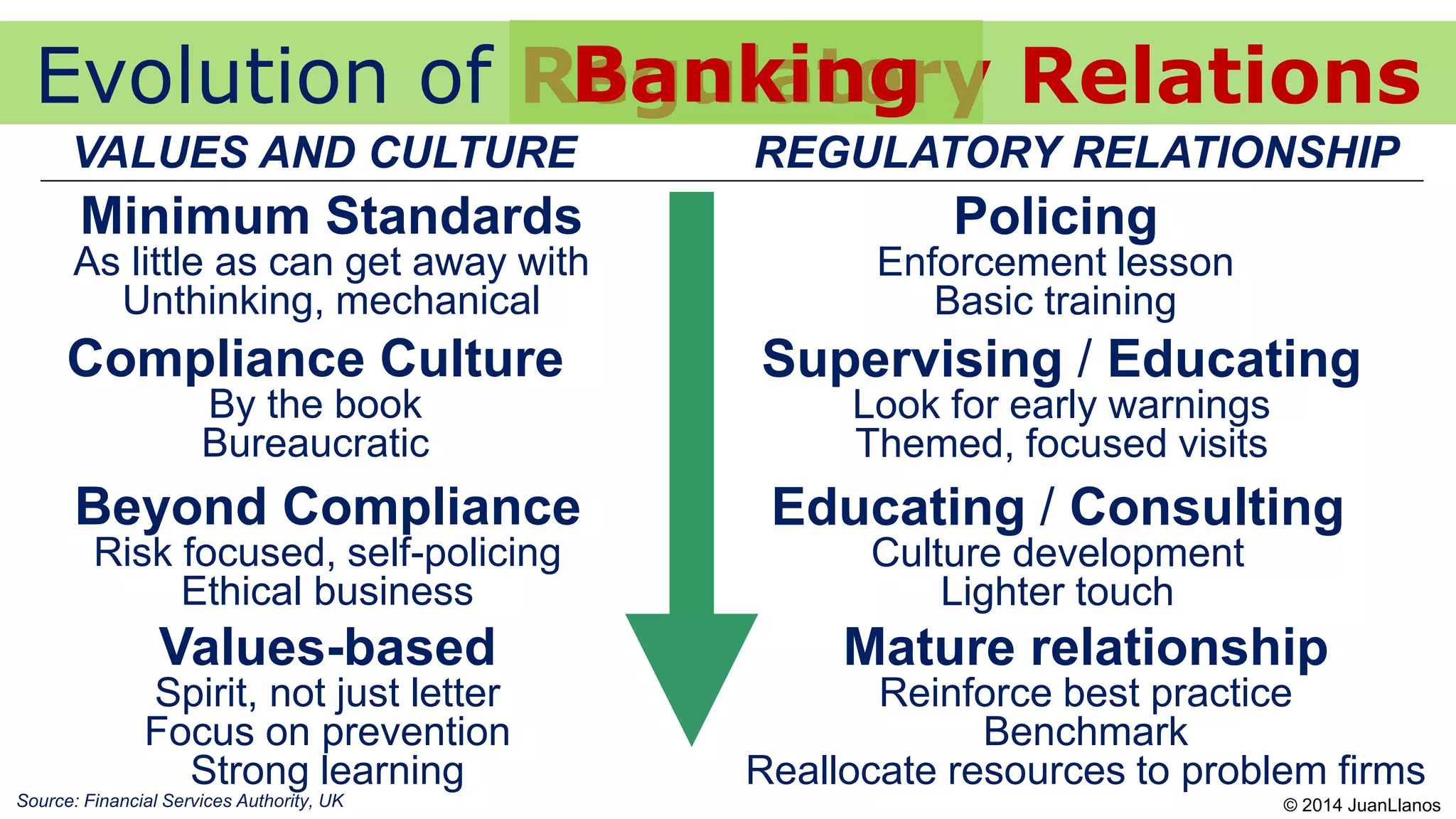
This document summarizes a presentation on Bitcoin and anti-money laundering (AML) regulation strategies. It discusses key risks like money laundering that virtual currency companies need to focus on mitigating. It provides tips for designing effective AML programs, including mapping money flows and processes. It also outlines tools for customer identification and behavioral analytics to help "de-anonymize" transactions. The presentation emphasizes the importance of substance over form in AML compliance and moving beyond a minimal compliance culture to a values-based, risk-focused approach to regulatory relationships.